Deck 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/65
العب
ملء الشاشة (f)
Deck 24: Securing Email with Cisco Email Security Appliance (300-720 SESA)
1
A network engineer must enforce access control using special tags, without re-engineering the network design. Which feature should be configured to achieve this in a scalable manner?
A) RBAC
B) dACL
C) SGT
D) VLAN
A) RBAC
B) dACL
C) SGT
D) VLAN
SGT
2
In which two ways can users and endpoints be classified for TrustSec? (Choose two.)
A) VLAN
B) dynamic
C) QoS
D) SGACL
E) SXP
A) VLAN
B) dynamic
C) QoS
D) SGACL
E) SXP
VLAN
SGACL
SGACL
3
What should be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
A) continue
B) pass
C) drop
D) reject
A) continue
B) pass
C) drop
D) reject
continue
4
Which two actions occur when a Cisco ISE server device administrator logs in to a device? (Choose two.)
A) The Cisco ISE server queries the internal identity store.
B) The device queries the external identity store.
C) The device queries the Cisco ISE authorization server.
D) The device queries the internal identity store.
E) The Cisco ISE server queries the external identity store.
A) The Cisco ISE server queries the internal identity store.
B) The device queries the external identity store.
C) The device queries the Cisco ISE authorization server.
D) The device queries the internal identity store.
E) The Cisco ISE server queries the external identity store.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
5
What is a requirement for Feed Service to work?
A) TCP port 8080 must be opened between Cisco ISE and the feed server.
B) Cisco ISE has access to an internal server to download feed update.
C) Cisco ISE has a base license.
D) Cisco ISE has Internet access to download feed update.
A) TCP port 8080 must be opened between Cisco ISE and the feed server.
B) Cisco ISE has access to an internal server to download feed update.
C) Cisco ISE has a base license.
D) Cisco ISE has Internet access to download feed update.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
6
What are two requirements of generating a single certificate in Cisco ISE by using a certificate provisioning portal, without generating a certificate signing request? (Choose two.)
A) Enter the IP address of the device.
B) Enter the common name.
C) Choose the hashing method.
D) Locate the CSV file for the device MAC.
E) Select the certificate template.
A) Enter the IP address of the device.
B) Enter the common name.
C) Choose the hashing method.
D) Locate the CSV file for the device MAC.
E) Select the certificate template.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
7
Which permission is common to the Active Directory Join and Leave operations?
A) Remove the Cisco ISE machine account from the domain.
B) Search Active Directory to see if a Cisco ISE machine account already exists.
C) Set attributes on the Cisco ISE machine account.
D) Create a Cisco ISE machine account in the domain if the machine account does not already exist.
A) Remove the Cisco ISE machine account from the domain.
B) Search Active Directory to see if a Cisco ISE machine account already exists.
C) Set attributes on the Cisco ISE machine account.
D) Create a Cisco ISE machine account in the domain if the machine account does not already exist.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
8
Which command displays all 802.1X/MAB sessions that are active on the switch ports of a Cisco Catalyst switch?
A) show authentication sessions interface Gi1/0/x output
B) show authentication sessions
C) show authentication sessions output
D) show authentication sessions interface Gi 1/0/x
A) show authentication sessions interface Gi1/0/x output
B) show authentication sessions
C) show authentication sessions output
D) show authentication sessions interface Gi 1/0/x

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
9
Which advanced option within a WLAN must be enabled to trigger Central Web Authentication for Wireless users on AireOS controller?
A) DHCP server
B) override Interface ACL
C) static IP tunneling
D) AAA override
A) DHCP server
B) override Interface ACL
C) static IP tunneling
D) AAA override

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
10
How is policy services node redundancy achieved in a deployment?
A) by creating a node group
B) by deploying both primary and secondary node
C) by enabling VIP
D) by utilizing RADIUS server list on the NAD
A) by creating a node group
B) by deploying both primary and secondary node
C) by enabling VIP
D) by utilizing RADIUS server list on the NAD

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
11
What is a method for transporting security group tags throughout the network?
A) by embedding the security group tag in the 802.1Q header
B) by the Security Group Tag Exchange Protocol
C) by enabling 802.1AE on every network device
D) by embedding the security group tag in the IP header
A) by embedding the security group tag in the 802.1Q header
B) by the Security Group Tag Exchange Protocol
C) by enabling 802.1AE on every network device
D) by embedding the security group tag in the IP header

