Deck 2: Storage Networking Management and Administration
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/80
العب
ملء الشاشة (f)
Deck 2: Storage Networking Management and Administration
1
You have a new storage array with the following drive types: 1. SAS (6 Gbps) 2. SSD 3. SATA (6 Gbps) 4. FC(4Gbps) You need to decide which drive type to use based on speed, cost, and drive availability for your Tier 1 storage. Which type of drive would you choose?
A) SSD
B) SAS
C) SATA
D) FC
A) SSD
B) SAS
C) SATA
D) FC
B
2
A line of business (LOB) executive informs you that a new application requires 99.999% (five 9s) of up-time from both planned and unplanned outages before a service level objective (SLO) will be breached. What is the amount of permissible downtown per week?
A) 20.16 minutes
B) .605 seconds
C) 5.04 minutes
D) 6.06 seconds
A) 20.16 minutes
B) .605 seconds
C) 5.04 minutes
D) 6.06 seconds
D
3
You have received an emergency call from the night shift after they attempted to merge three small SANs in the engineering department. Once completed, all devices in SANs A and B communicate with one another but SAN C could not communicate with either of the other SANs because the fabric has become segmented. Which statement is correct?
A) The port is isolated until a fabric rebuild occurs,
B) The port is isolated until a fabric re-configuration occurs.
C) The system administrator must manually correct the issue that caused segmentation (port isolation) and then start the Build Fabric (BF) process.
D) The system administrator must manually correct the issue that caused port isolation (segmentation) and then start the Reconfiguration Fabric (RCF) process.
A) The port is isolated until a fabric rebuild occurs,
B) The port is isolated until a fabric re-configuration occurs.
C) The system administrator must manually correct the issue that caused segmentation (port isolation) and then start the Build Fabric (BF) process.
D) The system administrator must manually correct the issue that caused port isolation (segmentation) and then start the Reconfiguration Fabric (RCF) process.
D
4
Click the Exhibit button. 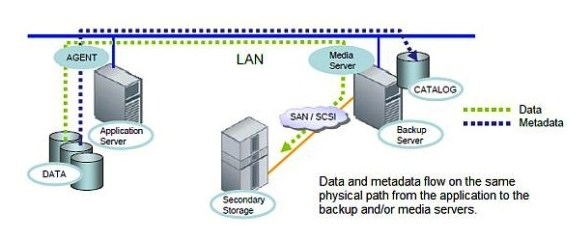 Referring to the exhibit, which backup type is represented?
Referring to the exhibit, which backup type is represented?
A) Server-free backup
B) Cloud backup
C) LAN-free backup
D) LAN backup
 Referring to the exhibit, which backup type is represented?
Referring to the exhibit, which backup type is represented?A) Server-free backup
B) Cloud backup
C) LAN-free backup
D) LAN backup

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
5
Only one of many servers has poor performance within an enterprise SAN. The server administrator has found high disk timeout values without a decrease in throughput. The server has multiple paths to the storage system but only one path is active at this time. What should the storage administrator monitor to assist with troubleshooting?
A) Number of errors on the active storage port
B) IOPS on the active storage port
C) MBps on the active storage port
D) Buffer-to-buffer utilization by the active storage port
A) Number of errors on the active storage port
B) IOPS on the active storage port
C) MBps on the active storage port
D) Buffer-to-buffer utilization by the active storage port

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
6
What should be considered when implementing remote replication of storage?
A) The IOPS requirements at the primary site
B) The geographical location of the primary site
C) The availability of communication links
D) The availability of server hardware at the secondary site
A) The IOPS requirements at the primary site
B) The geographical location of the primary site
C) The availability of communication links
D) The availability of server hardware at the secondary site

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
7
A company has a storage subsystem that supports a variety of replication options. They have purchased an identical array and placed it at a secondary site 4,200 km away and want to keep the two arrays as closely synchronized as possible. Which solution should be chosen?
A) Asynchronous replication is the only replication option for distances of this length.
B) Synchronous replication is the only replication option for distances over 4,000 km.
C) Snapshots allow for data to be quickly captured, copied, and mounted from one storage array to another and is the ideal solution for all distances.
D) Synchronous replication will keep the arrays in the closest sync and is ideal for short distances such as 4,200 km.
A) Asynchronous replication is the only replication option for distances of this length.
B) Synchronous replication is the only replication option for distances over 4,000 km.
C) Snapshots allow for data to be quickly captured, copied, and mounted from one storage array to another and is the ideal solution for all distances.
D) Synchronous replication will keep the arrays in the closest sync and is ideal for short distances such as 4,200 km.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
8
You have been hired as a consultant to help resolve boot-from-SAN server reboots. The company has hosts, storage devices, and tape drives in the same zones. A large number of RSCNs are generated during the backup window. What is the cause of the problem?
A) Tape drives are more sensitive to RSCNs than hosts or disk storage devices.
B) Storage devices and tape drives are configured within the same zone.
C) Storage devices are more sensitive to RSCNs than hosts or tape storage devices.
D) Most SAN switches do not support having both disk and tape frames flowing over the same switch ports at the same time.
A) Tape drives are more sensitive to RSCNs than hosts or disk storage devices.
B) Storage devices and tape drives are configured within the same zone.
C) Storage devices are more sensitive to RSCNs than hosts or tape storage devices.
D) Most SAN switches do not support having both disk and tape frames flowing over the same switch ports at the same time.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
9
Which standard would be used to increase interoperability between solutions of different cloud storage providers?
A) SES
B) CDMI
C) CWDM
D) DWDM
A) SES
B) CDMI
C) CWDM
D) DWDM

