Deck 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/141
العب
ملء الشاشة (f)
Deck 3: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
1
What is a benefit of agent-based protection when compared to agentless protection?
A) It lowers maintenance costs
B) It provides a centralized platform
C) It collects and detects all traffic locally
D) It manages numerous devices simultaneously
A) It lowers maintenance costs
B) It provides a centralized platform
C) It collects and detects all traffic locally
D) It manages numerous devices simultaneously
It provides a centralized platform
2
What does an attacker use to determine which network ports are listening on a potential target device?
A) man-in-the-middle
B) port scanning
C) SQL injection
D) ping sweep
A) man-in-the-middle
B) port scanning
C) SQL injection
D) ping sweep
port scanning
3
What is a difference between SOAR and SIEM?
A) SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
B) SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
C) SOAR receives information from a single platform and delivers it to a SIEM
D) SIEM receives information from a single platform and delivers it to a SOAR
A) SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
B) SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
C) SOAR receives information from a single platform and delivers it to a SIEM
D) SIEM receives information from a single platform and delivers it to a SOAR
SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
4
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
A) least privilege
B) need to know
C) integrity validation
D) due diligence
A) least privilege
B) need to know
C) integrity validation
D) due diligence

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
5
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
A) reconnaissance
B) action on objectives
C) installation
D) exploitation
A) reconnaissance
B) action on objectives
C) installation
D) exploitation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
6
Which process is used when IPS events are removed to improve data integrity?
A) data availability
B) data normalization
C) data signature
D) data protection
A) data availability
B) data normalization
C) data signature
D) data protection

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
7
What is the practice of giving an employee access to only the resources needed to accomplish their job?
A) principle of least privilege
B) organizational separation
C) separation of duties
D) need to know principle
A) principle of least privilege
B) organizational separation
C) separation of duties
D) need to know principle

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
8
What is the difference between deep packet inspection and stateful inspection?
A) Deep packet inspection is more secure than stateful inspection on Layer 4
B) Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
C) Stateful inspection is more secure than deep packet inspection on Layer 7
D) Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
A) Deep packet inspection is more secure than stateful inspection on Layer 4
B) Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
C) Stateful inspection is more secure than deep packet inspection on Layer 7
D) Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
9
Which security principle is violated by running all processes as root or administrator?
A) principle of least privilege
B) role-based access control
C) separation of duties
D) trusted computing base
A) principle of least privilege
B) role-based access control
C) separation of duties
D) trusted computing base

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
10
An analyst is investigating an incident in a SOC environment. Which method is used to identify a session from a group of logs?
A) sequence numbers
B) IP identifier
C) 5-tuple
D) timestamps
A) sequence numbers
B) IP identifier
C) 5-tuple
D) timestamps

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
11
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
A) weaponization
B) reconnaissance
C) installation
D) delivery
A) weaponization
B) reconnaissance
C) installation
D) delivery

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
12
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
A) MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
B) MAC is the strictest of all levels of control and DAC is object-based access
C) DAC is controlled by the operating system and MAC is controlled by an administrator
D) DAC is the strictest of all levels of control and MAC is object-based access
A) MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
B) MAC is the strictest of all levels of control and DAC is object-based access
C) DAC is controlled by the operating system and MAC is controlled by an administrator
D) DAC is the strictest of all levels of control and MAC is object-based access

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
13
Which attack method intercepts traffic on a switched network?
A) denial of service
B) ARP cache poisoning
C) DHCP snooping
D) command and control
A) denial of service
B) ARP cache poisoning
C) DHCP snooping
D) command and control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
14
Which security principle requires more than one person is required to perform a critical task?
A) least privilege
B) need to know
C) separation of duties
D) due diligence
A) least privilege
B) need to know
C) separation of duties
D) due diligence

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
15
What is the difference between an attack vector and attack surface?
A) An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies vulnerabilities that are independent of user actions.
B) An attack vector identifies components that can be exploited; and an attack surface identifies the potential path an attack can take to penetrate the network.
C) An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which attacks are possible with these vulnerabilities.
D) An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using several methods against the identified vulnerabilities.
A) An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies vulnerabilities that are independent of user actions.
B) An attack vector identifies components that can be exploited; and an attack surface identifies the potential path an attack can take to penetrate the network.
C) An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which attacks are possible with these vulnerabilities.
D) An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using several methods against the identified vulnerabilities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
16
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
A) fragmentation
B) pivoting
C) encryption
D) stenography
A) fragmentation
B) pivoting
C) encryption
D) stenography

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
17
Which evasion technique is a function of ransomware?
A) extended sleep calls
B) encryption
C) resource exhaustion
D) encoding
A) extended sleep calls
B) encryption
C) resource exhaustion
D) encoding