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
12
What is the purpose of the ip http server command on a switch?
A) It enables the https server for users for web authentication.
B) It enables dot1x authentication on the switch.
C) It enables MAB authentication on the switch.
D) It enables the switch to redirect users for web authentication.
A) It enables the https server for users for web authentication.
B) It enables dot1x authentication on the switch.
C) It enables MAB authentication on the switch.
D) It enables the switch to redirect users for web authentication.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
13
Which interface-level command is needed to turn on 802.1X authentication?
A) dot1x system-auth-control
B) dot1x pae authenticator
C) aaa server radius dynamic-author
D) authentication host-mode single-host
A) dot1x system-auth-control
B) dot1x pae authenticator
C) aaa server radius dynamic-author
D) authentication host-mode single-host

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
14
What is needed to configure wireless guest access on the network?
A) endpoint already profiled in ISE
B) WEBAUTH ACL for redirection
C) Captive Portal Bypass turned on
D) valid user account in Active Directory
A) endpoint already profiled in ISE
B) WEBAUTH ACL for redirection
C) Captive Portal Bypass turned on
D) valid user account in Active Directory

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
15
Which personas can a Cisco ISE node assume?
A) policy service, gatekeeping, and monitoring
B) administration, monitoring, and gatekeeping
C) administration, policy service, and monitoring
D) administration, policy service, gatekeeping
A) policy service, gatekeeping, and monitoring
B) administration, monitoring, and gatekeeping
C) administration, policy service, and monitoring
D) administration, policy service, gatekeeping

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
16
An engineer is using the low-impact mode for a phased deployment of Cisco ISE and is trying to connect to the network prior to authentication. Which access will be denied in this deployment?
A) DNS
B) DHCP
C) EAP
D) HTTP
A) DNS
B) DHCP
C) EAP
D) HTTP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
17
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from the Cisco ISE node?
A) session-timeout
B) termination-action
C) radius-server timeout
D) idle-timeout
A) session-timeout
B) termination-action
C) radius-server timeout
D) idle-timeout

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
18
An engineer is configuring a guest password policy and needs to ensure that the password complexity requirements are set to mitigate brute force attacks. Which two requirements should be included in this policy? (Choose two.)
A) active username limit
B) password expiration period
C) access code control
D) username expiration date
E) minimum password length
A) active username limit
B) password expiration period
C) access code control
D) username expiration date
E) minimum password length

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
19
In a standalone Cisco ISE deployment, which two personas are configured on a node? (Choose two.)
A) subscriber
B) primary
C) administration
D) publisher
E) policy service
A) subscriber
B) primary
C) administration
D) publisher
E) policy service

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
20
What happens when an internal user is configured with an external identity store for authentication, but an engineer uses the Cisco ISE admin portal to select an internal identity store as the identity source?
A) Authentication is redirected to the internal identity source.
B) Authentication is granted.
C) Authentication fails.
D) Authentication is redirected to the external identity source.
A) Authentication is redirected to the internal identity source.
B) Authentication is granted.
C) Authentication fails.
D) Authentication is redirected to the external identity source.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
21
Which portal is used to customize the settings for a user to log in and download the compliance module?
A) Client Provisioning
B) Client Endpoint
C) Client Profiling
D) Client Guest
A) Client Provisioning
B) Client Endpoint
C) Client Profiling
D) Client Guest

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
22
An engineer is working with a distributed deployment of Cisco ISE and needs to configure various network probes to collect a set of attributes from the endpoints on the network. Which node should be used to accomplish this task?
A) policy service
B) monitoring
C) primary policy administrator
D) pxGrid
A) policy service
B) monitoring
C) primary policy administrator
D) pxGrid

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
23
Which protocol must be allowed for a BYOD device to access the BYOD portal?
A) HTTPS
B) HTTP
C) SSH
D) SMTP
A) HTTPS
B) HTTP
C) SSH
D) SMTP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
24
Which default endpoint identity group does an endpoint that does not match any profile in Cisco ISE become a member of?
A) block list
B) unknown
C) allow list
D) profiled
E) endpoint
A) block list
B) unknown
C) allow list
D) profiled
E) endpoint

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
25
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
A) Application Visibility and Control
B) Supplicant Provisioning Wizard
C) My Devices Portal
D) Network Access Control
A) Application Visibility and Control
B) Supplicant Provisioning Wizard
C) My Devices Portal
D) Network Access Control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
26
Which use case validates a change of authorization?
A) An endpoint that is disconnected from the network is discovered.
B) Endpoints are created through device registration for the guests.
C) An endpoint profiling policy is changed for authorization policy.
D) An authenticated, wired EAP-capable endpoint is discovered.
A) An endpoint that is disconnected from the network is discovered.
B) Endpoints are created through device registration for the guests.
C) An endpoint profiling policy is changed for authorization policy.
D) An authenticated, wired EAP-capable endpoint is discovered.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
27
Which profiling probe collects the user-agent string?
A) DHCP
B) HTTP
C) NMAP
D) AD
A) DHCP
B) HTTP
C) NMAP
D) AD

