Deck 13: AWS Certified SysOps Administrator (SOA-C01)
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/976
العب
ملء الشاشة (f)
Deck 13: AWS Certified SysOps Administrator (SOA-C01)
1
An application that you are managing has EC2 instances & Dynamo OB tables deployed to several AWS Regions in order to monitor the performance of the application globally, you would like to see two graphs: 1) Avg CPU Utilization across all EC2 instances 2) Number of Throttled Requests for all DynamoDB tables. How can you accomplish this?
A) Tag your resources with the application name, and select the tag name as the dimension in the Cloudwatch Management console to view the respective graphs
B) Use the Cloud Watch CLI tools to pull the respective metrics from each regional endpoint Aggregate the data offline & store it for graphing in CloudWatch.
C) Add SNMP traps to each instance and DynamoDB table Leverage a central monitoring server to capture data from each instance and table Put the aggregate data into Cloud Watch for graphing.
D) Add a CloudWatch agent to each instance and attach one to each DynamoDB table. When configuring the agent set the appropriate application name & view the graphs in CloudWatch.
A) Tag your resources with the application name, and select the tag name as the dimension in the Cloudwatch Management console to view the respective graphs
B) Use the Cloud Watch CLI tools to pull the respective metrics from each regional endpoint Aggregate the data offline & store it for graphing in CloudWatch.
C) Add SNMP traps to each instance and DynamoDB table Leverage a central monitoring server to capture data from each instance and table Put the aggregate data into Cloud Watch for graphing.
D) Add a CloudWatch agent to each instance and attach one to each DynamoDB table. When configuring the agent set the appropriate application name & view the graphs in CloudWatch.
Use the Cloud Watch CLI tools to pull the respective metrics from each regional endpoint Aggregate the data offline & store it for graphing in CloudWatch.
2
What is a placement group?
A) A collection of Auto Scaling groups in the same Region
B) Feature that enables EC2 instances to interact with each other via nigh bandwidth, low latency connections
C) A collection of Elastic Load Balancers in the same Region or Availability Zone
D) A collection of authorized Cloud Front edge locations for a distribution
A) A collection of Auto Scaling groups in the same Region
B) Feature that enables EC2 instances to interact with each other via nigh bandwidth, low latency connections
C) A collection of Elastic Load Balancers in the same Region or Availability Zone
D) A collection of authorized Cloud Front edge locations for a distribution
Feature that enables EC2 instances to interact with each other via nigh bandwidth, low latency connections
3
When creation of an EBS snapshot Is initiated but not completed the EBS volume?
A) Cannot De detached or attached to an EC2 instance until me snapshot completes
B) Can be used in read-only mode while me snapshot is in progress
C) Can be used while me snapshot Is in progress
D) Cannot be used until the snapshot completes
A) Cannot De detached or attached to an EC2 instance until me snapshot completes
B) Can be used in read-only mode while me snapshot is in progress
C) Can be used while me snapshot Is in progress
D) Cannot be used until the snapshot completes
Can be used while me snapshot Is in progress
4
You have a web-style application with a stateless but CPU and memory-intensive web tier running on a cc2 8xlarge EC2 instance inside of a VPC The instance when under load is having problems returning requests within the SLA as defined by your business The application maintains its state in a DynamoDB table, but the data tier is properly provisioned and responses are consistently fast. How can you best resolve the issue of the application responses not meeting your SLA?
A) Add another cc2 8xlarge application instance, and put both behind an Elastic Load Balancer
B) Move the cc2 8xlarge to the same Availability Zone as the DynamoDB table
C) Cache the database responses in ElastiCache for more rapid access
D) Move the database from DynamoDB to RDS MySQL in scale-out read-replica configuration
A) Add another cc2 8xlarge application instance, and put both behind an Elastic Load Balancer
B) Move the cc2 8xlarge to the same Availability Zone as the DynamoDB table
C) Cache the database responses in ElastiCache for more rapid access
D) Move the database from DynamoDB to RDS MySQL in scale-out read-replica configuration

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
5
Your entire AWS infrastructure lives inside of one Amazon VPC. You have an Infrastructure monitoring application running on an Amazon instance in Availability Zone (AZ) A of the region, and another application instance running in AZ B. The monitoring application needs to make use of ICMP ping to confirm network reachability of the instance hosting the application. Can you configure the security groups for these instances to only allow the ICMP ping to pass from the monitoring instance to the application instance and nothing else? If so how?
A) No, two instances in two different AZ's can't talk directly to each other via ICMP ping as that protocol is not allowed across subnet (iebroadcast) boundaries
B) Yes, both the monitoring instance and the application instance have to be a part of the same security group, and that security group needs to allow inbound ICMP
C) Yes, the security group for the monitoring instance needs to allow outbound ICMP and the application instance's security group needs to allow Inbound ICMP
D) Yes, both the monitoring instance's security group and the application instance's security group need to allow both inbound and outbound ICMP ping packets since ICMP is not a connection-oriented protocol
A) No, two instances in two different AZ's can't talk directly to each other via ICMP ping as that protocol is not allowed across subnet (iebroadcast) boundaries
B) Yes, both the monitoring instance and the application instance have to be a part of the same security group, and that security group needs to allow inbound ICMP
C) Yes, the security group for the monitoring instance needs to allow outbound ICMP and the application instance's security group needs to allow Inbound ICMP
D) Yes, both the monitoring instance's security group and the application instance's security group need to allow both inbound and outbound ICMP ping packets since ICMP is not a connection-oriented protocol