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
18
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
A) confidentiality, identity, and authorization
B) confidentiality, integrity, and authorization
C) confidentiality, identity, and availability
D) confidentiality, integrity, and availability
A) confidentiality, identity, and authorization
B) confidentiality, integrity, and authorization
C) confidentiality, identity, and availability
D) confidentiality, integrity, and availability

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
19
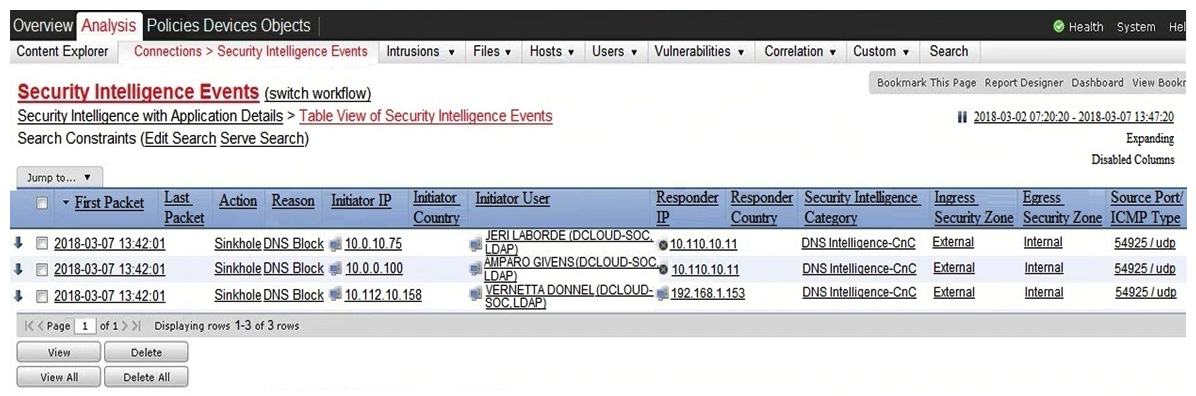 Refer to the exhibit. Which two elements in the table are parts of the 5-tuple? (Choose two.)
Refer to the exhibit. Which two elements in the table are parts of the 5-tuple? (Choose two.)A) First Packet
B) Initiator User
C) Ingress Security Zone
D) Source Port
E) Initiator IP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
20
Why is encryption challenging to security monitoring?
A) Encryption analysis is used by attackers to monitor VPN tunnels.
B) Encryption is used by threat actors as a method of evasion and obfuscation.
C) Encryption introduces additional processing requirements by the CPU.
D) Encryption introduces larger packet sizes to analyze and store.
A) Encryption analysis is used by attackers to monitor VPN tunnels.
B) Encryption is used by threat actors as a method of evasion and obfuscation.
C) Encryption introduces additional processing requirements by the CPU.
D) Encryption introduces larger packet sizes to analyze and store.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
21
 Refer to the exhibit. What is occurring in this network traffic?
Refer to the exhibit. What is occurring in this network traffic?A) high rate of SYN packets being sent from a multiple source towards a single destination IP
B) high rate of SYN packets being sent from a single source IP towards multiple destination IPs
C) flood of ACK packets coming from a single source IP to multiple destination IPs
D) flood of SYN packets coming from a single source IP to a single destination IP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
22
What are the two characteristics of the full packet captures? (Choose two.)
A) Identifying network loops and collision domains.
B) Troubleshooting the cause of security and performance issues.
C) Reassembling fragmented traffic from raw data.
D) Detecting common hardware faults and identify faulty assets.
E) Providing a historical record of a network transaction.
A) Identifying network loops and collision domains.
B) Troubleshooting the cause of security and performance issues.
C) Reassembling fragmented traffic from raw data.
D) Detecting common hardware faults and identify faulty assets.
E) Providing a historical record of a network transaction.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
23
Which type of data consists of connection level, application-specific records generated from network traffic?
A) transaction data
B) location data
C) statistical data
D) alert data
A) transaction data
B) location data
C) statistical data
D) alert data

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
24
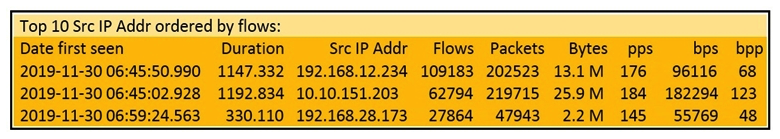 Refer to the exhibit. What information is depicted?
Refer to the exhibit. What information is depicted?A) IIS data
B) NetFlow data
C) network discovery event
D) IPS event data