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
10
Click the Exhibit button. 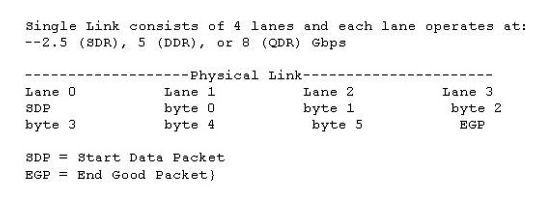 The physical interface shown in the exhibit is taken from which transport protocol?
The physical interface shown in the exhibit is taken from which transport protocol?
A) Ethernet
B) FCP
C) FCoE
D) InfiniBand
 The physical interface shown in the exhibit is taken from which transport protocol?
The physical interface shown in the exhibit is taken from which transport protocol?A) Ethernet
B) FCP
C) FCoE
D) InfiniBand

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
11
You are designing a security solution for a storage array which stores customer credit card information. Data on the storage array must be encrypted and if necessary, you want to be able to revoke access to data on demand. In addition to encryption, which solution would allow you to do this in a secure and automated fashion?
A) Use a manual record deletion solution.
B) Physically destroy hard drives holding the data
C) Store data indefinitely.
D) Use the key management solution.
A) Use a manual record deletion solution.
B) Physically destroy hard drives holding the data
C) Store data indefinitely.
D) Use the key management solution.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
12
Five out of 4S servers using one particular enterprise storage system are experiencing performance degradation during normal working hours. All 48 servers have similar workload characteristics. There are multiple disk groups that make up your enterprise storage. What should be monitored to determine the root cause?
A) IOPS per RAID array
B) Cache read hit ratio
C) Traffic levels on the SAN switches
D) Clone sessions
A) IOPS per RAID array
B) Cache read hit ratio
C) Traffic levels on the SAN switches
D) Clone sessions

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
13
Your company's Service Level Agreement (SLA) requires that no more then one hour's worth of data be lost in case of a system crash. The data must also be restored within 10 hours. Which two RTO/RPO combinations meet the SLA? (Choose two.)
A) RTO 1 hour, RPO 10 hours
B) RTO 10 hours, RPO 1 hour
C) RTO 9 hours, RPO 1 hour
D) RTO 1 hour, RPO 9 hours
A) RTO 1 hour, RPO 10 hours
B) RTO 10 hours, RPO 1 hour
C) RTO 9 hours, RPO 1 hour
D) RTO 1 hour, RPO 9 hours

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
14
Which type of a backup changes the archive bit?
A) Full
B) Differential
C) Incremental
D) Block-level
A) Full
B) Differential
C) Incremental
D) Block-level

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
15
A storage subsystems Web browser management interface reports that the subsystem has become degraded and remotely opens a service request with the vendor. Your vendors level three storage support engineer wants to remotely access your storage subsystem for troubleshooting. What is a SNIA Storage Security Best Current Practices solution?
A) Open firewall ports to allow the vendor's support engineer to access the Web browser management interface.
B) Provide the vendor's support engineer with a temporary user ID that has sudo access to become a super user on the storage subsystem; this ensures an audit trail for all remote support activities.
C) Provide the vendor's support engineer with a shared remote control session where you can monitor what the support engineer is doing while troubleshooting the subsystem without needing to share credentials.
D) Provide a temporary user ID to allow the vendor's support engineer to access the Web browser management interface remotely over HTTP/TLS.
A) Open firewall ports to allow the vendor's support engineer to access the Web browser management interface.
B) Provide the vendor's support engineer with a temporary user ID that has sudo access to become a super user on the storage subsystem; this ensures an audit trail for all remote support activities.
C) Provide the vendor's support engineer with a shared remote control session where you can monitor what the support engineer is doing while troubleshooting the subsystem without needing to share credentials.
D) Provide a temporary user ID to allow the vendor's support engineer to access the Web browser management interface remotely over HTTP/TLS.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
16
You have a server which is booting from a SAN. After adding new SAN storage to a host, the host will not boot from the SAN. What will resolve this problem?
A) LUN masking
B) Persistent binding
C) Trunking
D) Multiplex binding
A) LUN masking
B) Persistent binding
C) Trunking
D) Multiplex binding

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
17
You want to prevent unauthorized switches from connecting to your company's fabrics. What should you do?
A) Configure ACLs.
B) Implement CHAP.
C) Deploy FC-SP policy.
D) Implement binding lists.
A) Configure ACLs.
B) Implement CHAP.
C) Deploy FC-SP policy.
D) Implement binding lists.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
18
A company has a storage subsystem that supports a variety of replication options. They have purchased an identical array and placed it at a secondary site 50 km away and will provide the shortest RPO. Which statement is correct?
A) Asynchronous replication is the only replication option for distances over 50 km.
B) Synchronous replication is the only replication option for distances over 50 km.
C) Snapshots allow for data to be quickly captured, copied, and mounted from one storage array to another and is the ideal solution for all distances.
D) Synchronous replication will keep the arrays closely synchronized and is ideal for short distances.
A) Asynchronous replication is the only replication option for distances over 50 km.
B) Synchronous replication is the only replication option for distances over 50 km.
C) Snapshots allow for data to be quickly captured, copied, and mounted from one storage array to another and is the ideal solution for all distances.
D) Synchronous replication will keep the arrays closely synchronized and is ideal for short distances.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
19
A new server needs to start from LUN 1 instead of LUN 0. Which HBA setting must be configured?
A) Selectable Boot
B) Persistent Binding
C) Enable Target Reset
D) LUNs per Target
A) Selectable Boot
B) Persistent Binding
C) Enable Target Reset
D) LUNs per Target

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
20
The CIO would like to segregate management device IP network traffic from server IP network traffic within the data center to limit potential security threats. What would be used to accomplish this?
A) IPsec
B) Firewall
C) VLANs
D) PKI
A) IPsec
B) Firewall
C) VLANs
D) PKI

