Deck 9: Risk Management: Controlling Risk
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/26
العب
ملء الشاشة (f)
Deck 9: Risk Management: Controlling Risk
1
Mike and Iris were reviewing the asset valuation worksheets that had been collected from all the company managers.
"Iris," Mike said after a few minutes, "the problem, as I see it, is that no two managers gave us answers that can be compared to each other's. Some gave only one value, and some didn't actually use a rank order for the last part. In fact, we don't know what criteria were used to assess the ranks or even where they got the cost or replacement values."
"I agree," Iris said, nodding. "These values and ranks are really inconsistent. This makes it a real challenge to make a useful comprehensive list of information assets. We're going to have to visit all the managers and figure out where they got their values and how the assets were ranked."
If you could have spoken to Mike Edwards before he distributed the asset valuation worksheets, what advice would you have given him to make the consolidation process easier
"Iris," Mike said after a few minutes, "the problem, as I see it, is that no two managers gave us answers that can be compared to each other's. Some gave only one value, and some didn't actually use a rank order for the last part. In fact, we don't know what criteria were used to assess the ranks or even where they got the cost or replacement values."
"I agree," Iris said, nodding. "These values and ranks are really inconsistent. This makes it a real challenge to make a useful comprehensive list of information assets. We're going to have to visit all the managers and figure out where they got their values and how the assets were ranked."
If you could have spoken to Mike Edwards before he distributed the asset valuation worksheets, what advice would you have given him to make the consolidation process easier
Before the distribution of the asset valuation worksheets following should have been done.
1. A meeting should have been called, and a list of assets for which valuation was required should have been worked out.
2. A list containing assets based on their ranks should have been distributed among the managers, and then they should have been asked the priorities. If possible then asset valuation should have done based on some qualitative features. The criteria should have been conveyed to managers. For example: Assets which gives maximum rate of return. Then managers would have been asked to assess the asset.
1. A meeting should have been called, and a list of assets for which valuation was required should have been worked out.
2. A list containing assets based on their ranks should have been distributed among the managers, and then they should have been asked the priorities. If possible then asset valuation should have done based on some qualitative features. The criteria should have been conveyed to managers. For example: Assets which gives maximum rate of return. Then managers would have been asked to assess the asset.
2
What is competitive advantage How has it changed in the years since the IT industry began
Competitive advantage is the lead an organisation can have over others due to its
• products,
• services, and
• strategies
In the early years when IT Industry began, competitive advantage was to establish a competitive business model, method or technique. This allowed an organisation to provide a product or service that was superior in some decisive way. But with the time it has changed because now IT is readily available to almost all the organisations. Each organisation is willing to make the investment, and they can all react quickly to changes in the market.
• products,
• services, and
• strategies
In the early years when IT Industry began, competitive advantage was to establish a competitive business model, method or technique. This allowed an organisation to provide a product or service that was superior in some decisive way. But with the time it has changed because now IT is readily available to almost all the organisations. Each organisation is willing to make the investment, and they can all react quickly to changes in the market.
3
Mike and Iris were reviewing the asset valuation worksheets that had been collected from all the company managers.
"Iris," Mike said after a few minutes, "the problem, as I see it, is that no two managers gave us answers that can be compared to each other's. Some gave only one value, and some didn't actually use a rank order for the last part. In fact, we don't know what criteria were used to assess the ranks or even where they got the cost or replacement values."
"I agree," Iris said, nodding. "These values and ranks are really inconsistent. This makes it a real challenge to make a useful comprehensive list of information assets. We're going to have to visit all the managers and figure out where they got their values and how the assets were ranked."
How would you advise Mike and Iris to proceed with the worksheets they already have in hand
"Iris," Mike said after a few minutes, "the problem, as I see it, is that no two managers gave us answers that can be compared to each other's. Some gave only one value, and some didn't actually use a rank order for the last part. In fact, we don't know what criteria were used to assess the ranks or even where they got the cost or replacement values."
"I agree," Iris said, nodding. "These values and ranks are really inconsistent. This makes it a real challenge to make a useful comprehensive list of information assets. We're going to have to visit all the managers and figure out where they got their values and how the assets were ranked."
How would you advise Mike and Iris to proceed with the worksheets they already have in hand
They can take the following steps:
• Make their own one universal list of assets, and if possible, then decide the criteria of prioritizing the assets in the list.
• Put the names of the managers in rows.
• Place their assigned values in cells. Values in extremes can be marked. For instance, a manager may have given 100% priority to an asset.
• Print the matrix.
• Ask each manager about their choices based on the criteria. If there is any change, update the sheet.
• Make their own one universal list of assets, and if possible, then decide the criteria of prioritizing the assets in the list.
• Put the names of the managers in rows.
• Place their assigned values in cells. Values in extremes can be marked. For instance, a manager may have given 100% priority to an asset.
• Print the matrix.
• Ask each manager about their choices based on the criteria. If there is any change, update the sheet.
4
How did the XYZ Software Company arrive at the values shown in the table that is included in Exercise 1 For each row in the table, describe the process of determining the cost per incident and the frequency of occurrence.
Reference: Exercise 1
Using the following table, calculate the SLE, ARO, and ALE for each threat category listed.
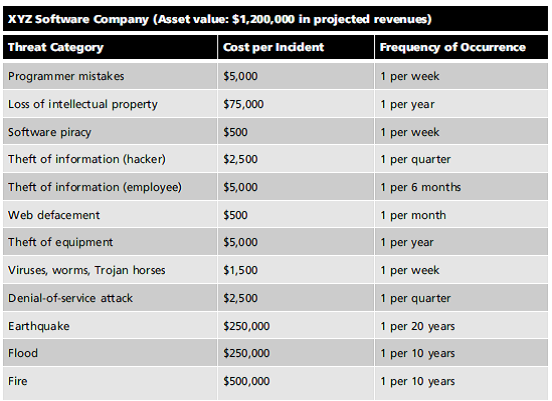
Reference: Exercise 1
Using the following table, calculate the SLE, ARO, and ALE for each threat category listed.


فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
5
What is competitive disadvantage Why has it emerged as a factor

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
6
What are the five risk control strategies presented in this chapter

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
7
Assume a year has passed and XYZ has improved its security. Using the following table, calculate the SLE, ARO, and ALE for each threat category listed.
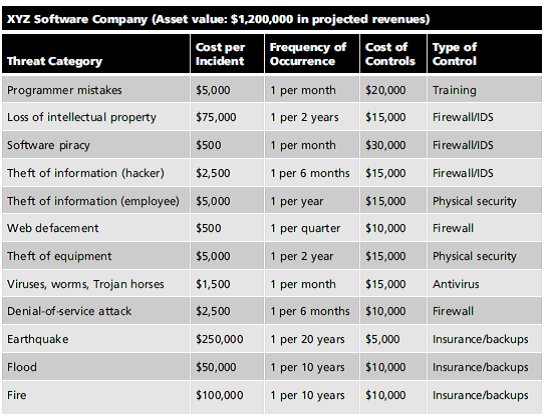
Why have some values changed in the following columns: Cost per Incident and Frequency of Occurrence How could a control affect one but not the other

Why have some values changed in the following columns: Cost per Incident and Frequency of Occurrence How could a control affect one but not the other

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
8
Describe the strategy of defense.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
9
Assume that the costs of controls presented in the table for Exercise 4 were unique costs directly associated with protecting against that threat. In other words, do not worry about overlapping costs between threats. Calculate the CBA for each control. Are they worth the costs listed
Reference: Exercise 4
Assume a year has passed and XYZ has improved its security. Using the following table, calculate the SLE, ARO, and ALE for each threat category listed.
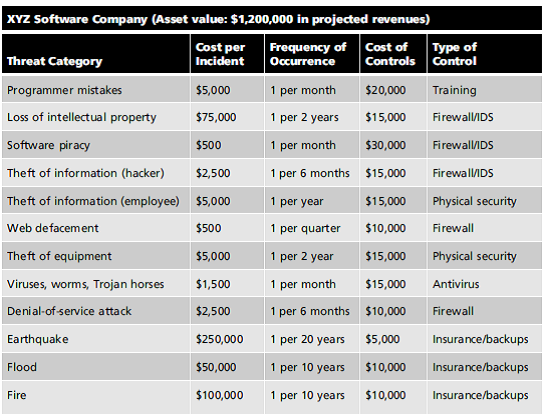
Why have some values changed in the following columns: Cost per Incident and Frequency of Occurrence How could a control affect one but not the other
Reference: Exercise 4
Assume a year has passed and XYZ has improved its security. Using the following table, calculate the SLE, ARO, and ALE for each threat category listed.

Why have some values changed in the following columns: Cost per Incident and Frequency of Occurrence How could a control affect one but not the other

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
10
Describe the strategy of transferal.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
11
Using the Web, research the costs associated with the following items when implemented by a firm with 1,000 employees and 100 servers:
Managed antivirus software (not open source) licenses for 500 workstations
Cisco firewall (other than residential models from LinkSys)
Tripwire host-based IDS for 10 servers
Managed antivirus software (not open source) licenses for 500 workstations
Cisco firewall (other than residential models from LinkSys)
Tripwire host-based IDS for 10 servers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
12
Describe the strategy of mitigation.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
13
Describe the strategy of acceptance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
14
Describe residual risk.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
15
What four types of controls or applications can be used to avoid risk

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
16
Describe how outsourcing can be used for risk transference.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
17
What conditions must be met to ensure that risk acceptance has been used properly

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
18
What is risk appetite Explain why risk appetite varies from organization to organization.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
19
What is a cost-benefit analysis

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
20
What is the difference between intrinsic value and acquired value

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
21
What is single loss expectancy What is annual loss expectancy

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
22
What is the difference between benchmarking and baselining

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
23
What is the difference between organizational feasibility and operational feasibility

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
24
What is the difference between qualitative measurement and quantitative measurement

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
25
What is the OCTAVE Method What does it provide to those who adopt it

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck
26
How does Microsoft define "risk management" What phases are used in its approach

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 26 في هذه المجموعة.
فتح الحزمة
k this deck