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
28
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profiling service so that a user can reliably bind the IP addresses and MAC addresses of endpoints? (Choose two.)
A) SNMP
B) HTTP
C) RADIUS
D) DHCP
E) NetFlow
A) SNMP
B) HTTP
C) RADIUS
D) DHCP
E) NetFlow

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
29
An engineer is configuring web authentication using non-standard ports and needs the switch to redirect traffic to the correct port. Which command should be used to accomplish this task?
A) permit tcp any any eq
B) ip http port
C) aaa group server radius
D) aaa group server radius proxy
A) permit tcp any any eq
B) ip http port
C) aaa group server radius
D) aaa group server radius proxy

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
30
An engineer is configuring Cisco ISE to reprofile endpoints based only on new requests of INIT-REBOOT and SELECTING message types. Which probe should be used to accomplish this task?
A) DHCP
B) DNS
C) NMAP
D) RADIUS
A) DHCP
B) DNS
C) NMAP
D) RADIUS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
31
What should be considered when configuring certificates for BYOD?
A) The SAN field is populated with the end user name.
B) The CN field is populated with the endpoint host name.
C) An endpoint certificate is mandatory for the Cisco ISE BYOD.
D) An Android endpoint uses EST, whereas other operating systems use SCEP for enrollment.
A) The SAN field is populated with the end user name.
B) The CN field is populated with the endpoint host name.
C) An endpoint certificate is mandatory for the Cisco ISE BYOD.
D) An Android endpoint uses EST, whereas other operating systems use SCEP for enrollment.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
32
Which two components are required for creating a Native Supplicant Profile within a BYOD flow? (Choose two.)
A) Redirect ACL
B) Connection Type
C) Operating System
D) Windows Settings
E) iOS Settings
A) Redirect ACL
B) Connection Type
C) Operating System
D) Windows Settings
E) iOS Settings

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
33
What service can be enabled on the Cisco ISE node to identify the types of devices connecting to a network?
A) profiling
B) central web authentication
C) MAB
D) posture
A) profiling
B) central web authentication
C) MAB
D) posture

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
34
What sends the redirect ACL that is configured in the authorization profile back to the Cisco WLC?
A) State attribute
B) Class attribute
C) Event
D) Cisco-av-pair
A) State attribute
B) Class attribute
C) Event
D) Cisco-av-pair

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
35
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
A) Client Provisioning
B) BYOD
C) Guest
D) Block list
A) Client Provisioning
B) BYOD
C) Guest
D) Block list

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
36
A network engineer needs to ensure that the access credentials are not exposed during the 802.1X authentication among components. Which two protocols should be configured to accomplish this task? (Choose two.)
A) PEAP
B) EAP-TLS
C) EAP-MD5
D) EAP-TTLS
E) LEAP
A) PEAP
B) EAP-TLS
C) EAP-MD5
D) EAP-TTLS
E) LEAP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
37
During BYOD flow, where does a Microsoft Windows PC download the Network Setup Assistant?
A) Microsoft App Store
B) Cisco App Store
C) Cisco ISE directly
D) Native OTA functionality
A) Microsoft App Store
B) Cisco App Store
C) Cisco ISE directly
D) Native OTA functionality

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
38
Which Cisco ISE service allows an engineer to check the compliance of endpoints before connecting to the network?
A) qualys
B) posture
C) personas
D) nexpose
A) qualys
B) posture
C) personas
D) nexpose

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
39
What is the minimum certainty factor when creating a profiler policy?
A) the minimum number that a predefined condition provides
B) the maximum number that a predefined condition provides
C) the minimum number that a device certainty factor must reach to become a member of the profile
D) the maximum number that a device certainty factor must reach to become a member of the profile
A) the minimum number that a predefined condition provides
B) the maximum number that a predefined condition provides
C) the minimum number that a device certainty factor must reach to become a member of the profile
D) the maximum number that a device certainty factor must reach to become a member of the profile

