Deck 10: System Architecture
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/78
العب
ملء الشاشة (f)
Deck 10: System Architecture
1
A _____ follows Internet design protocols and enables a company to integrate new applications into its ecommerce strategy.
A) web-centric architecture
B) thin client
C) data processing center
D) corporate portal
A) web-centric architecture
B) thin client
C) data processing center
D) corporate portal
A
2
An information system includes _____, which are programs that handle the input, manage the processing logic, and provide the required output.
A) applications
B) clients
C) data frames
D) magnetic tapes
A) applications
B) clients
C) data frames
D) magnetic tapes
A
3
Web 2.0 is a reference to a more technically advanced version of the current web.
False
4
Many companies are extending internal enterprise resource planning (ERP) systems to their suppliers and customers, using a concept called _____.
A) supply chain management (SCM)
B) stand-alone computing
C) cloud computing
D) behavioral management
A) supply chain management (SCM)
B) stand-alone computing
C) cloud computing
D) behavioral management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
5
Implementation of early client/server systems was expensive because clients needed more powerful hardware and software to handle shared processing tasks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
6
In contrast to a centralized system, a client/server design separates applications and data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
7
_____ is the measure of a system's ability to expand, change, or downsize easily to meet the changing needs of a business enterprise.
A) Transparency
B) Scalability
C) Redundancy
D) Interoperability
A) Transparency
B) Scalability
C) Redundancy
D) Interoperability

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
8
A fat client, also called a thick client, design locates all or most of the application processing logic at the server.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
9
Even if a user's Internet connection becomes unavailable, the user will still be able to access certain cloud-based services.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
10
The cloud computing concept envisions a cloud of remote computers that provide a total online software and data environment that is hosted by third parties.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
11
_____ translates the logical design of an information system into a physical structure that includes hardware, software, network support, and processing methods.
A) Legacy data
B) Multipath design
C) System architecture
D) System file checker
A) Legacy data
B) Multipath design
C) System architecture
D) System file checker

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
12
Security is especially important when data or processing is performed at a centralized facility, rather than at remote locations.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
13
In online processing, data is managed and processed in groups.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
14
A client is a computer that supplies data, processing services, or other support to one or more computers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
15
As the size of a business changes, it is easier to alter the capability of a large-scale central server than it is to adjust the number of clients and the processing functions they perform.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
16
_____ establishes a company-wide strategy for IT resources and specific standards for data, processing, network, and user interface design.
A) Legacy data
B) Stand-alone computing
C) Enterprise resource planning (ERP)
D) Scalability
A) Legacy data
B) Stand-alone computing
C) Enterprise resource planning (ERP)
D) Scalability

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
17
A web-based application encounters all of the connectivity and compatibility problems that typically arise when different hardware environments are involved.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
18
The advantage of the application logic layer is that a three-tier design enhances overall performance by reducing the data server's workload.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
19
A three-tier design includes a middle layer between the client and server that processes the client requests and translates them into data access commands that can be understood and carried out by the server.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
20
A main advantage of enterprise resource planning (ERP) is that it describes a _____ that ensures connectivity and easy integration of future systems, including in-house software and commercial packages.
A) data frame
B) platform
C) bandwidth
D) hub
A) data frame
B) platform
C) bandwidth
D) hub

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
21
Most companies resolved the problems of stand-alone computing by joining clients into a _____ that allows sharing of data and hardware resources.
A) storage area network (SAN)
B) wide area network (WAN)
C) desk area network (DAN)
D) local area network (LAN)
A) storage area network (SAN)
B) wide area network (WAN)
C) desk area network (DAN)
D) local area network (LAN)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
22
Cloud computing provides _____, which matches resources to needs at any given time.
A) roaming service
B) scaling on demand
C) point-of-sale (POS) terminal
D) resource management
A) roaming service
B) scaling on demand
C) point-of-sale (POS) terminal
D) resource management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
23
_____ is the amount of data that can be transferred in a fixed time period.
A) Resolution
B) Dimensionality
C) Topology
D) Bandwidth
A) Resolution
B) Dimensionality
C) Topology
D) Bandwidth

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
24
A(n) _____ is a web-based repository of information that anyone can access, contribute to, or modify.
A) blog
B) iOS
C) wiki
D) portal
A) blog
B) iOS
C) wiki
D) portal

