Deck 5: Data Security
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
Match between columns
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/71
العب
ملء الشاشة (f)
Deck 5: Data Security
1
 Crackers , like the kind shown in the accompanying figure, are messages containing information about the user sent from a Web server to a browser and stored on the user's hard drive.
Crackers , like the kind shown in the accompanying figure, are messages containing information about the user sent from a Web server to a browser and stored on the user's hard drive.False
2
A(n) differential backup makes a backup of the files that were added or changed since the last backup.
False
3
Cyberterrorism uses viruses and worms to destroy data and disrupt computer-related operations such as power grids and telecommunication systems.
True
4
A recovery disk contains a complete copy of your computer's hard drive, including your data files and software you installed.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
5
Spam is email generated by marketing firms using e-mail addresses from mailing lists, membership applications, and Web sites.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
6
In Safe Mode, you can use the Control Panel to uninstall recently added programs or hardware.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
7
A Trojan is designed to replicate itself and spread to other computers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
8
A security suite might include detecting intrusions into your wireless network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
9
A Remote Access Trojan allows hackers to transmit files to victims' computers, search for data, run programs, and use a victim's computer as a relay station for breaking into other computers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
10
If a pop-up ad for a security suite opens on your computer, you should click on it to install the software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
11
A person who controls many computers infested with intelligent agents is called a(n) botmaster .

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
12
A(n) password usually can be entered using a numeric keypad.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
13
One advantage of using a network server for backup is that you do not need to be connected to the network server in order to backup or retrieve your files.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
14
Hackers can spread worms over file-sharing networks and instant messaging links.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
15
Even a brief interruption in power can force your computer to lose all data in ROM.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
16
A virus spreads by itself from one computer to another.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
17
Software failure can be caused by a(n) worm , which is a flaw in the program code or design.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
18
Operator error refers to a mistake made by a computer user or programmer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
19
Spyware gathers personal information, without the victim's knowledge.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
20
Security experts use the term mixed threat to describe malware that combines more than one type of malicious program.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
21
During startup, if your computer's screen remains blank or an error message appears, you may have a ____.
A) network problem
B) bug
C) software problem
D) hardware problem
A) network problem
B) bug
C) software problem
D) hardware problem

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
22
____ spikes can damage sensitive computer parts.
A) Risk
B) RAT
C) Voltage
D) WPA2
A) Risk
B) RAT
C) Voltage
D) WPA2

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
23
All of the following are other terms for user IDs EXCEPT ____.
A) username
B) password
C) online nickname
D) screen name
A) username
B) password
C) online nickname
D) screen name

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
24
 The accompanying figure shows an example of a ____.
The accompanying figure shows an example of a ____.A) UPS
B) surge strip
C) ventilation system
D) boot disk

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
25
Black hats and crackers are ____.
A) types of viruses
B) people who LANjack
C) virus protection software programs
D) names for people who create malware
A) types of viruses
B) people who LANjack
C) virus protection software programs
D) names for people who create malware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
26
A ____ is a self-copying program that spreads by itself from one computer to another.
A) worm
B) bug
C) virus
D) Trojan horse
A) worm
B) bug
C) virus
D) Trojan horse

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
27
A key characteristic of a(n) ____ is the ability to lurk in a computer for days or months, quietly copying itself.
A) worm
B) bug
C) virus
D) Trojan horse
A) worm
B) bug
C) virus
D) Trojan horse

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
28
The objective of ____ management is to help reduce downtime, and maintain the best working conditions.
A) network
B) risk
C) security
D) threat
A) network
B) risk
C) security
D) threat

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
29
 The item in the accompanying figure is used to protect your computer from ____.
The item in the accompanying figure is used to protect your computer from ____.A) viruses
B) hackers
C) power problems
D) thieves

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
30
A(n) ____ is a computer that carries out instructions without the knowledge of the computer owner.
A) zombie
B) bot
C) botmaster
D) RAT
A) zombie
B) bot
C) botmaster
D) RAT

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
31
All of the following are good tips for creating secure passwords EXCEPT ____.
A) use a password of at least eight characters
B) use uppercase and lowercase letters
C) do not use public information, such as your phone number
D) use a common word, but spell it backwards
A) use a password of at least eight characters
B) use uppercase and lowercase letters
C) do not use public information, such as your phone number
D) use a common word, but spell it backwards

