Deck 6: Data Security
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/91
العب
ملء الشاشة (f)
Deck 6: Data Security
1
Some Web sites offer fee-based backup storage space.
True
2
A firewall is software or hardware designed to filter out suspicious packets attempting to enter or leave a computer.
True
3
Worms attach themselves to a file, reproduce, and spread to other files on the same computer.
False
4
Spam filters are not included in email clients and security suites.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
5
Viruses programmed to deliver their payloads on a certain date are called time bombs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
6
Encryption transforms a message so that its contents are hidden from unauthorized readers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
7
A voltage spike is another term for power spike.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
8
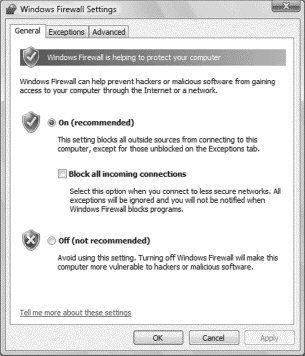 Windows Vista includes firewall software, as shown above, and can be configured from the Support Center.
Windows Vista includes firewall software, as shown above, and can be configured from the Support Center.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
9
MTBF measures the security risks of a computer system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
10
A keylogger is a program that secretly records your keystrokes.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
11
A boot disk contains a complete copy of your computer's hard disk as it existed when shipped from the manufacturer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
12
One of email's main disadvantages is spam.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
13
Developing steps to recover from an unavoidable disaster is one step in the process of risk management.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
14
Biometrics is a method of authentication used to confirm a person's identity based on some physical trait.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
15
 Publications like the one shown above help risk management professionals design and update disaster recovery plans.
Publications like the one shown above help risk management professionals design and update disaster recovery plans.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
16
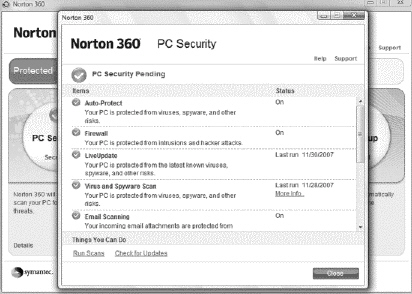 A security suite , which integrates several security modules, is shown in the figure above.
A security suite , which integrates several security modules, is shown in the figure above.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
17
 The power strip shown in the figure above is an appliance designed to protect electrical devices from power surges and voltage spikes.
The power strip shown in the figure above is an appliance designed to protect electrical devices from power surges and voltage spikes.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
18
A surge strip offers an uninterruptible power supply.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
19
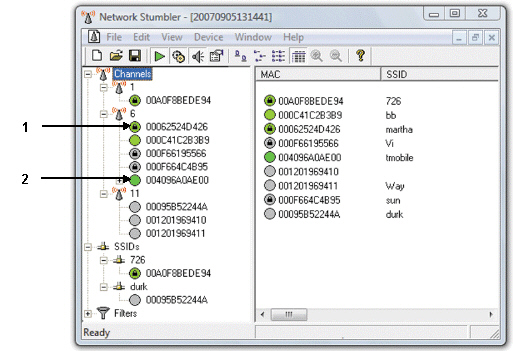 LANjackers use network-detecting and monitoring software, like the software shown in the figure above, to help locate and identify secured and unsecured networks.
LANjackers use network-detecting and monitoring software, like the software shown in the figure above, to help locate and identify secured and unsecured networks.
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
20
Power strips offer similar protection to surge strips.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
21
A ____ is a message containing information about a user sent from a Web server to a browser and stored on the user's hard drive.
A)Trojan horse
B)multi-partite
C)cookie
D)stealth
A)Trojan horse
B)multi-partite
C)cookie
D)stealth

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
22
____ involves writing specific symbols on walls, sidewalks, or lampposts to signal others they can tap into a wireless network in the area.
A)War driving
B)LANjacking
C)War chalking
D)GPS
A)War driving
B)LANjacking
C)War chalking
D)GPS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
23
Which of the following is NOT a method used in a disaster recovery plan?
A)remote offsite backup servers
B)surge protectors
C)botnets
D)UPSs
A)remote offsite backup servers
B)surge protectors
C)botnets
D)UPSs

