Deck 12: Managing Systems Support and Security
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/81
العب
ملء الشاشة (f)
Deck 12: Managing Systems Support and Security
1
_____ costs include expenses for items such as supplies, equipment rental, and software leases.
A) Operational
B) Corrective
C) Maintenance
D) Adaptive
A) Operational
B) Corrective
C) Maintenance
D) Adaptive
A
2
Retention periods of backups can be a specific number of months or years, depending on legal requirements and company policy.
True
3
Wrapping refers to the practice of storing backup media away from the main business location, in order to mitigate the risk of a catastrophic disaster, such as a flood, fire, or earthquake.
False
4
Both adaptive and perfective maintenance activities decrease in a dynamic business environment.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
5
A help desk can boost its productivity by using _____, which allows IT staff to take over a user's workstation and provide support and troubleshooting.
A) high-level synthesis
B) wireless fidelity
C) word editing software
D) remote control software
A) high-level synthesis
B) wireless fidelity
C) word editing software
D) remote control software

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
6
In a broad sense, credentials include formal degrees, diplomas, or certificates granted by learning institutions to show that a certain level of education has been achieved.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
7
Bandwidth requirements are expressed in bytes per minute.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
8
The hardening process that makes a system more secure is fully automatic.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
9
As enterprise-wide information systems grow more complex, configuration management becomes trivial.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
10
If significant changes take place in an existing system or if a new version is released, the IT department might develop a _____.
A) user training package
B) user presence software
C) maintenance module
D) utility index
A) user training package
B) user presence software
C) maintenance module
D) utility index

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
11
One highly publicized form of social engineering is called post texting, which is a method of obtaining personal information under false pretenses.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
12
In dumpster diving attacks, an intruder raids desks or trash bins for valuable information.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
13
The systems support and _____ phase begins when a system becomes operational and continues until the system reaches the end of its useful life.
A) implementation
B) verification
C) security
D) testing
A) implementation
B) verification
C) security
D) testing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
14
_____ expenses vary significantly during a system's operational life and include spending to support maintenance activities.
A) Secure
B) Maintenance
C) Principal
D) Capital
A) Secure
B) Maintenance
C) Principal
D) Capital

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
15
Using a release methodology reduces the documentation burden.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
16
_____ include changing programs, procedures, or documentation to ensure correct system performance; adapting the system to changing requirements; and making the system operate more efficiently.
A) Team building activities
B) Elicitation activities
C) Maintenance activities
D) Testing activities
A) Team building activities
B) Elicitation activities
C) Maintenance activities
D) Testing activities

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
17
A(n) _____ is a centralized resource staffed by IT professionals who provide users with the support they need to do their jobs.
A) help desk
B) white spot
C) maintenance software module
D) utility point
A) help desk
B) white spot
C) maintenance software module
D) utility point

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
18
In a public key encryption environment, each user on the network has a pair of keys: a foreign key and a private key.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
19
In a secluded engineering attack, an intruder uses social interaction to gain access to a computer system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
20
When network traffic is encrypted, it is invisible and its content and purpose are masked.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
21
When a new version of a system is installed, the prior release is _____, or stored.
A) archived
B) deleted
C) discontinued
D) reinstalled
A) archived
B) deleted
C) discontinued
D) reinstalled

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
22
In a typical system, the initial version of the system is 1.0, and the release that includes the first set of maintenance changes is version _____.
A) 2.1
B) 1.1
C) 0.1
D) 2.1
A) 2.1
B) 1.1
C) 0.1
D) 2.1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
23
_____ is a process for controlling changes in system requirements during software development.
A) Data management
B) Disk management
C) Configuration management
D) Email management
A) Data management
B) Disk management
C) Configuration management
D) Email management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
24
Adaptive maintenance _____.
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) competes for resources in an operational system
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) competes for resources in an operational system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
25
The _____ describes a system at the beginning of system operation and includes the results of performance and acceptance tests for the operational system.
A) functional baseline
B) operational baseline
C) allocated baseline
D) product baseline
A) functional baseline
B) operational baseline
C) allocated baseline
D) product baseline

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
26
Corrective maintenance _____.
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) competes for resources in an operational system
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) competes for resources in an operational system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
27
The _____ is the configuration of a system documented at the beginning of the project and consists of all necessary system requirements and design constraints.
A) functional baseline
B) extension baseline
C) allocated baseline
D) product baseline
A) functional baseline
B) extension baseline
C) allocated baseline
D) product baseline

