Deck 31: Security, Privacy, and Ethics Online
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
Match between columns

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/41
العب
ملء الشاشة (f)
Deck 31: Security, Privacy, and Ethics Online
1
Phishing is a way hackers can trick e-mail users into sharing personal information. ____________________
True
2
A site license is needed when you purchase software for your home computer.
False
3
A cookie is an important file stored on your desktop that collects keystroke information.
False
4
Two-step verification requires more than just a password to authenticate your identity on a Web site.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
5
Keylogging is a way to block content being passed through the Internet. _______________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
6
A ____ is a malicious program that records your keystrokes to keep track of information such as credit card and account numbers.
A) keylogger
B) hijacker
C) spyware
D) sniffer
A) keylogger
B) hijacker
C) spyware
D) sniffer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
7
Public domain software provides remote access to software applications on the Internet. ____________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
8
A time bomb virus replicates itself and consumes the computer's resources, resulting in a computer slowdown.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
9
If a network is small, a(n) hardware firewall is sufficient. _______________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
10
Identity theft is an example of unethical behavior.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
11
A strong password contains all of the following EXCEPT: ____.
A) personal information, such as a birth date
B) at least eight characters
C) at least one special character, such as @ or *
D) letters and numbers
A) personal information, such as a birth date
B) at least eight characters
C) at least one special character, such as @ or *
D) letters and numbers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
12
An End User License Agreement is a contract between you and your Internet service provider.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
13
Computer hacking involves invading someone else's computer without his or her permission. _______________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
14
A virus is a program written by a hacker to corrupt data on a computer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
15
Which of the following is NOT true regarding computer hacking?
A) The FBI has a cybercrime branch.
B) Hackers are usually computer novices.
C) Hackers steal, change, or damage data.
D) Hacking causes millions of dollars of damage each year.
A) The FBI has a cybercrime branch.
B) Hackers are usually computer novices.
C) Hackers steal, change, or damage data.
D) Hacking causes millions of dollars of damage each year.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
16
A software firewall is more secure and easier to monitor for large networks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
17
SSL technology is used to wipe data from your computer so you can reformat the hard drive.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
18
An ergonomic workstation requires a wireless connection.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
19
Which of the following is NOT a guideline for using network protection?
A) Reset any default passwords on your wireless router.
B) Enable encryption software.
C) Create strong passwords.
D) Keep your network running at all times.
A) Reset any default passwords on your wireless router.
B) Enable encryption software.
C) Create strong passwords.
D) Keep your network running at all times.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
20
In the workplace, turning on _____ controls who can use the Internet and when.
A) spyware
B) malware
C) filtering
D) keylogging
A) spyware
B) malware
C) filtering
D) keylogging

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
21
Abby is a human resource director. She is preparing a presentation on ergonomics and responsible computer use for an upcoming employee meeting. The best position for a monitor is _____.
A) directly in front of the user, with the bottom of the monitor positioned at eye level
B) to the left of the user, with the top of the monitor positioned at eye level
C) to the right of the user, with the monitor centered at eye level
D) directly in front of the user, with the top of the monitor positioned at eye level
A) directly in front of the user, with the bottom of the monitor positioned at eye level
B) to the left of the user, with the top of the monitor positioned at eye level
C) to the right of the user, with the monitor centered at eye level
D) directly in front of the user, with the top of the monitor positioned at eye level

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
22
Which of the following is NOT a type of virus?
A) worm
B) Trojan horse
C) time bomb
D) cookie
A) worm
B) Trojan horse
C) time bomb
D) cookie

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
23
Joanna is a responsible and secure computer user. Joanna wants to make sure her password is strong, so she does all of the following EXCEPT: ______.
A) uses a number she can easily remember like her birthdate
B) includes at least one letter, number, and special character
C) uses at least 8 characters
D) uses upper- and lowercase letters
A) uses a number she can easily remember like her birthdate
B) includes at least one letter, number, and special character
C) uses at least 8 characters
D) uses upper- and lowercase letters

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
24
A ____ program can take control of your browser.
A) keylogger
B) hijacker
C) spyware
D) sniffer
A) keylogger
B) hijacker
C) spyware
D) sniffer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
25
A(n) ____________________ can provide a Web site owner with information about you and your preferences.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
26
_______________________ design adapts equipment and the workplace to fit the worker and helps prevent RSIs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
27
When a URL begins with https://, it indicates the Web site is _____.
A) phishing for information
B) filtered
C) secure
D) backed up
A) phishing for information
B) filtered
C) secure
D) backed up

