Deck 8: Operating Systems and Utility Programs
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/191
العب
ملء الشاشة (f)
Deck 8: Operating Systems and Utility Programs
1
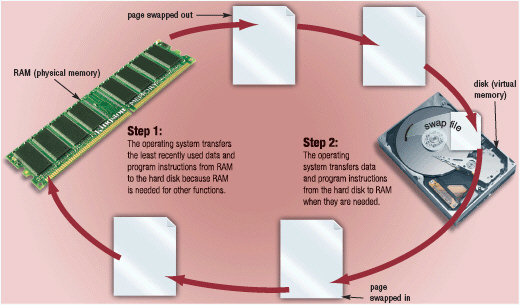 Figure 8-1 With virtual memory, which is illustrated in Figure 8-1, a ____ is the amount of data and program instructions that can swap at a given time.
Figure 8-1 With virtual memory, which is illustrated in Figure 8-1, a ____ is the amount of data and program instructions that can swap at a given time.A) log
B) page
C) spool
D) boot
B
2
With Windows Vista, a warm boot can be performed by ____.
A) pressing the power button on the computer
B) clicking a button on the task bar, then a Start menu button, and then a Lock menu button
C) pressing the restart button on the computer
D) all of the above
A) pressing the power button on the computer
B) clicking a button on the task bar, then a Start menu button, and then a Lock menu button
C) pressing the restart button on the computer
D) all of the above
B
3
 Figure 8-3 When first developed by Microsoft, ____ used a command-line interface like the one in Figure 8-3, but later versions included both command-line and menu driven user interfaces.
Figure 8-3 When first developed by Microsoft, ____ used a command-line interface like the one in Figure 8-3, but later versions included both command-line and menu driven user interfaces.A) Windows XP
B) DOS
C) Mac OS X
D) UNIX
B
4
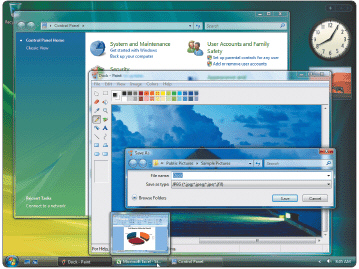 Figure 8-4 Computers with more than ____ of RAM work with the Aero interface in Windows Vista as shown in Figure 8-4.
Figure 8-4 Computers with more than ____ of RAM work with the Aero interface in Windows Vista as shown in Figure 8-4.A) 256 MB
B) 526 MB
C) 1 GB
D) 2.5 GB

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
5
 Figure 8-3 In a ____ like the one shown in Figure 8-3, a user types commands or presses special keys on the keyboard (such as function keys or key combinations) to enter data and instructions.
Figure 8-3 In a ____ like the one shown in Figure 8-3, a user types commands or presses special keys on the keyboard (such as function keys or key combinations) to enter data and instructions.A) command-line interface
B) menu-driven interface
C) performance-monitor interface
D) graphical user interface (GUI)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
6
With a ____, users interact with menus and visual images such as icons, buttons, and other objects to issue commands.
A) command-line interface
B) menu-driven interface
C) performance-monitor interface
D) graphical user interface (GUI)
A) command-line interface
B) menu-driven interface
C) performance-monitor interface
D) graphical user interface (GUI)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
7
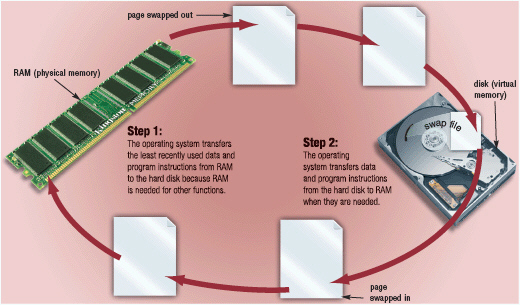 Figure 8-1 With virtual memory, which is illustrated in Figure 8-1, when an operating system spends much of its time paging, instead of executing application software, it is said to be ____.
Figure 8-1 With virtual memory, which is illustrated in Figure 8-1, when an operating system spends much of its time paging, instead of executing application software, it is said to be ____.A) zipping
B) compressing
C) restoring
D) thrashing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
8
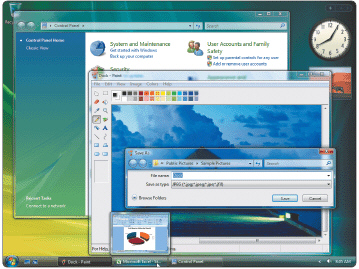 Figure 8-4 The Aero interface in Windows Vista shown in Figure 8-4 offers ____.
Figure 8-4 The Aero interface in Windows Vista shown in Figure 8-4 offers ____.A) an enhanced visual look
B) animation
C) additional navigation options
D) All of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
9
The person overseeing network operations, called the ____, uses the network OS to add and remove users, computers, and other devices to and from a network.
A) network administrator
B) network operator
C) network performance monitor
D) network server
A) network administrator
B) network operator
C) network performance monitor
D) network server

