Deck 31: Security, Privacy, and Ethics Online
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns
سؤال
Match between columns
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/46
العب
ملء الشاشة (f)
Deck 31: Security, Privacy, and Ethics Online
1
When using a notebook computer, put it on your lap for stability.
False
2
Which of the following is NOT a guideline for using network protection?
A) Reset any default passwords on your wireless router.
B) Enable encryption software.
C) To access an unsecured wireless connection, a hackers only needs a computer, wireless network card, and eavesdropping software.
D) Keep your network running at all times.
A) Reset any default passwords on your wireless router.
B) Enable encryption software.
C) To access an unsecured wireless connection, a hackers only needs a computer, wireless network card, and eavesdropping software.
D) Keep your network running at all times.
D
3
Generally, any information gathered from a company's computer system is company property and not an individual worker's personal property.
True
4
Which of the following is NOT true regarding computer hacking?
A) The FBI has a cybercrime branch.
B) Hackers are usually computer novices.
C) Hackers steal, change, or damage data.
D) Hacking causes millions of dollars of damage each year.
A) The FBI has a cybercrime branch.
B) Hackers are usually computer novices.
C) Hackers steal, change, or damage data.
D) Hacking causes millions of dollars of damage each year.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
5
A(n) ____ is usually a battery that provides power if the normal current is disrupted.
A) surge suppressor
B) surge protector
C) uninterruptible power supply
D) power strip
A) surge suppressor
B) surge protector
C) uninterruptible power supply
D) power strip

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
6
Unauthorized use of an unsecured wireless network can slow down your Internet access.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
7
Windows Defender is an example of antivirus software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
8
Network Solutions is a company that offers SSL certificates for sites that require privacy and security requirements.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
9
OSHA provides guidelines for using and purchasing computer equipment.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
10
Some tablet users are at risk for shoulder and neck pain.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
11
A virus is a program written by a hacker to corrupt data on a computer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
12
Typical phishing messages come from social networking sites, auction sites, banks, and the IRS.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
13
RSI stands for Repetitive____ injury
A) strain
B) stress
C) syndrome
D) symptom
A) strain
B) stress
C) syndrome
D) symptom

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
14
You should store your backup files near the computer so they will be accessible in case your hard drive fails.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
15
A software firewall is more secure and easier to monitor for large networks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
16
A brute force attack is also called a dictionary attack.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
17
Which of the following is NOT true about backing up data?
A) Backing up entails saving them to removable disks.
B) All hard drives fail eventually.
C) Web sites provide online backup services for a fee.
D) You backup procedure should place a priority on recently created files.
A) Backing up entails saving them to removable disks.
B) All hard drives fail eventually.
C) Web sites provide online backup services for a fee.
D) You backup procedure should place a priority on recently created files.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
18
If a network is small, a hardware firewall is sufficient.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
19
Spyware does not have any redeeming qualities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
20
Avoid or minimize eye strain by using a low -resolution monitor.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
21
Abby is a human resource director. She is preparing a presentation on ergonomics for an upcoming employee meeting. Abby tells the employees that they should avoid RSI, which can result when ____.
A) your eyes are strained
B) you use poor posture
C) you are tense when sitting at the computer
D) you make the same motion over a long period of time
A) your eyes are strained
B) you use poor posture
C) you are tense when sitting at the computer
D) you make the same motion over a long period of time

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
22
_______________________ designs adapt equipment and the workplace to help prevent RSIs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
23
____ is a third-party payment service.
A) VeriSign
B) Ebay
C) GoDaddy
D) PayPal
A) VeriSign
B) Ebay
C) GoDaddy
D) PayPal

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
24
Which of the following is true about viruses?
A) Viruses are attached to files.
B) You can inadvertently run a virus program by opening an e-mail message or attachment.
C) To protect against viruses, you should use strong passwords.
D) All of the above are true.
A) Viruses are attached to files.
B) You can inadvertently run a virus program by opening an e-mail message or attachment.
C) To protect against viruses, you should use strong passwords.
D) All of the above are true.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
25
A(n) _______________________ is a program used to capture user names and passwords.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
26
____ attacks use a script or program to log on to an account using hundreds of words or phrases stored in a file.
A) Virus
B) Sniffer
C) Brute force
D) Strong
A) Virus
B) Sniffer
C) Brute force
D) Strong

