Deck 9: Sending E-Mail and Attachments
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/75
العب
ملء الشاشة (f)
Deck 9: Sending E-Mail and Attachments
1
An e-mail letter is a file that travels along with an e-mail message.
False
2
Compressed files usually have a .zip file extension.
True
3
When you want to compose or read e-mail messages, your first step is to start an e-mail client.
True
4
Remote e-mail allows you to compose and read your mail while you are offline.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
5
If you want to send a larger file, you might be able to compress it before you attach it.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
6
Software designed for creating images, videos, and music usually offers ways to save your work in compressed file formats.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
7
Your incoming mail remains on the Web server rather than on your own computer when using local e-mail .

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
8
An e-mail message is a computer that essentially acts as a central post office serving a group of people.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
9
One of the advantages of Web-based e-mail is its availability from any computer that's connected to the Internet.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
10
All file formats can be compressed significantly.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
11
One of e-mail's main disadvantages is junk .

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
12
When you receive a compressed folder, you have to undress it to extract the files and folders it contains, reconstituting them to their original state.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
13
Your e-mail client software transmits the message files from your Outbox to the mail server.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
14
A spam filter is a type of utility software that captures unsolicited e-mail messages before they reach your Inbox.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
15
Most e-mail software indicates the existence of an attachment with a symbol.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
16
You can attach files that are in virtually any format, including DOCX documents, PDF documents, MP3 music, and JPEG images.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
17
E-mail is an electronic version of the postal system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
18
Messages that pertain to a particular topic are sometimes referred to as a weave.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
19
When using a private computer to access your e-mail account, it is important to log off when you are done to make sure that unauthorized persons do not use your account.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
20
Your e-mail client might provide a way to prioritize messages, allowing you to deal with the most urgent correspondence first.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
21
Unread mail is usually displayed in ____, and that feature helps to ensure that you've not missed an important message.
A) blue
B) italics
C) bold
D) color
A) blue
B) italics
C) bold
D) color

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
22
Files with ____ extensions, such as .exe, .com, .bat, and .app, are blocked by most e-mail servers.
A) top-level
B) executable
C) encrypted
D) executive
A) top-level
B) executable
C) encrypted
D) executive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
23
Some attachments harbor viruses, especially those with a(n) ____ extension.
A) .jpeg
B) .docx
C) .exe
D) .zip
A) .jpeg
B) .docx
C) .exe
D) .zip

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
24
You can organize messages by creating additional folders in your ____.
A) Outbox
B) Inbox
C) hard drive
D) desktop
A) Outbox
B) Inbox
C) hard drive
D) desktop

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
25
Which of the following is NOT an e-mail service?
A) Google Gmail
B) Microsoft Outlook
C) Yahoo! Mail
D) NBC Mail
A) Google Gmail
B) Microsoft Outlook
C) Yahoo! Mail
D) NBC Mail

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
26
As part of the setup process for local email, you must have local ____ software.
A) e-mail client
B) e-mail system
C) e-mail
D) POP mail
A) e-mail client
B) e-mail system
C) e-mail
D) POP mail

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
27
Local e-mail is based on ____ technology, which means that an e-mail server stores incoming messages until your client computer connects and requests them.
A) input-and-output
B) send-and-receive
C) store-and-send
D) store-and-forward
A) input-and-output
B) send-and-receive
C) store-and-send
D) store-and-forward

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
28
The person who receives an attachment can double-click the ____ to open the attachment.
A) icon
B) file name
C) >
D) <
A) icon
B) file name
C) >
D) <

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
29
To get your mail, connect to the mail server and download new messages to your ____.
A) POP mailbox
B) local box
C) Inbox
D) Outbox
A) POP mailbox
B) local box
C) Inbox
D) Outbox

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
30
The ____ is a folder on your PC's hard disk that temporarily stores outgoing e-mail messages.
A) e-mail box
B) Inbox
C) Outbox
D) Send folder
A) e-mail box
B) Inbox
C) Outbox
D) Send folder

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
31
____ uses Web browser software to connect to the Web to read and compose e-mail messages.
A) Local e-mail
B) Webmail
C) POP mail
D) An e-mail client
A) Local e-mail
B) Webmail
C) POP mail
D) An e-mail client

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
32
Local mail is sometimes called ____ mail.
A) home
B) snail
C) POP
D) received
A) home
B) snail
C) POP
D) received

