Deck 25: Networks Fundamentals
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/46
العب
ملء الشاشة (f)
Deck 25: Networks Fundamentals
1
A(n) modem converts analog signals to digital and vice versa.
True
2
Intranets and extranets use and support Web technologies, such as hyperlinks and HTML.
True
3
Communication channels can include telephone systems, fiber optics, satellites, microwaves, or any combination of these.
True
4
Which of the following is NOT an example of malicious code?
A) Trojan horses
B) Worms
C) Hackers
D) Spyware
A) Trojan horses
B) Worms
C) Hackers
D) Spyware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
5
A(n) ____ is a software program such as Internet Explorer.
A) client
B) server
C) operating system
D) router
A) client
B) server
C) operating system
D) router

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
6
With software sharing companies purchase a site license for users.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
7
Digital, mobile, and standard telephones are supported through the PSTN network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
8
Sniffer software is used to located hot spots.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
9
Network connections can be in the same city or in different locations all over the world.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
10
Different from a desktop computer, a network server doesn't require an operating system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
11
WAN stands for Wireless Access Network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
12
PSTN stands for Public Switched ____ Network.
A) Telephone
B) Telecommunications
C) Technology
D) Triangular
A) Telephone
B) Telecommunications
C) Technology
D) Triangular

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
13
A telephone network is similar in makeup to a computer network, though it transfers voice data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
14
The term client/server network describes a network design model.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
15
Networks can be categorized by type as LANs or WANs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
16
Information sent over telephone lines is transmitted in the form of binary code.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
17
Which of the following is NOT true about network risks?
A) Server malfunctions or failures mean users temporarily lose access to printers, drives, and information.
B) A standalone system is vulnerable to the same risks as networked computers.
C) Hackers can delete data.
D) Some people threaten networks and data by creating viruses and other types of malicious software..
A) Server malfunctions or failures mean users temporarily lose access to printers, drives, and information.
B) A standalone system is vulnerable to the same risks as networked computers.
C) Hackers can delete data.
D) Some people threaten networks and data by creating viruses and other types of malicious software..

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
18
The cost for e-mail depends on the size of the message and the distance the message has to travel.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
19
To communicate on a WLAN, the computer and other devices that access the network must contain a modem.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
20
Which of the following is true about the benefits of networking?
A) People share information through special group projects, databases, blogs, FTP, and more.
B) One hardware device connected to a network can serve the needs of many users.
C) Software sharing saves money.
D) All of the above are true.
A) People share information through special group projects, databases, blogs, FTP, and more.
B) One hardware device connected to a network can serve the needs of many users.
C) Software sharing saves money.
D) All of the above are true.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
21
The ____________________ is the biggest network of all.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
22
____ operating systems provide network control and include special functions for connecting computers and other devices.
A) Client
B) LAN
C) Server
D) WAN
A) Client
B) LAN
C) Server
D) WAN

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
23
Ali is researching communication hardware for her Intro to Networking class so that she can write a report for her instructor. Ali learns that ____ is high-speed Internet access.
A) dial-up
B) USB
C) broadband
D) firewall
A) dial-up
B) USB
C) broadband
D) firewall

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
24
A(n) ____________________ directs traffic on the Internet or on multiple connected networks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
25
Which of the following is NOT true about connecting to the Internet?
A) A cable modem uses the same type of cable as used for cable TV.
B) A cable modem can be connected to a router so that your computer has wireless access to the Internet.
C) T-1 lines can be used for data transfer on a network or provide phone service for a building.
D) A DSL can carry data, but not voice.
A) A cable modem uses the same type of cable as used for cable TV.
B) A cable modem can be connected to a router so that your computer has wireless access to the Internet.
C) T-1 lines can be used for data transfer on a network or provide phone service for a building.
D) A DSL can carry data, but not voice.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
26
A(n) ____________________ is a small, simple, inexpensive device that joins multiple computers together.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
27
Which of the following types of networks use IP technology?
A) Intranets
B) Extranets
C) the Internet
D) All of the above
A) Intranets
B) Extranets
C) the Internet
D) All of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
28
____ consist of special hardware and software that protects an Internal network from external networks.
A) Proxy servers
B) Antivirus
C) Biometrics
D) Firewalls
A) Proxy servers
B) Antivirus
C) Biometrics
D) Firewalls

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
29
Which of the following is NOT a type of server operating system?
A) Microsoft Windows
B) Mac OS X
C) Adobe Dreamweaver
D) UNIX/Linux
A) Microsoft Windows
B) Mac OS X
C) Adobe Dreamweaver
D) UNIX/Linux

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
30
Which of the following is NOT a classification type of network?
A) client/server
B) peer-to-peer
C) intranet
D) LAN
A) client/server
B) peer-to-peer
C) intranet
D) LAN