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
21
Your company uses a cryptographic key system to encrypt tapes. After several years of use and thousands of tapes shipped to off-site locations, an IT audit reveals that encryption keys have been inadvertently stored as ciphertext on file shares to which everyone in the company has read permissions. Which response reflects industry best practice?
A) All data encrypted with the keys exposed as ciphertext should be considered safe.
B) All data encrypted with the keys exposed as ciphertext and not yet sent off-site as an encrypted tape should be re-keyed (decrypted and re-encrypted using a new key).
C) All data encrypted with the keys exposed as ciphertext should be re-keyed (decrypted and re-encrypted using a new key).
D) All data encrypted with the keys exposed as ciphertext should be considered safe as ciphertext is very difficult to use.
A) All data encrypted with the keys exposed as ciphertext should be considered safe.
B) All data encrypted with the keys exposed as ciphertext and not yet sent off-site as an encrypted tape should be re-keyed (decrypted and re-encrypted using a new key).
C) All data encrypted with the keys exposed as ciphertext should be re-keyed (decrypted and re-encrypted using a new key).
D) All data encrypted with the keys exposed as ciphertext should be considered safe as ciphertext is very difficult to use.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
22
You have been asked to secure your FC switches in the data center. Unsecure protocols have already been disabled but you also need to restrict access to the switches only from specific IP addresses located on the production network. What should be used?
A) Roles
B) VSAN
C) ACL
D) Zone
A) Roles
B) VSAN
C) ACL
D) Zone

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
23
Your company asks you to increase restore speeds. What should you do?
A) Upgrade existing LTO3 drives to LTO5 drives to take advantage of faster read/write speeds and larger tape cartridge sizes.
B) Add a mirrored disk based backup target that can be used for backups that support point-in-time recovery.
C) Attach the existing tape libraries to a backup server with local drives configured with RAID 5.
D) Attach a JBOD drive array to the backup media server to improve the read performance of the backup catalog.
A) Upgrade existing LTO3 drives to LTO5 drives to take advantage of faster read/write speeds and larger tape cartridge sizes.
B) Add a mirrored disk based backup target that can be used for backups that support point-in-time recovery.
C) Attach the existing tape libraries to a backup server with local drives configured with RAID 5.
D) Attach a JBOD drive array to the backup media server to improve the read performance of the backup catalog.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
24
You have been asked to create a LUN on a storage array that is comprised of 7,200 rpm SATA drives. Each drive is rated at 100 IOPS. The LUN should provide a minimum of 1100 IOPS and withstand multiple drive failures using the least number of drives. How many drives and which RAID level should you use to create this LUN?
A) 11 drives and RAID 0
B) 12 drives and RAID 5
C) 13 drives and RAID 6
D) 22 drives and RAID 1
A) 11 drives and RAID 0
B) 12 drives and RAID 5
C) 13 drives and RAID 6
D) 22 drives and RAID 1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
25
You have completed installing your FC SAN. When everything is powered on, numerous devices are not available. You need to verify that the devices appear within the FC fabric by accessing the appropriate FC service that provides a list of devices and their respective function. Which server within the Fibre Channel fabric would be used to do this?
A) Fabric Login server
B) Name server
C) Management server
D) Fabric Controller
A) Fabric Login server
B) Name server
C) Management server
D) Fabric Controller

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
26
After the storage administrator merged two multi-vendor FC SANs, an error indicates that two ports have become isolated causing a segmentation to exist in the fabric. Which two events would cause this? (Choose two.)
A) Overlapping zones
B) Different port names
C) Unsupported routing protocols
D) Different link speeds
A) Overlapping zones
B) Different port names
C) Unsupported routing protocols
D) Different link speeds

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
27
Click the Exhibit button. 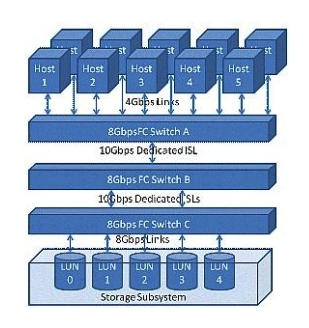 The customer configuration shown in the exhibit is not meeting the throughput needs of a newly installed application. The application's I/O profile consists of 100% 4 kilobyte reads and all servers require a sustained bandwidth of 150 MBps. Which location within the configuration presents a performance bottleneck?
The customer configuration shown in the exhibit is not meeting the throughput needs of a newly installed application. The application's I/O profile consists of 100% 4 kilobyte reads and all servers require a sustained bandwidth of 150 MBps. Which location within the configuration presents a performance bottleneck?
A) Links between hosts and Switch A
B) Inter-switch link between Switch A and Switch B
C) Inter-switch link between Switch B and Switch C
D) Links between Switch C and storage subsystem
 The customer configuration shown in the exhibit is not meeting the throughput needs of a newly installed application. The application's I/O profile consists of 100% 4 kilobyte reads and all servers require a sustained bandwidth of 150 MBps. Which location within the configuration presents a performance bottleneck?
The customer configuration shown in the exhibit is not meeting the throughput needs of a newly installed application. The application's I/O profile consists of 100% 4 kilobyte reads and all servers require a sustained bandwidth of 150 MBps. Which location within the configuration presents a performance bottleneck?A) Links between hosts and Switch A
B) Inter-switch link between Switch A and Switch B
C) Inter-switch link between Switch B and Switch C
D) Links between Switch C and storage subsystem

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
28
When troubleshooting an issue on a host, you discover that the existing file system partition has been corrupted after you provisioned a LUN to another host connected to the same FC fabric. What is the cause of this problem?
A) Incorrect zoning
B) Incorrect LUN masking
C) Incorrect multipathing policy
D) Incorrect LUN size
A) Incorrect zoning
B) Incorrect LUN masking
C) Incorrect multipathing policy
D) Incorrect LUN size