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
25
A _____ is an entrance to a multifunction website.
A) semantic web
B) batch link
C) portal
D) protocol
A) semantic web
B) batch link
C) portal
D) protocol

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
26
In a multi-tier system, special utility software called _____ enables the tiers to communicate and pass data back and forth.
A) shareware
B) middleware
C) groupware
D) malware
A) shareware
B) middleware
C) groupware
D) malware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
27
A new system might have to interface with one or more _____, which are older systems that use outdated technology.
A) enterprise resource planning (ERP) systems
B) mission-critical systems
C) legacy systems
D) intrusion detection systems
A) enterprise resource planning (ERP) systems
B) mission-critical systems
C) legacy systems
D) intrusion detection systems

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
28
A system design where the server performs all the processing is described as _____.
A) mainframe architecture
B) dataflow architecture
C) workstation architecture
D) cache architecture
A) mainframe architecture
B) dataflow architecture
C) workstation architecture
D) cache architecture

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
29
A _____ locates all or most of the processing logic on the server.
A) thin client
B) batch client
C) topological client
D) portal client
A) thin client
B) batch client
C) topological client
D) portal client

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
30
In addition to centralized data processing, the earliest systems performed all data input and output at a central location, often called a _____.
A) web-centric hub
B) thin client
C) data processing center
D) portal
A) web-centric hub
B) thin client
C) data processing center
D) portal

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
31
The way a network is configured is called the _____.
A) network orientation
B) network baseline
C) network topology
D) network index
A) network orientation
B) network baseline
C) network topology
D) network index

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
32
A(n) _____ provides access for customers, employees, suppliers, and the public.
A) mainframe architecture
B) corporate portal
C) application server
D) thick client
A) mainframe architecture
B) corporate portal
C) application server
D) thick client

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
33
When an individual user works in _____, the workstation performs all the functions of a server by storing, accessing, and processing data as well as providing a user interface.
A) safe mode
B) stand-alone mode
C) quirks mode
D) mission-critical mode
A) safe mode
B) stand-alone mode
C) quirks mode
D) mission-critical mode

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
34
Many companies had an installed base of data, called _____, which was difficult to access and transport to a client/server environment.
A) legacy data
B) advanced data
C) primary data
D) qualitative data
A) legacy data
B) advanced data
C) primary data
D) qualitative data

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
35
When developing e-business systems, an in-house solution usually requires a _____ for a company that must adapt quickly in a dynamic ecommerce environment.
A) smaller initial investment and provides more flexibility
B) smaller initial investment but provides less flexibility
C) greater initial investment but provides more flexibility
D) greater initial investment and provides less flexibility
A) smaller initial investment and provides more flexibility
B) smaller initial investment but provides less flexibility
C) greater initial investment but provides more flexibility
D) greater initial investment and provides less flexibility

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
36
In a client/server architecture, just as processing can be done at various places, data can be stored in more than one location using a _____.
A) distributed data frame
B) distributed supply chain management (DSCM) scheme
C) distributed database management system (DDBMS)
D) distributed data dictionary
A) distributed data frame
B) distributed supply chain management (DSCM) scheme
C) distributed database management system (DDBMS)
D) distributed data dictionary

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
37
In a(n) _____, the remote user's keystrokes are transmitted to the mainframe, which responds by sending screen output back to the user's screen.
A) closed design
B) distributed design
C) open design
D) centralized design
A) closed design
B) distributed design
C) open design
D) centralized design

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
38
The _____ describes how data actually moves from an application on one computer to an application on another networked computer.
A) OSI (Open Systems Interconnection) model
B) five forces model
C) object-oriented database model
D) subscription model
A) OSI (Open Systems Interconnection) model
B) five forces model
C) object-oriented database model
D) subscription model

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
39
The term _____ generally refers to systems that divide processing between one or more networked clients and a central server.
A) fat client
B) glueware
C) client/server
D) mission-critical
A) fat client
B) glueware
C) client/server
D) mission-critical

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
40
Company-wide systems that connect one or more local area networks (LANs) or wide area networks (WANs) are called _____.
A) legacy systems
B) distributed systems
C) web-centric systems
D) mission-critical systems
A) legacy systems
B) distributed systems
C) web-centric systems
D) mission-critical systems