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
25
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
A) ransomware communicating after infection
B) users downloading copyrighted content
C) data exfiltration
D) user circumvention of the firewall
A) ransomware communicating after infection
B) users downloading copyrighted content
C) data exfiltration
D) user circumvention of the firewall

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
26
When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification. Which information is available on the server certificate?
A) server name, trusted subordinate CA, and private key
B) trusted subordinate CA, public key, and cipher suites
C) trusted CA name, cipher suites, and private key
D) server name, trusted CA, and public key
A) server name, trusted subordinate CA, and private key
B) trusted subordinate CA, public key, and cipher suites
C) trusted CA name, cipher suites, and private key
D) server name, trusted CA, and public key

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
27
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor. Which type of evidence is this?
A) best evidence
B) prima facie evidence
C) indirect evidence
D) physical evidence
A) best evidence
B) prima facie evidence
C) indirect evidence
D) physical evidence

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
28
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A) Untampered images are used in the security investigation process
B) Tampered images are used in the security investigation process
C) The image is tampered if the stored hash and the computed hash match
D) Tampered images are used in the incident recovery process
E) The image is untampered if the stored hash and the computed hash match
A) Untampered images are used in the security investigation process
B) Tampered images are used in the security investigation process
C) The image is tampered if the stored hash and the computed hash match
D) Tampered images are used in the incident recovery process
E) The image is untampered if the stored hash and the computed hash match

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
29
What does cyber attribution identity in an investigation?
A) cause of an attack
B) exploit of an attack
C) vulnerabilities exploited
D) threat actors of an attack
A) cause of an attack
B) exploit of an attack
C) vulnerabilities exploited
D) threat actors of an attack

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
30
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
A) syslog messages
B) full packet capture
C) NetFlow
D) firewall event logs
A) syslog messages
B) full packet capture
C) NetFlow
D) firewall event logs

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
31
How is NetFlow different than traffic mirroring?
A) NetFlow collects metadata and traffic mirroring clones data
B) Traffic mirroring impacts switch performance and NetFlow does not
C) Traffic mirroring costs less to operate than NetFlow
D) NetFlow generates more data than traffic mirroring
A) NetFlow collects metadata and traffic mirroring clones data
B) Traffic mirroring impacts switch performance and NetFlow does not
C) Traffic mirroring costs less to operate than NetFlow
D) NetFlow generates more data than traffic mirroring

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
32
Which security technology allows only a set of pre-approved applications to run on a system?
A) application-level blacklisting
B) host-based IPS
C) application-level whitelisting
D) antivirus
A) application-level blacklisting
B) host-based IPS
C) application-level whitelisting
D) antivirus

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
33
What is an attack surface as compared to a vulnerability?
A) any potential danger to an asset
B) the sum of all paths for data into and out of the application
C) an exploitable weakness in a system or its design
D) the individuals who perform an attack
A) any potential danger to an asset
B) the sum of all paths for data into and out of the application
C) an exploitable weakness in a system or its design
D) the individuals who perform an attack

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
34
How does an SSL certificate impact security between the client and the server?
A) by enabling an authenticated channel between the client and the server
B) by creating an integrated channel between the client and the server
C) by enabling an authorized channel between the client and the server
D) by creating an encrypted channel between the client and the server
A) by enabling an authenticated channel between the client and the server
B) by creating an integrated channel between the client and the server
C) by enabling an authorized channel between the client and the server
D) by creating an encrypted channel between the client and the server