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
29
A security audit reveals deficiencies in your company's FC zoning practices. Your manager asks you to make a recommendation to implement the most secure FC zoning possible. Your company is using switches from a single vendor. What do you recommend?
A) All zones should use frame-based hardware enforcement using pWWN identification exclusively for all configurations.
B) All zones should use software-based enforcement using pWWN identification exclusively for all configurations.
C) All zones should use frame-based hardware enforcement using destination port identification exclusively for all configurations.
D) All zones should use software-based enforcement using destination port identification exclusively for all configurations.
A) All zones should use frame-based hardware enforcement using pWWN identification exclusively for all configurations.
B) All zones should use software-based enforcement using pWWN identification exclusively for all configurations.
C) All zones should use frame-based hardware enforcement using destination port identification exclusively for all configurations.
D) All zones should use software-based enforcement using destination port identification exclusively for all configurations.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
30
Click the Exhibit button. 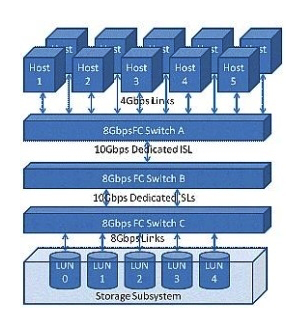 The customer application requires a 50/50 R/W ratio with 100 MBps throughput requirements for each direction of the link. The application servers will simultaneously sustain these data rates across all LUNs in parallel. Referring to the exhibit, where will the oversubscribed link(s) occur?
The customer application requires a 50/50 R/W ratio with 100 MBps throughput requirements for each direction of the link. The application servers will simultaneously sustain these data rates across all LUNs in parallel. Referring to the exhibit, where will the oversubscribed link(s) occur?
A) Links between hosts and Switch A
B) Inter-switch link between Switch A and Switch B
C) Inter-switch link between Switch B and Switch C
D) Links between Switch C and storage
 The customer application requires a 50/50 R/W ratio with 100 MBps throughput requirements for each direction of the link. The application servers will simultaneously sustain these data rates across all LUNs in parallel. Referring to the exhibit, where will the oversubscribed link(s) occur?
The customer application requires a 50/50 R/W ratio with 100 MBps throughput requirements for each direction of the link. The application servers will simultaneously sustain these data rates across all LUNs in parallel. Referring to the exhibit, where will the oversubscribed link(s) occur?A) Links between hosts and Switch A
B) Inter-switch link between Switch A and Switch B
C) Inter-switch link between Switch B and Switch C
D) Links between Switch C and storage

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
31
Click the Exhibit button. 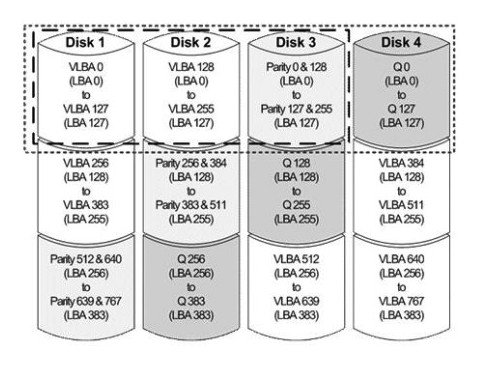 Which RAID level is shown in the exhibit?
Which RAID level is shown in the exhibit?
A) RAID 4
B) RAID 5
C) RAID 0
D) RAID 6
 Which RAID level is shown in the exhibit?
Which RAID level is shown in the exhibit?A) RAID 4
B) RAID 5
C) RAID 0
D) RAID 6

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
32
A storage networking device has experienced a failure that has "phone home" and opened a service request for a part that can be a customer replaceable unit (CRU). Your support vendor has dispatched a replacement part using a secure courier service. According to SNIA Storage Security Best Current Practices, which statement is correct about the repair process?
A) The support vendor's parts courier should have access to the secure data center to facilitate an unattended part swap-out bringing the fastest resolution to the failure.
B) The data center operations staff should accept the part and place it in a secure staging area awaiting a qualified administrator to perform the installation.
C) Any data center operator on-site should perform the part installation bringing the fastest resolution to the failure.
D) The support vendors parts courier should coordinate with a field service staff person from your support vender; both should have access to the secure data center to facilitate an unattended part swap-out.
A) The support vendor's parts courier should have access to the secure data center to facilitate an unattended part swap-out bringing the fastest resolution to the failure.
B) The data center operations staff should accept the part and place it in a secure staging area awaiting a qualified administrator to perform the installation.
C) Any data center operator on-site should perform the part installation bringing the fastest resolution to the failure.
D) The support vendors parts courier should coordinate with a field service staff person from your support vender; both should have access to the secure data center to facilitate an unattended part swap-out.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
33
What is the storage protocol used between initiators and targets connected to an FCoE fabric?
A) SATA
B) SCSI
C) SAS
D) FCoE
A) SATA
B) SCSI
C) SAS
D) FCoE

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
34
Some business critical database applications have been suffering from slowly increasing performance issues with one enterprise SAN-attached storage system. In particular, the applications are showing higher than normal read response times. What should the storage administrator monitor to determine the root cause?
A) Storage utilization
B) Available free space
C) Write response time
D) Cache hit rate
A) Storage utilization
B) Available free space
C) Write response time
D) Cache hit rate