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
10
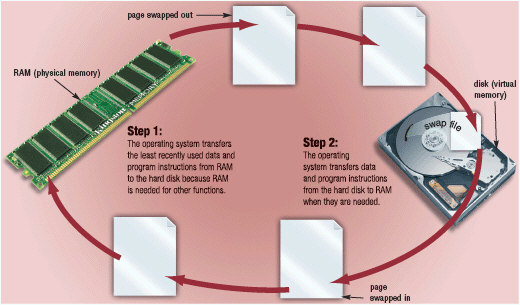 Figure 8-1 With virtual memory, which is illustrated in Figure 8-1, the technique of swapping items between memory and storage, called ____, is a time-consuming process for the computer.
Figure 8-1 With virtual memory, which is illustrated in Figure 8-1, the technique of swapping items between memory and storage, called ____, is a time-consuming process for the computer.A) logging
B) paging
C) spooling
D) booting

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
11
A cross-platform program is one that runs ____.
A) only on one operating system
B) differently on every operating system
C) the same on multiple operating systems
D) differently on one operating system
A) only on one operating system
B) differently on every operating system
C) the same on multiple operating systems
D) differently on one operating system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
12
Two types of system software are ____.
A) application software and utility programs
B) Web browsers and application software
C) operating systems and utility programs
D) operating systems and Web browsers
A) application software and utility programs
B) Web browsers and application software
C) operating systems and utility programs
D) operating systems and Web browsers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
13
Networks, servers, mainframes, and supercomputers allow hundreds to thousands of users to connect at the same time, and thus are ____.
A) single user
B) single processing
C) multiuser
D) multiprocessing
A) single user
B) single processing
C) multiuser
D) multiprocessing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
14
During a cold boot on a personal computer, the POST (power-on self test) results are compared with data in a ____ chip.
A) CMOS
B) UNIX
C) BIOS
D) SCSI
A) CMOS
B) UNIX
C) BIOS
D) SCSI

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
15
In Windows Vista, the ____ contains a list of programs that open automatically when users boot the computer.
A) Restore folder
B) Startup folder
C) Swap folder
D) Backup folder
A) Restore folder
B) Startup folder
C) Swap folder
D) Backup folder

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
16
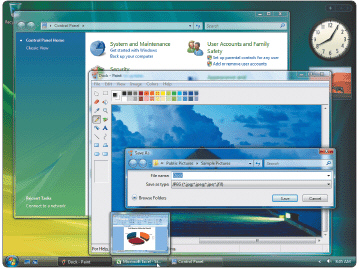 Figure 8-4 Windows Vista ____ offers the Aero interface (shown in Figure 8-4) to basic users.
Figure 8-4 Windows Vista ____ offers the Aero interface (shown in Figure 8-4) to basic users.A) Home Basic
B) Home Premium
C) Professional
D) Enterprise

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
17
In Windows Vista, the ____ consists of several files that contain the system configuration information.
A) buffer
B) driver
C) platform
D) registry
A) buffer
B) driver
C) platform
D) registry