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
35
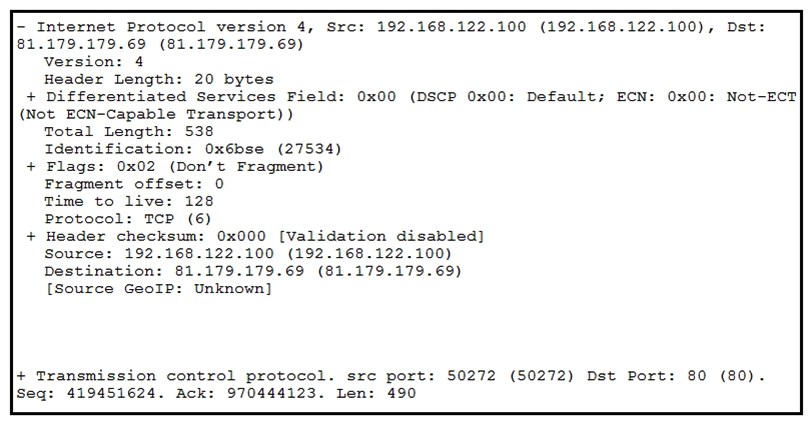 Refer to the exhibit. What should be interpreted from this packet capture?
Refer to the exhibit. What should be interpreted from this packet capture?A) IP address 179.179.69/50272/192.168.122.100/80/6 is sending a packet from port 80 of IP address 192.168.122.100 that is going to port 50272 of IP address 81.179.179.69 using IP protocol 6.
B) IP address 192.168.122.100/50272/81.179.179.69/80/6 is sending a packet from port 50272 of IP address 192.168.122.100 that is going to port 80 of IP address 81.179.179.69 using IP protocol 6.
C) IP address 192.168.122.100/50272/81.179.179.69/80/6 is sending a packet from port 80 of IP address 192.168.122.100 that is going to port 50272 of IP address 81.179.179.69 using IP protocol 6.
D) IP address 179.179.69/50272/192.168.122.100/80/6 is sending a packet from port 50272 of IP address 192.168.122.100 that is going to port 80 of IP address 81.179.179.69 using IP protocol 6.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
36
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network. Which testing method did the intruder use?
A) social engineering
B) eavesdropping
C) piggybacking
D) tailgating
A) social engineering
B) eavesdropping
C) piggybacking
D) tailgating

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
37
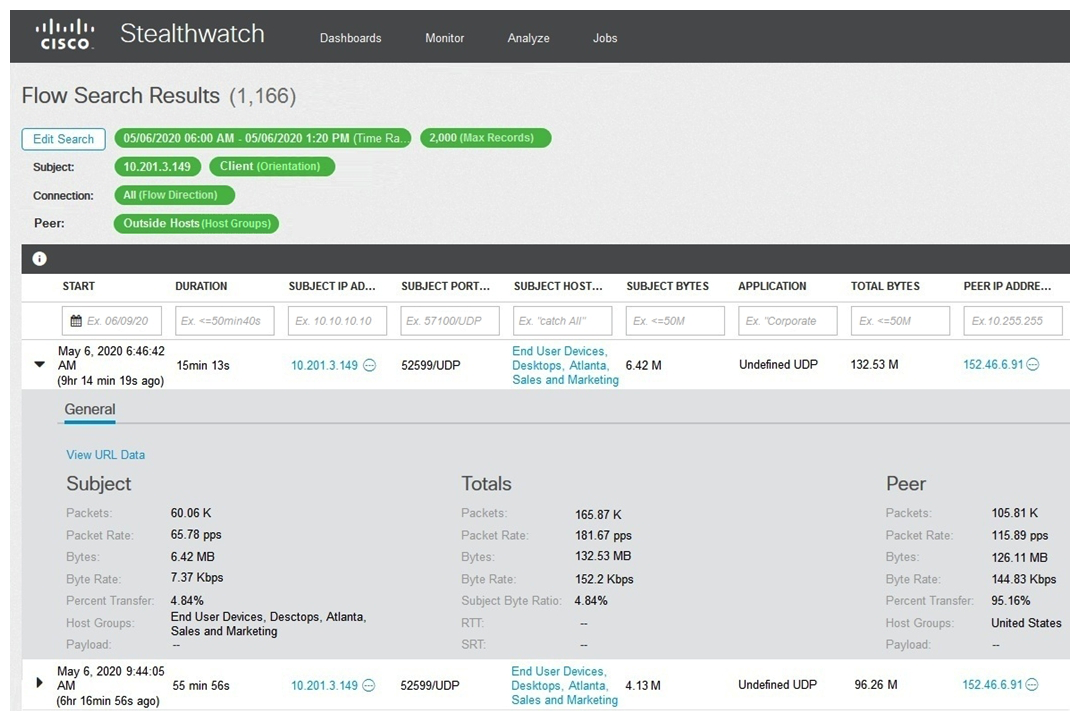 Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?A) Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
B) Host 152.46.6.91 is being identified as a watchlist country for data transfer.
C) Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
D) Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
38
 Refer to the exhibit. Which type of log is displayed?
Refer to the exhibit. Which type of log is displayed?A) IDS
B) proxy
C) NetFlow
D) sys

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
39
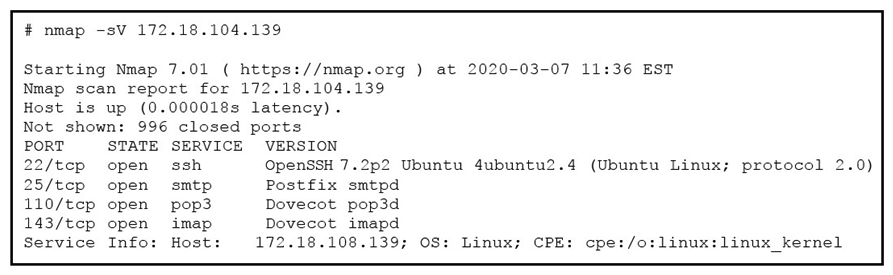 Refer to the exhibit. What does the output indicate about the server with the IP address 172.18.104.139?
Refer to the exhibit. What does the output indicate about the server with the IP address 172.18.104.139?A) open ports of a web server
B) open port of an FTP server
C) open ports of an email server
D) running processes of the server

