Deck 6: Intellectual Property Rights and Ethics
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/100
العب
ملء الشاشة (f)
Deck 6: Intellectual Property Rights and Ethics
1
To present someone else's work as your own is plagiarism, which is both a violation of copyright law and an unethical act.
True
2
The legal concept of limited use permits limited duplication and use of a portion of copyrighted material for certain purposes, such as criticism, commentary, news reporting, teaching, and research. _________________________
False
3
Employees who reveal wrongdoing within an organization to the public or to authorities are referred to as whistle-blowers.
True
4
Although registration is not required for copyright protection, it does offer an advantage if the need to prove ownership of a copyright ever arises, such as during a copyright-infringement lawsuit.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
5
 Research has shown that having an academic honor code like the one students are signing in the accompanying figure does not effectively reduce cheating.
Research has shown that having an academic honor code like the one students are signing in the accompanying figure does not effectively reduce cheating.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
6
The MPAA recently began pursuing civil litigation against movie pirates.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
7
An individual may be able to purchase a bootleg copy of a music CD in some countries, and the United States will then allow the item to be brought into the country to be sold.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
8
The Copyright Term Extension Act makes it illegal to circumvent antipiracy measures built into digital media and devices.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
9
Digital currency, such as Bitcoins, is considered virtual by most countries and so is not subject to that country's existing laws.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
10
Requiring proof of age at delivery is required by law in some states for certain types of shipments.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
11
Laws to increase the penalties for illegally sharing music and movies via the Internet are proposed on a regular basis.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
12
Pirated copies of movies are often created today by videotaping them with a camcorder during a prerelease screening or on the opening day of a movie.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
13
Some human resources departments view college degrees from online diploma mills or other nonaccredited organizations as another form of digital manipulation.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
14
The Family Entertainment and Copyright Act of 2005 makes it illegal to transmit or record a movie being shown at a movie theater.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
15
In some countries, bootleg copies of music CDs and movie DVDs are sold openly.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
16
The popularity of e-books has resulted in legal and ethical issues, as well as a rapid increase in piracy.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
17
Ethics with respect to the use of computers are referred to as bit ethics.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
18
Scandals related to business ethics, such as the ones surrounding executives at Apple, Cisco, and Google, involved lies, fraud, deception, and other illegal and unethical behavior.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
19
Legislation regarding ethics has been difficult to pass-but easy to keep as law once it has passed.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
20
In some countries, such as Kuwait, you can be arrested for for some types of social media posts.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
21
State and federal laws do not require Web sites selling any products and services to use online age- and identity-verification services, such as Veratad or Jumio. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
22
Although some publications allow the use of "photo illustrations," others have strict rules about digital manipulation -especially for news photojournalists. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
23

Although works created in the United States after March 1, ____ are not required to display a copyright notice to retain their copyright protection, it is wise to display this type of copyright statement on a published work (as illustrated in the accompanying figure).
A)1980
B)1989
C)1990
D)1999

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
24

If you saw a copyright mark as shown in the accompanying figure and wanted to use those materials, you would first obtain permission from ____ and pay any required fee.
A)your company
B)the copyright holder's lawyer
C)the copyright holder
D)the publisher of the material

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
25

Copyrights like the ones in the accompanying figure for works registered by an organization (or as anonymous works)last ____ years from the date of publication or 120 years from the date of creation, whichever is shorter.
A)65
B)75
C)85
D)95

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
26
A(n)____ is a form of protection available to the creator of an original artistic or literary work, such as a book, movie, software program, musical composition, or painting.
A)trademark
B)copyright
C)patent
D)intellectual ownership right
A)trademark
B)copyright
C)patent
D)intellectual ownership right

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
27
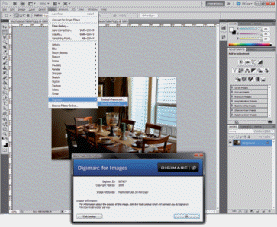
A ____ like that being used in the accompanying figure is a subtle alteration of digital content that is not noticeable when the work is viewed or played but that identifies the copyright holder.
A)digital patent
B)digital trademark
C)digital watermark
D)digital copyright

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
28
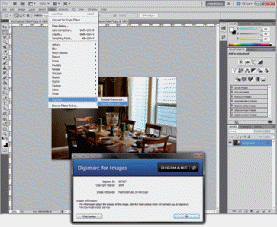
A ____ like the one used in the accompanying figure can be read with Adobe Photoshop or a proprietary reader.
A)digital patent
B)digital watermark
C)digital copyright
D)digital trademark