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
18
If a new device, such as a printer or scanner, is attached to a computer, its ____ must be installed before the device can be used.
A) driver
B) platform
C) manager
D) kernel
A) driver
B) platform
C) manager
D) kernel

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
19
A(n) ____ is a communications line between a device and the processor.
A) disk operating system line (DOS)
B) preemptive multitasking line (PMT)
C) interrupt request line (IRQ)
D) fault-tolerant computer line (FTC)
A) disk operating system line (DOS)
B) preemptive multitasking line (PMT)
C) interrupt request line (IRQ)
D) fault-tolerant computer line (FTC)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
20
PDAs, smart phones, and other small computing devices often use a ____ operating system.
A) single user/single tasking
B) single user/multitasking
C) multiuser
D) multiprocessing
A) single user/single tasking
B) single user/multitasking
C) multiuser
D) multiprocessing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
21
Some stand-alone operating systems are called ____ because they also work in conjunction with a network operating system.
A) embedded operating systems
B) client operating systems
C) multitasking operating systems
D) server operating systems
A) embedded operating systems
B) client operating systems
C) multitasking operating systems
D) server operating systems

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
22
While entering a ____, most computers hide the actual characters by displaying some other characters, such as asterisks (*) or dots.
A) user name
B) password
C) user ID
D) all of the above
A) user name
B) password
C) user ID
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
23
Windows Vista includes the diagnostic utility, ____, which diagnoses problems as well as suggests courses of action.
A) Disk Cleanup
B) Windows Explorer
C) DriveSpace
D) Problem Reports & Solutions
A) Disk Cleanup
B) Windows Explorer
C) DriveSpace
D) Problem Reports & Solutions

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
24
A new feature of Windows Vista is ____, which helps users locate documents by showing thumbnails that previews documents' content.
A) Document Explorer
B) Windows Explorer
C) Virtual Folders
D) Business Folders
A) Document Explorer
B) Windows Explorer
C) Virtual Folders
D) Business Folders

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
25
____ a disk, or reorganizing it so the files are stored in contiguous sectors, speeds up disk access and thus the performance of the entire computer.
A) Formatting
B) Defragmenting
C) Spooling
D) Compressing
A) Formatting
B) Defragmenting
C) Spooling
D) Compressing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
26
In Windows XP, the uninstaller is available through the ____ program command in the Control Panel.
A) Add New Hardware
B) Uninstall
C) Add/Remove Programs
D) Power Management
A) Add New Hardware
B) Uninstall
C) Add/Remove Programs
D) Power Management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
27
____ is available in five editions: Home Basic, Home Premium, Ultimate, Business, and Enterprise.
A) Windows Vista
B) Linux
C) UNIX
D) DOS
A) Windows Vista
B) Linux
C) UNIX
D) DOS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
28
Bell Labs licensed ____ for a low fee to numerous colleges and universities, where the operating system obtained a wide following.
A) Linux
B) DOX
C) UNIX
D) Windows XP
A) Linux
B) DOX
C) UNIX
D) Windows XP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
29
Screen savers originally were developed to prevent a problem called ____, in which images could be permanently etched on a monitor's screen.
A) thrashing
B) paging
C) ghosting
D) hacking
A) thrashing
B) paging
C) ghosting
D) hacking

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
30
____ includes features from previous Apple computer operating systems, such as large photo-quality icons, built-in networking support, and enhanced speech recognition.
A) DOS
B) UNIX
C) Linux
D) Mac OS X
A) DOS
B) UNIX
C) Linux
D) Mac OS X

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
31
A ____ is an icon on the desktop that provides a user with immediate access to a program or file.
A) kernel
B) spooler
C) buffer
D) shortcut
A) kernel
B) spooler
C) buffer
D) shortcut

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
32
Windows Vista includes file managers called ____.
A) Viewers
B) Windows Explorer
C) Windows Controllers
D) Managers
A) Viewers
B) Windows Explorer
C) Windows Controllers
D) Managers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
33
Released in 2006, ____ is an upgrade to Windows XP.
A) DOS
B) Windows Professional x64 Edition
C) Windows Vista
D) Windows Millennium
A) DOS
B) Windows Professional x64 Edition
C) Windows Vista
D) Windows Millennium

