Deck 6: Firewalls and Border Security
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/86
العب
ملء الشاشة (f)
Deck 6: Firewalls and Border Security
1
Routers that use a single protocol (such as TCP/IP) maintain multiple address databases.
False
2
Network redundancy translation is used when there is a limited number of decoy addresses available, or when there are more computers on the internal network than decoy addresses.
False
3
A route map is used to determine the best route through a network.
False
4
With CIDR, the number after the slash is the number of bits in the address that are allocated for the host identifier.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
5
There are six IP address classes, Class A through Class F, each used with a different type of network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
6
Some proxies are able to provide caching services as a way to reduce the load on servers within the internal network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
7
IP is a connection-oriented protocol because its primary mission is to provide network-to-network addressing and routing information, and to change the size of packets when the size varies from network to network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
8
One element in border security is to configure security policies on each firewall so that access is automatically allowed, except for those who are manually configured to have access blocked through the firewall.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
9
In Windows Server 2003, Radius is a set of services that enable or manage remote access to Windows Server 2003, for instance, through dial-up or telecommunications lines.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
10
A router performs packet filtering and is often used as a firewall on a network, in addition to the other functions it performs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
11
UDP does not provide the same level of reliability and error checking as TCP, because it relies only on the checksum to ensure reliability.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
12
The border router is a firewall that is configured with security policies to control the traffic that is permitted to cross a border in either direction.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
13
The payload data within the IP packet is actually the TCP header and the application data when connection-oriented services are used.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
14
Packet filtering is accomplished using one of two techniques: stateless filtering and stateful filtering.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
15
Routers can isolate portions of a network to prevent areas of heavy traffic from reaching the broader network system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
16
IPTables is a powerful tool that can be used to implement network security in many ways; it is configured through a terminal window using the iptables command.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
17
Class D addresses do not reflect the network size, but only tell you that the communication is a multicast.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
18
The simplest way to configure a firewall in Red Hat Linux 9.x is by using the Security Level Configuration tool.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
19
TCP/IP consists of nearly 200 nonproprietary protocols that interconnect computer systems efficiently and reliably.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
20
Stateless filtering does not filter on the basis of the context of the communication, and so it has limited value in a firewall.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
21
Which TCP ports are considered to be "well-known" ports?
A) 0-511
B) 0-1023
C) 1-512
D) 1-1024
A) 0-511
B) 0-1023
C) 1-512
D) 1-1024

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
22
Which TCP field is used when there is too little or no optional data to complete the required header length, which must be divisible by 32?
A) Checksum
B) Options
C) Padding
D) Window
A) Checksum
B) Options
C) Padding
D) Window

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
23
Which of the following applications use UDP for network communications?
A) DNS
B) NetBIOS naming functions
C) Streaming audio applications
D) All of the above
A) DNS
B) NetBIOS naming functions
C) Streaming audio applications
D) All of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
24
When using classful addressing, the IP address 122.16.232.4 belongs to which network class?
A) A
B) B
C) C
D) D
A) A
B) B
C) C
D) D

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
25
Which field in an IP packet contains the network address and the address of the receiving device?
A) Source address
B) Identification
C) Version
D) Destination address
A) Source address
B) Identification
C) Version
D) Destination address

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
26
What is the length of the MAC address on a host system?
A) 32 bits
B) 48 bits
C) 64 bits
D) 128 bits
A) 32 bits
B) 48 bits
C) 64 bits
D) 128 bits

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
27
How many station addresses are available in a Class B network?
A) 254
B) 65,232
C) 65,534
D) 63,535
A) 254
B) 65,232
C) 65,534
D) 63,535

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
28
Which of the following protocols both sequences and acknowledges frames?
A) IP
B) UDP
C) TCP
D) ICMP
A) IP
B) UDP
C) TCP
D) ICMP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
29
Which of the following is performed by UDP to provide communication reliability?
A) Flow control
B) Sequencing
C) Checksum
D) Both a and b
E) Both a and c
A) Flow control
B) Sequencing
C) Checksum
D) Both a and b
E) Both a and c

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
30
Which of the following TCP/UDP ports is used for NetBIOS applications?
A) 23
B) 53
C) 119
D) 139
A) 23
B) 53
C) 119
D) 139

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
31
Which of the following can port-scanning software be used for?
A) To collect information about a target computer
B) To crash a system
C) To intercept and decrypt data sent from a target computer
D) Both a and b
E) Both b and c
A) To collect information about a target computer
B) To crash a system
C) To intercept and decrypt data sent from a target computer
D) Both a and b
E) Both b and c

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
32
Which of the following is the proper range for a Class D network?
A) 1.0.0.0 - 126.255.255.255
B) 128.0.0.0 - 191.255.255.255
C) 192.0.0.0 - 223.255.255.255
D) 224.0.0.0 to 239.255.255.255
A) 1.0.0.0 - 126.255.255.255
B) 128.0.0.0 - 191.255.255.255
C) 192.0.0.0 - 223.255.255.255
D) 224.0.0.0 to 239.255.255.255