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
29
Following the large number of corporate scandals, personal ethics have never been quite so much in the public eye. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
30
A(n)digital trademark is a subtle alteration of digital content that is not noticeable when the work is viewed or played but that identifies the copyright holder. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
31
The No Electronic Theft Act expands computer antipiracy laws to include distribution of copyrighted material over the Internet and sets penalties for willfully infringing a copyright for purposes of commercial advantage or private financial gain. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
32
Social commerce is the use of social networking sites and other social media to promote online sales. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
33
The Children's Online Privacy Protection Act (COPPA)regulates how Web sites can collect information from minors and communicate with them. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
34
 As shown in the examples in the accompanying figure, a(n)copyright is a word, phrase, symbol, or design (or a combination of words, phrases, symbols, or designs)that identifies and distinguishes one product or service from another. _________________________
As shown in the examples in the accompanying figure, a(n)copyright is a word, phrase, symbol, or design (or a combination of words, phrases, symbols, or designs)that identifies and distinguishes one product or service from another. _________________________
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
35
To protect children from predators, many states are pushing online auction Web sites, such as MySpace and Facebook, to implement age verification systems. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
36
Ethics are fundamentally based on values , so when beliefs, laws, customs, and traditions vary among businesses, the ethics associated with those businesses will likely differ as well. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
37
When exchanging e-mail with individuals in other countries, especially business e-mail, avoid trying to add hyperlinks to your messages. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
38
Businesses are often faced with ethically questionable business decisions related to fair use , which requires them to decide how to use customer information. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
39
The eBay Web site states that it will not allow auction listings for items that promote hate, violence, or racial intolerance. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
40
A minority of businesses monitor employees to some extent. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
41
The Sarbanes-Oxley Act requires archiving a variety of electronic records and protecting the integrity of ____ financial data.
A)personal
B)public
C)national
D)corporate
A)personal
B)public
C)national
D)corporate

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
42
To catch people who are sharing movies illegally on the Internet, the MPAA uses special software that monitors file sharing networks to find copyrighted movies and then identifies the responsible individual by using the ____ of the computer being used to share the movie.
A)IP address
B)broadcast flag
C)RAM
D)serial port
A)IP address
B)broadcast flag
C)RAM
D)serial port

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
43
It is never legal to download unauthorized music from ____ sites without compensating the artist and the record label.
A)DRM
B)CRM
C)SCM
D)P2P
A)DRM
B)CRM
C)SCM
D)P2P

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
44
A teacher sharing a poem with a class, leading the class to believe the poem was his original work, is engaging in ____.
A)bad manners
B)plagiarism
C)trademark theft
D)patent infringement
A)bad manners
B)plagiarism
C)trademark theft
D)patent infringement

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
45
During one recent study of middle and high school students, about ____ of the students did not think storing notes on a mobile phone and texting during an exam constituted cheating.
A)25%
B)50%
C)70%
D)85%
A)25%
B)50%
C)70%
D)85%

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
46
Only the creator of a work or ____ can rightfully claim copyright.
A)his or her employer (if created under the scope of employment)
B)fellow employees (if created under the scope of employment)
C)family members
D)all of the above
A)his or her employer (if created under the scope of employment)
B)fellow employees (if created under the scope of employment)
C)family members
D)all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
47

One study found that cheating on tests on campuses with honor codes, like the code being signed in the accompanying figure, is typically ____ compared to campuses that do not have honor codes.
A)the same
B)one-third to one-half less
C)twice as much
D)one-third to one-half more

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
48
In addition to being annoying and a waste of time, ____ bog(s)down e-mail systems and clog(s)users' Inboxes.
A)computer worms
B)Trojan horses
C)e-mail hoaxes
D)digital manipulation
A)computer worms
B)Trojan horses
C)e-mail hoaxes
D)digital manipulation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
49
Ethical decisions need to be made whenever a business practice or product is legal or socially acceptable in one country, but not another. One example is ____.
A)copyright law
B)religion
C)human cloning
D)corporate missions
A)copyright law
B)religion
C)human cloning
D)corporate missions

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
50
____ recently agreed to pay AOL $1 billion for 800 undisclosed technology patents.
A)Microsoft
B)Cisco
C)Google
D)Verizon
A)Microsoft
B)Cisco
C)Google
D)Verizon