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
41
The _____ standard uses multiple input/multiple output (MIMO) technology to boost performance.
A) 802.11a
B) 802.11b
C) 802.11cn
D) 802.11ac
A) 802.11a
B) 802.11b
C) 802.11cn
D) 802.11ac

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
42
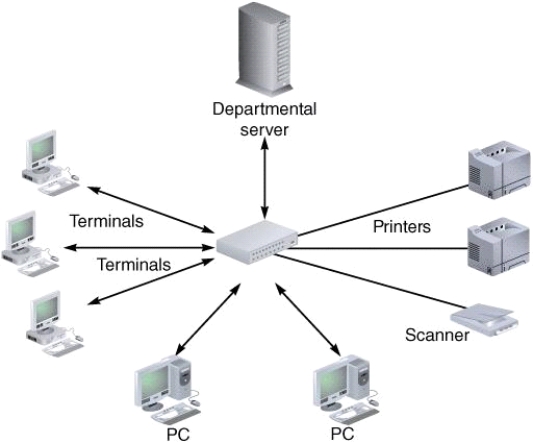
At the center of the network, shown in the accompanying figure, is the _____, which manages the network and acts as a communications conduit for all network traffic.
A) log
B) scale
C) switch
D) portal

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
43
_____ relies on collective data paths to increase bandwidth and range.
A) Supply chain management (SCM)
B) Microsoft Visio
C) Bluetooth
D) Multiple input/multiple output (MIMO) technology
A) Supply chain management (SCM)
B) Microsoft Visio
C) Bluetooth
D) Multiple input/multiple output (MIMO) technology

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
44
In its wireless configuration, the _____ is similar to a hub in the local area network (LAN) star topology, except it provides network services to wireless clients instead of wired clients.
A) Wi-Fi Alliance
B) access point
C) fat client
D) data frame
A) Wi-Fi Alliance
B) access point
C) fat client
D) data frame

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
45
The _____ allows the expansion of wireless access over a wide area.
A) Basic Service Set (BSS) topology
B) Extended Service Set (ESS) topology
C) physical topology
D) logical topology
A) Basic Service Set (BSS) topology
B) Extended Service Set (ESS) topology
C) physical topology
D) logical topology

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
46
The _____ was formed in 1999 to certify interoperability of wireless network products based on IEEE 802.11 specifications.
A) Wi-Fi Alliance
B) Institute of Electrical and Electronics Engineers (IEEE)
C) World Wide Web Consortium (W3C)
D) Wi-MAX
A) Wi-Fi Alliance
B) Institute of Electrical and Electronics Engineers (IEEE)
C) World Wide Web Consortium (W3C)
D) Wi-MAX

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
47
In a _____, one or more powerful servers control the network, and departmental servers control lower levels of processing and network devices.
A) hierarchical network
B) star network
C) bus network
D) ring network
A) hierarchical network
B) star network
C) bus network
D) ring network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
48
Wireless network speed is measured in _____.
A) Bps (bits per second)
B) Kbps (kilobytes per second)
C) Gbps (gigabits per second)
D) Tbps (terabytes per second)
A) Bps (bits per second)
B) Kbps (kilobytes per second)
C) Gbps (gigabits per second)
D) Tbps (terabytes per second)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
49
In a typical system design specification, the _____ section contains the complete design for a new system, including the user interface, outputs, inputs, files, databases, and network specifications.
A) system components
B) system summaries
C) implementation requirements
D) implementation environments
A) system components
B) system summaries
C) implementation requirements
D) implementation environments

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
50

A _____, such as that illustrated in the accompanying figure, has a central networking device that manages the network.
A) hierarchical network
B) star network
C) bus network
D) ring network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
51
A _____ is relatively inexpensive to install and is well-suited to workgroups and users who are not anchored to a specific desk or location.
A) local area network (LAN)
B) wireless local area network (WLAN)
C) metropolitan area network (MAN)
D) storage area network (SAN)
A) local area network (LAN)
B) wireless local area network (WLAN)
C) metropolitan area network (MAN)
D) storage area network (SAN)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
52
The system design specification is a document that presents the complete design for a new information system, along with _____ for completing the next SDLC phase - systems implementation.
A) access points
B) web-based components
C) detailed costs
D) data frames
A) access points
B) web-based components
C) detailed costs
D) data frames