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
6
You have a web application leveraging an Elastic Load Balancer (ELB) In front of the web servers deployed using an Auto Scaling Group Your database is running on Relational Database Service (RDS) The application serves out technical articles and responses to them in general there are more views of an article than there are responses to the article. On occasion, an article on the site becomes extremely popular resulting in significant traffic Increases that causes the site to go down. What could you do to help alleviate the pressure on the infrastructure while maintaining availability during these events? (Choose three.)
A) Leverage CloudFront for the delivery of the articles.
B) Add RDS read-replicas for the read traffic going to your relational database
C) Leverage ElastiCache for caching the most frequently used data.
D) Use SOS to queue up the requests for the technical posts and deliver them out of the queue.
E) Use Route53 health checks to fail over to an S3 bucket for an error page.
A) Leverage CloudFront for the delivery of the articles.
B) Add RDS read-replicas for the read traffic going to your relational database
C) Leverage ElastiCache for caching the most frequently used data.
D) Use SOS to queue up the requests for the technical posts and deliver them out of the queue.
E) Use Route53 health checks to fail over to an S3 bucket for an error page.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
7
When an EC2 instance that is backed by an S3-based AMI Is terminated, what happens to the data on me root volume?
A) Data is automatically saved as an E8S volume.
B) Data is automatically saved as an ESS snapshot.
C) Data is automatically deleted.
D) Data is unavailable until the instance is restarted.
A) Data is automatically saved as an E8S volume.
B) Data is automatically saved as an ESS snapshot.
C) Data is automatically deleted.
D) Data is unavailable until the instance is restarted.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
8
Your EC2-Based Multi-tier application includes a monitoring instance that periodically makes application -level read only requests of various application components and if any of those fail more than three times 30 seconds calls CloudWatch lo fire an alarm, and the alarm notifies your operations team by email and SMS of a possible application health problem. However, you also need to watch the watcher -the monitoring instance itself - and be notified if it becomes unhealthy. Which of the following is a simple way to achieve that goal?
A) Run another monitoring instance that pings the monitoring instance and fires a could watch alarm mat notifies your operations team should the primary monitoring instance become unhealthy.
B) Set a CloudWatch alarm based on EC2 system and instance status checks and have the alarm notify your operations team of any detected problem with the monitoring instance.
C) Set a CloudWatch alarm based on the CPU utilization of the monitoring instance and have the alarm notify your operations team if C r the CPU usage exceeds 50% few more than one minute: then have your monitoring application go into a CPU-bound loop should it Detect any application problems.
D) Have the monitoring instances post messages to an SOS queue and then dequeue those messages on another instance should the queue cease to have new messages, the second instance should first terminate the original monitoring instance start another backup monitoring instance and assume (he role of the previous monitoring instance and beginning adding messages to the SQSqueue.
A) Run another monitoring instance that pings the monitoring instance and fires a could watch alarm mat notifies your operations team should the primary monitoring instance become unhealthy.
B) Set a CloudWatch alarm based on EC2 system and instance status checks and have the alarm notify your operations team of any detected problem with the monitoring instance.
C) Set a CloudWatch alarm based on the CPU utilization of the monitoring instance and have the alarm notify your operations team if C r the CPU usage exceeds 50% few more than one minute: then have your monitoring application go into a CPU-bound loop should it Detect any application problems.
D) Have the monitoring instances post messages to an SOS queue and then dequeue those messages on another instance should the queue cease to have new messages, the second instance should first terminate the original monitoring instance start another backup monitoring instance and assume (he role of the previous monitoring instance and beginning adding messages to the SQSqueue.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
9
You have set up Individual AWS accounts for each project. You have been asked to make sure your AWS Infrastructure costs do not exceed the budget set per project for each month. Which of the following approaches can help ensure that you do not exceed the budget each month?
A) Consolidate your accounts so you have a single bill for all accounts and projects
B) Set up auto scaling with CloudWatch alarms using SNS to notify you when you are running too many Instances in a given account
C) Set up CloudWatch billing alerts for all AWS resources used by each project, with a notification occurring when the amount for each resource tagged to a particular project matches the budget allocated to the project.
D) Set up CloudWatch billing alerts for all AWS resources used by each account, with email notifications when it hits 50%. 80% and 90% of its budgeted monthly spend
A) Consolidate your accounts so you have a single bill for all accounts and projects
B) Set up auto scaling with CloudWatch alarms using SNS to notify you when you are running too many Instances in a given account
C) Set up CloudWatch billing alerts for all AWS resources used by each project, with a notification occurring when the amount for each resource tagged to a particular project matches the budget allocated to the project.
D) Set up CloudWatch billing alerts for all AWS resources used by each account, with email notifications when it hits 50%. 80% and 90% of its budgeted monthly spend

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
10
Which of the following statements about this S3 bucket policy is true? 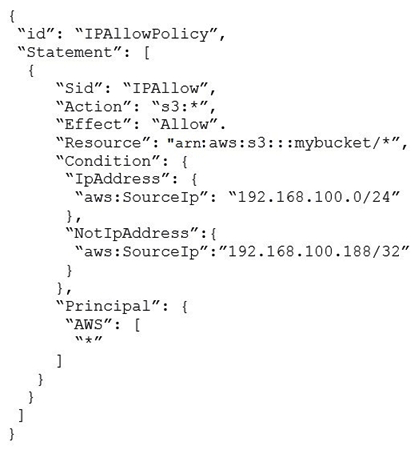
A) Denies the server with the IP address 192 168 100 0 full access to the "mybucket" bucket
B) Denies the server with the IP address 192 168 100 188 full access to the "mybucket" bucket
C) Grants all the servers within the 192 168 100 0/24 subnet full access to the "mybucket" bucket
D) Grants all the servers within the 192 168 100 188/32 subnet full access to the "mybucket" bucket

A) Denies the server with the IP address 192 168 100 0 full access to the "mybucket" bucket
B) Denies the server with the IP address 192 168 100 188 full access to the "mybucket" bucket
C) Grants all the servers within the 192 168 100 0/24 subnet full access to the "mybucket" bucket
D) Grants all the servers within the 192 168 100 188/32 subnet full access to the "mybucket" bucket

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
11
Which services allow the customer to retain full administrative privileges of the underlying EC2 instances? (Choose two.)
A) Amazon Elastic Map Reduce
B) Elastic Load Balancing
C) AWS Elastic Beanstalk
D) Amazon Elasticache
E) Amazon Relational Database service
A) Amazon Elastic Map Reduce
B) Elastic Load Balancing
C) AWS Elastic Beanstalk
D) Amazon Elasticache
E) Amazon Relational Database service

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
12
You are using ElastiCache Memcached to store session state and cache database queries in your infrastructure. You notice in CloudWatch that Evictions and GetMisses are Doth very high. What two actions could you take to rectify this? (Choose two.)
A) Increase the number of nodes in your cluster
B) Tweak the max_item_size parameter
C) Shrink the number of nodes in your cluster
D) Increase the size of the nodes in the duster
A) Increase the number of nodes in your cluster
B) Tweak the max_item_size parameter
C) Shrink the number of nodes in your cluster
D) Increase the size of the nodes in the duster

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
13
You have decided to change the Instance type for instances running in your application tier that are using Auto Scaling. In which area below would you change the instance type definition?
A) Auto Scaling launch configuration
B) Auto Scaling group
C) Auto Scaling policy
D) Auto Scaling tags
A) Auto Scaling launch configuration
B) Auto Scaling group
C) Auto Scaling policy
D) Auto Scaling tags

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
14
When preparing for a compliance assessment of your system built inside of AWS. what are three best-practices for you to prepare for an audit? (Choose three.)
A) Gather evidence of your IT operational controls
B) Request and obtain applicable third-party audited AWS compliance reports and certifications
C) Request and obtain a compliance and security tour of an AWS data center for a pre-assessment security review
D) Request and obtain approval from AWS to perform relevant network scans and in-depth penetration tests of your system's Instances and endpoints
E) Schedule meetings with AWS's third-party auditors to provide evidence of AWS compliance that maps to your control objectives
A) Gather evidence of your IT operational controls
B) Request and obtain applicable third-party audited AWS compliance reports and certifications
C) Request and obtain a compliance and security tour of an AWS data center for a pre-assessment security review
D) Request and obtain approval from AWS to perform relevant network scans and in-depth penetration tests of your system's Instances and endpoints
E) Schedule meetings with AWS's third-party auditors to provide evidence of AWS compliance that maps to your control objectives