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
40
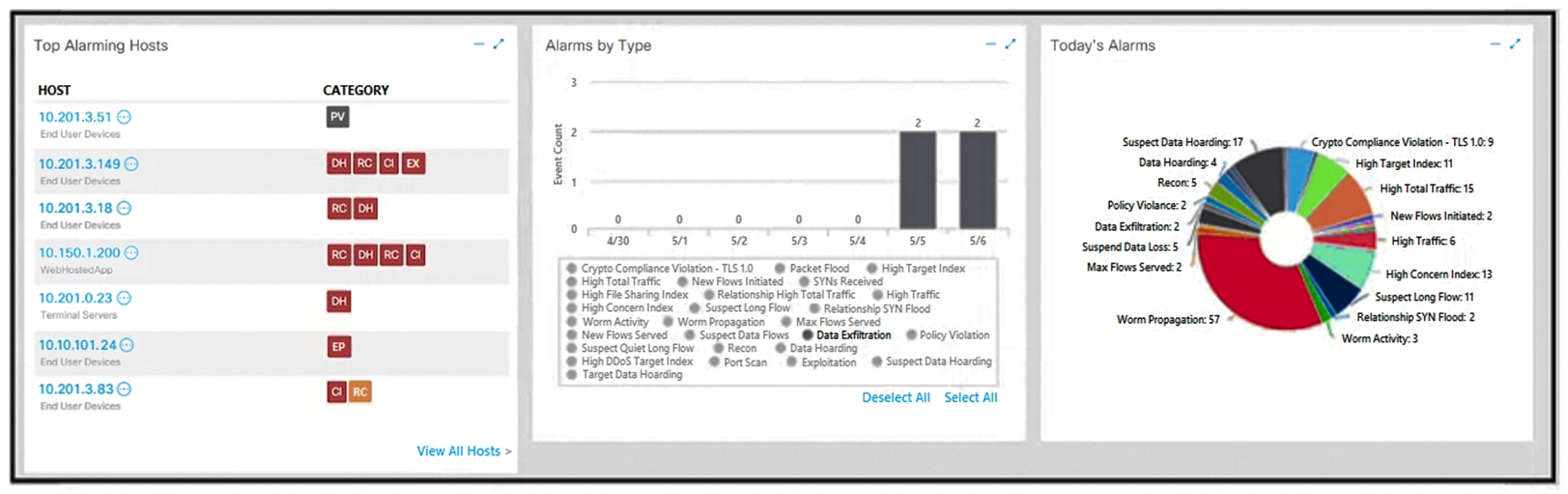 Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?A) A policy violation is active for host 10.10.101.24.
B) A host on the network is sending a DDoS attack to another inside host.
C) There are two active data exfiltration alerts.
D) A policy violation is active for host 10.201.3.149.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
41
Which signature impacts network traffic by causing legitimate traffic to be blocked?
A) false negative
B) true positive
C) true negative
D) false positive
A) false negative
B) true positive
C) true negative
D) false positive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
42
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs. Which technology should be used to accomplish this task?
A) application whitelisting/blacklisting
B) network NGFW
C) host-based IDS
D) antivirus/antispyware software
A) application whitelisting/blacklisting
B) network NGFW
C) host-based IDS
D) antivirus/antispyware software

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
43
Which system monitors local system operation and local network access for violations of a security policy?
A) host-based intrusion detection
B) systems-based sandboxing
C) host-based firewall
D) antivirus
A) host-based intrusion detection
B) systems-based sandboxing
C) host-based firewall
D) antivirus