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
35
You receive a ticket from a database group which is complaining about slow access to storage on only one particular server, as compared to other servers in an active-active cluster. You verify zoning and LUN masking which are fine. On the FC switch, you verify link speed, errors, and throughput for the FC switch ports used by this server. There are no errors on the ports and the link speed is the same as on the switch ports used by other servers in the cluster. You notice that on one port on the FC switch used by this server, that there is no throughput at all. What is causing the problem?
A) The switch has obsolete firmware.
B) There are too many ports used on the FC switch.
C) Multipathing was not configured for load-balancing.
D) The switch is over-subscribed.
A) The switch has obsolete firmware.
B) There are too many ports used on the FC switch.
C) Multipathing was not configured for load-balancing.
D) The switch is over-subscribed.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
36
The enterprise storage system has the "call home" feature enabled and configured. However, the storage administrator has been told that "call home" is not working. Which two actions should you perform? (Choose two.)
A) Verify SMTP settings.
B) Verify SNMP thresholds.
C) Verify firewall rules.
D) Verify the SMI-S configuration.
E) Verify VSAN configuration.
A) Verify SMTP settings.
B) Verify SNMP thresholds.
C) Verify firewall rules.
D) Verify the SMI-S configuration.
E) Verify VSAN configuration.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
37
A server with a dual-ported HBA loses access to storage during switch SFP replacement. You want to prevent this from happening in the future. Which action should you perform?
A) Use zoning
B) Enable trunking.
C) Use LUN masking
D) Configure multipathing
A) Use zoning
B) Enable trunking.
C) Use LUN masking
D) Configure multipathing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
38
Which protocol commonly uses CNA devices?
A) FCIP
B) iFCP
C) FCoE
D) FCR
A) FCIP
B) iFCP
C) FCoE
D) FCR

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
39
Click the Exhibit button. 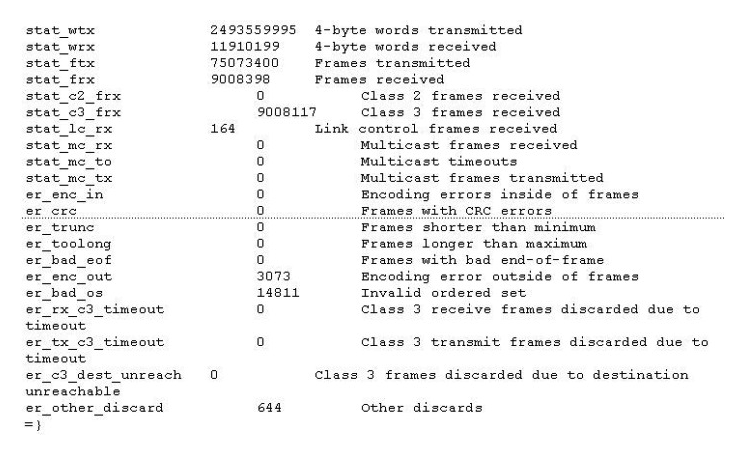 Referring to the exhibit, which three switch indicators will help you to determine the stability of a link? (Choose three.)
Referring to the exhibit, which three switch indicators will help you to determine the stability of a link? (Choose three.)
A) er_crc
B) er_toolong
C) er_enc_in
D) er_bad_eof
E) er_trunk
 Referring to the exhibit, which three switch indicators will help you to determine the stability of a link? (Choose three.)
Referring to the exhibit, which three switch indicators will help you to determine the stability of a link? (Choose three.)A) er_crc
B) er_toolong
C) er_enc_in
D) er_bad_eof
E) er_trunk

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
40
Which two high availability elements can be achieved by remote storage replication? (Choose two.)
A) Recoverability
B) Fault tolerance
C) Robustness
D) Redundancy
E) Serviceability
A) Recoverability
B) Fault tolerance
C) Robustness
D) Redundancy
E) Serviceability

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
41
You are asked to secure 2.5 PB of data so that in case of a failed drive replacement, data on the drives is not usable. Which data protection method should be used in this case?
A) Encrypting data-in-flight
B) Encrypting data-at-rest
C) Password protect each file
D) Use file permissions
A) Encrypting data-in-flight
B) Encrypting data-at-rest
C) Password protect each file
D) Use file permissions

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
42
A company needs to replicate a database from its main office to a disaster recovery site 3,000 km away with a five minute recovery point objective. Which type of replication should the company use to replicate the data?
A) Synchronous
B) Asynchronous
C) Multi-synchronous
D) Local replication
A) Synchronous
B) Asynchronous
C) Multi-synchronous
D) Local replication

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
43
You have been asked to implement a remote data replication scheme. The current data center is mostly constructed of FC components and the corporation is highly invested in the technology. The remote data center needs a synchronous replication solution. What will accomplish this goal?
A) iSCSI
B) NAS
C) FCIP
D) FCoE
A) iSCSI
B) NAS
C) FCIP
D) FCoE