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
15
Which of the following requires a custom CloudWatch metric to monitor?
A) Data transfer of an EC2 instance
B) Disk usage activity of an EC2 instance
C) Memory Utilization of an EC2 instance
D) CPU Utilization of an EC2 instance
A) Data transfer of an EC2 instance
B) Disk usage activity of an EC2 instance
C) Memory Utilization of an EC2 instance
D) CPU Utilization of an EC2 instance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
16
When assessing an organization s use of AWS API access credentials which of the following three credentials should be evaluated? (Choose three.)
A) Key pairs
B) Console passwords
C) Access keys
D) Signing certificates
E) Security Group memberships
A) Key pairs
B) Console passwords
C) Access keys
D) Signing certificates
E) Security Group memberships

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
17
You have been asked to leverage Amazon VPC BC2 and SOS to implement an application that submits and receives millions of messages per second to a message queue. You want to ensure your application has sufficient bandwidth between your EC2 instances and SQS Which option will provide the most scalable solution for communicating between the application and SQS?
A) Ensure the application instances are properly configured with an Elastic Load Balancer
B) Ensure the application instances are launched in private subnets with the EBS-optimized option enabled
C) Ensure the application instances are launched in public subnets with the associate-public-IP-address=true option enabled
D) Launch application instances in private subnets with an Auto Scaling group and Auto Scaling triggers configured to watch the SQS queue size
A) Ensure the application instances are properly configured with an Elastic Load Balancer
B) Ensure the application instances are launched in private subnets with the EBS-optimized option enabled
C) Ensure the application instances are launched in public subnets with the associate-public-IP-address=true option enabled
D) Launch application instances in private subnets with an Auto Scaling group and Auto Scaling triggers configured to watch the SQS queue size

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
18
You are creating an Auto Scaling group whose Instances need to insert a custom metric into CloudWatch. Which method would be the best way to authenticate your CloudWatch PUT request?
A) Create an IAM role with the Put MetricData permission and modify the Auto Scaling launch configuration to launch instances in that role
B) Create an IAM user with the PutMetricData permission and modify the Auto Scaling launch configuration to inject the userscredentials into the instance User Data
C) Modify the appropriate Cloud Watch metric policies to allow the Put MetricData permission to instances from the Auto Scaling group
D) Create an IAM user with the PutMetricData permission and put the credentials in a private repository and have applications on the server pull the credentials as needed
A) Create an IAM role with the Put MetricData permission and modify the Auto Scaling launch configuration to launch instances in that role
B) Create an IAM user with the PutMetricData permission and modify the Auto Scaling launch configuration to inject the userscredentials into the instance User Data
C) Modify the appropriate Cloud Watch metric policies to allow the Put MetricData permission to instances from the Auto Scaling group
D) Create an IAM user with the PutMetricData permission and put the credentials in a private repository and have applications on the server pull the credentials as needed

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
19
You are currently hosting multiple applications in a VPC and have logged numerous port scans coming in from a specific IP address block. Your security team has requested that all access from the offending IP address block be denied for the next 24 hours. Which of the following is the best method to quickly and temporarily deny access from the specified IP address block?
A) Create an AD policy to modify Windows Firewall settings on all hosts in the VPC to deny access from the IP address block
B) Modify the Network ACLs associated with all public subnets in the VPC to deny access from the IP address block
C) Add a rule to all of the VPC 5 Security Groups to deny access from the IP address block
D) Modify the Windows Firewall settings on all Amazon Machine Images (AMIs) that your organization uses in that VPC to deny access from the IP address block
A) Create an AD policy to modify Windows Firewall settings on all hosts in the VPC to deny access from the IP address block
B) Modify the Network ACLs associated with all public subnets in the VPC to deny access from the IP address block
C) Add a rule to all of the VPC 5 Security Groups to deny access from the IP address block
D) Modify the Windows Firewall settings on all Amazon Machine Images (AMIs) that your organization uses in that VPC to deny access from the IP address block

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
20
You are managing a legacy application Inside VPC with hard coded IP addresses in its configuration. Which two mechanisms will allow the application to failover to new instances without the need for reconfiguration? (Choose two.)
A) Create an ELB to reroute traffic to a failover instance
B) Create a secondary ENI that can be moved to a failover instance
C) Use Route53 health checks to fail traffic over to a failover instance
D) Assign a secondary private IP address to the primary ENIO that can be moved to a failover instance
A) Create an ELB to reroute traffic to a failover instance
B) Create a secondary ENI that can be moved to a failover instance
C) Use Route53 health checks to fail traffic over to a failover instance
D) Assign a secondary private IP address to the primary ENIO that can be moved to a failover instance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
21
A user has created a web application with Auto Scaling. The user is regularly monitoring the application and he observed that the traffic is highest on Thursday and Friday between 8 AM to 6 PM. What is the best solution to handle scaling in this case?
A) Add a new instance manually by 8 AM Thursday and terminate the same by 6 PM Friday
B) Schedule Auto Scaling to scale up by 8 AM Thursday and scale down after 6 PM on Friday
C) Schedule a policy which may scale up every day at 8 AM and scales down by 6 PM
D) Configure a batch process to add an instance by 8 AM and remove it by Friday 6 PM
A) Add a new instance manually by 8 AM Thursday and terminate the same by 6 PM Friday
B) Schedule Auto Scaling to scale up by 8 AM Thursday and scale down after 6 PM on Friday
C) Schedule a policy which may scale up every day at 8 AM and scales down by 6 PM
D) Configure a batch process to add an instance by 8 AM and remove it by Friday 6 PM

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
22
When an EC2 EBS-backed (EBS root) instance is stopped, what happens to the data on any ephemeral store volumes?
A) Data will be deleted and win no longer be accessible
B) Data is automatically saved in an EBS volume.
C) Data is automatically saved as an EBS snapshot
D) Data is unavailable until the instance is restarted
A) Data will be deleted and win no longer be accessible
B) Data is automatically saved in an EBS volume.
C) Data is automatically saved as an EBS snapshot
D) Data is unavailable until the instance is restarted

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
23
A user is trying to aggregate all the CloudWatch metric data of the last 1 week. Which of the below mentioned statistics is not available for the user as a part of data aggregation?
A) Aggregate
B) Sum
C) Sample data
D) Average
A) Aggregate
B) Sum
C) Sample data
D) Average