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
44
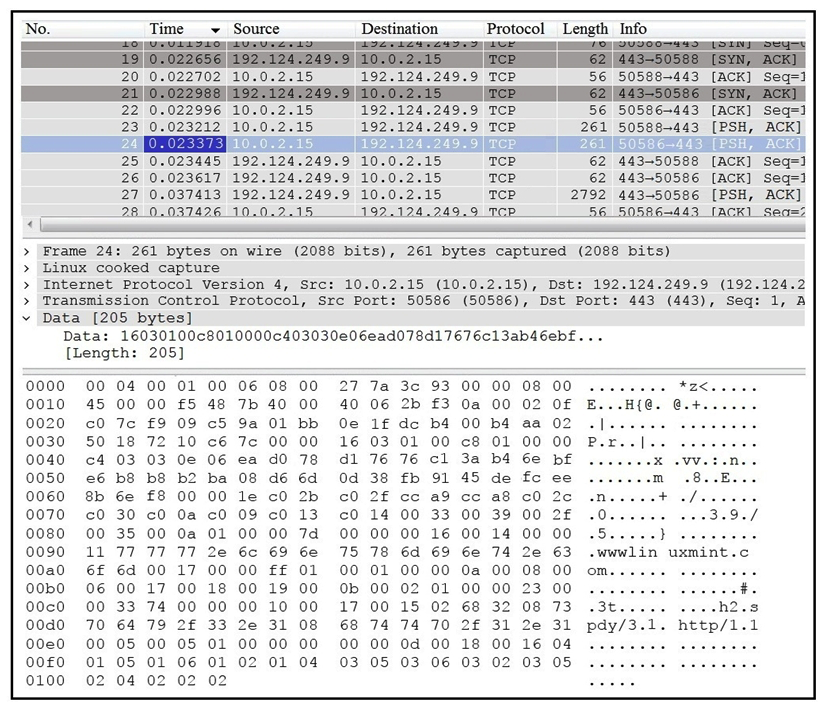 Refer to the exhibit. Which application protocol is in this PCAP file?
Refer to the exhibit. Which application protocol is in this PCAP file?A) SSH
B) TCP
C) TLS
D) HTTP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
45
Which regex matches only on all lowercase letters?
A) [a?z]+
B) [^a?z]+
C) a?z+
D) a*z+
A) [a?z]+
B) [^a?z]+
C) a?z+
D) a*z+

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
46
Which incidence response step includes identifying all hosts affected by an attack?
A) detection and analysis
B) post-incident activity
C) preparation
D) containment, eradication, and recovery
A) detection and analysis
B) post-incident activity
C) preparation
D) containment, eradication, and recovery

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
47
Which type of data collection requires the largest amount of storage space?
A) alert data
B) transaction data
C) session data
D) full packet capture
A) alert data
B) transaction data
C) session data
D) full packet capture

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
48
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header. Which technology makes this behavior possible?
A) encapsulation
B) TOR
C) tunneling
D) NAT
A) encapsulation
B) TOR
C) tunneling
D) NAT

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
49
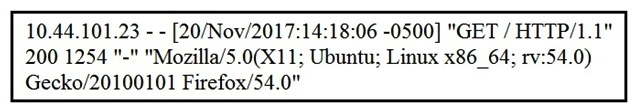 Refer to the exhibit. What does the message indicate?
Refer to the exhibit. What does the message indicate?A) an access attempt was made from the Mosaic web browser
B) a successful access attempt was made to retrieve the password file
C) a successful access attempt was made to retrieve the root of the website
D) a denied access attempt was made to retrieve the password file

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
50
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
A) application identification number
B) active process identification number
C) runtime identification number
D) process identification number
A) application identification number
B) active process identification number
C) runtime identification number
D) process identification number

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
51
Which HTTP header field is used in forensics to identify the type of browser used?
A) referrer
B) host
C) user-agent
D) accept-language
A) referrer
B) host
C) user-agent
D) accept-language

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
52
What is a difference between inline traffic interrogation and traffic mirroring?
A) Inline inspection acts on the original traffic data flow
B) Traffic mirroring passes live traffic to a tool for blocking
C) Traffic mirroring inspects live traffic for analysis and mitigation
D) Inline traffic copies packets for analysis and security
A) Inline inspection acts on the original traffic data flow
B) Traffic mirroring passes live traffic to a tool for blocking
C) Traffic mirroring inspects live traffic for analysis and mitigation
D) Inline traffic copies packets for analysis and security