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
32
A keylogger is a(n) ____.
A) password generation program
B) program that secretly records keystrokes and sends the information to a hacker
C) encryption method
D) type of worm
A) password generation program
B) program that secretly records keystrokes and sends the information to a hacker
C) encryption method
D) type of worm

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
33
A ____ is a program that seems to perform one function while actually doing something else.
A) worm
B) bug
C) virus
D) Trojan horse
A) worm
B) bug
C) virus
D) Trojan horse

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
34
STOP is ____.
A) a plate with a unique ID number
B) a type of encryption
C) an anti-cyberterrorism group
D) a virus protection software program
A) a plate with a unique ID number
B) a type of encryption
C) an anti-cyberterrorism group
D) a virus protection software program

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
35
If you encounter the blue screen of death, ____.
A) the computer no longer can accept commands
B) the operating system has a critical error
C) you might need to contact a technical support person
D) All of the above.
A) the computer no longer can accept commands
B) the operating system has a critical error
C) you might need to contact a technical support person
D) All of the above.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
36
____ are rules that limit access to directories and files.
A) Encryption protocols
B) Passwords
C) User rights
D) Authentication protocols
A) Encryption protocols
B) Passwords
C) User rights
D) Authentication protocols

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
37
____ viruses infect the system files your computer uses every time it powers up.
A) Logic
B) Payload
C) Boot sector
D) Black hat
A) Logic
B) Payload
C) Boot sector
D) Black hat

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
38
A(n) ____ is software that can automate a task or autonomously execute a task when commanded to do so.
A) zombie
B) intelligent agent
C) botmaster
D) RAT
A) zombie
B) intelligent agent
C) botmaster
D) RAT

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
39
A power ____ is a complete loss of power to the computer system.
A) failure
B) spike
C) surge
D) outage
A) failure
B) spike
C) surge
D) outage

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
40
Viruses that deliver their payloads in response to a system event are referred to as ____ bombs.
A) logic
B) time
C) boot sector
D) black hat
A) logic
B) time
C) boot sector
D) black hat

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
41
A good ____ can be used to scan the Web to assemble data for search engines.
A) zombie
B) spyware program
C) bot
D) RAT
A) zombie
B) spyware program
C) bot
D) RAT

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
42
____ is the practice of intercepting signals with a Wi-Fi enabled notebook.
A) LANjacking
B) War driving
C) Keylogging
D) Both A and B.
A) LANjacking
B) War driving
C) Keylogging
D) Both A and B.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
43
Kyle is training a new employee named Mira on how to set up measures to protect the computers and systems in their company. Kyle tells his co-worker Mira that ____ is the most secure password for her to choose.
A) Mira1980
B) drowssapMira
C) 9785550101
D) Fl0wErch1ld
A) Mira1980
B) drowssapMira
C) 9785550101
D) Fl0wErch1ld

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
44
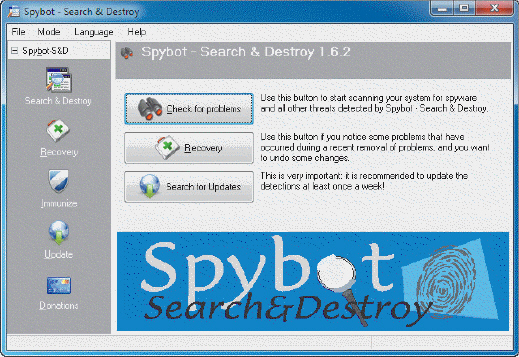 The application in the accompanying figure is an example of a program that protects against ____.
The application in the accompanying figure is an example of a program that protects against ____.A) spyware
B) viruses
C) phishing
D) pharming

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
45
Kyle is training a new employee named Mira on how to set up measures to protect the computers and systems in their company. Kyle tells his co-worker Mira that which of the following is NOT true about cookies?
A) Clicking a banner ad can create a cookie that tracks your activities.
B) To avoid risks associated with cookies, you should block them all.
C) Privacy advocates worry that shopper profiles can be sold and used for unauthorized purposes.
D) Several companies offer an opt-out cookie option.
A) Clicking a banner ad can create a cookie that tracks your activities.
B) To avoid risks associated with cookies, you should block them all.
C) Privacy advocates worry that shopper profiles can be sold and used for unauthorized purposes.
D) Several companies offer an opt-out cookie option.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
46
Jordanna recently lost a lot of data when a virus attacked her computer system. She is coming up with a backup plan to minimize future data loss. Jordanna knows that a ____ is a bootable disk that contains a complete copy of your computer's hard drive as it existed when shipped from the manufacturer.
A) boot disk
B) recovery CD
C) restore point
D) backup disk
A) boot disk
B) recovery CD
C) restore point
D) backup disk