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
24
A media company produces new video files on-premises every day with a total size of around 100 GBS after compression All files have a size of 1 -2 GB and need to be uploaded to Amazon S3 every night in a fixed time window between 3am and 5am Current upload takes almost 3 hours, although less than half of the available bandwidth is used. What step(s) would ensure that the file uploads are able to complete in the allotted time window?
A) Increase your network bandwidth to provide faster throughput to S3
B) Upload the files in parallel to S3
C) Pack all files into a single archive, upload it to S3, then extract the files in AWS
D) Use AWS Import/Export to transfer the video files
A) Increase your network bandwidth to provide faster throughput to S3
B) Upload the files in parallel to S3
C) Pack all files into a single archive, upload it to S3, then extract the files in AWS
D) Use AWS Import/Export to transfer the video files

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
25
A customer has a web application that uses cookie Based sessions to track logged in users. It is deployed on AWS using ELB and Auto Scaling. The customer observes that when load increases. Auto Scaling launches new Instances but the load on the easting Instances does not decrease, causing all existing users have a sluggish experience. Which two answer choices independently describe a behavior that could be the cause of the sluggish user experience? (Choose two.)
A) ELB's normal behavior sends requests from the same user to the same backend instance
B) ELB's behavior when sticky sessions are enabled causes ELB to send requests in the same session to the same backend instance
C) A faulty browser is not honoring the TTL of the ELB DNS name
D) The web application uses long polling such as comet or websockets. Thereby keeping a connection open to a web server tor a long time
A) ELB's normal behavior sends requests from the same user to the same backend instance
B) ELB's behavior when sticky sessions are enabled causes ELB to send requests in the same session to the same backend instance
C) A faulty browser is not honoring the TTL of the ELB DNS name
D) The web application uses long polling such as comet or websockets. Thereby keeping a connection open to a web server tor a long time

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
26
What are characteristics of Amazon S3? (Choose two.)
A) Objects are directly accessible via a URL
B) S3 should be used to host a relational database
C) S3 allows you to store objects or virtually unlimited size
D) S3 allows you to store virtually unlimited amounts of data
E) S3 offers Provisioned IOPS
A) Objects are directly accessible via a URL
B) S3 should be used to host a relational database
C) S3 allows you to store objects or virtually unlimited size
D) S3 allows you to store virtually unlimited amounts of data
E) S3 offers Provisioned IOPS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
27
A user has setup a CloudWatch alarm on an EC2 action when the CPU utilization is above 75%. The alarm sends a notification to SNS on the alarm state. If the user wants to simulate the alarm action how can he achieve this?
A) Run activities on the CPU such that its utilization reaches above 75%
B) From the AWS console change the state to 'Alarm'
C) The user can set the alarm state to 'Alarm' using CLI
D) Run the SNS action manually
A) Run activities on the CPU such that its utilization reaches above 75%
B) From the AWS console change the state to 'Alarm'
C) The user can set the alarm state to 'Alarm' using CLI
D) Run the SNS action manually

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
28
A user is planning to use AWS Cloud formation for his automatic deployment requirements. Which of the below mentioned components are required as a part of the template?
A) Parameters
B) Outputs
C) Template version
D) Resources
A) Parameters
B) Outputs
C) Template version
D) Resources

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
29
An organization's security policy requires multiple copies of all critical data to be replicated across at least a primary and backup data center. The organization has decided to store some critical data on Amazon S3. Which option should you implement to ensure this requirement is met?
A) Use the S3 copy API to replicate data between two S3 buckets in different regions
B) You do not need to implement anything since S3 data is automatically replicated between regions
C) Use the S3 copy API to replicate data between two S3 buckets in different facilities within an AWS Region
D) You do not need to implement anything since S3 data is automatically replicated between multiple facilities within an AWS Region
A) Use the S3 copy API to replicate data between two S3 buckets in different regions
B) You do not need to implement anything since S3 data is automatically replicated between regions
C) Use the S3 copy API to replicate data between two S3 buckets in different facilities within an AWS Region
D) You do not need to implement anything since S3 data is automatically replicated between multiple facilities within an AWS Region

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
30
A user is trying to save some cost on the AWS services. Which of the below mentioned options will not help him save cost?
A) Delete the unutilized EBS volumes once the instance is terminated
B) Delete the AutoScaling launch configuration after the instances are terminated
C) Release the elastic IP if not required once the instance is terminated
D) Delete the AWS ELB after the instances are terminated
A) Delete the unutilized EBS volumes once the instance is terminated
B) Delete the AutoScaling launch configuration after the instances are terminated
C) Release the elastic IP if not required once the instance is terminated
D) Delete the AWS ELB after the instances are terminated

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
31
An organization has created 5 IAM users. The organization wants to give them the same login ID but different passwords. How can the organization achieve this?
A) The organization should create a separate login ID but give the IAM users the same alias so that each one can login with their alias
B) The organization should create each user in a separate region so that they have their own URL to login
C) It is not possible to have the same login ID for multiple IAM users of the same account
D) The organization should create various groups and add each user with the same login ID to different groups. The user can login with their own group ID
A) The organization should create a separate login ID but give the IAM users the same alias so that each one can login with their alias
B) The organization should create each user in a separate region so that they have their own URL to login
C) It is not possible to have the same login ID for multiple IAM users of the same account
D) The organization should create various groups and add each user with the same login ID to different groups. The user can login with their own group ID

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
32
You use S3 to store critical data for your company Several users within your group currently have lull permissions to your S3 buckets You need to come up with a solution mat does not impact your users and also protect against the accidental deletion of objects. Which two options will address this issue? (Choose two.)
A) Enable versioning on your S3 Buckets
B) Configure your S3 Buckets with MFA delete
C) Create a Bucket policy and only allow read only permissions to all users at the bucket level
D) Enable object life cycle policies and configure the data older than 3 months to be archived in Glacier
A) Enable versioning on your S3 Buckets
B) Configure your S3 Buckets with MFA delete
C) Create a Bucket policy and only allow read only permissions to all users at the bucket level
D) Enable object life cycle policies and configure the data older than 3 months to be archived in Glacier

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
33
A user has deployed an application on his private cloud. The user is using his own monitoring tool. He wants to configure that whenever there is an error, the monitoring tool should notify him via SMS. Which of the below mentioned AWS services will help in this scenario?
A) None because the user infrastructure is in the private cloud/
B) AWS SNS
C) AWS SES
D) AWS SMS
A) None because the user infrastructure is in the private cloud/
B) AWS SNS
C) AWS SES
D) AWS SMS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
34
Your company Is moving towards tracking web page users with a small tracking Image loaded on each page Currently you are serving this image out of US-East, but are starting to get concerned about the time It takes to load the image for users on the west coast. What are the two best ways to speed up serving this image? (Choose two.)
A) Use Route 53's Latency Based Routing and serve the image out of US-West-2 as well as US-East-1
B) Serve the image out through CloudFront
C) Serve the image out of S3 so that it isn't being served oft of your web application tier
D) Use EBS PIOPs to serve the image faster out of your EC2 instances
A) Use Route 53's Latency Based Routing and serve the image out of US-West-2 as well as US-East-1
B) Serve the image out through CloudFront
C) Serve the image out of S3 so that it isn't being served oft of your web application tier
D) Use EBS PIOPs to serve the image faster out of your EC2 instances