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
53
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
A) true negative
B) false negative
C) false positive
D) true positive
A) true negative
B) false negative
C) false positive
D) true positive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
54
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
A) CSIRT
B) PSIRT
C) public affairs
D) management
A) CSIRT
B) PSIRT
C) public affairs
D) management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
55
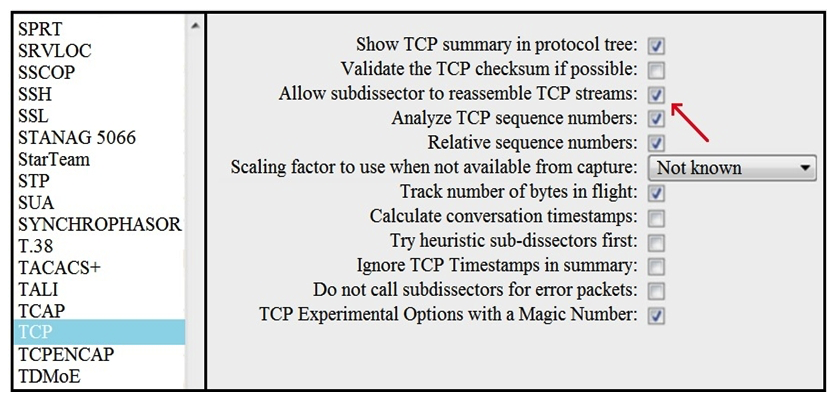 Refer to the exhibit. What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Refer to the exhibit. What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?A) insert TCP subdissectors
B) extract a file from a packet capture
C) disable TCP streams
D) unfragment TCP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
56
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
A) UDP port to which the traffic is destined
B) TCP port from which the traffic was sourced
C) source IP address of the packet
D) destination IP address of the packet
E) UDP port from which the traffic is sourced
A) UDP port to which the traffic is destined
B) TCP port from which the traffic was sourced
C) source IP address of the packet
D) destination IP address of the packet
E) UDP port from which the traffic is sourced

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
57
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. What is the initial event called in the NIST SP800-61?
A) online assault
B) precursor
C) trigger
D) instigator
A) online assault
B) precursor
C) trigger
D) instigator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
58
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
A) The computer has a HIPS installed on it.
B) The computer has a NIPS installed on it.
C) The computer has a HIDS installed on it.
D) The computer has a NIDS installed on it.
A) The computer has a HIPS installed on it.
B) The computer has a NIPS installed on it.
C) The computer has a HIDS installed on it.
D) The computer has a NIDS installed on it.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
59
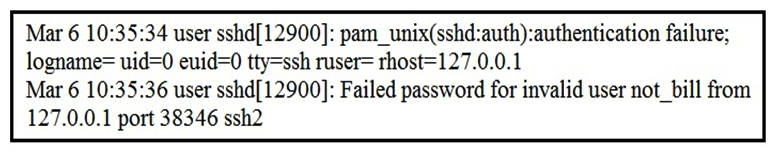 Refer to the exhibit. In which Linux log file is this output found?
Refer to the exhibit. In which Linux log file is this output found?A) /var/log/authorization.log
B) /var/log/dmesg
C) var/log/var.log
D) /var/log/auth.log

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
60
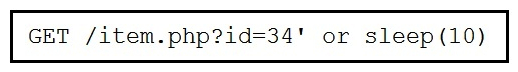 Refer to the exhibit. This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Refer to the exhibit. This request was sent to a web application server driven by a database. Which type of web server attack is represented?A) parameter manipulation
B) heap memory corruption
C) command injection
D) blind SQL injection

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
61
What makes HTTPS traffic difficult to monitor?
A) SSL interception
B) packet header size
C) signature detection time
D) encryption
A) SSL interception
B) packet header size
C) signature detection time
D) encryption

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
62
Which regular expression matches "color" and "colour"?
A) colo?ur
B) col[0?8]+our
C) colou?r
D) col[0?9]+our
A) colo?ur
B) col[0?8]+our
C) colou?r
D) col[0?9]+our

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
63
Which event is user interaction?
A) gaining root access
B) executing remote code
C) reading and writing file permission
D) opening a malicious file
A) gaining root access
B) executing remote code
C) reading and writing file permission
D) opening a malicious file

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
64
Which event artifact is used to identity HTTP GET requests for a specific file?
A) destination IP address
B) TCP ACK
C) HTTP status code
D) URI
A) destination IP address
B) TCP ACK
C) HTTP status code
D) URI

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
65
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
A) detection and analysis
B) post-incident activity
C) vulnerability management
D) risk assessment
E) vulnerability scoring
A) detection and analysis
B) post-incident activity
C) vulnerability management
D) risk assessment
E) vulnerability scoring

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
66
Which two elements are used for profiling a network? (Choose two.)
A) session duration
B) total throughput
C) running processes
D) listening ports
E) OS fingerprint
A) session duration
B) total throughput
C) running processes
D) listening ports
E) OS fingerprint

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
67
Which two components reduce the attack surface on an endpoint? (Choose two.)
A) secure boot
B) load balancing
C) increased audit log levels
D) restricting USB ports
E) full packet captures at the endpoint
A) secure boot
B) load balancing
C) increased audit log levels
D) restricting USB ports
E) full packet captures at the endpoint

