Deck 27: Communications and Collaboration
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/46
العب
ملء الشاشة (f)
Deck 27: Communications and Collaboration
1
The RSS format is widely used to share the contents of blogs.
True
2
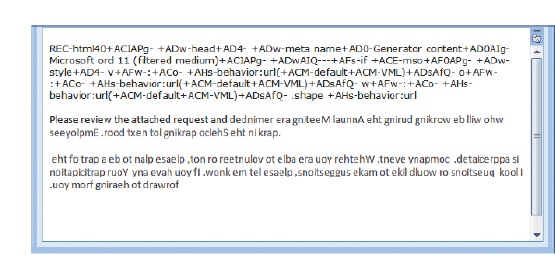 Which of the following is NOT true about the figure above?
Which of the following is NOT true about the figure above?A) The e-mail message is garbled.
B) The sender may not receive a message that the e-mail was not delivered properly.
C) Its file type does not enable formatting such as fonts and colors.
D) All of the above are true.
D
3
Which of the following is NOT an example of many-to-many communication?
A) Blogs
B) Telnet
C) Wikis
D) Tagging
A) Blogs
B) Telnet
C) Wikis
D) Tagging
B
4
 The e-mail in the figure above was likely sent using ____ format.
The e-mail in the figure above was likely sent using ____ format.A) PDF
B) Plain Text
C) RTF
D) HTML

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
5
Google Docs is an example of online document sharing.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
6
An attachment is a file sent along with an e-mail message.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
7
Spam advertising is very inexpensive.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
8
Teleconferencing is generally free.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
9
Netiquette refers to good manners and proper behaviors when communicating through electronic media.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
10
Posting files on an FTP site is an example of one-to-one communication.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
11
The ____ format was originally developed to syndicate news articles electronically.
A) Really Simple Syndication
B) Rich Site Summary
C) RDF Summary
D) all of the above
A) Really Simple Syndication
B) Rich Site Summary
C) RDF Summary
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
12
You attach multiple files to the same message, but the files must be of the same type.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
13
A e-mail warning message about a virus is likely safe.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
14
All e-mail programs return delivery failure notices for e-mail that cannot be delivered.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
15
One way to protect yourself from viruses is to save an e-mail attachment to your computer before opening it.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
16
Electronic fraud is a computer crime that involves the manipulation of a computer or computer data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
17
Which of the following is NOT a good use of e-mail?
A) When communication needs to be accessed in real time.
B) When the correspondence might require a paper trail.
C) When the correspondence covers multiple points.
D) When the correspondence needs to be accessed frequently.
A) When communication needs to be accessed in real time.
B) When the correspondence might require a paper trail.
C) When the correspondence covers multiple points.
D) When the correspondence needs to be accessed frequently.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
18
Most e-mail users rate spam over too much e-mail as their biggest e-mail problem.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
19
If an e-mail is sent in HTML format and the recipient's e-mail program does not support HTML, the message is displayed in RTF format.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
20
A(n) hoax is a story that at one time could have been partially true but has grown into a mythical yarn.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
21
A(n) ____ is an attempt to deceive an audience into believing that something false is real.
A) pyramid scheme
B) phishing message
C) hoax
D) virus
A) pyramid scheme
B) phishing message
C) hoax
D) virus

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
22
A(n) ____ is an illicit business model where profits are based on the investor's ability to recruit other people.
A) pyramid scheme
B) phishing
C) hoax
D) virus
A) pyramid scheme
B) phishing
C) hoax
D) virus

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
23
____________________ is used in blogs and other informational sites to simplify the search process.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
24
Jin is preparing a report on electronic communication for his Intro to Computer class. Jin writes in his report that all of the following can cause e-mail delivery failure, EXCEPT: ____.
A) The e-mail address is mistyped
B) The e-mail attachment contains malware
C) The recipient's mailbox is full
D) A garbled message
A) The e-mail address is mistyped
B) The e-mail attachment contains malware
C) The recipient's mailbox is full
D) A garbled message

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
25
E-mail ____________________ allows you to define rules to manage incoming e-mail.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
26
____________________ is also called junk e-mail, and may include unsolicited advertisements.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
27
Which of the following is NOT true about filtering e-mail?
A) You can use filtering to sort messages into folders.
B) You can use filtering to tag messages.
C) Spam costs U.S. businesses more than $71 billion annually.
D) E-mail clients are the computers that send and receive e-mail.
A) You can use filtering to sort messages into folders.
B) You can use filtering to tag messages.
C) Spam costs U.S. businesses more than $71 billion annually.
D) E-mail clients are the computers that send and receive e-mail.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
28
Which of the following is NOT true about sending e-mail?
A) When you receive a message that was also sent to other recipients, always use Reply All to ensure everyone receives all responses.
B) Only send responses that apply to the original message.
C) Use the Cc option if someone needs to know the information in the e-mail but does not need to respond.
D) Use the Bcc option when someone's e-mail address should not appear in the delivered e-mail message.
A) When you receive a message that was also sent to other recipients, always use Reply All to ensure everyone receives all responses.
B) Only send responses that apply to the original message.
C) Use the Cc option if someone needs to know the information in the e-mail but does not need to respond.
D) Use the Bcc option when someone's e-mail address should not appear in the delivered e-mail message.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
29
____ messages appear to come from a legitimate source, and ask you to update or verify your personal information.
A) Pyramid scheme
B) Phishing
C) Hoax
D) Virus
A) Pyramid scheme
B) Phishing
C) Hoax
D) Virus