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
35
A sys admin has created the below mentioned policy and applied to an S3 object named aws. j p g. The aws. j p g is inside a bucket named cloudacademy. What does this policy define? 
A) It is not possible to define a policy at the object level
B) It will make all the objects of the bucket cloudacademy as public
C) It will make the bucket cloudacademy as public
D) the aws. j p g object as public

A) It is not possible to define a policy at the object level
B) It will make all the objects of the bucket cloudacademy as public
C) It will make the bucket cloudacademy as public
D) the aws. j p g object as public

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
36
A user is trying to setup a scheduled scaling activity using Auto Scaling. The user wants to setup the recurring schedule. Which of the below mentioned parameters is not required in this case?
A) Maximum size
B) Auto Scaling group name
C) End time
D) Recurrence value
A) Maximum size
B) Auto Scaling group name
C) End time
D) Recurrence value

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
37
You are running a web-application on AWS consisting of the following components an Elastic Load Balancer (ELB) an Auto-Scaling Group of EC2 instances running Linux/PHP/Apache, and Relational DataBase Service (RDS) MySQL. Which security measures fall into AWS's responsibility?
A) Protect the EC2 instances against unsolicited access by enforcing the principle of least-privilege access
B) Protect against IP spoofing or packet sniffing
C) Assure all communication between EC2 instances and ELB is encrypted
D) Install latest security patches on ELB. RDS and EC2 instances
A) Protect the EC2 instances against unsolicited access by enforcing the principle of least-privilege access
B) Protect against IP spoofing or packet sniffing
C) Assure all communication between EC2 instances and ELB is encrypted
D) Install latest security patches on ELB. RDS and EC2 instances

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
38
An organization has created 50 IAM users. The organization has introduced a new policy which will change the access of an IAM user. How can the organization implement this effectively so that there is no need to apply the policy at the individual user level?
A) Use the IAM groups and add users as per their role to different groups and apply policy to group
B) The user can create a policy and apply it to multiple users in a single go with the AWS CLI
C) Add each user to the IAM role as per their organization role to achieve effective policy setup
D) Use the IAM role and implement access at the role level
A) Use the IAM groups and add users as per their role to different groups and apply policy to group
B) The user can create a policy and apply it to multiple users in a single go with the AWS CLI
C) Add each user to the IAM role as per their organization role to achieve effective policy setup
D) Use the IAM role and implement access at the role level

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
39
A user has created a subnet with VPC and launched an EC2 instance in that subnet with only default settings. Which of the below mentioned options is ready to use on the EC2 instance as soon as it is launched?
A) Elastic IP
B) Private IP
C) Public IP
D) Internet gateway
A) Elastic IP
B) Private IP
C) Public IP
D) Internet gateway

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
40
A user has launched an EC2 instance. The user is planning to setup the CloudWatch alarm. Which of the below mentioned actions is not supported by the CloudWatch alarm?
A) Notify the Auto Scaling launch config to scale up
B) Send an SMS using SNS
C) Notify the Auto Scaling group to scale down
D) Stop the EC2 instance
A) Notify the Auto Scaling launch config to scale up
B) Send an SMS using SNS
C) Notify the Auto Scaling group to scale down
D) Stop the EC2 instance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
41
An organization is using AWS since a few months. The finance team wants to visualize the pattern of AWS spending. Which of the below AWS tool will help for this requirement?
A) AWS Cost Manager
B) AWS Cost Explorer
C) AWS CloudWatch
D) AWS Consolidated Billing
A) AWS Cost Manager
B) AWS Cost Explorer
C) AWS CloudWatch
D) AWS Consolidated Billing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
42
A user has created a VPC with CIDR 20.0.0.0/24. The user has created a public subnet with CIDR 20.0.0.0/25. The user is trying to create the private subnet with CIDR 20.0.0.128/25. Which of the below mentioned statements is true in this scenario?
A) It will not allow the user to create the private subnet due to a CIDR overlap
B) It will allow the user to create a private subnet with CIDR as 20.0.0.128/25
C) This statement is wrong as AWS does not allow CIDR 20.0.0.0/25
D) It will not allow the user to create a private subnet due to a wrong CIDR range
A) It will not allow the user to create the private subnet due to a CIDR overlap
B) It will allow the user to create a private subnet with CIDR as 20.0.0.128/25
C) This statement is wrong as AWS does not allow CIDR 20.0.0.0/25
D) It will not allow the user to create a private subnet due to a wrong CIDR range

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
43
A user is publishing custom metrics to CloudWatch. Which of the below mentioned statements will help the user understand the functionality better?
A) The user can use the CloudWatch Import tool
B) The user should be able to see the data in the console after around 15 minutes
C) If the user is uploading the custom data, the user must supply the namespace, timezone, and metric name as part of the command
D) The user can view as well as upload data using the console, CLI and APIs
A) The user can use the CloudWatch Import tool
B) The user should be able to see the data in the console after around 15 minutes
C) If the user is uploading the custom data, the user must supply the namespace, timezone, and metric name as part of the command
D) The user can view as well as upload data using the console, CLI and APIs

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
44
An organization wants to move to Cloud. They are looking for a secure encrypted database storage option. Which of the below mentioned AWS functionalities helps them to achieve this?
A) AWS MFA with EBS
B) AWS EBS encryption
C) Multi-tier encryption with Redshift
D) AWS S3 server side storage
A) AWS MFA with EBS
B) AWS EBS encryption
C) Multi-tier encryption with Redshift
D) AWS S3 server side storage

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
45
A user is planning to setup notifications on the RDS DB for a snapshot. Which of the below mentioned event categories is not supported by RDS for this snapshot source type?
A) Backup
B) Creation
C) Deletion
D) Restoration
A) Backup
B) Creation
C) Deletion
D) Restoration

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
46
A user is accessing RDS from an application. The user has enabled the Multi AZ feature with the MS SQL RDS DB. During a planned outage how will AWS ensure that a switch from DB to a standby replica will not affect access to the application?
A) RDS will have an internal IP which will redirect all requests to the new DB
B) RDS uses DNS to switch over to stand by replica for seamless transition
C) The switch over changes Hardware so RDS does not need to worry about access
D) RDS will have both the DBs running independently and the user has to manually switch over
A) RDS will have an internal IP which will redirect all requests to the new DB
B) RDS uses DNS to switch over to stand by replica for seamless transition
C) The switch over changes Hardware so RDS does not need to worry about access
D) RDS will have both the DBs running independently and the user has to manually switch over

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
47
A user has launched an ELB which has 5 instances registered with it. The user deletes the ELB by mistake. What will happen to the instances?
A) ELB will ask the user whether to delete the instances or not
B) Instances will be terminated
C) ELB cannot be deleted if it has running instances registered with it
D) Instances will keep running
A) ELB will ask the user whether to delete the instances or not
B) Instances will be terminated
C) ELB cannot be deleted if it has running instances registered with it
D) Instances will keep running