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
33
Which of the following TCP/UDP ports is used for DNS server applications?
A) 53
B) 80
C) 139
D) 443
A) 53
B) 80
C) 139
D) 443

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
34
What is the default subnet mask for a Class D network?
A) 255.0.0.0
B) 255.255.0.0
C) 255.255.255.0
D) 255.255.255.224
E) None of the above
A) 255.0.0.0
B) 255.255.0.0
C) 255.255.255.0
D) 255.255.255.224
E) None of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
35
IPv6 has a(n) _____ address capability and a 40-byte header.
A) 32 bit
B) 64 bit
C) 128 bit
D) 256 bit
A) 32 bit
B) 64 bit
C) 128 bit
D) 256 bit

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
36
What is the minimum length of a TCP header?
A) 8 bytes
B) 16 bytes
C) 20 bytes
D) 32 bytes
A) 8 bytes
B) 16 bytes
C) 20 bytes
D) 32 bytes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
37
When using Class B addressing, which portion of the IP address 140.26.23.48 is the network address?
A) 140
B) 140.26
C) 140.26.23
D) 26.23
A) 140
B) 140.26
C) 140.26.23
D) 26.23

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
38
What is the length of the sequence number that TCP uses to ensure that all frames are received?
A) 16 bits
B) 32 bits
C) 32 bytes
D) 64 bytes
A) 16 bits
B) 32 bits
C) 32 bytes
D) 64 bytes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
39
In the OSI model, what layer is the network layer?
A) 1
B) 2
C) 3
D) 4
A) 1
B) 2
C) 3
D) 4

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
40
Which port does SMTP use for communication?
A) 23
B) 25
C) 110
D) 443
A) 23
B) 25
C) 110
D) 443

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
41
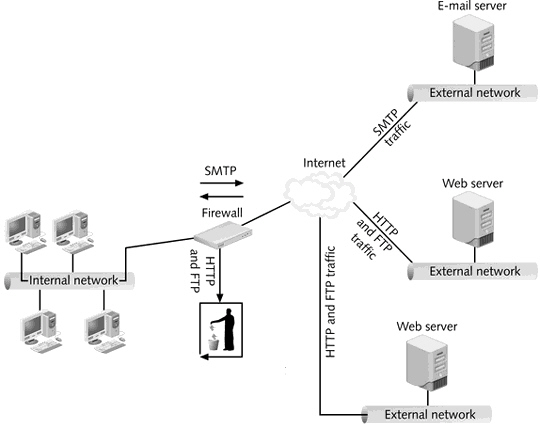 What is displayed in the figure above?
What is displayed in the figure above?A) Proxy firewall as an application-level gateway
B) Firewall proxy as a circuit-level gateway
C) OSPF border areas
D) Implementing border security

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
42
Does NetBEUI use the type of addressing that would enable it to be forwarded or routed to networks other than the one on which it is used?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
43
When two devices communicate using connection-oriented methods, do they establish sequence numbers for each frame that is transmitted and place the sequence number in the frame header?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
44
Which of the following can be used to calculate a metric?
A) Number of hops
B) Size of the packet
C) Bandwidth
D) Both a and b
E) a, b, and c
A) Number of hops
B) Size of the packet
C) Bandwidth
D) Both a and b
E) a, b, and c

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
45
Which of the following is the loopback address?
A) 127.0.0.0
B) 172.0.0.1
C) 172.0.0.0
D) 127.0.0.1
A) 127.0.0.0
B) 172.0.0.1
C) 172.0.0.0
D) 127.0.0.1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
46
You have configured a firewall to block Telnet and SSH communications by blocking the TCP and UDP ports 22 and 80. Will this accomplish the job?
A) Yes
B) No, because it is also necessary to block port 443 for FTP
C) No, because SSH is still not blocked
D) No, because Telnet is still not blocked
A) Yes
B) No, because it is also necessary to block port 443 for FTP
C) No, because SSH is still not blocked
D) No, because Telnet is still not blocked

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
47
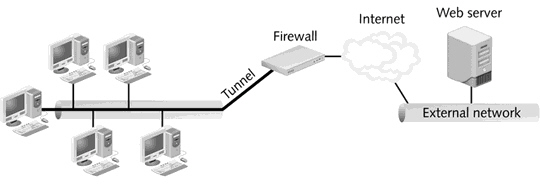 What is displayed in the figure above?
What is displayed in the figure above?A) OSPF border areas
B) Using NAT on a small office network
C) Proxy firewall as an application-level gateway
D) Firewall proxy as a circuit-level gateway

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
48
If you had configured a firewall in Windows XP and were concerned that you had been the victim of an attack, where would you look to be able to find out this information?
A) In the Registry of your workstation
B) In the \Windows\pfirewall.log file
C) In the ICS properties under the View log tab
D) In the System event log
A) In the Registry of your workstation
B) In the \Windows\pfirewall.log file
C) In the ICS properties under the View log tab
D) In the System event log