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
28
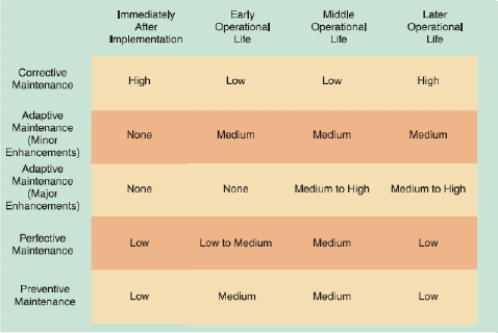
As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by _____.
A) corrective maintenance
B) adaptive maintenance
C) perfective maintenance
D) obsolete maintenance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
29
In maintenance management, _____ means examining the whole in order to learn about the individual elements.
A) synthesis
B) adoption
C) analysis
D) elucidation
A) synthesis
B) adoption
C) analysis
D) elucidation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
30
Perfective maintenance _____.
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) competes for resources in an operational system
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) competes for resources in an operational system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
31
In maintenance management, _____ involves studying the parts of a system to understand the overall system.
A) synthesis
B) adoption
C) fusion
D) elucidation
A) synthesis
B) adoption
C) fusion
D) elucidation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
32
The _____ documents a system at the end of the design phase, identifies any changes since the beginning of the project, and includes testing and verification of all system requirements and features.
A) functional baseline
B) operational baseline
C) allocated baseline
D) product baseline
A) functional baseline
B) operational baseline
C) allocated baseline
D) product baseline

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
33
A _____ is a formal reference point that measures system characteristics at a specific time.
A) feature line
B) baseline
C) product point
D) viewport
A) feature line
B) baseline
C) product point
D) viewport

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
34
To avoid problems, preventive maintenance _____.
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) requires analysis of areas where trouble is likely to occur
A) adds enhancements to an operational system and makes the system easier to use
B) diagnoses and corrects errors in an operational system
C) involves changing an operational system to make it more efficient, reliable, or maintainable
D) requires analysis of areas where trouble is likely to occur

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
35
Many IT departments also use a job title of _____ to designate positions that require a combination of systems analysis and programming skills.
A) tester/programmer
B) strategist/analyst
C) programmer/analyst
D) designer/debugger
A) tester/programmer
B) strategist/analyst
C) programmer/analyst
D) designer/debugger

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
36
A _____ is responsible for assigning maintenance tasks to individuals or to a maintenance team.
A) tester
B) programmer
C) system validator
D) system administrator
A) tester
B) programmer
C) system validator
D) system administrator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
37

As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor _____ maintenance.
A) corrective
B) adaptive
C) perfective
D) preventive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
38
Perfective maintenance usually is cost effective _____ a system's operational life.
A) early in
B) during the middle of
C) during the end of
D) throughout
A) early in
B) during the middle of
C) during the end of
D) throughout

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
39

As shown in the accompanying figure, near the end of a system's useful life, _____ when it becomes clear that a company plans to replace the system.
A) adaptive, corrective, and perfective maintenance expenses all increase rapidly
B) perfective maintenance expenses increase rapidly, but adaptive and corrective maintenance typically decrease
C) adaptive and corrective maintenance expenses increase rapidly, but perfective maintenance typically decreases
D) adaptive, corrective, and perfective maintenance expenses all decrease rapidly

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
40
_____ is the process of tracking system releases.
A) Configuration control
B) Version control
C) Source control
D) Quality control
A) Configuration control
B) Version control
C) Source control
D) Quality control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
41
_____ is a process that monitors current activity and performance levels, anticipates future activity, and forecasts the resources needed to provide desired levels of service.
A) Restructuring
B) Capacity planning
C) Resource sizing
D) Reorganizing
A) Restructuring
B) Capacity planning
C) Resource sizing
D) Reorganizing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
42
_____ ensures that authorized users have timely and reliable access to necessary information.
A) Availability
B) Integrity
C) Confidentiality
D) Concealability
A) Availability
B) Integrity
C) Confidentiality
D) Concealability

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
43
_____ prevents unauthorized users from creating, modifying, or deleting information.
A) Availability
B) Integrity
C) Confidentiality
D) Evacuation
A) Availability
B) Integrity
C) Confidentiality
D) Evacuation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
44
The first step in managing IT security is to develop a _____ based on confidentiality, integrity, and availability.
A) security policy
B) risk policy
C) threat report
D) concealment report
A) security policy
B) risk policy
C) threat report
D) concealment report

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
45
_____ includes monitoring a system for signs of trouble, logging all system failures, diagnosing the problem, and applying corrective action.
A) Benchmark testing
B) Throughput management
C) Responsive testing
D) Fault management
A) Benchmark testing
B) Throughput management
C) Responsive testing
D) Fault management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
46
_____ is the overall time between a request for system activity and the delivery of the response.
A) Response time
B) Throughput time
C) Refresh rate
D) Base rate
A) Response time
B) Throughput time
C) Refresh rate
D) Base rate

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
47
To measure system performance, companies use _____, which uses a set of standard tests on one system to compare its performance and capacity to that of other systems.
A) metric analysis
B) benchmark testing
C) threat analysis
D) allocation testing
A) metric analysis
B) benchmark testing
C) threat analysis
D) allocation testing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
48
_____ analyzes an organization's assets, threats, and vulnerabilities.
A) Risk uncertainty
B) Risk diversification
C) Risk identification
D) Risk control
A) Risk uncertainty
B) Risk diversification
C) Risk identification
D) Risk control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
49
_____ protects information from unauthorized disclosure and safeguards privacy.
A) Availability
B) Integrity
C) Confidentiality
D) Accessibility
A) Availability
B) Integrity
C) Confidentiality
D) Accessibility