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
28
Abby is a human resource director. She is preparing a presentation on ergonomics and responsible computer use for an upcoming employee meeting. Abby tells employees that they should do all of the following EXCEPT: ____.
A) Use keyboard trays, if possible.
B) Sit at least 20 inches away from the computer screen.
C) When they find a computer position that feels comfortable, sit in the same position for your entire computer session.
D) Be sure not to obstruct air vents on your notebook computer.
A) Use keyboard trays, if possible.
B) Sit at least 20 inches away from the computer screen.
C) When they find a computer position that feels comfortable, sit in the same position for your entire computer session.
D) Be sure not to obstruct air vents on your notebook computer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
29
_____ technology uses public key encryption.
A) Send Secure Layer
B) Safe Secure Locket
C) Sensitive Layer Locket
D) Secure Sockets Layer
A) Send Secure Layer
B) Safe Secure Locket
C) Sensitive Layer Locket
D) Secure Sockets Layer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
30
Joanna is a responsible and secure computer user. Joanna knows that all of the following are true about securing data EXCEPT: ____.
A) Companies often establish password-protected locations on hard drives.
B) It is always evident when some kind of computer crime or intrusion has occurred.
C) Unauthorized access is more likely to occur by people gaining access through a written or shared password than by people guessing your username or password.
D) You should change your password frequently.
A) Companies often establish password-protected locations on hard drives.
B) It is always evident when some kind of computer crime or intrusion has occurred.
C) Unauthorized access is more likely to occur by people gaining access through a written or shared password than by people guessing your username or password.
D) You should change your password frequently.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
31
An electronic document called a(n) ____________________ verifies the identity of a person or company and confirms that they own a public key.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
32
A virus that releases itself on a specific date is called a(n) ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
33
Reproducing and distributing music without the permission of the artist is called software ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
34
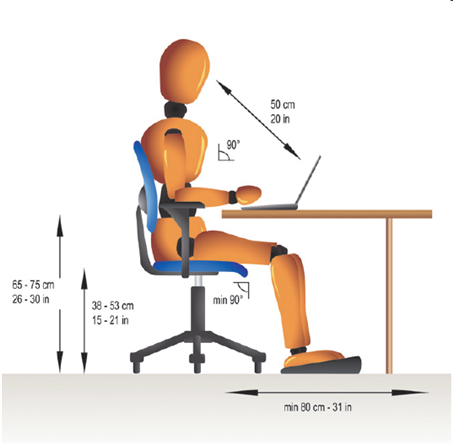
The accompanying figure shows a workstation that ____.
A) follows ergonomic design
B) is protected by biometrics
C) is likely to cause RSIs
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
35
Explain the purpose of an End User License Agreement. List three different types of software licensing available and how they work.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
36
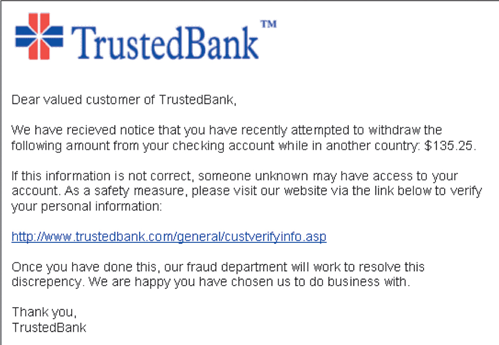
The accompanying figure shows a likely ____ scheme.
A) sniffing
B) phishing
C) hijacking
D) adware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
37
Which of the following is true about viruses?
A) Viruses are attached to files.
B) You can inadvertently run a virus program by opening an e-mail message or attachment.
C) To protect against viruses, you should use strong passwords.
D) All of the above are true.
A) Viruses are attached to files.
B) You can inadvertently run a virus program by opening an e-mail message or attachment.
C) To protect against viruses, you should use strong passwords.
D) All of the above are true.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
38
A _____ is an act intended to deceive or defraud users.
A) virus
B) sniffer
C) hoax
D) hacker
A) virus
B) sniffer
C) hoax
D) hacker

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
39
Which of the following is NOT an acceptable way to protect a system?
A) Update software once a year.
B) Install the latest security updates for your operating system.
C) Set strong passwords.
D) Install antivirus software.
A) Update software once a year.
B) Install the latest security updates for your operating system.
C) Set strong passwords.
D) Install antivirus software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
40
Which of the following is NOT true about securing data?
A) Use an alias when communicating on a blog or social network.
B) The security and privacy of personal information on the Internet is getting worse all the time.
C) Verify that you log off a computer used in a public place such as a library.
D) All of the above are true.
A) Use an alias when communicating on a blog or social network.
B) The security and privacy of personal information on the Internet is getting worse all the time.
C) Verify that you log off a computer used in a public place such as a library.
D) All of the above are true.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck
41
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 41 في هذه المجموعة.
فتح الحزمة
k this deck