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
47
____ is an email or IM-based scam designed to persuade you to reveal confidential information.
A) Sniffing
B) Spamming
C) Pharming
D) Phishing
A) Sniffing
B) Spamming
C) Pharming
D) Phishing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
48
 The application shown in the accompanying figure is an example of a(n) ____.
The application shown in the accompanying figure is an example of a(n) ____.A) firewall
B) Trojan horse
C) encryption program
D) security suite

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
49
Internet service providers use e-mail ____ techniques to verify that e-mail messages originate from the Internet domain from which they claim to have been sent.
A) firewall
B) authentication
C) concatenation
D) recovery
A) firewall
B) authentication
C) concatenation
D) recovery

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
50
A(n) ____ is software or hardware designed to filter out suspicious data attempting to enter or leave a computer.
A) firewall
B) security suite
C) antivirus program
D) antispyware program
A) firewall
B) security suite
C) antivirus program
D) antispyware program

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
51
____ can encrypt data based on the user's password and implements message integrity checking.
A) WEP
B) WPA
C) Security Suites
D) All of the above.
A) WEP
B) WPA
C) Security Suites
D) All of the above.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
52
A ____ attack is when hackers intercept information sent out over networks.
A) phishing
B) pharming
C) sniffing
D) spamming
A) phishing
B) pharming
C) sniffing
D) spamming

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
53
Kyle is training a new employee named Mira on how to set up measures to protect the computers and systems in their company. Kyle tells his co-worker Mira that to avoid malware, she should avoid all of the following EXCEPT ____.
A) clicking pop-up ads
B) getting software from unknown sources
C) hiding file extensions
D) opening email attachments
A) clicking pop-up ads
B) getting software from unknown sources
C) hiding file extensions
D) opening email attachments

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
54
The information that antivirus software uses to identify and remove malware is referred to as a virus ____.
A) flag
B) signature
C) definition
D) scan
A) flag
B) signature
C) definition
D) scan

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
55
Port scanning software can examine more than ____ computers per minute.
A) 300
B) 3000
C) 30,000
D) 300,000
A) 300
B) 3000
C) 30,000
D) 300,000

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
56
In Safe Mode, you can use all of the following EXCEPT ____.
A) mouse
B) printer
C) screen
D) keyboard
A) mouse
B) printer
C) screen
D) keyboard

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
57
A ____ is the basis for encrypting and decrypting the data transmitted between wireless devices.
A) wireless network key
B) password
C) PIN
D) port key
A) wireless network key
B) password
C) PIN
D) port key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
58
Jordanna recently lost a lot of data when a virus attacked her computer system. She is coming up with a backup plan to minimize future data loss. Jordanna uses her Windows installation CD as a ____, because it contains the operating system files needed to boot her computer without accessing the hard drive.
A) boot disk
B) recovery CD
C) restore point
D) backup disk
A) boot disk
B) recovery CD
C) restore point
D) backup disk

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
59
A virus ____ is a section of program code that can be used to identify a known malicious program.
A) flag
B) signature
C) definition
D) scan
A) flag
B) signature
C) definition
D) scan

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
60
A(n) ____ contains your computer settings and is used if you experience a hard drive problem.
A) boot disk
B) restore point
C) differential backup
D) incremental backup
A) boot disk
B) restore point
C) differential backup
D) incremental backup

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
61
A(n) ____________________ strip is an appliance designed to protect electrical devices from power problems but that does not contain a battery to keep the computer running.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
62
A(n) ____________________ spreads when a person distributes an infected file.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
63
A(n) ____________________ probe is the use of automated software to locate computers that are vulnerable to unauthorized access.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
64
 Technology like the kind shown in the accompanying figure is an example of a ____________________ identification system.
Technology like the kind shown in the accompanying figure is an example of a ____________________ identification system.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
65
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
66
____________________ management is the process of identifying potential threats, avoiding as many threats as possible, and developing steps to fix whatever went wrong.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
67
What are five tips for preventing computer theft?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
68
What is malware? List and describe four things that malware can do to your computer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
69
One of the biggest security threats to your computer is the result of malicious code, called ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
70
An email with a dire warning about a new virus is usually a virus ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck
71
Provide 10 tips for keeping your computer system in good working condition.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 71 في هذه المجموعة.
فتح الحزمة
k this deck