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
48
A user wants to disable connection draining on an existing ELB. Which of the below mentioned statements helps the user disable connection draining on the ELB?
A) The user can only disable connection draining from CLI
B) It is not possible to disable the connection draining feature once enabled
C) The user can disable the connection draining feature from EC2 -> ELB console or from CLI
D) The user needs to stop all instances before disabling connection draining
A) The user can only disable connection draining from CLI
B) It is not possible to disable the connection draining feature once enabled
C) The user can disable the connection draining feature from EC2 -> ELB console or from CLI
D) The user needs to stop all instances before disabling connection draining

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
49
A user has created numerous EBS volumes. What is the general limit for each AWS account for the maximum number of EBS volumes that can be created?
A) 10000
B) 5000
C) 100
D) 1000
A) 10000
B) 5000
C) 100
D) 1000

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
50
A user has created an ELB with three instances. How many security groups will ELB create by default?
A) 3
B) 5
C) 2
D) 1
A) 3
B) 5
C) 2
D) 1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
51
A user has launched 10 instances from the same AMI ID using Auto Scaling. The user is trying to see the average CPU utilization across all instances of the last 2 weeks under the CloudWatch console. How can the user achieve this?
A) View the Auto Scaling CPU metrics
B) Aggregate the data over the instance AMI ID
C) The user has to use the CloudWatchanalyser to find the average data across instances
D) It is not possible to see the average CPU utilization of the same AMI ID since the instance ID is different
A) View the Auto Scaling CPU metrics
B) Aggregate the data over the instance AMI ID
C) The user has to use the CloudWatchanalyser to find the average data across instances
D) It is not possible to see the average CPU utilization of the same AMI ID since the instance ID is different

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
52
A sys admin has created a shopping cart application and hosted it on EC2. The EC2 instances are running behind ELB. The admin wants to ensure that the end user request will always go to the EC2 instance where the user session has been created. How can the admin configure this?
A) Enable ELB cross zone load balancing
B) Enable ELB cookie setup
C) Enable ELB sticky session
D) Enable ELB connection draining
A) Enable ELB cross zone load balancing
B) Enable ELB cookie setup
C) Enable ELB sticky session
D) Enable ELB connection draining

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
53
A user has created a VPC with CIDR 20.0.0.0/16 with only a private subnet and VPN connection using the VPC wizard. The user wants to connect to the instance in a private subnet over SSH. How should the user define the security rule for SSH?
A) Allow Inbound traffic on port 22 from the user's network
B) The user has to create an instance in EC2 Classic with an elastic IP and configure the security group of a private subnet to allow SSH from that elastic IP
C) The user can connect to a instance in a private subnet using the NAT instance
D) Allow Inbound traffic on port 80 and 22 to allow the user to connect to a private subnet over the Internet
A) Allow Inbound traffic on port 22 from the user's network
B) The user has to create an instance in EC2 Classic with an elastic IP and configure the security group of a private subnet to allow SSH from that elastic IP
C) The user can connect to a instance in a private subnet using the NAT instance
D) Allow Inbound traffic on port 80 and 22 to allow the user to connect to a private subnet over the Internet

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
54
An organization has configured the custom metric upload with CloudWatch. The organization has given permission to its employees to upload data using CLI as well SDK. How can the user track the calls made to CloudWatch?
A) The user can enable logging with CloudWatch which logs all the activities
B) Use CloudTrail to monitor the API calls
C) Create an IAM user and allow each user to log the data using the S3 bucket
D) Enable detailed monitoring with CloudWatch
A) The user can enable logging with CloudWatch which logs all the activities
B) Use CloudTrail to monitor the API calls
C) Create an IAM user and allow each user to log the data using the S3 bucket
D) Enable detailed monitoring with CloudWatch

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
55
A sys admin is maintaining an application on AWS. The application is installed on EC2 and user has configured ELB and Auto Scaling. Considering future load increase, the user is planning to launch new servers proactively so that they get registered with ELB. How can the user add these instances with Auto Scaling?
A) Increase the desired capacity of the Auto Scaling group
B) Increase the maximum limit of the Auto Scaling group
C) Launch an instance manually and register it with ELB on the fly
D) Decrease the minimum limit of the Auto Scaling group
A) Increase the desired capacity of the Auto Scaling group
B) Increase the maximum limit of the Auto Scaling group
C) Launch an instance manually and register it with ELB on the fly
D) Decrease the minimum limit of the Auto Scaling group

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
56
A system admin is planning to setup event notifications on RDS. Which of the below mentioned services will help the admin setup notifications?
A) AWS SES
B) AWS Cloudtrail
C) AWS Cloudwatch
D) AWS SNS
A) AWS SES
B) AWS Cloudtrail
C) AWS Cloudwatch
D) AWS SNS

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
57
An admin is planning to monitor the ELB. Which of the below mentioned services does not help the admin capture the monitoring information about the ELB activity?
A) ELB Access logs
B) ELB health check
C) CloudWatch metrics
D) ELB API calls with CloudTrail
A) ELB Access logs
B) ELB health check
C) CloudWatch metrics
D) ELB API calls with CloudTrail

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
58
A user has configured the AWS CloudWatch alarm for estimated usage charges in the US East region. Which of the below mentioned statements is not true with respect to the estimated charges?
A) It will store the estimated charges data of the last 14 days
B) It will include the estimated charges of every AWS service
C) The metric data will represent the data of all the regions
D) The metric data will show data specific to that region
A) It will store the estimated charges data of the last 14 days
B) It will include the estimated charges of every AWS service
C) The metric data will represent the data of all the regions
D) The metric data will show data specific to that region

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
59
A user has a refrigerator plant. The user is measuring the temperature of the plant every 15 minutes. If the user wants to send the data to CloudWatch to view the data visually, which of the below mentioned statements is true with respect to the information given above?
A) The user needs to use AWS CLI or API to upload the data
B) The user can use the AWS Import Export facility to import data to CloudWatch
C) The user will upload data from the AWS console
D) The user cannot upload data to CloudWatch since it is not an AWS service metric
A) The user needs to use AWS CLI or API to upload the data
B) The user can use the AWS Import Export facility to import data to CloudWatch
C) The user will upload data from the AWS console
D) The user cannot upload data to CloudWatch since it is not an AWS service metric

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
60
A user has stored data on an encrypted EBS volume. The user wants to share the data with his friend's AWS account. How can user achieve this?
A) Create an AMI from the volume and share the AMI
B) Copy the data to an unencrypted volume and then share
C) Take a snapshot and share the snapshot with a friend
D) If both the accounts are using the same encryption key then the user can share the volume directly
A) Create an AMI from the volume and share the AMI
B) Copy the data to an unencrypted volume and then share
C) Take a snapshot and share the snapshot with a friend
D) If both the accounts are using the same encryption key then the user can share the volume directly