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
30
Jin is preparing a report on electronic communication for his Intro to Computer class. Jin writes in his report that ____ is the process of selecting paths in a network along which to send network traffic.
A) directing
B) routing
C) networking
D) tagging
A) directing
B) routing
C) networking
D) tagging

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
31
Which of the following is NOT true about computer security?
A) The best way to protect data is to control access to it.
B) A firewall is software that protects your system from viruses.
C) Change passwords frequently.
D) Regularly back up data and store it offsite.
A) The best way to protect data is to control access to it.
B) A firewall is software that protects your system from viruses.
C) Change passwords frequently.
D) Regularly back up data and store it offsite.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
32
Which of the following is NOT true about professional and effective communications?
A) A customer who needs immediate assistance should receive a reply within 24 hours.
B) Instant messaging should be short and to the point.
C) Ideally, the recipient should not have to scroll past one page to read an e-mail message.
D) Include one subject per e-mail message.
A) A customer who needs immediate assistance should receive a reply within 24 hours.
B) Instant messaging should be short and to the point.
C) Ideally, the recipient should not have to scroll past one page to read an e-mail message.
D) Include one subject per e-mail message.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
33
____________________ e-mails are personal information scams.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
34
____________________ uses a telecommunication system to serve groups, permitting the live exchange and sharing of information between two or more people.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
35
Meredith is researching how to manage her e-mail messages to keep herself organized and protect her computer data. Meredith wants to send all messages from her soccer coach to a specific folder. She sets up a(n) ____.
A) filter
B) protocol
C) route
D) firewall
A) filter
B) protocol
C) route
D) firewall

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
36
Which of the following is NOT a sign that an e-mail or chain letter contains a virus?
A) The e-mail message contains all capital letters or dozens of exclamation points.
B) The message comes with an attachment, and you don't know who it is from.
C) The message encourages you to keep the information confidential.
D) All of the above are true.
A) The e-mail message contains all capital letters or dozens of exclamation points.
B) The message comes with an attachment, and you don't know who it is from.
C) The message encourages you to keep the information confidential.
D) All of the above are true.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
37
Which of the following is NOT true about e-mail options?
A) Most e-mail services have a limit on the size of a message.
B) Most e-mail services enable .exe files to go through filtering.
C) When creating an e-mail, you can create a link to a file instead of including it as an attachment.
D) Some e-mail readers cannot display graphics or animations.
A) Most e-mail services have a limit on the size of a message.
B) Most e-mail services enable .exe files to go through filtering.
C) When creating an e-mail, you can create a link to a file instead of including it as an attachment.
D) Some e-mail readers cannot display graphics or animations.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
38
Which of the following is NOT true about viruses?
A) Viruses are written by hackers.
B) Viruses can be attached to a program file or an e-mail message.
C) Viruses spread from one file to another when the program is executed.
D) Viruses always cause major damage to a computer's data.
A) Viruses are written by hackers.
B) Viruses can be attached to a program file or an e-mail message.
C) Viruses spread from one file to another when the program is executed.
D) Viruses always cause major damage to a computer's data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
39
Which of the following is NOT true about spam?
A) Do not publish your e-mail address online.
B) Verify that a Web site does not permit sharing your e-mail address before providing it.
C) You should reply to a junk e-mail message so you can request that they not send you any additional messages.
D) Microsoft Outlook includes a junk e-mail filter.
A) Do not publish your e-mail address online.
B) Verify that a Web site does not permit sharing your e-mail address before providing it.
C) You should reply to a junk e-mail message so you can request that they not send you any additional messages.
D) Microsoft Outlook includes a junk e-mail filter.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
40
Meredith is researching how to manage her e-mail messages to keep herself organized and protect her computer data. Meredith does all of the following to prevent threats to her computer, EXCEPT: ____.
A) Avoid posting her e-mail address in a public place
B) Make sure her e-mail program does not include a feature that encrypts messages so the messages cannot be scanned
C) Scan all incoming e-mail messages and attachments
D) Backs up and archives correspondence regularly
A) Avoid posting her e-mail address in a public place
B) Make sure her e-mail program does not include a feature that encrypts messages so the messages cannot be scanned
C) Scan all incoming e-mail messages and attachments
D) Backs up and archives correspondence regularly

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
41
List four guidelines you can use for safe electronic communication.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
42
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
43
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
44
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
45
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
46
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck