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
44
Which process allows for the reduction of disk space consumption on a shared storage of OS images used by 200 users?
A) Thin provisioning
B) Deduplication
C) Synchronous replication
D) Defragmentation
A) Thin provisioning
B) Deduplication
C) Synchronous replication
D) Defragmentation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
45
You have two new FC switches from the same vendor and want to connect them together. You have ensured that the domain IDs are unique, switch names are unique, and the firmware levels are identical. When you connect the ISL cables from one switch to the other, the fabric does not merge. What should be confirmed?
A) Ensure the ISL ports are E_Ports.
B) Ensure the ISL ports are B_Ports.
C) Ensure the ISL ports are F_Ports.
D) Ensure the ISL ports are N_Ports.
A) Ensure the ISL ports are E_Ports.
B) Ensure the ISL ports are B_Ports.
C) Ensure the ISL ports are F_Ports.
D) Ensure the ISL ports are N_Ports.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
46
Your organization operates in a regulated environment and contracts with a service provider to manage tape backup media for highly confidential, secure data. Using SNIA Storage Security Best Practices, which two statements are correct? (Choose two.)
A) Tape backup media is stored in a secure, temperature controlled vault.
B) The service provider keeps unencrypted backup media locked during transport.
C) All removable media is encrypted and backup media locked during transport.
D) The customer manages the chain of custody.
A) Tape backup media is stored in a secure, temperature controlled vault.
B) The service provider keeps unencrypted backup media locked during transport.
C) All removable media is encrypted and backup media locked during transport.
D) The customer manages the chain of custody.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
47
You need to merge two existing FC fabrics. After connecting the ISL to join the fabrics, numerous switches segment. What should be done to prevent the segmentation?
A) Physically separate the switches to opposite sides of the data center.
B) Move business critical applications to clusters.
C) Increase the frequency of snapshots for critical data.
D) Assign domain IDs which are unique across both fabrics.
A) Physically separate the switches to opposite sides of the data center.
B) Move business critical applications to clusters.
C) Increase the frequency of snapshots for critical data.
D) Assign domain IDs which are unique across both fabrics.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
48
Click the Exhibit button. 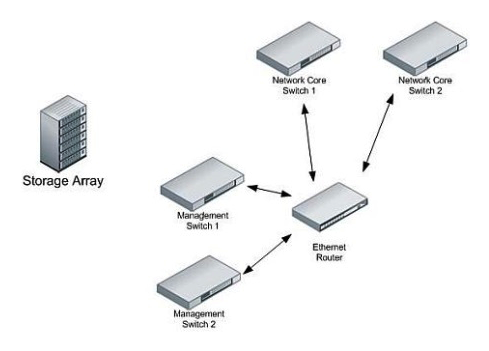 Your company has purchased a new storage array that has dual management access network ports. You need to connect the array and provide maximum redundancy without affecting production traffic. Referring to the exhibit, where should the ports be attached?
Your company has purchased a new storage array that has dual management access network ports. You need to connect the array and provide maximum redundancy without affecting production traffic. Referring to the exhibit, where should the ports be attached?
A) Cable one management access network port into management switch 1 and the other port into management switch 2.
B) Cable both management access network ports into management switch 2.
C) Cable one management access network port into core switch 1 and the other into core switch 2.
D) Cable both management access network ports into management switch 1.
 Your company has purchased a new storage array that has dual management access network ports. You need to connect the array and provide maximum redundancy without affecting production traffic. Referring to the exhibit, where should the ports be attached?
Your company has purchased a new storage array that has dual management access network ports. You need to connect the array and provide maximum redundancy without affecting production traffic. Referring to the exhibit, where should the ports be attached?A) Cable one management access network port into management switch 1 and the other port into management switch 2.
B) Cable both management access network ports into management switch 2.
C) Cable one management access network port into core switch 1 and the other into core switch 2.
D) Cable both management access network ports into management switch 1.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
49
A server has lost half of its paths to its LUN on a storage system. The help desk determines that one of the two HBAs was just replaced. The SAN administrator has modified the zoning with the new WWPN of the replacement HBA port, but the missing paths have still not recovered. Which action would you perform next?
A) Rescan disks on the server.
B) Reconfigure persistent binding on the server.
C) Reboot the server.
D) Modify the host definitions for LUN masking on the storage system.
A) Rescan disks on the server.
B) Reconfigure persistent binding on the server.
C) Reboot the server.
D) Modify the host definitions for LUN masking on the storage system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
50
You are installing an OLTP application on a new server. The I/O profile of the application consists of 100% random read operations of 8 kilobyte transfers. You need to determine which HBA to use in your application to accommodate 50,000 IOPS. What is the minimum FC link speed that will satisfy the application's requirements?
A) 1 Gbps
B) 2 Gbps
C) 4 Gbps
D) 8 Gbps
A) 1 Gbps
B) 2 Gbps
C) 4 Gbps
D) 8 Gbps

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
51
You have replaced an HBA and are trying to add it to an existing zone using the FC switch GUI interface. You are unable to do so. Why is this happening?
A) The OS login has not occurred.
B) The Web login has not occurred.
C) The fabric login has not occurred.
D) The port login has occurred.
A) The OS login has not occurred.
B) The Web login has not occurred.
C) The fabric login has not occurred.
D) The port login has occurred.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
52
After provisioning a new LUN to a host, new storage cannot be detected on the host. Which three actions should be performed to troubleshoot this problem? (Choose three.)
A) Scan memory on a host.
B) Scan for new storage on the host,
C) Verify that LUN mapping is correct.
D) Verify that zoning on the FC switch is correct.
E) Verify that the size of memory pages and block size is the same.
A) Scan memory on a host.
B) Scan for new storage on the host,
C) Verify that LUN mapping is correct.
D) Verify that zoning on the FC switch is correct.
E) Verify that the size of memory pages and block size is the same.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
53
You determine that throughput between a server and an FC storage array is lower than expected. Your privileges only allow you to change the configuration of the HBA on the server. Which configuration setting can you change to increase throughput?
A) Queue length
B) Queue depth
C) Topology
D) Class 1 service
A) Queue length
B) Queue depth
C) Topology
D) Class 1 service

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
54
You need to implement a solution for a high transaction database which should have the lowest write latency as possible and still be able to sustain a failure of a single drive in a RAID group. Which type of RAID you would use?
A) RAID 0
B) RAID 5
C) RAID 6
D) RAID 10
A) RAID 0
B) RAID 5
C) RAID 6
D) RAID 10

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
55
You have twelve 500 GB drives and you need to provide two LUNs using RAID 6 protection for a customer. What will be the size of each LUN?
A) 1.5 TB
B) 1.75 TB
C) 2 TB
D) 2.25 TB
A) 1.5 TB
B) 1.75 TB
C) 2 TB
D) 2.25 TB

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
56
Click the Exhibit button. 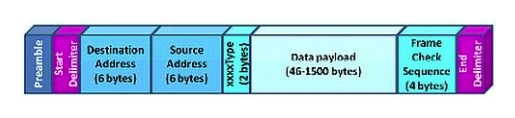 Which protocol is represented in the exhibit?
Which protocol is represented in the exhibit?
A) iSCSI
B) IPv6 Ethernet
C) IPv4 Ethernet
D) FCoE
 Which protocol is represented in the exhibit?
Which protocol is represented in the exhibit?A) iSCSI
B) IPv6 Ethernet
C) IPv4 Ethernet
D) FCoE

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
57
You are provisioning storage to a host with multipathing software installed and correctly configured. You discover that there are four paths to LUNs instead of the expected eight paths. Why does this happen?
A) Incorrect zoning
B) Incorrect multipathing policy
C) Incorrect LUN masking
D) Incorrect LUN size
A) Incorrect zoning
B) Incorrect multipathing policy
C) Incorrect LUN masking
D) Incorrect LUN size