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
68
In a SOC environment, what is a vulnerability management metric?
A) code signing enforcement
B) full assets scan
C) internet exposed devices
D) single factor authentication
A) code signing enforcement
B) full assets scan
C) internet exposed devices
D) single factor authentication

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
69
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
A) NetScout
B) tcpdump
C) SolarWinds
D) netsh
A) NetScout
B) tcpdump
C) SolarWinds
D) netsh

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
70
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
A) context
B) session
C) laptop
D) firewall logs
E) threat actor
A) context
B) session
C) laptop
D) firewall logs
E) threat actor

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
71
Which utility blocks a host portscan?
A) HIDS
B) sandboxing
C) host-based firewall
D) antimalware
A) HIDS
B) sandboxing
C) host-based firewall
D) antimalware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
72
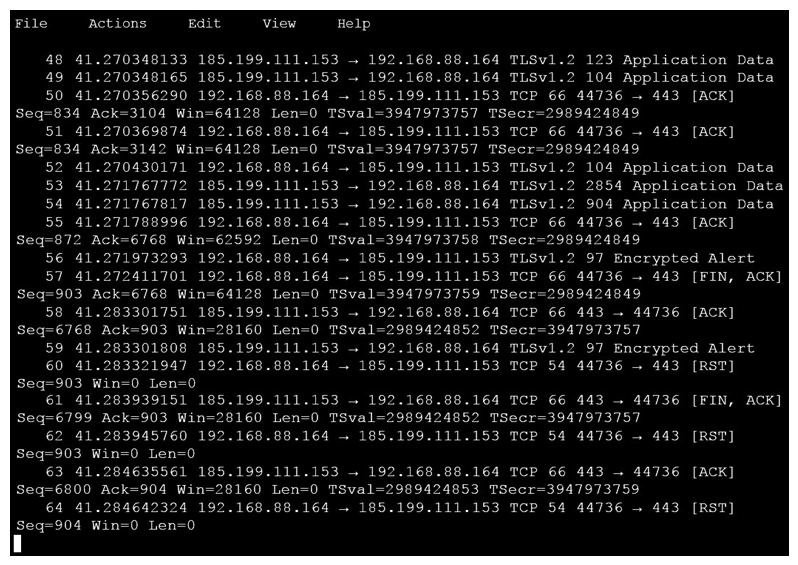 An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture the analyst cannot determine the technique and payload used for the communication. Which obfuscation technique is the attacker using?A) Base64 encoding
B) transport layer security encryption
C) SHA-256 hashing
D) ROT13 encryption

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
73
Which category relates to improper use or disclosure of PII data?
A) legal
B) compliance
C) regulated
D) contractual
A) legal
B) compliance
C) regulated
D) contractual

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
74
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
A) Tapping interrogation replicates signals to a separate port for analyzing traffic
B) Tapping interrogations detect and block malicious traffic
C) Inline interrogation enables viewing a copy of traffic to ensure traffic is in compliance with security policies
D) Inline interrogation detects malicious traffic but does not block the traffic
A) Tapping interrogation replicates signals to a separate port for analyzing traffic
B) Tapping interrogations detect and block malicious traffic
C) Inline interrogation enables viewing a copy of traffic to ensure traffic is in compliance with security policies
D) Inline interrogation detects malicious traffic but does not block the traffic

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
75
What is personally identifiable information that must be safeguarded from unauthorized access?
A) date of birth
B) driver's license number
C) gender
D) zip code
A) date of birth
B) driver's license number
C) gender
D) zip code

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
76
What is rule-based detection when compared to statistical detection?
A) proof of a user's identity
B) proof of a user's action
C) likelihood of user's action
D) falsification of a user's identity
A) proof of a user's identity
B) proof of a user's action
C) likelihood of user's action
D) falsification of a user's identity

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
77
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
A) data from a CD copied using Mac-based system
B) data from a CD copied using Linux system
C) data from a DVD copied using Windows system
D) data from a CD copied using Windows
A) data from a CD copied using Mac-based system
B) data from a CD copied using Linux system
C) data from a DVD copied using Windows system
D) data from a CD copied using Windows

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
78
How is attacking a vulnerability categorized?
A) action on objectives
B) delivery
C) exploitation
D) installation
A) action on objectives
B) delivery
C) exploitation
D) installation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
79
Which type of evidence supports a theory or an assumption that results from initial evidence?
A) probabilistic
B) indirect
C) best
D) corroborative
A) probabilistic
B) indirect
C) best
D) corroborative

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck
80
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A) The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
B) The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
C) The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D) The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
A) The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
B) The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
C) The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D) The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 141 في هذه المجموعة.
فتح الحزمة
k this deck