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
24
Which of the following is NOT true about bots?
A)They cannot be designed for destructive tasks.
B)They can be spread by worms or Trojans.
C)They can perform helpful tasks.
D)They can carry out instructions without the knowledge of the PCs owner.
A)They cannot be designed for destructive tasks.
B)They can be spread by worms or Trojans.
C)They can perform helpful tasks.
D)They can carry out instructions without the knowledge of the PCs owner.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
25
A ____ virus infects the system files on your computer causing widespread damage to your hard drive.
A)blended threat
B)boot sector
C)RAT
D)Trojan horse
A)blended threat
B)boot sector
C)RAT
D)Trojan horse

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
26
MTBF is a rating that attempts to measure the time before a(n)____ failure occurs.
A)hardware
B)software
C)power
D)operator
A)hardware
B)software
C)power
D)operator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
27
A ____ is one term for someone who creates and unleashes malware.
A)cracker
B)Trojan horse
C)worm
D)bot
A)cracker
B)Trojan horse
C)worm
D)bot

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
28
A security suite typically includes ____.
A)antivirus modules
B)firewalls
C)antispyware modules
D)all of the above
A)antivirus modules
B)firewalls
C)antispyware modules
D)all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
29
A power ____ can be caused by a malfunction in the power distribution network.
A)supply
B)surge
C)voltage
D)error
A)supply
B)surge
C)voltage
D)error

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
30
A ____ is the basis for scrambling and unscrambling the data transmission between wireless devices.
A)firewall
B)cookie
C)wireless network key
D)wireless node
A)firewall
B)cookie
C)wireless network key
D)wireless node

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
31
A(n)virus ____ is a section of program code that can be used to identify a known malicious program.
A)fingerprint
B)ID
C)signature
D)procedure
A)fingerprint
B)ID
C)signature
D)procedure

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
32
Which of the following is a common source of viruses?
A)Removable storage media
B)Email attachments
C)Downloaded software
D)All of the above
A)Removable storage media
B)Email attachments
C)Downloaded software
D)All of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
33
____ is the term used to describe terrorist acts committed via the Internet.
A)Hacking
B)Cyberterrorism
C)Operator error
D)LANjacking
A)Hacking
B)Cyberterrorism
C)Operator error
D)LANjacking

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
34
 The device shown in the figure above is a locking device .
The device shown in the figure above is a locking device .
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
35
Which of the following is NOT one of the steps a worm makes when infecting a computer system?
A)Slows processing time.
B)Enters the host computer through e-mail.
C)Destroys storage space.
D)Copies itself and attempts to travel to other hosts.
A)Slows processing time.
B)Enters the host computer through e-mail.
C)Destroys storage space.
D)Copies itself and attempts to travel to other hosts.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
36
Much better security is offered by ____.
A)WPA2
B)WEP
C)WPA
D)GPS
A)WPA2
B)WEP
C)WPA
D)GPS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
37
A ____ is a program that seems to perform one function, while actually doing something else.
A)malicious program
B)worm
C)macro
D)Trojan horse
A)malicious program
B)worm
C)macro
D)Trojan horse

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
38
A virus ____ is a file that your antivirus software uses to identify and remove malware.
A)signature
B)definition
C)checksum
D)patch
A)signature
B)definition
C)checksum
D)patch

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
39
 The device shown in the figure above is a security plate .
The device shown in the figure above is a security plate .
فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
40
A ____ usually arrives as an email message containing warnings of a new virus.
A)botmaster
B)virus hoax
C)keylogger
D)zombie
A)botmaster
B)virus hoax
C)keylogger
D)zombie

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
41
When referring to war driving and war chalking, war stands for ____.
A)wireless area resources
B)wireless access revolution
C)wired access resources
D)wireless account resources
A)wireless area resources
B)wireless access revolution
C)wired access resources
D)wireless account resources

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
42
 Which of the following statements it NOT true about the figure shown above?
Which of the following statements it NOT true about the figure shown above?A)It prevents unauthorized data access.
B)It is affixed to the underside of the computer or to a desk.
C)It is used to prevent theft.
D)It anchors your computer to your desk.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
43
 The device shown in the figure above provides the best protection against power problems. What is the name for this device?
The device shown in the figure above provides the best protection against power problems. What is the name for this device?A)GPS
B)UBS
C)GIS
D)UPS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
44
UPS stands for ____.
A)uninterruptible power source
B)uninterruptible power supply
C)uniform power source
D)uniform power supply
A)uninterruptible power source
B)uninterruptible power supply
C)uniform power source
D)uniform power supply