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
58
Your company does a full backup on Sunday night and incremental backups from Monday through Saturday at midnight. The full backup requires two tapes and each incremental backup requires one tape. There is a system failure Wednesday morning. How many tapes will be used to restore to the most current backup?
A) 1
B) 3
C) 4
D) 8
A) 1
B) 3
C) 4
D) 8

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
59
What are two concerns when trying to migrate from one cloud storage provider to another one? (Choose two.)
A) Stability
B) Accessibility
C) Different drive types
D) CAN protocol compatibility
A) Stability
B) Accessibility
C) Different drive types
D) CAN protocol compatibility

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
60
You have determined that the root cause of your problem is related to invalid characters being intermittently transmitted on your 4 Gb FC link. What describes this condition?
A) Disparity error character
B) Link hardware cannot detect k28.3 characters
C) Link hardware cannot detect k28.5 characters
D) Character does not fit in allowed 8b/10b codes or special characters
A) Disparity error character
B) Link hardware cannot detect k28.3 characters
C) Link hardware cannot detect k28.5 characters
D) Character does not fit in allowed 8b/10b codes or special characters

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
61
Click the Exhibit button.  Referring to the configuration shown in the exhibit, when will the servers oversubscribe the connections between the storage array and the switch?
Referring to the configuration shown in the exhibit, when will the servers oversubscribe the connections between the storage array and the switch?
A) When the 6th server is added to the configuration
B) When the 7th server is added to the configuration
C) When the 8th server is added to the configuration
D) When the 9th server is added to the configuration
 Referring to the configuration shown in the exhibit, when will the servers oversubscribe the connections between the storage array and the switch?
Referring to the configuration shown in the exhibit, when will the servers oversubscribe the connections between the storage array and the switch?A) When the 6th server is added to the configuration
B) When the 7th server is added to the configuration
C) When the 8th server is added to the configuration
D) When the 9th server is added to the configuration

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
62
Click the Exhibit button. 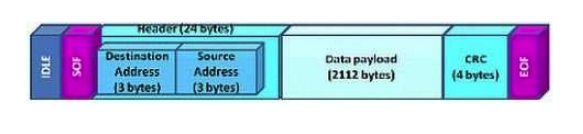 Which protocol is represented by the frame shown in the exhibit?
Which protocol is represented by the frame shown in the exhibit?
A) FCoE
B) iSCSI
C) Ethernet
D) Fibre Channel
 Which protocol is represented by the frame shown in the exhibit?
Which protocol is represented by the frame shown in the exhibit?A) FCoE
B) iSCSI
C) Ethernet
D) Fibre Channel

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
63
You are asked to secure management access to your SAN devices. Which three actions should you perform? (Choose three.)
A) Disable all unused protocols.
B) Limit network access.
C) Create individual access accounts.
D) Write to the syslog server.
E) Enable NTP synchronization.
A) Disable all unused protocols.
B) Limit network access.
C) Create individual access accounts.
D) Write to the syslog server.
E) Enable NTP synchronization.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
64
Which storage related offering serves as intermediaries to multiple cloud storage providers?
A) Cloud storage provider
B) Cloud storage broker
C) Cloud storage gateway
D) Cloud storage shifting
A) Cloud storage provider
B) Cloud storage broker
C) Cloud storage gateway
D) Cloud storage shifting

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
65
A small business with an IP SAN and NAS storage is experiencing slow response times on the servers which have NAS storage resources. Which two should the storage administrator monitor to determine the root cause? (Choose two.)
A) Latency per NAS port
B) IOPS per NAS port
C) Link speed per NAS port
D) MBps per NAS port
E) I question the question
A) Latency per NAS port
B) IOPS per NAS port
C) Link speed per NAS port
D) MBps per NAS port
E) I question the question

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
66
A solution architect needs to know how your switches enforce zoning. The enforcement method and identification type being used in your current FC switches must provide the highest level of security. Which zoning enforcement should you use?
A) Session-based without hardware support
B) Frame-based and hardware support
C) Software-based with hardware support
D) Frame-based and software enforced
A) Session-based without hardware support
B) Frame-based and hardware support
C) Software-based with hardware support
D) Frame-based and software enforced

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
67
Two different departments have funded the purchase of a new director-class switch. Each department wants to have control of the fabric. Two logical switches will need to be created, each with its own set of administrators. Which feature must be enabled on the switch to do this?
A) ACL
B) Virtual SAN
C) Virtual LAN
D) Virtual Fabrics
A) ACL
B) Virtual SAN
C) Virtual LAN
D) Virtual Fabrics

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
68
You want to visibly verify FC port initialization by reading an analyzer trace. Your objective is to find the frames associated with the initialization protocol to ensure that the FC device is operating correctly during the login process, to be recognized as part of the switched fabric, and appear in a directory of attached FC devices. What must all Fibre Channel devices do to accomplish this?
A) Log in using the Name server.
B) Log in using the Fabric Controller.
C) Log in using the Management server.
D) Log in using the Fabric Login server.
A) Log in using the Name server.
B) Log in using the Fabric Controller.
C) Log in using the Management server.
D) Log in using the Fabric Login server.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
69
You are using asynchronous storage replication to protect your critical database server. There are no replication agents installed on the database server. After a disaster, you are unable to bring up the database at the DR site. What is the cause?
A) The database requires replication from a second storage array.
B) The database requires synchronous storage replication.
C) Two copies of databases are required at the DR site to be able to replay transaction logs.
D) An installed agent is required for the database to be quiesce and replicated in crash-consistent state.
A) The database requires replication from a second storage array.
B) The database requires synchronous storage replication.
C) Two copies of databases are required at the DR site to be able to replay transaction logs.
D) An installed agent is required for the database to be quiesce and replicated in crash-consistent state.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
70
A number of servers are experiencing slower than expected performance. Analyzing the server, switch, and storage logs do not indicate any issues. You have been asked by the customer to address this issue. What will improve performance?
A) Increase the current queue depth setting from 1.
B) Change the frame size from 2148 bytes,
C) Decrease the buffer-to-buffer credits setting.
D) Enable write caching functionality for the device driver.
A) Increase the current queue depth setting from 1.
B) Change the frame size from 2148 bytes,
C) Decrease the buffer-to-buffer credits setting.
D) Enable write caching functionality for the device driver.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
71
The latest storage utilization report shows that 80% of the current 500 TB of enterprise storage is allocated. The storage administrator must specify the amount of additional storage needed for local copies for approximately half of the active storage. How much additional storage should the administrator request?
A) 400 TB
B) 300 TB
C) 200 TB
D) 100 TB
A) 400 TB
B) 300 TB
C) 200 TB
D) 100 TB