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
61
A user wants to make so that whenever the CPU utilization of the AWS EC2 instance is above 90%, the redlight of his bedroom turns on. Which of the below mentioned AWS services is helpful for this purpose?
A) AWS CloudWatch + AWS SES
B) AWS CloudWatch + AWS SNS
C) None. It is not possible to configure the light with the AWS infrastructure services
D) AWS CloudWatch and a dedicated software turning on the light
A) AWS CloudWatch + AWS SES
B) AWS CloudWatch + AWS SNS
C) None. It is not possible to configure the light with the AWS infrastructure services
D) AWS CloudWatch and a dedicated software turning on the light

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
62
A user has created a VPC with CIDR 20.0.0.0/16. The user has created public and VPN only subnets along with hardware VPN access to connect to the user's datacenter. The user wants to make so that all traffic coming to the public subnet follows the organization's proxy policy. How can the user make this happen?
A) Setting up a NAT with the proxy protocol and configure that the public subnet receives traffic from NAT
B) Setting up a proxy policy in the internet gateway connected with the public subnet
C) It is not possible to setup the proxy policy for a public subnet
D) Setting the route table and security group of the public subnet which receives traffic from a virtual private gateway
A) Setting up a NAT with the proxy protocol and configure that the public subnet receives traffic from NAT
B) Setting up a proxy policy in the internet gateway connected with the public subnet
C) It is not possible to setup the proxy policy for a public subnet
D) Setting the route table and security group of the public subnet which receives traffic from a virtual private gateway

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
63
An organization (Account ID 123412341234. has attached the below mentioned IAM policy to a user. What does this policy statement entitle the user to perform? 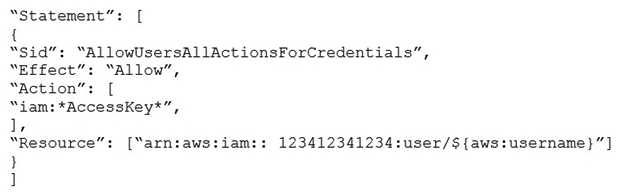
A) The policy allows the IAM user to modify all IAM users' access keys using the console, SDK, CLI or APIs
B) The policy allows the IAM user to modify all IAM users' credentials using the console, SDK, CLI or APIs
C) The policy allows the IAM user to modify all credentials using only the console
D) The policy allows the IAM user to modify the IAM user's own credentials using the console, SDK, CLI or APIs

A) The policy allows the IAM user to modify all IAM users' access keys using the console, SDK, CLI or APIs
B) The policy allows the IAM user to modify all IAM users' credentials using the console, SDK, CLI or APIs
C) The policy allows the IAM user to modify all credentials using only the console
D) The policy allows the IAM user to modify the IAM user's own credentials using the console, SDK, CLI or APIs

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
64
A user has configured Elastic Load Balancing by enabling a Secure Socket Layer (SSL) negotiation configuration known as a Security Policy. Which of the below mentioned options is not part of this secure policy while negotiating the SSL connection between the user and the client?
A) SSL Protocols
B) Client Order Preference
C) SSL Ciphers
D) Server Order Preference
A) SSL Protocols
B) Client Order Preference
C) SSL Ciphers
D) Server Order Preference

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
65
A user has created an ELB with Auto Scaling. Which of the below mentioned offerings from ELB helps the user to stop sending new requests traffic from the load balancer to the EC2 instance when the instance is being deregistered while continuing in-flight requests?
A) ELB sticky session
B) ELB deregistration check
C) ELB connection draining
D) ELB auto registration Off
A) ELB sticky session
B) ELB deregistration check
C) ELB connection draining
D) ELB auto registration Off

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
66
A user is trying to configure the CloudWatch billing alarm. Which of the below mentioned steps should be performed by the user for the first time alarm creation in the AWS Account Management section?
A) Enable Receiving Billing Reports
B) Enable Receiving Billing Alerts
C) Enable AWS billing utility
D) Enable CloudWatch Billing Threshold
A) Enable Receiving Billing Reports
B) Enable Receiving Billing Alerts
C) Enable AWS billing utility
D) Enable CloudWatch Billing Threshold

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
67
A user has received a message from the support team that an issue occurred 1 week back between 3 AM to 4 AM and the EC2 server was not reachable. The user is checking the CloudWatch metrics of that instance. How can the user find the data easily using the CloudWatch console?
A) The user can find the data by giving the exact values in the time Tab under CloudWatch metrics
B) The user can find the data by filtering values of the last 1 week for a 1 hour period in the Relative tab under CloudWatch metrics
C) It is not possible to find the exact time from the console. The user has to use CLI to provide the specific time
D) The user can find the data by giving the exact values in the Absolute tab under CloudWatch metrics
A) The user can find the data by giving the exact values in the time Tab under CloudWatch metrics
B) The user can find the data by filtering values of the last 1 week for a 1 hour period in the Relative tab under CloudWatch metrics
C) It is not possible to find the exact time from the console. The user has to use CLI to provide the specific time
D) The user can find the data by giving the exact values in the Absolute tab under CloudWatch metrics

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
68
A user has launched two EBS backed EC2 instances in the US-East-1a region. The user wants to change the zone of one of the instances. How can the user change it?
A) Stop one of the instances and change the availability zone
B) The zone can only be modified using the AWS CLI
C) From the AWS EC2 console, select the Actions - > Change zones and specify new zone
D) Create an AMI of the running instance and launch the instance in a separate AZ
A) Stop one of the instances and change the availability zone
B) The zone can only be modified using the AWS CLI
C) From the AWS EC2 console, select the Actions - > Change zones and specify new zone
D) Create an AMI of the running instance and launch the instance in a separate AZ

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
69
A user has created a queue named "myqueue" in US-East region with AWS SQS. The user's AWS account ID is 123456789012. If the user wants to perform some action on this queue, which of the below Queue URL should he use?
A) http://sqs.us-east-1.amazonaws.com/123456789012/myqueue
B) http://sqs.amazonaws.com/123456789012/myqueue
C) http://sqs. 123456789012.us-east-1.amazonaws.com/myqueue
D) http:// 123456789012.sqs. us-east-1.amazonaws.com/myqueue
A) http://sqs.us-east-1.amazonaws.com/123456789012/myqueue
B) http://sqs.amazonaws.com/123456789012/myqueue
C) http://sqs. 123456789012.us-east-1.amazonaws.com/myqueue
D) http:// 123456789012.sqs. us-east-1.amazonaws.com/myqueue