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
27
Browser ____________________ occurs when hackers use spyware to control your browser.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
28
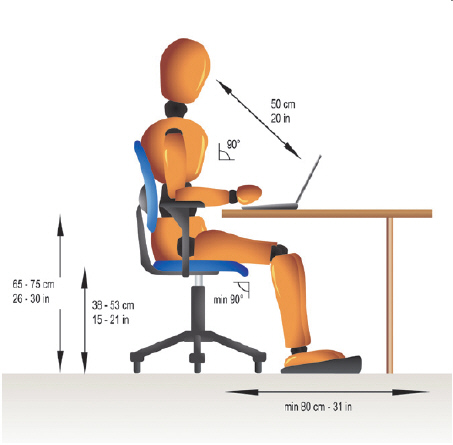 The above figure shows a workstation that is ____.
The above figure shows a workstation that is ____.A) set up using ergonomics
B) protected by biometrics
C) likely to cause RSIs
D) All of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
29
Joanna is a responsible and secure computer user. Joanna knows that all of the following are TRUE about securing data, EXCEPT: ____.
A) Companies often establish password-protected locations on hard drives.
B) It is always evident when some kind of computer crime or intrusion has occurred.
C) Unauthorized access is more likely to be caused by people who gain access through a written or shared password than by guessing your user name or password.
D) You should change your password frequently.
A) Companies often establish password-protected locations on hard drives.
B) It is always evident when some kind of computer crime or intrusion has occurred.
C) Unauthorized access is more likely to be caused by people who gain access through a written or shared password than by guessing your user name or password.
D) You should change your password frequently.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
30
Which of the following is NOT true about securing data?
A) Use an alias when communicating on a blog or social network.
B) The security and privacy of personal information on the Internet is getting worse all the time.
C) Verify that you log off a computer used in a public place such as a library.
D) All of the above are true.
A) Use an alias when communicating on a blog or social network.
B) The security and privacy of personal information on the Internet is getting worse all the time.
C) Verify that you log off a computer used in a public place such as a library.
D) All of the above are true.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
31
Which of the following is NOT true about setting access restrictions?
A) Most organizations use hardware firewalls to protect data from employee access.
B) Malicious tampering can also result in data loss.
C) Software enables parents to monitor computer usage.
D) Protecting users should be balanced with preserving privacy.
A) Most organizations use hardware firewalls to protect data from employee access.
B) Malicious tampering can also result in data loss.
C) Software enables parents to monitor computer usage.
D) Protecting users should be balanced with preserving privacy.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
32
Computer _______________________ involves invading someone else's computer, usually for personal gain or the satisfaction of defeating a securing system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
33
A(n) ____________________ can be used to provide the Web site owner with information about you and your computer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
34
A strong password contains all of the following, EXCEPT: ____.
A) personal information, such as a birth date
B) at least eight characters
C) at least one special character, such as @ or *
D) letters and numbers
A) personal information, such as a birth date
B) at least eight characters
C) at least one special character, such as @ or *
D) letters and numbers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
35
Joanna is a responsible and secure computer user. Joanna is familiar with the Code of Ethics published by the ____ that helps establish guidelines for developing and using computing technology.
A) IEEE
B) FTC
C) FBI
D) Department of Justice
A) IEEE
B) FTC
C) FBI
D) Department of Justice

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
36
A(n) ____ program is also called adware.
A) keylogger
B) hijacker
C) spyware
D) sniffer
A) keylogger
B) hijacker
C) spyware
D) sniffer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
37
Abby is a human resource director. She is preparing a presentation on ergonomics for an upcoming employee meeting. Abby tells the employees that they should do all of the following, EXCEPT: ____.
A) Use a plug that has a third pin for grounding when plugging in your computer.
B) Review the OSHA guidelines for using and purchasing computer equipment.
C) When you find a computer position that feels comfortable, sit in the same position for your entire computer session.
D) Be sure not to obstruct air vents on your notebook computer.
A) Use a plug that has a third pin for grounding when plugging in your computer.
B) Review the OSHA guidelines for using and purchasing computer equipment.
C) When you find a computer position that feels comfortable, sit in the same position for your entire computer session.
D) Be sure not to obstruct air vents on your notebook computer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
38
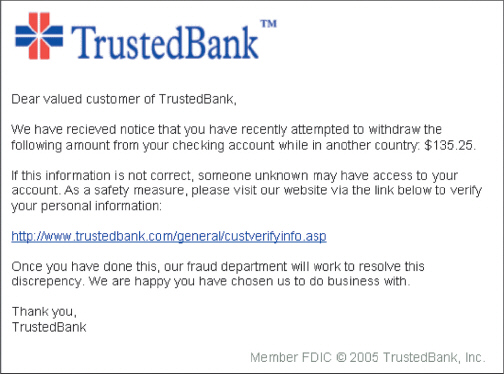 The figure above shows a likely ____ scheme.
The figure above shows a likely ____ scheme.A) sniffing
B) phishing
C) hijacking
D) adware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
39
GoDaddy is a site that provides ____.
A) domain name registration
B) antivirus software
C) certificates for e-commerce sites
D) online backup services
A) domain name registration
B) antivirus software
C) certificates for e-commerce sites
D) online backup services

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
40
A(n) ____ is a malicious program that records your keystrokes to keep track of the information such as credit card and account numbers.
A) keylogger
B) hijacker
C) spyware
D) sniffer
A) keylogger
B) hijacker
C) spyware
D) sniffer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
41
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
42
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
43
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
44
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
45
Match between columns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck
46
What effect can an unexpected power outage have on your data? What to most software programs do to prevent data loss? List two things you can use to safeguard computer systems against power outages. What does backing up entail? What priority should your backup procedure have?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 46 في هذه المجموعة.
فتح الحزمة
k this deck