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
34
Examples of network operating systems include all of the following except ____.
A) Windows Server 2003
B) NetWare and Solaris
C) Windows Vista
D) UNIX and Linux
A) Windows Server 2003
B) NetWare and Solaris
C) Windows Vista
D) UNIX and Linux

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
35
Many backup programs ____, or shrink the size of, files during the backup process.
A) restore
B) register
C) fragment
D) compress
A) restore
B) register
C) fragment
D) compress

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
36
____ is the process of encoding data and information into an unreadable form.
A) Encryption
B) Formatting
C) Transmission
D) Spooling
A) Encryption
B) Formatting
C) Transmission
D) Spooling

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
37
The two most popular GUIs available for ____ are GNOME and KDE.
A) DOS
B) Windows XP
C) Mac OS X
D) Linux
A) DOS
B) Windows XP
C) Mac OS X
D) Linux

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
38
Windows Vista includes an image viewer called ____.
A) Windows Photo Gallery
B) Windows Explorer
C) DriveSpace
D) the Documents Explorer
A) Windows Photo Gallery
B) Windows Explorer
C) DriveSpace
D) the Documents Explorer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
39
Examples of stand-alone operating systems include all of the following except ____.
A) Windows Vista
B) NetWare and Solaris
C) Mac OS X
D) UNIX and Linux
A) Windows Vista
B) NetWare and Solaris
C) Mac OS X
D) UNIX and Linux

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
40
Utility programs included with most operating systems provide all of the following functions except ____.
A) managing files and viewing images
B) uninstalling programs and diagnosing problems
C) removing viruses and compressing files
D) backing up files and defragmenting disks
A) managing files and viewing images
B) uninstalling programs and diagnosing problems
C) removing viruses and compressing files
D) backing up files and defragmenting disks

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
41
The Windows Server 2003 family includes ____ for medium- to large-sized businesses, including those with e-commerce operations.
A) Windows Server 2003, Standard Edition
B) Windows Server 2003, Enterprise Edition
C) Windows Server 2003, Datacenter Edition
D) Windows Server 2003, Web Edition
A) Windows Server 2003, Standard Edition
B) Windows Server 2003, Enterprise Edition
C) Windows Server 2003, Datacenter Edition
D) Windows Server 2003, Web Edition

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
42
____ is software that acts without a user's knowledge and deliberately alters a computer's operations.
A) Malware
B) A utility program
C) System software
D) A diagnostic program
A) Malware
B) A utility program
C) System software
D) A diagnostic program

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
43
A(n) ____ drive is the drive from which a personal computer starts.
A) origin
B) initiating
C) archive
D) boot
A) origin
B) initiating
C) archive
D) boot

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
44
The Windows Server 2003 family includes ____ for businesses with huge volumes of transactions and large-scale databases.
A) Windows Server 2003, Standard Edition
B) Windows Server 2003, Enterprise Edition
C) Windows Server 2003, Datacenter Edition
D) Windows Server 2003, Web Edition
A) Windows Server 2003, Standard Edition
B) Windows Server 2003, Enterprise Edition
C) Windows Server 2003, Datacenter Edition
D) Windows Server 2003, Web Edition

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
45
The kernel is memory ____, which means it remains in memory while the computer is running.
A) resident
B) linked
C) based
D) indexed
A) resident
B) linked
C) based
D) indexed

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
46
A ____ does not replicate itself to other computers.
A) virus
B) worm
C) Trojan horse
D) all of the above
A) virus
B) worm
C) Trojan horse
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
47
The BIOS executes a series of tests, collectively called the ____, which check the various system components including the buses, system clock, adapter cards, RAM chips, mouse, keyboard, and drives.
A) boot
B) preemption
C) POST
D) UNIX
A) boot
B) preemption
C) POST
D) UNIX