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
53
A _____ resembles a group of computers in which data flows in only one direction from one device to the next.
A) hierarchical network
B) star network
C) bus network
D) ring network
A) hierarchical network
B) star network
C) bus network
D) ring network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
54
_____ describes the actual network cabling and connections.
A) Logical topology
B) Bus topology
C) Star topology
D) Physical topology
A) Logical topology
B) Bus topology
C) Star topology
D) Physical topology

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
55
_____ describes the way the components in a network interact.
A) Interactive topology
B) Physical topology
C) Engagement topology
D) Logical topology
A) Interactive topology
B) Physical topology
C) Engagement topology
D) Logical topology

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
56
A form of wireless transmission called _____ is very popular for short-distance wireless communication that does not require high power.
A) Bluetooth
B) Microsoft Visio
C) multipath design
D) Wi-MAX
A) Bluetooth
B) Microsoft Visio
C) multipath design
D) Wi-MAX

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
57
In a _____, a single communication path connects the network server, departmental servers, workstations, and peripheral devices.
A) hierarchical network
B) star network
C) bus network
D) ring network
A) hierarchical network
B) star network
C) bus network
D) ring network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
58
In a typical system design specification, the _____ section describes the constraints, or conditions, affecting a system, including any requirements that involve operations, hardware, systems software, or security.
A) time and cost estimates
B) system environment
C) executive summary
D) implementation requirements
A) time and cost estimates
B) system environment
C) executive summary
D) implementation requirements

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
59
Which of the following configurations has a central wireless device that is used to serve all wireless clients?
A) The Basic Service Set (BSS)
B) A point-of-sale (POS) terminal
C) A data frame
D) The OSI (Open Systems Interconnection) model
A) The Basic Service Set (BSS)
B) A point-of-sale (POS) terminal
C) A data frame
D) The OSI (Open Systems Interconnection) model

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
60
A disadvantage of a bus network is that _____.
A) performance can decline as more users and devices are added
B) devices cannot be attached or detached without disturbing the rest of the network
C) failure in one workstation necessarily affects other workstations on the network
D) data flows in only one direction from one computer to the next
A) performance can decline as more users and devices are added
B) devices cannot be attached or detached without disturbing the rest of the network
C) failure in one workstation necessarily affects other workstations on the network
D) data flows in only one direction from one computer to the next

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
61
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is used to connect any network topology to a larger, dissimilar network.
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is used to connect any network topology to a larger, dissimilar network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
62
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is a process that automatically allows a wireless client to associate with a stronger access point.
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is a process that automatically allows a wireless client to associate with a stronger access point.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
63
In a typical system design specification, in the _____ section, start-up processing, initial data entry or acquisition, user training requirements, and software test plans are specified.?
A) system environment
B) executive summary
C) system components
D) implementation requirements
A) system environment
B) executive summary
C) system components
D) implementation requirements

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
64
Which of the following sections are included in a typical system design specification?
A) Management summary
B) Time and cost estimates
C) Processing options
D) Implementation requirements
A) Management summary
B) Time and cost estimates
C) Processing options
D) Implementation requirements

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
65
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is important in implementing systems that are volume-related, such as transaction processing systems.
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is important in implementing systems that are volume-related, such as transaction processing systems.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
66
Case 10-1
Sam has been asked to classify a number of different processing systems that his consultancy's client uses.
Sam is analyzing a processing system and he has determined that it is an online processing system and not a batch processing system. Which of the following observations helped him determine the system?
A) The system allowing delays in transactions
B) The system's tasks running on a predetermined schedule, without user involvement
C) The system avoiding a constant dialog between the user and the system
D) The system processing transactions completely when and where they occur
Sam has been asked to classify a number of different processing systems that his consultancy's client uses.
Sam is analyzing a processing system and he has determined that it is an online processing system and not a batch processing system. Which of the following observations helped him determine the system?
A) The system allowing delays in transactions
B) The system's tasks running on a predetermined schedule, without user involvement
C) The system avoiding a constant dialog between the user and the system
D) The system processing transactions completely when and where they occur