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
45
You do not have to click anything to receive a third-party cookie generated by a ____.
A)clear GIF
B)Flash cookie
C)Web bug
D)A or C
A)clear GIF
B)Flash cookie
C)Web bug
D)A or C

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
46
Backup software is a set of ____ programs designed to back up and restore files.
A)security
B)utility
C)defrag
D)technique
A)security
B)utility
C)defrag
D)technique

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
47
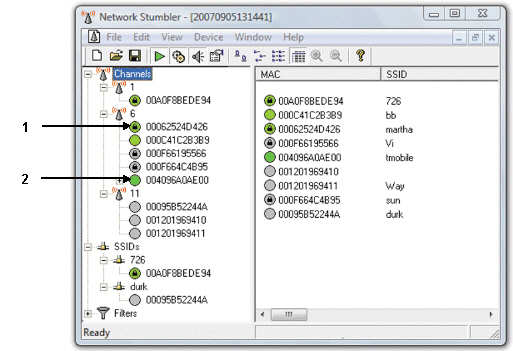 Item 2 in the figure above indicates ____.
Item 2 in the figure above indicates ____.A)an encrypted network
B)an unencrypted network
C)a closed network
D)None of the above.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
48
When storing your backup files on a LAN, consider each of the following EXCEPT ____:
A)The size of your backup files.
B)Password-protected folders to prevent unauthorized access.
C)That the server is backed up regularly.
D)You should consider all of the above.
A)The size of your backup files.
B)Password-protected folders to prevent unauthorized access.
C)That the server is backed up regularly.
D)You should consider all of the above.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
49
A(n)____ backup contains a copy of every program, data, and system file on a computer.
A)restoration
B)bootstrap
C)differential
D)full
A)restoration
B)bootstrap
C)differential
D)full

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
50
The Windows ____ is a file that stores configuration information about the devices and software installed on a computer system.
A)root directory
B)backup
C)Registry
D)Explorer
A)root directory
B)backup
C)Registry
D)Explorer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
51
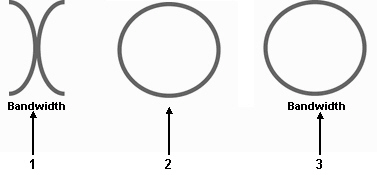 Item ____ in the figure above indicates an open (available)node.
Item ____ in the figure above indicates an open (available)node.A)1
B)2
C)3
D)None of the symbols indicate an open node.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
52
Which of the following is NOT typically included with a data center?
A)fireproof construction
B)power generators
C)static floor coverings
D)sprinkler systems
A)fireproof construction
B)power generators
C)static floor coverings
D)sprinkler systems

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
53
 The device shown in the figure above is a ____ device.
The device shown in the figure above is a ____ device.A)restore
B)registry
C)backup
D)Web

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
54
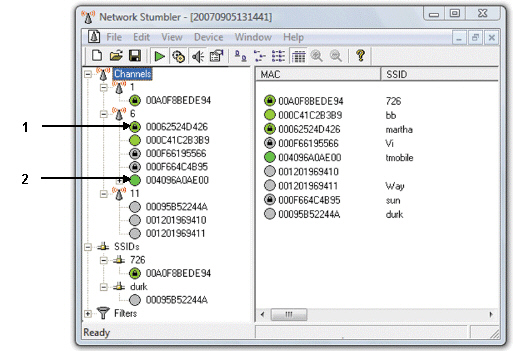 Item 1 in the figure above indicates ____.
Item 1 in the figure above indicates ____.A)an unencrypted network
B)an open network
C)an encrypted network
D)a low strength signal

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
55
Which of the following is NOT an objective of risk management?
A)help reduce downtime
B)increase downtime
C)promote business continuity
D)maintain good quality service
A)help reduce downtime
B)increase downtime
C)promote business continuity
D)maintain good quality service

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
56
 Which of the following statements it NOT true about the figure shown above?
Which of the following statements it NOT true about the figure shown above?A)It is a specially designed lock.
B)It can be attached to a cable.
C)It is used to prevent theft.
D)It cannot be fastened to a desk.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
57
A ____ contains your computer's settings.
A)restore point
B)recovery CD
C)Web-based backup system
D)Flash cookie
A)restore point
B)recovery CD
C)Web-based backup system
D)Flash cookie