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
49
Which type of NAT is used when the firewall is connected to multiple public networks or Internet service providers, and thus there is a range of different decoy addresses used for each external network?
A) Network redundancy translation
B) Dynamic translation
C) Static translation
D) Load balancing
A) Network redundancy translation
B) Dynamic translation
C) Static translation
D) Load balancing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
50
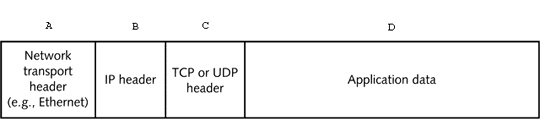 In the figure above, which letter indicates the portion of the TCP/IP packet that is the TCP segment?
In the figure above, which letter indicates the portion of the TCP/IP packet that is the TCP segment?A) A
B) A and B
C) B and C
D) C and D

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
51
Which type of packet filtering tracks information about a communication session, such as which ports are in use, drawing from the contents of multiple packets?
A) Ingress
B) Stateful
C) Stateless
D) Source route
A) Ingress
B) Stateful
C) Stateless
D) Source route

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
52
Does dynamic NAT translate a range of addresses on the internal network to a range of specific decoy addresses?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
53
IPTables is used to configure firewall and NAT activities in which of the following operating systems?
A) Windows 2000 Server
B) Windows Server 2003
C) Mac OS X
D) Red Hat Linux
A) Windows 2000 Server
B) Windows Server 2003
C) Mac OS X
D) Red Hat Linux

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
54
Which type of proxy stores recently made service requests, allowing them to fulfill an individual client's request without needing to contact the server on the internal network?
A) Application-level gateway
B) Circuit-level gateway
C) Caching
D) Firewall
A) Application-level gateway
B) Circuit-level gateway
C) Caching
D) Firewall

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
55
Are network classes A through C intended for unicast addressing methods?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
56
What protocol was used extensively for versions of NetWare prior to version 5?
A) UDP
B) IPX
C) TCP/IP
D) NetBEUI
A) UDP
B) IPX
C) TCP/IP
D) NetBEUI

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
57
Does UDP provide the same level of reliability and error checking as TCP?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
58
If you required 1000 IP host identities for your network, which of the following CIDR addresses would be valid if you want to make the best use of IP addressing?
A) 161.15.37.16/12
B) 161.15.37.16/20
C) 161.15.37.16/22
D) 161.15.37.16/25
A) 161.15.37.16/12
B) 161.15.37.16/20
C) 161.15.37.16/22
D) 161.15.37.16/25

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
59
When using the Red Hat Linux 9.x Security Level Configuration tool, which security level only allows connections for using DNS and DHCP services?
A) High
B) Medium
C) Low
D) No Firewall
A) High
B) Medium
C) Low
D) No Firewall

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
60
What is the only metric used by the RIP routing protocol?
A) Bandwidth
B) Size of the packet
C) Number of incoming packets waiting to be processed
D) Number of hops
A) Bandwidth
B) Size of the packet
C) Number of incoming packets waiting to be processed
D) Number of hops

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
61
Does RIP have the ability to send only routing updates to other routers instead of the entire routing table?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
62
What are the three component protocols within the TCP/IP protocol suite?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
63
In TCP communications, the number of data bytes transmitted in a frame is called the ____________________ because the number can be increased or decreased from one moment to the next by mutual agreement of the two communicating stations.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
64
When a TCP segment is formatted with the additional IP header information, the entire unit is called a(n) ____________________ or packet.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
65
In a TCP header, the ____________________ is a 16-bit CRC that is computed by adding the length of all header fields plus the length of the data payload field. 6

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
66
Firewalls provide border security by using three different approaches. What are they?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
67
Can routers filter packets on the basis of information associated with each port (inbound and outbound connections) to control network traffic?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
68
What five border points should be protected by a strong border security design?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
69
UDP does not provide the same level of reliability and error checking as TCP, because it relies only on the ____________________ to ensure reliability.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
70
When a server is set up for ______________________________, it performs address translation between the local network clients (including the server as an Internet user) and the Internet.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
71
When an application on a network station uses a(n) ____________________ packet (which is the most typical packet used by an application), one copy of each packet in a transmission is sent to each destination intended to receive the packet.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
72
What four fields does a UDP header contain?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
73
What are the four ways to perform network address translation?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
74
Red Hat Linux 9.x offers the ____________________ interface for configuring NAT and complex firewall security from the command line in a terminal window.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
75
Connection-oriented services occur between the ____________________ sublayer of the data-link layer (layer 2) and the network layer (layer 3) in the OSI model.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
76
A newer way to ignore address class designation is by using ______________________________ addressing, which puts a slash (/) after the dotted decimal notation.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
77
Is Internet Connection Firewall available in Windows Server 2003, Enterprise Edition?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
78
Is one function of a proxy to screen application requests that go across a firewall placed between an internal network and an external or public network?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
79
Do routers maintain information about network station addresses and network status in databases?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck
80
TCP (and UDP) ____________________ software may be used to simply collect information about a target, without the target's knowledge; it may be used to gain access to a system, or it may be used to crash a system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 86 في هذه المجموعة.
فتح الحزمة
k this deck