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
72
You are asked to set up a server to boot from a SAN. Which setting on the HBA needs to be configured?
A) Change the queue depth value.
B) Set Enable BIOS.
C) Enable Persistent Bindings.
D) Set Enable Target Rescan.
A) Change the queue depth value.
B) Set Enable BIOS.
C) Enable Persistent Bindings.
D) Set Enable Target Rescan.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
73
A customer has upgraded all switches in their redundant fabrics during a single maintenance window. Shortly after the upgrades are completed on the core switches, all servers lose access to all SAN attached storage. What would have prevented this scenario?
A) High availability
B) Fault tolerance
C) Change or risk management
D) Clustered servers
A) High availability
B) Fault tolerance
C) Change or risk management
D) Clustered servers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
74
A company wants to implement a database which requires a storage subsystem with no more than 2 ms write latency and 1 ms read latency. Which type of drive would you use?
A) SATA
B) FC
C) SSD
D) ATA
A) SATA
B) FC
C) SSD
D) ATA

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
75
The storage administrator is required to create five zones within the FC SAN. Which Fibre Channel server would be used to do this?
A) Fabric Login server
B) Name server
C) Management server
D) Fabric Controller
A) Fabric Login server
B) Name server
C) Management server
D) Fabric Controller

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
76
Click the Exhibit button. 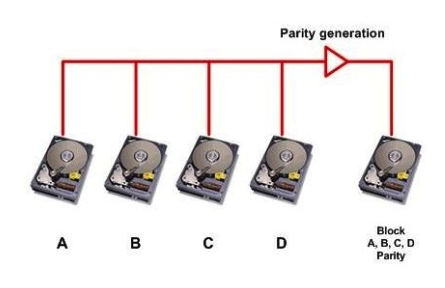 Referring to the exhibit, which RAID level is shown?
Referring to the exhibit, which RAID level is shown?
A) RAID 4
B) RAID 5
C) RAID 0
D) RAID 6
 Referring to the exhibit, which RAID level is shown?
Referring to the exhibit, which RAID level is shown?A) RAID 4
B) RAID 5
C) RAID 0
D) RAID 6

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
77
A business critical enterprise resource planning (ERP) system uses a central database at a company's primary data center. The company has built an out-of-region disaster recovery data center and intends to implement a standby ERP system with an eight hour RTO and 30 minute RPO. Which architectural approach to implement service continuity for the ERP database will meet the RTO and RPO targets?
A) Implement asynchronous replication of the ERP database, application, and middle tiers to ensure the ERP system is back online with less than 30 minutes of data loss within eight hours of an event.
B) Implement asynchronous replication of the ERP database, application, and middle tiers to ensure the ERP system is back online with less than eight hours of data loss within 30 minutes of an event.
C) Perform daily full database backups to tape and overnight ship the backup tape media from one data center to the other to ensure the ERP system is back online with less than eight hours of data loss within 30 minutes of an event.
D) Implement synchronous database replication and configure application logic to ensure transactions are identical in both data centers as the recovery objectives do not allow for any inflight data loss.
A) Implement asynchronous replication of the ERP database, application, and middle tiers to ensure the ERP system is back online with less than 30 minutes of data loss within eight hours of an event.
B) Implement asynchronous replication of the ERP database, application, and middle tiers to ensure the ERP system is back online with less than eight hours of data loss within 30 minutes of an event.
C) Perform daily full database backups to tape and overnight ship the backup tape media from one data center to the other to ensure the ERP system is back online with less than eight hours of data loss within 30 minutes of an event.
D) Implement synchronous database replication and configure application logic to ensure transactions are identical in both data centers as the recovery objectives do not allow for any inflight data loss.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
78
You need to add an iSCSI host and storage array to your environment. Your manager wants at least two options that allow all iSCSI initiators to query a central management server to locate the address of all iSCSI resources (e.g., iSCSI initiators, targets, switches, and management stations). Which two protocol methods would be used? (Choose two.)
A) Directory Name Service protocol (DNS)
B) Simple Network Management Protocol (SNMP)
C) Internet Storage Name Server protocol (iSNS)
D) Service Location Protocol (SLP)
A) Directory Name Service protocol (DNS)
B) Simple Network Management Protocol (SNMP)
C) Internet Storage Name Server protocol (iSNS)
D) Service Location Protocol (SLP)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
79
What is the maximum distance between two 8 Gb FC ports that can be connected using 50 µOM3 grade multimode fiber cable?
A) 500 meters
B) 300 meters
C) 250 meters
D) 150 meters
A) 500 meters
B) 300 meters
C) 250 meters
D) 150 meters

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck
80
Which type of storage replication is required, at a minimum, for a non-critical application?
A) Synchronous
B) Asynchronous
C) Semi-synchronous
D) Multi-synchronous
A) Synchronous
B) Asynchronous
C) Semi-synchronous
D) Multi-synchronous

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 80 في هذه المجموعة.
فتح الحزمة
k this deck