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
31
Which of the following is NOT true about network security?
A) It is not always evident that some type of computer crime or intrusion has occurred.
B) The best way to protect data is to effectively control access to it.
C) The most common form of restricting access to data is biometrics.
D) A secure password uses a mixture of upper- and lower-case letters, as well as numbers and special characters.
A) It is not always evident that some type of computer crime or intrusion has occurred.
B) The best way to protect data is to effectively control access to it.
C) The most common form of restricting access to data is biometrics.
D) A secure password uses a mixture of upper- and lower-case letters, as well as numbers and special characters.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
32
Ali is researching communication hardware for her Intro to Networking class so that she can write a report for her instructor. Ali learns that all of the following are true, EXCEPT: ____.
A) a cable modem can be connected directly to your computer, enabling you to connect to the Internet.
B) DSL modems are widely used to provide broadband Internet access.
C) T-1 lines can be used to transmit 25 digitized voice channels.
D) sniffer software devices are usually external devices, not built-in.
A) a cable modem can be connected directly to your computer, enabling you to connect to the Internet.
B) DSL modems are widely used to provide broadband Internet access.
C) T-1 lines can be used to transmit 25 digitized voice channels.
D) sniffer software devices are usually external devices, not built-in.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
33
A(n) ____________________ is a group of two or more computers linked together.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
34
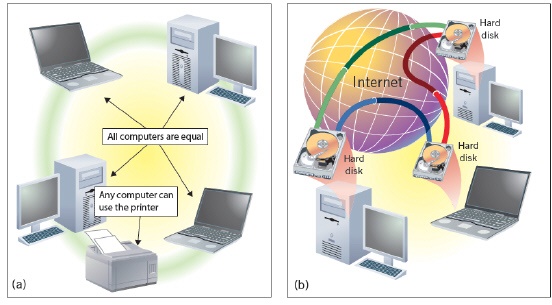 The figure above shows examples of a(n) ____ network.
The figure above shows examples of a(n) ____ network.A) client/server
B) peer-to-peer
C) intranet
D) extranet

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
35
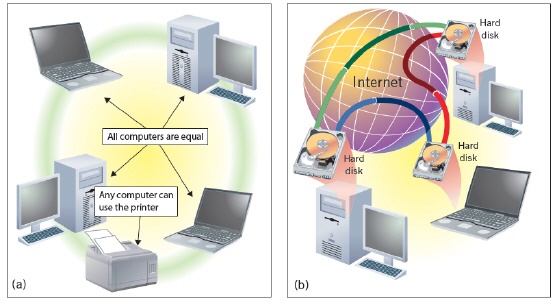 Which of the following is NOT true about the networks shown in the figure above?
Which of the following is NOT true about the networks shown in the figure above?A) No computer is designated as the server.
B) People on the network can determine what files on their computer they share with others on the network.
C) Designed for the exclusive use of people within an organization.
D) Used in many small offices.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
36
____________________ are people who break into computer systems to steal services and information.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
37
Simon is in charge of network security at a medium-sized company. His boss has asked him to give an overview of the company's network security to the board of directors. Simon tells the board that his department does all of the following, EXCEPT: ____.
A) regularly back up data and store it off site.
B) occasionally run antivirus software in order to protect data and programs.
C) use biometric security measures, which examine a fingerprint in order to gain access to a secure area.
D) use a firewall to keep unauthorized users from accessing the computers.
A) regularly back up data and store it off site.
B) occasionally run antivirus software in order to protect data and programs.
C) use biometric security measures, which examine a fingerprint in order to gain access to a secure area.
D) use a firewall to keep unauthorized users from accessing the computers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
38
Most WANs consist of two or more LANs and are connected by ____.
A) routers
B) modems
C) cables
D) nodes
A) routers
B) modems
C) cables
D) nodes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
39
A(n) ____ is hardware (a computer) that can be used to share mail, databases, and more.
A) client
B) server
C) operating system
D) router
A) client
B) server
C) operating system
D) router

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
40
Simon is in charge of network security at a medium-sized company. His boss has asked him to give an overview of the company's network security to the board of directors. Simon tells the board that he uses a(n) ____ as an intermediary between a user and the Internet, ensuring security, administrative control, and caching service.
A) proxy server
B) firewall
C) router
D) hub
A) proxy server
B) firewall
C) router
D) hub

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
41
Do you always know that computer crime or an intrusion has occurred? What is the best way to protect data? What might someone do if they gain unauthorized access to data? What is the most common form of restricting access? What should a secure password include? Give an example of a secure password. How is most password protection broken?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
42
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
43
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
44
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
45
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
46
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck