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
51
Presenting someone else's work as your own is referred to as ____, which is illegal and unethical.
A)duplicating
B)printing
C)plagiarism
D)copying
A)duplicating
B)printing
C)plagiarism
D)copying

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
52
A teacher can legally read a copyrighted poem for discussion in a poetry class under the legal concept of ____.
A)education use
B)fair use
C)the 2-second rule
D)global share
A)education use
B)fair use
C)the 2-second rule
D)global share

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
53
In addition to the problem of unethical ____, the use of digital cameras today virtually eliminates any concrete evidence-namely, negatives.
A)cybersquatting
B)digital counterfeiting
C)identity theft
D)digital manipulation
A)cybersquatting
B)digital counterfeiting
C)identity theft
D)digital manipulation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
54
A ____ is a policy, often for a school or business, that specifies allowable use of resources such as computers and other equipment.
A)code of ethics
B)code of conduct
C)privacy policy
D)piracy policy
A)code of ethics
B)code of conduct
C)privacy policy
D)piracy policy

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
55
The acquisition of a domain by someone other than the holder of the trademark for the purpose of harming the trademark holder or selling the domain name at an inflated price is an act referred to as ____.
A)cyberinvasion
B)cyberintrusion
C)digital invasion
D)cybersquatting
A)cyberinvasion
B)cyberintrusion
C)digital invasion
D)cybersquatting

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
56
In reaction to scandals, Congress passed the Sarbanes-Oxley Act of 2002, which includes provisions to require ____ to personally vouch for the truth and fairness of their company's disclosures.
A)CIOs
B)CEOs and CFOs
C)CEOs
D)CFOs
A)CIOs
B)CEOs and CFOs
C)CEOs
D)CFOs

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
57
In addition to being a copyright concern, ____ can be used to misquote individuals, repeat comments out of context, retouch photographs-even to create false or misleading photographs.
A)digital counterfeiting
B)identity theft
C)plagiarism
D)digital manipulation
A)digital counterfeiting
B)identity theft
C)plagiarism
D)digital manipulation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
58
____, used in conjunction with business documents, can protect a sensitive business document by controlling usage of that document, such as who can view, print, or copy it.
A)DRM software
B)Copyright statements
C)Copyright notices
D)Digital watermarks
A)DRM software
B)Copyright statements
C)Copyright notices
D)Digital watermarks

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
59
The Family Entertainment and Copyright Act makes it illegal to transmit or record a movie being shown ____.
A)at a movie theater
B)at a school
C)at a public park
D)on an airplane
A)at a movie theater
B)at a school
C)at a public park
D)on an airplane

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
60

Honor codes like that being signed in the accompanying figure help prevent ____.
A)creating plagiarized material
B)texting answers to others
C)storing notes on a smartphone
D)all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
61
The Child Internet Protection Act (CIPA)requires public ____ to use filtering software to block access to certain Web content in order to receive public funds.
A)libraries and schools
B)movie theatres
C)government agencies
D)daycare agencies
A)libraries and schools
B)movie theatres
C)government agencies
D)daycare agencies

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
62
The Children's ____ Privacy Protection Act regulates how Web sites can collect information from minors and communicate with them.
A)Online
B)Web
C)Internet
D)Electronic
A)Online
B)Web
C)Internet
D)Electronic

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
63
____________________ are the legal rights to which the creators of intellectual property-original creative works-are entitled.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
64
The Communications Decency Act makes it a criminal offense to distribute patently indecent or offensive material online and was declared ____ by the U.S. Supreme Court in 1997.
A)into law
B)a landmark case
C)unconstitutional
D)constitutional
A)into law
B)a landmark case
C)unconstitutional
D)constitutional

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
65
Case-Based Critical Thinking Questions Case 6-1 Jenna has been hired by a large corporation to present trademark concepts to its employees. If the eBay logo displays the mark T, Jenna explains, this means that the trademark is ____ with the U.S. Patent and Trademark Office (USPTO).
A)claimed and registered
B)claimed but not registered
C)not claimed and not registered
D)not claimed and registered
A)claimed and registered
B)claimed but not registered
C)not claimed and not registered
D)not claimed and registered