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
33
An e-mail ____ consists of an original message and all of the replies and forwards that stem from it.
A) server
B) system
C) thread
D) message
A) server
B) system
C) thread
D) message

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
34
Clicking a button labeled ____ replies to a message.
A) Reply
B) Send/Receive
C) Fill Inbox
D) Check Mail
A) Reply
B) Send/Receive
C) Fill Inbox
D) Check Mail

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
35
The computers and software that provide e-mail services form a(n) ____.
A) e-mail system
B) e-mail message
C) e-mail server
D) local e-mail
A) e-mail system
B) e-mail message
C) e-mail server
D) local e-mail

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
36
A(n) ____ is a file that travels along with an e-mail message.
A) attachment
B) letter
C) announcement
D) message
A) attachment
B) letter
C) announcement
D) message

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
37
The information required to obtain an e-mail address includes a user ID and ____.
A) computer ID
B) password
C) code
D) user name
A) computer ID
B) password
C) code
D) user name

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
38
One of the advantages of Webmail is ____.
A) being able to access mail during an Internet outage
B) the potential privacy risk of storing your e-mail on a remote server
C) its availability from any computer that's connected to the Internet
D) its inability to connect on public computers
A) being able to access mail during an Internet outage
B) the potential privacy risk of storing your e-mail on a remote server
C) its availability from any computer that's connected to the Internet
D) its inability to connect on public computers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
39
Because ____ e-mail is stored on your computer's hard disk, you control messages once they have been downloaded.
A) local
B) remote
C) POP
D) Web-based
A) local
B) remote
C) POP
D) Web-based

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
40
An e-mail message is a(n) ____ document that can be transmitted from one computer to another, usually over the Internet.
A) automated
B) Word
C) digital
D) public
A) automated
B) Word
C) digital
D) public

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
41
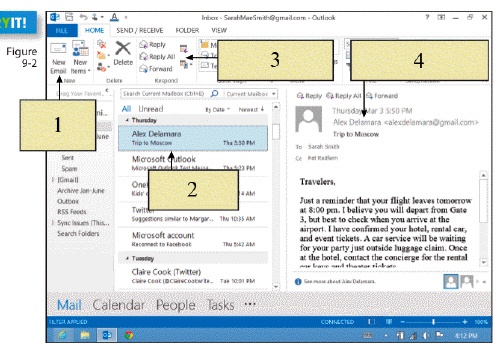
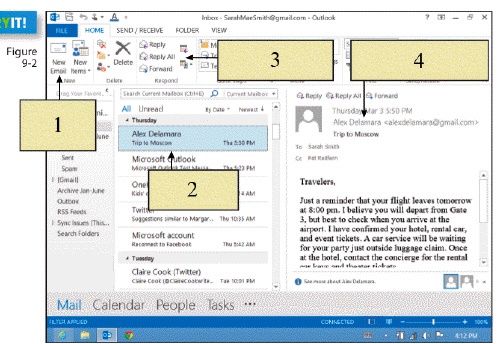 To compose a new e-mail message, you would click on ____ in the figure above.
To compose a new e-mail message, you would click on ____ in the figure above.A) item 1
B) item 2
C) item 3
D) item 4

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
42
Zipped files have an advantage because they are not usually blocked by ____ filters.
A) file
B) spam
C) junk
D) compressed
A) file
B) spam
C) junk
D) compressed

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
43
Which of the following is NOT a step to reduce the amount of spam you receive?
A) Reply to spam when you receive it.
B) Don't click links in e-mail messages, even if it's an opt-out link.
C) If your e-mail provider offers a way to report spam, use it.
D) When spam gets out of hand, consider changing your e-mail account so that you have a different e-mail address.
A) Reply to spam when you receive it.
B) Don't click links in e-mail messages, even if it's an opt-out link.
C) If your e-mail provider offers a way to report spam, use it.
D) When spam gets out of hand, consider changing your e-mail account so that you have a different e-mail address.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
44
____ is a technique for compressing a file and then reconstituting all its data into its original state.
A) Spam filtering
B) Lossy Compression
C) Lossless compression
D) E-mail reply
A) Spam filtering
B) Lossy Compression
C) Lossless compression
D) E-mail reply

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
45
Attachments to ____ are stored in a temporary folder on your computer's hard disk.
A) Webmail
B) all emails
C) local mail
D) zipped files
A) Webmail
B) all emails
C) local mail
D) zipped files