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
67
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is another name for the wireless configuration in which a central wireless device is used to serve all wireless clients.
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is another name for the wireless configuration in which a central wireless device is used to serve all wireless clients.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
68
Case 10-2
Neil holds a discussion session with his clients. He recommends the kinds of network topologies the clients should consider, according to their circumstances.
Neil's client wants to follow the current trends with everyone else in terms of speed and versatility. He is risk-averse and wants to leverage the most popular local area network (LAN) topology. Which of the following will Neil recommend to this client?
A) A bus network
B) A ring network
C) A hub network
D) A star network
Neil holds a discussion session with his clients. He recommends the kinds of network topologies the clients should consider, according to their circumstances.
Neil's client wants to follow the current trends with everyone else in terms of speed and versatility. He is risk-averse and wants to leverage the most popular local area network (LAN) topology. Which of the following will Neil recommend to this client?
A) A bus network
B) A ring network
C) A hub network
D) A star network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
69
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
Compared to mainframe architecture, these increase concerns about data security and integrity because many individual clients require access to perform processing.
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
Compared to mainframe architecture, these increase concerns about data security and integrity because many individual clients require access to perform processing.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
70
Case 10-1
Sam has been asked to classify a number of different processing systems that his consultancy's client uses.
Sam is looking at a second system. This system, he determines, is a batch processing system. Which of the following observations helped him determine the system?
A) Users accessing data randomly
B) The information system at the client site being available whenever necessary, supporting business functions
C) The system at the client side processing transactions completely when and where they occur
D) The IT operations group at the client site running programs at a predetermined schedule, without user involvement
Sam has been asked to classify a number of different processing systems that his consultancy's client uses.
Sam is looking at a second system. This system, he determines, is a batch processing system. Which of the following observations helped him determine the system?
A) Users accessing data randomly
B) The information system at the client site being available whenever necessary, supporting business functions
C) The system at the client side processing transactions completely when and where they occur
D) The IT operations group at the client site running programs at a predetermined schedule, without user involvement

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
71
The characteristics of online processing systems are that _____.
A) users interact directly with the information system
B) the systems avoid a constant dialog between the user and the system
C) users can access data randomly
D) the systems process transactions completely when and where they occur
A) users interact directly with the information system
B) the systems avoid a constant dialog between the user and the system
C) users can access data randomly
D) the systems process transactions completely when and where they occur

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
72
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is a standard that increased bandwidth to 54 Mbps.
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is a standard that increased bandwidth to 54 Mbps.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
73
List the guidelines for in-house ecommerce site development.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
74
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is a device that connects network segments, determines the most efficient data path, and guides the flow of data.
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
This is a device that connects network segments, determines the most efficient data path, and guides the flow of data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
75
Case 10-2
Neil holds a discussion session with his clients. He recommends the kinds of network topologies the clients should consider, according to their circumstances.
One of Neil's clients, Ann, is looking for a highly redundant and reliable network topology Ann is not particularly concerned about the expenditure that would go behind the installation and maintenance of the network. Which of the following networks is Neil most likely to recommend?
A) A mesh network
B) A bus network
C) A star network
D) A hub network
Neil holds a discussion session with his clients. He recommends the kinds of network topologies the clients should consider, according to their circumstances.
One of Neil's clients, Ann, is looking for a highly redundant and reliable network topology Ann is not particularly concerned about the expenditure that would go behind the installation and maintenance of the network. Which of the following networks is Neil most likely to recommend?
A) A mesh network
B) A bus network
C) A star network
D) A hub network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
76
Matching
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
These are broadband wireless communications protocols for metropolitan area networks (MANs).
Identify the letter of the choice that best matches the sentence or definition.
a. Wi-MAX
b. Distributed systems
c. Scalability
d. 802.11g
e. Router
f. Infrastructure mode
g. Roaming
h. Gateway
These are broadband wireless communications protocols for metropolitan area networks (MANs).

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
77
Discuss cloud computing at length, including its advantages and disadvantages. Be sure to include a definition of all relevant terms in your explanation.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck
78
Which of the following are the advantages of using a distributed database management system (DDBMS)?
A) The system is scalable, so new data sites can be added without reworking the system design.
B) The data stored closer to users can reduce network traffic.
C) The system is less likely to experience a catastrophic failure when data is stored in various locations.
D) The data is stored in various locations thereby making it is easy to maintain controls and standards.
A) The system is scalable, so new data sites can be added without reworking the system design.
B) The data stored closer to users can reduce network traffic.
C) The system is less likely to experience a catastrophic failure when data is stored in various locations.
D) The data is stored in various locations thereby making it is easy to maintain controls and standards.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 78 في هذه المجموعة.
فتح الحزمة
k this deck