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
66
Case-Based Critical Thinking Questions Case 6-1 Jenna has been hired by a large corporation to present trademark concepts to its employees. Jenna explains that nonregistered service marks can use the symbol ____.
A)NS
B)SM
C)STM
D)TMS
A)NS
B)SM
C)STM
D)TMS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
67
The ____________________ extended copyright protection to nonpublished works, so, immediately after creating a work in some type of material form, the creator automatically owns the copyright of that work.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
68
The Digital ____ Copyright Act makes it illegal to circumvent antipiracy measures built into digital media and devices.
A)Millennium
B)National
C)Antipiracy
D)Theft
A)Millennium
B)National
C)Antipiracy
D)Theft

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
69
Case-Based Critical Thinking Questions Case 6-1 Jenna has been hired by a large corporation to present trademark concepts to its employees. Jenna cautions employees that trademark law also protects domain names that ____, such as Amazon.com and Lego.com.
A)match a company's trademark
B)appear similar to a company's trademark
C)match a company's copyright
D)appear similar to a company's copyright
A)match a company's trademark
B)appear similar to a company's trademark
C)match a company's copyright
D)appear similar to a company's copyright

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
70
Case-Based Critical Thinking Questions Case 6-1 Jenna has been hired by a large corporation to present trademark concepts to its employees. With regard to the duration of trademarks, Jenna explains that they last 10 years, but can be renewed as many times as desired, as long as they are being used ____.
A)inside the company
B)in commerce
C)outside the company
D)on the Web
A)inside the company
B)in commerce
C)outside the company
D)on the Web

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
71
The Digital Theft Deterrence and Copyright Damages Improvement Act of ____ amends federal copyright law to increase statutory and additional damages a court may award for copyright infringement.
A)1995
B)1999
C)2003
D)2007
A)1995
B)1999
C)2003
D)2007

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
72
If the current ____________________ holder has a legitimate reason for using that name and does not appear to be a cybersquatter, WIPO may allow the holder to continue to use that domain name.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
73
The No Electronic Theft (NET)Act expands computer antipiracy laws to include distribution of copyrighted material over the Internet and sets penalties for willfully infringing a copyright for purposes of ____.
A)commercial advantage
B)private financial gain
C)both a and b
D)neither a nor b
A)commercial advantage
B)private financial gain
C)both a and b
D)neither a nor b

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
74
A student copying and pasting information from various online documents to create her research paper without crediting the original authors is considered to be committing ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
75
____________________ are the standards of conduct that guide a business's policies, decisions, and actions.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
76
The U.S. Anticybersquatting Consumer Protection Act of 1999 amends the ____ Act of 1946 to extend the kind of protection available to the logos in the accompanying figure to domain names and makes cybersquatting illegal.
A)Lowell
B)Listner
C)Lanham
D)Layne
A)Lowell
B)Listner
C)Lanham
D)Layne

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
77
The Copyright Term Extension Act extends the duration of copyright in a work created on or after January 1, 1978 by ____ years.
A)10
B)20
C)30
D)40
A)10
B)20
C)30
D)40

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
78
Case-Based Critical Thinking Questions Case 6-1 Jenna has been hired by a large corporation to present trademark concepts to its employees. During her training session, Jenna posits that the symbol ® is reserved for ____.
A)registered trademarks
B)registered service marks
C)both a and b
D)neither a nor b
A)registered trademarks
B)registered service marks
C)both a and b
D)neither a nor b

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
79
The Copyright Act of ____ gives the owner of a copyright the exclusive right to publish, reproduce, distribute, perform, or display the work.
A)1970
B)1976
C)1982
D)1988
A)1970
B)1976
C)1982
D)1988

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck
80
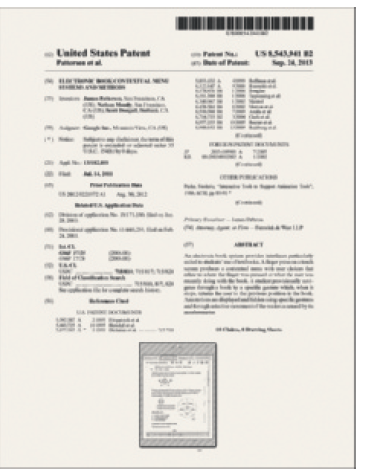 The item in the accompanying figure protects inventions by granting ____________________ rights of an invention to its inventor for a period of 20 years.
The item in the accompanying figure protects inventions by granting ____________________ rights of an invention to its inventor for a period of 20 years.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 100 في هذه المجموعة.
فتح الحزمة
k this deck