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
40
Which two events trigger a CoA for an endpoint when CoA is enabled globally for ReAuth? (Choose two.)
A) addition of endpoint to My Devices Portal
B) endpoint marked as lost in My Devices Portal
C) updating of endpoint dACL
D) endpoint profile transition from Apple-device to Apple-iPhone
E) endpoint profile transition from Unknown to Windows10-Workstation
A) addition of endpoint to My Devices Portal
B) endpoint marked as lost in My Devices Portal
C) updating of endpoint dACL
D) endpoint profile transition from Apple-device to Apple-iPhone
E) endpoint profile transition from Unknown to Windows10-Workstation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
41
Which two values are compared by the binary comparison function in authentication that is based on Active Directory?
A) user-presented certificate and a certificate stored in Active Directory
B) MS-CHAPv2 provided machine credentials and credentials stored in Active Directory
C) user-presented password hash and a hash stored in Active Directory
D) subject alternative name and the common name
A) user-presented certificate and a certificate stored in Active Directory
B) MS-CHAPv2 provided machine credentials and credentials stored in Active Directory
C) user-presented password hash and a hash stored in Active Directory
D) subject alternative name and the common name

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
42
Which are two characteristics of TACACS+? (Choose two.)
A) It separates authorization and authentication functions.
B) It combines authorization and authentication functions.
C) It uses UDP port 49.
D) It encrypts the password only.
E) It uses TCP port 49.
A) It separates authorization and authentication functions.
B) It combines authorization and authentication functions.
C) It uses UDP port 49.
D) It encrypts the password only.
E) It uses TCP port 49.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
43
What must match between Cisco ISE and the network access device to successfully authenticate endpoints?
A) shared secret
B) profile
C) certificate
D) SNMP version
A) shared secret
B) profile
C) certificate
D) SNMP version

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
44
Which supplicant(s) and server(s) are capable of supporting EAP-CHAINING?
A) Cisco Secure Services Client and Cisco Access Control Server
B) Cisco AnyConnect NAM and Cisco Identity Service Engine
C) Cisco AnyConnect NAM and Cisco Access Control Server
D) Windows Native Supplicant and Cisco Identity Service Engine
A) Cisco Secure Services Client and Cisco Access Control Server
B) Cisco AnyConnect NAM and Cisco Identity Service Engine
C) Cisco AnyConnect NAM and Cisco Access Control Server
D) Windows Native Supplicant and Cisco Identity Service Engine

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
45
Which port does Cisco ISE use for native supplicant provisioning of a Windows laptop?
A) TCP 8905
B) TCP 8909
C) TCP 443
D) UDP 1812
A) TCP 8905
B) TCP 8909
C) TCP 443
D) UDP 1812

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
46
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two.)
A) Known
B) Monthly
C) Daily
D) Imported
E) Random
A) Known
B) Monthly
C) Daily
D) Imported
E) Random

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
47
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)
A) new AD user 802.1X authentication
B) hotspot
C) posture
D) guest AUP
E) BYOD
A) new AD user 802.1X authentication
B) hotspot
C) posture
D) guest AUP
E) BYOD

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
48
What is a valid guest portal type?
A) Sponsor
B) Sponsored-Guest
C) Captive-Guest
D) My Devices
A) Sponsor
B) Sponsored-Guest
C) Captive-Guest
D) My Devices

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
49
A network administrator has just added a front desk receptionist account to the Cisco ISE Guest Service sponsor group. Using the Cisco ISE Guest Sponsor Portal, which guest services can the receptionist provide?
A) Keep track of guest user activities.
B) Create and manage guest user accounts.
C) Configure authorization settings for guest users.
D) Authenticate guest users to Cisco ISE.
A) Keep track of guest user activities.
B) Create and manage guest user accounts.
C) Configure authorization settings for guest users.
D) Authenticate guest users to Cisco ISE.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
50
Which three default endpoint identity groups does Cisco ISE create? (Choose three.)
A) endpoint
B) unknown
C) blacklist
D) profiled
E) whitelist
A) endpoint
B) unknown
C) blacklist
D) profiled
E) whitelist

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
51
Which configuration is required in the Cisco ISE authentication policy to allow Central Web Authentication?
A) MAB and if user not found, continue
B) MAB and if authentication failed, continue
C) Dot1x and if authentication failed, continue
D) Dot1x and if user not found, continue
A) MAB and if user not found, continue
B) MAB and if authentication failed, continue
C) Dot1x and if authentication failed, continue
D) Dot1x and if user not found, continue