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
48
The Windows Server 2003 family includes ____ for the typical small- to medium-sized business network.
A) Windows Server 2003, Standard Edition
B) Windows Server 2003, Enterprise Edition
C) Windows Server 2003, Datacenter Edition
D) Windows Server 2003, Web Edition
A) Windows Server 2003, Standard Edition
B) Windows Server 2003, Enterprise Edition
C) Windows Server 2003, Datacenter Edition
D) Windows Server 2003, Web Edition

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
49
____ is the process of starting or restarting a computer.
A) Launching
B) Loading
C) Booting
D) Keying
A) Launching
B) Loading
C) Booting
D) Keying

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
50
____, which is used on PDAs and smart phones, includes handwriting recognition software called Graffiti.
A) Palm OS
B) Symbian OS
C) Windows Mobile
D) Windows CE
A) Palm OS
B) Symbian OS
C) Windows Mobile
D) Windows CE

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
51
Like Linux, ____ is a multipurpose operating system because it is both a stand-alone and network operating system.
A) NetWare
B) UNIX
C) Mac OS X
D) Windows XP
A) NetWare
B) UNIX
C) Mac OS X
D) Windows XP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
52
The ____ is firmware that contains a computer's startup instructions.
A) POST
B) BIOS
C) CMOS
D) DIOS
A) POST
B) BIOS
C) CMOS
D) DIOS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
53
Popular embedded operating systems include all of the following except ____.
A) Windows CE
B) Palm OS and Symbian OS
C) Windows Mobile
D) NetWare
A) Windows CE
B) Palm OS and Symbian OS
C) Windows Mobile
D) NetWare

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
54
The ____ is the core of an operating system that manages memory and devices, maintains the computer's clock, starts applications, and assigns the computer's resources, such as devices, programs, data, and information.
A) cell
B) grid
C) nexus
D) kernel
A) cell
B) grid
C) nexus
D) kernel

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
55
The operating system that a computer uses sometimes is called the ____.
A) base
B) platform
C) index
D) boot system
A) base
B) platform
C) index
D) boot system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
56
Compressed files, sometimes called ____.
A) ripped files, usually have a .rip extension
B) tipped files, usually have a .tip extension
C) slipped files, usually have a .slip extension
D) zipped files, usually have a .zip extension
A) ripped files, usually have a .rip extension
B) tipped files, usually have a .tip extension
C) slipped files, usually have a .slip extension
D) zipped files, usually have a .zip extension

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
57
____ is a program placed on a computer without the user's knowledge or consent that secretly collects information about the user, often related to Web browsing habits.
A) Spyware
B) A pop-up ad
C) Spam
D) A filter
A) Spyware
B) A pop-up ad
C) Spam
D) A filter

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
58
A(n) ____ system is a set of programs containing instructions that coordinate all the activities among computer hardware resources.
A) operating
B) disk-based
C) management
D) platform
A) operating
B) disk-based
C) management
D) platform

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
59
With ____ multitasking, the operating system interrupts a program that is executing and passes control to another program waiting to be executed.
A) preemptive
B) fault-tolerant
C) remastered
D) resident
A) preemptive
B) fault-tolerant
C) remastered
D) resident

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
60
____ is a program that removes or blocks certain items from being displayed.
A) Spyware
B) A pop-up ad
C) Spam
D) A filter
A) Spyware
B) A pop-up ad
C) Spam
D) A filter

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
61
A disk ____ is a utility that searches for and removes unnecessary files.
A) scanner
B) doctor
C) detective
D) archiver
A) scanner
B) doctor
C) detective
D) archiver

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
62
A file ____ utility is a utility that shrinks the size of a file(s).
A) unit
B) compression
C) matrix
D) conversion
A) unit
B) compression
C) matrix
D) conversion

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
63
The term, computer ____, describes a potentially damaging computer program that affects, or infects, a computer negatively by altering the way the computer works without the user's knowledge or permission.
A) hotspot
B) file compression utility
C) virus
D) file conversion utility
A) hotspot
B) file compression utility
C) virus
D) file conversion utility