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
46
A(n) ____ is a type of utility software that captures unsolicited e-mail messages before they reach your Inbox.
A) filter
B) spam filter
C) antivirus
D) scan filter
A) filter
B) spam filter
C) antivirus
D) scan filter

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
47
____ replaces a series of similarity colored pixels with a binary code that indicates the number of pixels and their colors.
A) Run-length encoding
B) Phishing
C) File compression
D) E-mail client software
A) Run-length encoding
B) Phishing
C) File compression
D) E-mail client software

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
48
When working with file types that do not offer built-in compression, you can use a standalone compression ____ to shrink the size of a file that you have saved in a non-compressed format.
A) application
B) operating system
C) utility
D) folder
A) application
B) operating system
C) utility
D) folder

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
49
Which is an example of a file format that is not automatically compressed?
A) GIF
B) RAW
C) JPEG
D) MPEG4
A) GIF
B) RAW
C) JPEG
D) MPEG4

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
50
Folders that display a(n) ____ contain compressed files.
A) icon
B) image
C) zipper
D) vice
A) icon
B) image
C) zipper
D) vice

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
51
____ software "zips" or reduces the size of a file using various techniques.
A) Reduction
B) Compression
C) Application
D) Operating system
A) Reduction
B) Compression
C) Application
D) Operating system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
52
Compressed files usually have a(n) ____ file extension.
A) .exe
B) .bmp
C) .pdf
D) .zip
A) .exe
B) .bmp
C) .pdf
D) .zip

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
53
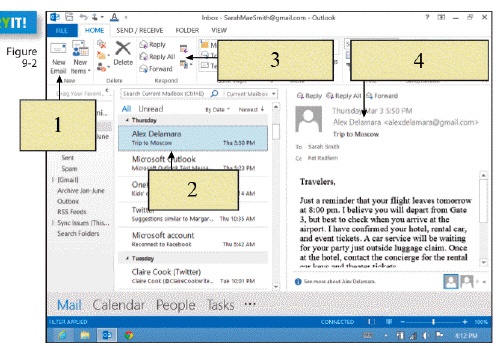 In the figure above, item 4 is pointing to the ____.
In the figure above, item 4 is pointing to the ____.A) Write button
B) message content
C) Inbox
D) Outbox

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
54
An e-mail-based scam that's designed to persuade you to reveal confidential information is called ____.
A) surfing
B) phishing
C) scanning
D) searching
A) surfing
B) phishing
C) scanning
D) searching

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
55
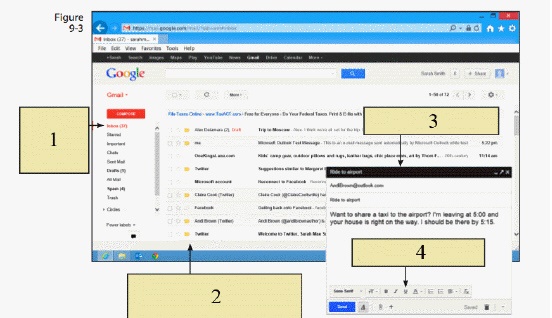 In the figure above, item 1 is pointing to ____.
In the figure above, item 1 is pointing to ____.A) a copy of the original message and waits for you to add the forwarding address
B) a new, blank e-mail and waits for you to add the address and text
C) the Inbox and other folders of incoming and outgoing mail
D) the e-mail and moves it to the Deleted folder

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
56
Unwanted electronic junk mail about medical products, low-cost loans, and fake software that arrives in your online mailbox is known as ____.
A) junk
B) viruses
C) spam
D) propaganda
A) junk
B) viruses
C) spam
D) propaganda

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
57
A Web-based e-mail account that you can discontinue if your account begins to accumulate lots of spam is called a(n) ____.
A) disposable e-mail address
B) temporary e-mail address
C) e-mail address
D) forwarded e-mail address
A) disposable e-mail address
B) temporary e-mail address
C) e-mail address
D) forwarded e-mail address

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
58
Most ____ techniques have adjustable compression levels so that you can decide how much data you can afford to lose.
A) spam filter
B) lossy compression
C) lossless compression
D) e-mail reply
A) spam filter
B) lossy compression
C) lossless compression
D) e-mail reply

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
59
 New mail is downloaded to the ____, represented by item 2 in the figure above.
New mail is downloaded to the ____, represented by item 2 in the figure above.A) Write button
B) message content
C) Outbox
D) Inbox