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
52
Which two task types are included in the Cisco ISE common tasks support for TACACS+ profiles? (Choose two.)
A) ASA
B) Firepower
C) Shell
D) WLC
E) IOS
A) ASA
B) Firepower
C) Shell
D) WLC
E) IOS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
53
Which statement about configuring certificates for BYOD is true?
A) The SAN field is populated with the end user name.
B) The CN field is populated with the endpoint host name.
C) An endpoint certificate is mandatory for the Cisco ISE BYOD.
D) An Android endpoint uses EST, whereas other operating systems use SCEP for enrollment.
A) The SAN field is populated with the end user name.
B) The CN field is populated with the endpoint host name.
C) An endpoint certificate is mandatory for the Cisco ISE BYOD.
D) An Android endpoint uses EST, whereas other operating systems use SCEP for enrollment.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
54
Which two features must be used on Cisco ISE to enable the TACACS+ feature? (Choose two.)
A) Command Sets
B) Server Sequence
C) Device Administration License
D) External TACACS Servers
E) Device Admin Service
A) Command Sets
B) Server Sequence
C) Device Administration License
D) External TACACS Servers
E) Device Admin Service

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
55
Which two ports do network devices typically use for CoA? (Choose two.)
A) 19005
B) 443
C) 3799
D) 8080
E) 1700
A) 19005
B) 443
C) 3799
D) 8080
E) 1700

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
56
What occurs when a Cisco ISE distributed deployment has two nodes and the secondary node is deregistered?
A) The secondary node restarts.
B) The primary node restarts.
C) Both nodes restart.
D) The primary node becomes standalone.
A) The secondary node restarts.
B) The primary node restarts.
C) Both nodes restart.
D) The primary node becomes standalone.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
57
Which two ports must be open between Cisco ISE and the client when you configure posture on Cisco ISE? (Choose two.)
A) TCP 80
B) TCP 8905
C) TCP 8443
D) TCP 8906
E) TCP 443
A) TCP 80
B) TCP 8905
C) TCP 8443
D) TCP 8906
E) TCP 443

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
58
Which two responses from the RADIUS server to NAS are valid during the authentication process? (Choose two.)
A) access-challenge
B) access-accept
C) access-request
D) access-reserved
E) access-response
A) access-challenge
B) access-accept
C) access-request
D) access-reserved
E) access-response

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
59
Which default endpoint identity group does an endpoint that does not match any profile in Cisco ISE become a member of?
A) blacklist
B) unknown
C) whitelist
D) profiled
E) endpoint
A) blacklist
B) unknown
C) whitelist
D) profiled
E) endpoint

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
60
Refer to the exhibit. 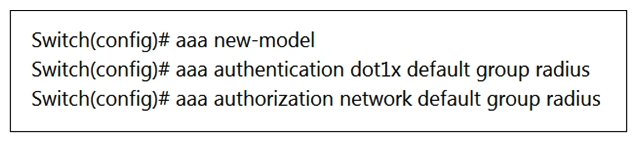 A network engineer is configuring the switch to accept downloadable ACLs from a Cisco ISE server. Which two commands should be run to complete the configuration? (Choose two.)
A network engineer is configuring the switch to accept downloadable ACLs from a Cisco ISE server. Which two commands should be run to complete the configuration? (Choose two.)
A) radius-server attribute 8 include-in-access-req
B) ip device tracking
C) dot1x system-auth-control
D) radius server vsa send authentication
E) aaa authorization auth-proxy default group radius
 A network engineer is configuring the switch to accept downloadable ACLs from a Cisco ISE server. Which two commands should be run to complete the configuration? (Choose two.)
A network engineer is configuring the switch to accept downloadable ACLs from a Cisco ISE server. Which two commands should be run to complete the configuration? (Choose two.)A) radius-server attribute 8 include-in-access-req
B) ip device tracking
C) dot1x system-auth-control
D) radius server vsa send authentication
E) aaa authorization auth-proxy default group radius

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
61
Which two endpoint compliance statuses are possible? (Choose two.)
A) compliant
B) valid
C) unknown
D) known
E) invalid
A) compliant
B) valid
C) unknown
D) known
E) invalid

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
62
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
A) Client Provisioning
B) BYOD
C) Guest
D) Blacklist
A) Client Provisioning
B) BYOD
C) Guest
D) Blacklist

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
63
Which term refers to an endpoint agent that tries to join an 802.1X-enabled network?
A) EAP server
B) authenticator
C) supplicant
D) client
A) EAP server
B) authenticator
C) supplicant
D) client

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
64
During BYOD flow, from where does a Microsoft Windows PC download the Network Setup Assistant?
A) Microsoft App Store
B) Cisco App Store
C) Cisco ISE directly
D) Native OTA functionality
A) Microsoft App Store
B) Cisco App Store
C) Cisco ISE directly
D) Native OTA functionality

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck
65
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose two.)
A) Client Provisioning portal
B) remediation actions
C) updates
D) access policy
E) conditions
A) Client Provisioning portal
B) remediation actions
C) updates
D) access policy
E) conditions

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 65 في هذه المجموعة.
فتح الحزمة
k this deck