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
70
An organization is planning to use AWS for 5 different departments. The finance department is responsible to pay for all the accounts. However, they want the cost separation for each account to map with the right cost center. How can the finance department achieve this?
A) Create 5 separate accounts and make them a part of one consolidate billing
B) Create 5 separate accounts and use the IAM cross account access with the roles for better management
C) Create 5 separate IAM users and set a different policy for their access
D) Create 5 separate IAM groups and add users as per the department's employees
A) Create 5 separate accounts and make them a part of one consolidate billing
B) Create 5 separate accounts and use the IAM cross account access with the roles for better management
C) Create 5 separate IAM users and set a different policy for their access
D) Create 5 separate IAM groups and add users as per the department's employees

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
71
A user has configured ELB with two EBS backed EC2 instances. The user is trying to understand the DNS access and IP support for ELB. Which of the below mentioned statements may not help the user understand the IP mechanism supported by ELB?
A) The client can connect over IPV4 or IPV6 using Dualstack
B) ELB DNS supports both IPV4 and IPV6
C) Communication between the load balancer and back-end instances is always through IPV4
D) The ELB supports either IPV4 or IPV6 but not both
A) The client can connect over IPV4 or IPV6 using Dualstack
B) ELB DNS supports both IPV4 and IPV6
C) Communication between the load balancer and back-end instances is always through IPV4
D) The ELB supports either IPV4 or IPV6 but not both

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
72
A user has launched an EBS backed EC2 instance. What will be the difference while performing the restart or stop/start options on that instance?
A) For restart it does not charge for an extra hour, while every stop/start it will be charged as a separate hour
B) Every restart is charged by AWS as a separate hour, while multiple start/stop actions during a single hour will be counted as a single hour
C) For every restart or start/stop it will be charged as a separate hour
D) For restart it charges extra only once, while for every stop/start it will be charged as a separate hour
A) For restart it does not charge for an extra hour, while every stop/start it will be charged as a separate hour
B) Every restart is charged by AWS as a separate hour, while multiple start/stop actions during a single hour will be counted as a single hour
C) For every restart or start/stop it will be charged as a separate hour
D) For restart it charges extra only once, while for every stop/start it will be charged as a separate hour

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
73
You are managing the AWS account of a big organization. The organization has more than 1000+ employees and they want to provide access to the various services to most of the employees. Which of the below mentioned options is the best possible solution in this case?
A) The user should create a separate IAM user for each employee and provide access to them as per the policy
B) The user should create an IAM role and attach STS with the role. The user should attach that role to the EC2 instance and setup AWS authentication on that server
C) The user should create IAM groups as per the organization's departments and add each user to the group for better access control
D) Attach an IAM role with the organization's authentication service to authorize each user for various AWS services
A) The user should create a separate IAM user for each employee and provide access to them as per the policy
B) The user should create an IAM role and attach STS with the role. The user should attach that role to the EC2 instance and setup AWS authentication on that server
C) The user should create IAM groups as per the organization's departments and add each user to the group for better access control
D) Attach an IAM role with the organization's authentication service to authorize each user for various AWS services

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
74
A user is launching an instance. He is on the "Tag the instance" screen. Which of the below mentioned information will not help the user understand the functionality of an AWS tag?
A) Each tag will have a key and value
B) The user can apply tags to the S3 bucket
C) The maximum value of the tag key length is 64 unicode characters
D) AWS tags are used to find the cost distribution of various resources
A) Each tag will have a key and value
B) The user can apply tags to the S3 bucket
C) The maximum value of the tag key length is 64 unicode characters
D) AWS tags are used to find the cost distribution of various resources

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
75
A user has configured CloudWatch monitoring on an EBS backed EC2 instance. If the user has not attached any additional device, which of the below mentioned metrics will always show a 0 value?
A) DiskReadBytes
B) NetworkIn
C) NetworkOut
D) CPUUtilization
A) DiskReadBytes
B) NetworkIn
C) NetworkOut
D) CPUUtilization

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
76
A user has setup an EBS backed instance and a CloudWatch alarm when the CPU utilization is more than 65%. The user has setup the alarm to watch it for 5 periods of 5 minutes each. The CPU utilization is 60% between 9 AM to 6 PM. The user has stopped the EC2 instance for 15 minutes between 11 AM to 11:15 AM. What will be the status of the alarm at 11:30 AM?
A) Alarm
B) OK
C) Insufficient Data
D) Error
A) Alarm
B) OK
C) Insufficient Data
D) Error

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
77
A sys admin is trying to understand EBS snapshots. Which of the below mentioned statements will not be useful to the admin to understand the concepts about a snapshot?
A) The snapshot is synchronous
B) It is recommended to stop the instance before taking a snapshot for consistent data
C) The snapshot is incremental
D) The snapshot captures the data that has been written to the hard disk when the snapshot command was executed
A) The snapshot is synchronous
B) It is recommended to stop the instance before taking a snapshot for consistent data
C) The snapshot is incremental
D) The snapshot captures the data that has been written to the hard disk when the snapshot command was executed

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
78
A user is checking the CloudWatch metrics from the AWS console. The user notices that the CloudWatch data is coming in UTC. The user wants to convert the data to a local time zone. How can the user perform this?
A) In the CloudWatch dashboard the user should set the local time zone so that CloudWatch shows the data only in the local time zone
B) In the CloudWatch console select the local time zone under the Time Range tab to view the data as per the local timezone
C) The CloudWatch data is always in UTC; the user has to manually convert the data
D) The user should have send the local time zone while uploading the data so that CloudWatch will show the data only in the local time zone
A) In the CloudWatch dashboard the user should set the local time zone so that CloudWatch shows the data only in the local time zone
B) In the CloudWatch console select the local time zone under the Time Range tab to view the data as per the local timezone
C) The CloudWatch data is always in UTC; the user has to manually convert the data
D) The user should have send the local time zone while uploading the data so that CloudWatch will show the data only in the local time zone

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
79
A user has launched an EC2 instance from an instance store backed AMI. The infrastructure team wants to create an AMI from the running instance. Which of the below mentioned steps will not be performed while creating the AMI?
A) Define the AMI launch permissions
B) Upload the bundled volume
C) Register the AMI
D) Bundle the volume
A) Define the AMI launch permissions
B) Upload the bundled volume
C) Register the AMI
D) Bundle the volume

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck
80
An organization has setup consolidated billing with 3 different AWS accounts. Which of the below mentioned advantages will organization receive in terms of the AWS pricing?
A) The consolidated billing does not bring any cost advantage for the organization
B) All AWS accounts will be charged for S3 storage by combining the total storage of each account
C) The EC2 instances of each account will receive a total of 750*3 micro instance hours free
D) The free usage tier for all the 3 accounts will be 3 years and not a single year
A) The consolidated billing does not bring any cost advantage for the organization
B) All AWS accounts will be charged for S3 storage by combining the total storage of each account
C) The EC2 instances of each account will receive a total of 750*3 micro instance hours free
D) The free usage tier for all the 3 accounts will be 3 years and not a single year

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 976 في هذه المجموعة.
فتح الحزمة
k this deck