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
64
A disk ____ is a utility that reorganizes the files and unused space on a computer's hard disk so the operating system accesses data more quickly and programs run faster.
A) manager
B) defragmenter
C) organizer
D) OS
A) manager
B) defragmenter
C) organizer
D) OS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
65
A ____ is malware that copies itself repeatedly, for example in memory or over a network, using up system resources and possibly shutting the system down.
A) Trojan horse
B) malex
C) file compression utility
D) worm
A) Trojan horse
B) malex
C) file compression utility
D) worm

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
66
A performance ____ is a program that assesses and reports information about various computer resources and devices.
A) roster
B) monitor
C) reporter
D) manager
A) roster
B) monitor
C) reporter
D) manager

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
67
A(n) ____ computer is a computer that continues to operate when one of its components fails, ensuring that no data is lost.
A) failsafe
B) antivirus
C) immune
D) fault-tolerant
A) failsafe
B) antivirus
C) immune
D) fault-tolerant

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
68
____ is an open source multitasking operating system designed for smart phones.
A) Mac OS X
B) Symbian OS
C) NetWare
D) Google OS
A) Mac OS X
B) Symbian OS
C) NetWare
D) Google OS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
69
The term ____ refers to several single user operating systems developed by Microsoft in the early 1980s for personal computers.
A) UNIX
B) Mac OS X
C) LINUX
D) DOS
A) UNIX
B) Mac OS X
C) LINUX
D) DOS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
70
____ is a fast, reliable Windows operating system, providing quicker startup, better performance, and a simpler visual look than previous Windows versions.
A) Windows XP
B) Windows Me
C) Windows Mobile
D) Windows CE
A) Windows XP
B) Windows Me
C) Windows Mobile
D) Windows CE

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
71
A ____ is malware that hides within or looks like a legitimate program, such as a screen saver.
A) Trojan horse
B) virus
C) worm
D) hidden file
A) Trojan horse
B) virus
C) worm
D) hidden file

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
72
A file ____ utility is a utility that transforms the contents of a file or data from one format to another.
A) compression
B) transformation
C) conversion
D) reformatting
A) compression
B) transformation
C) conversion
D) reformatting

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
73
A(n) ____ operating system supports two or more processors running programs at the same time.
A) virtual
B) indexed
C) multiprocessing
D) fault-tolerant
A) virtual
B) indexed
C) multiprocessing
D) fault-tolerant

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
74
A file ____ is a utility that performs functions related to file management.
A) monitor
B) controller
C) scanner
D) manager
A) monitor
B) controller
C) scanner
D) manager

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
75
With ____ memory, the operating system allocates a portion of a storage medium, usually the hard disk, to function as additional RAM.
A) virtual
B) performance
C) device
D) managed
A) virtual
B) performance
C) device
D) managed

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
76
A(n) ____ operating system enables two or more users to run programs simultaneously.
A) multiplied
B) multiuser
C) engaged
D) rasterized
A) multiplied
B) multiuser
C) engaged
D) rasterized

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
77
A(n) ____ utility is a utility that compiles technical information about a computer's hardware and certain system software programs and then prepares a report outlining any identified problems.
A) symbian
B) operational
C) diagnostic
D) analytic
A) symbian
B) operational
C) diagnostic
D) analytic

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
78
The area of the hard disk used for virtual memory is called a(n) ____ file because it exchanges data, information, and instructions between memory and storage.
A) exchange
B) swap
C) drive
D) device
A) exchange
B) swap
C) drive
D) device

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
79
A(n) ____ is a type of system software that allows a user to perform maintenance-type tasks, usually related to managing a computer, its devices, or its programs.
A) driver
B) scanner
C) utility
D) defragmenter
A) driver
B) scanner
C) utility
D) defragmenter

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck
80
A(n) ____ is a small program that tells the operating system how to communicate with a specific device.
A) driver
B) monitor
C) utility
D) OS
A) driver
B) monitor
C) utility
D) OS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 191 في هذه المجموعة.
فتح الحزمة
k this deck