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
60
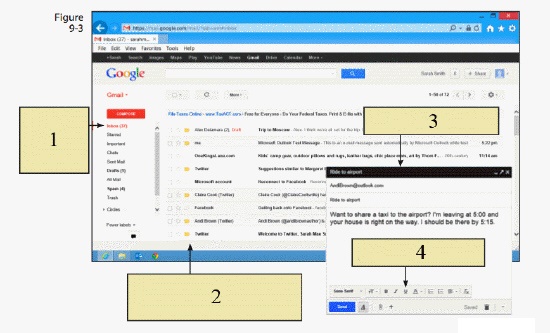 In the figure above, item 2 is pointing to the list of Inbox messages displaying ____.
In the figure above, item 2 is pointing to the list of Inbox messages displaying ____.A) unread messages
B) read and unread messages
C) sent and deleted messages
D) sent messages

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
61
An organizational technique is to create ____________________ that pertain to a specific subject in a folder.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
62
Case-Based Critical Thinking Questions Case 9-1 Tara has just gotten her first computer connected to the Internet. She is very excited to start e-mailing her friends and family. Tara wants to send her aunt some pictures from her last vacation. While attempting to attach the pictures individually to an e-mail, she notices that the file sizes are just too big. In order to easily remedy this problem, Tara should ____.
A) attach each picture to its own separate e-mail
B) compress all of the pictures into one smaller file with a .zip extension
C) send her aunt the pictures through the Post Office; e-mail is not made for sending pictures
D) learn how to make a Web site and post her pictures there
A) attach each picture to its own separate e-mail
B) compress all of the pictures into one smaller file with a .zip extension
C) send her aunt the pictures through the Post Office; e-mail is not made for sending pictures
D) learn how to make a Web site and post her pictures there

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
63
Describe two types of e-mail systems commonly used.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
64
____________________ systems were originally designed for sending short, text-only messages.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
65
A(n) ____________________ is a digital document that can be transmitted from one computer to another.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
66
Case-Based Critical Thinking Questions Case 9-1 Tara has just gotten her first computer connected to the Internet. She is very excited to start e-mailing her friends and family. In order to start e-mailing, Tara first needs to decide what kind of e-mail system she wants to use. She travels a lot without her computer and would like to be able to check her e-mail on the road. Based on these criteria, Tara should use ____.
A) a local e-mail system because it allows you to check your mail from any computer with an Internet connection
B) a local e-mail system because it offers the most versatility
C) a Web-based e-mail system because it allows you to check your mail from any computer with an Internet connection
D) there are no e-mail systems that allow you to check your mail from a computer that you do not own
A) a local e-mail system because it allows you to check your mail from any computer with an Internet connection
B) a local e-mail system because it offers the most versatility
C) a Web-based e-mail system because it allows you to check your mail from any computer with an Internet connection
D) there are no e-mail systems that allow you to check your mail from a computer that you do not own

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
67
____________________ can also be used for phishing scams.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
68
Compressed files usually have a(n) ____________________ file extension.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
69
The steps for saving a(n) email ____________________ depend on the e-mail client you're using.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
70
____________________ throws away some of the original data during the compression process.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
71
Describe three of the six steps you can take to avoid spam as presented in this chapter.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
72
The ____________________ is a folder on your PC's hard disk that temporarily stores outgoing e-mail messages.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
73
Clicking a button labeled ____________________ connects you to the mail server.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
74
Case-Based Critical Thinking Questions Case 9-1 Tara has just gotten her first computer connected to the Internet. She is very excited to start e-mailing her friends and family. Tara has obtained an e-mail address and is ready to begin sending messages to her family and friends. Her Aunt Jane has just sent her the very first e-mail and she is excited and wants to forward it to her mom. The easiest way for her to forward her message is to ____.
A) simply hit the Forward button and automatically the message will be opened for her to enter her mom's e-mail address
B) just call her; e-mail takes too long
C) open up a new blank e-mail, enter her aunt's e-mail address, and enter text in the subject line
D) copy and paste her e-mail into a blank e-mail
A) simply hit the Forward button and automatically the message will be opened for her to enter her mom's e-mail address
B) just call her; e-mail takes too long
C) open up a new blank e-mail, enter her aunt's e-mail address, and enter text in the subject line
D) copy and paste her e-mail into a blank e-mail

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
75
One way to reduce spam is to use a(n) ____________________ e-mail address.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck