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
58
Which of the following is NOT an appliance designed to protect electrical devices from power surges and voltage spikes?
A)surge suppressor
B)power strip
C)surge strip
D)surge protector
A)surge suppressor
B)power strip
C)surge strip
D)surge protector

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
59
A facility that is designed to house and protect a computer system and its data is called a(n)____ center.
A)data
B)information
C)recovery
D)disaster
A)data
B)information
C)recovery
D)disaster

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
60
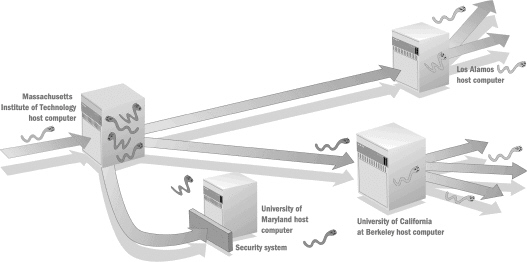 In the figure above, the worm enters the original host and other unprotected hosts using ____.
In the figure above, the worm enters the original host and other unprotected hosts using ____.A)infected files
B)a backdoor
C)e-mail
D)a packet

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
61
____________________ protocol refers to any method that confirms a person's identity when using a computer system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
62
Human error, also called ____________________ error, includes entering inaccurate data or not following procedures.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
63
A(n)____________________ attack helps hackers guess your password by stepping through a list of thousands of the most common passwords.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
64
Malware is created and unleashed by ____.
A)black hats
B)cybercriminals
C)crackers
D)all of the above
A)black hats
B)cybercriminals
C)crackers
D)all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
65
____________________ authentication verifies identity using two independent elements of confirmation.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
66
A(n)____ verifies a user ID and guarantees that you are the person you claim to be.
A)password
B)protocol
C)ID
D)username
A)password
B)protocol
C)ID
D)username

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
67
When your personal data is used illegally, it is called ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
68
A power ____________________ is a complete loss of power to a computer system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
69
A local shared object is also called a(n)____.
A)Flash cookie
B)ad-serving cookie
C)Web bug
D)clear GIF
A)Flash cookie
B)ad-serving cookie
C)Web bug
D)clear GIF

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
70
A RAT is a type of ____.
A)worm
B)Trojan
C)bot
D)zombie
A)worm
B)Trojan
C)bot
D)zombie

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
71
Hand-geometry scanners and voice recognition are examples of ____________________ devices.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
72
Antivirus software is available for ____.
A)USB flash drives
B)handheld computers
C)personal computers
D)all of the above
A)USB flash drives
B)handheld computers
C)personal computers
D)all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
73
____ scrambles the data transmitted between wireless devices and then unscrambles the data only on devices that have a valid key.
A)LANjacking
B)Wireless encryption
C)War chalking
D)War driving
A)LANjacking
B)Wireless encryption
C)War chalking
D)War driving

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
74
A(n)____________________ is your unique identifier on a computer or Web page.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
75
A ____ is a person who controls many bot-infested computers.
A)zombie
B)bot
C)botmaster
D)botnet
A)zombie
B)bot
C)botmaster
D)botnet

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
76
Authentication protocols that use more than one means of identification are ____ secure than others.
A)less
B)more
C)equally as
D)not as
A)less
B)more
C)equally as
D)not as

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
77
A ____ is a computer under the control of a bad bot.
A)botmaster
B)botnet
C)clone
D)zombie
A)botmaster
B)botnet
C)clone
D)zombie

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
78
____ is a type of program that secretly gathers personal information without the victim's knowledge, usually for advertising and other commercial purposes.
A)Botmaster
B)Trojan horse
C)Antivirus
D)Spyware
A)Botmaster
B)Trojan horse
C)Antivirus
D)Spyware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
79
A ____ is a set of program instructions that attaches itself to a file, reproduces itself, and spreads to other files on the same computer.
A)computer worm
B)mass-mailing worm
C)Trojan horse
D)computer virus
A)computer worm
B)mass-mailing worm
C)Trojan horse
D)computer virus

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck
80
Data security on a system that is guarded by user IDs and passwords depends on password ____.
A)protocol
B)secrecy
C)characteristics
D)rights
A)protocol
B)secrecy
C)characteristics
D)rights

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 91 في هذه المجموعة.
فتح الحزمة
k this deck