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
50
_____ measures risk likelihood and impact.
A) Risk assessment
B) Risk marker
C) Risk identification
D) Risk control
A) Risk assessment
B) Risk marker
C) Risk identification
D) Risk control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
51
_____ measures actual system performance under specific circumstances and is affected by network loads and hardware efficiency.
A) Throughput
B) Resolution
C) Dimensionality
D) Latency
A) Throughput
B) Resolution
C) Dimensionality
D) Latency

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
52
_____ describes the amount of data that a system can transfer in a fixed time period.
A) Latency
B) Resolution
C) Dimensionality
D) Bandwidth
A) Latency
B) Resolution
C) Dimensionality
D) Bandwidth

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
53
In addition to benchmark testing, performance measurements, called _____, can monitor the number of transactions processed in a given time period, the number of records accessed, and the volume of online data.
A) metrics
B) wireframes
C) viewports
D) baselines
A) metrics
B) wireframes
C) viewports
D) baselines

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
54
_____ measures the time between submitting a request for information and the fulfillment of the request.
A) Bandwidth
B) Turnaround time
C) Throughput
D) Frequency
A) Bandwidth
B) Turnaround time
C) Throughput
D) Frequency

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
55
A _____ is a security weakness or soft spot.
A) proxy
B) vulnerability
C) firewall
D) malware
A) proxy
B) vulnerability
C) firewall
D) malware

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
56
A(n) _____ is an attack that takes advantage of a vulnerability.
A) proxy
B) exploit
C) firewall
D) archive
A) proxy
B) exploit
C) firewall
D) archive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
57
A _____ is an internal or external entity that could endanger an asset.
A) proxy
B) facade
C) firewall
D) threat
A) proxy
B) facade
C) firewall
D) threat

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
58
_____ develops safeguards that reduce risks and their impact.
A) Risk assessment
B) Risk verification
C) Risk identification
D) Risk control
A) Risk assessment
B) Risk verification
C) Risk identification
D) Risk control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
59
In IT security terms, a _____ is the impact of an attack multiplied by the likelihood of a vulnerability being exploited.
A) proxy
B) risk
C) firewall
D) warning
A) proxy
B) risk
C) firewall
D) warning

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
60
_____, a risk control strategy, eliminates risks by adding protective safeguards.
A) Avoidance
B) Acceptance
C) Conveyance
D) Transference
A) Avoidance
B) Acceptance
C) Conveyance
D) Transference

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
61
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Uses a single key to encrypt and decrypt information
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Uses a single key to encrypt and decrypt information

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
62
As another one of his responsibilities, George captures information from clients about attacks they have borne and from their description, he identifies the kind of attack they have experienced.
Another of George's clients describes a situation in which a caller to their service desk pretended to be a legitimate user and requested that his password to his company account be changed. How does George categorize this incident?
A) Social engineering
B) Mail bombing
C) Spoofing
D) Privilege escalation
Another of George's clients describes a situation in which a caller to their service desk pretended to be a legitimate user and requested that his password to his company account be changed. How does George categorize this incident?
A) Social engineering
B) Mail bombing
C) Spoofing
D) Privilege escalation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
63
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Protects the system and keeps it safe, free from danger, and reliable
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Protects the system and keeps it safe, free from danger, and reliable

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
64
George's firm contracts to provide risk management services for a wide range of smaller companies that cannot provide the service for themselves. One of George's responsibilities at the end of each month is to review the threats encountered by the companies and put them into the appropriate categories.
Another of George's clients has software that is outdated and has become increasingly vulnerable to attack. How does George categorize this threat?
A) Human error
B) Technical obsolescence
C) Service failure
D) Espionage
Another of George's clients has software that is outdated and has become increasingly vulnerable to attack. How does George categorize this threat?
A) Human error
B) Technical obsolescence
C) Service failure
D) Espionage

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
65
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Might include company hardware, software, data, networks, people, or procedure
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Might include company hardware, software, data, networks, people, or procedure

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
66
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Uses analytical techniques to identify potential quality and performance improvements in an information system
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Uses analytical techniques to identify potential quality and performance improvements in an information system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
67
_____ is concerned with managerial policies and controls that ensure secure operations.
A) Procedural security
B) Network security
C) Operational security
D) Application security
A) Procedural security
B) Network security
C) Operational security
D) Application security

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
68
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Records everything that is typed into the keyboard, including passwords, while the system continues to function normally
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Records everything that is typed into the keyboard, including passwords, while the system continues to function normally

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
69
A(n) _____ can prevent an unauthorized person from booting a computer by using a CD-ROM or USB device.
A) boot-level password
B) application-level password
C) BIOS-level password
D) power-on password
A) boot-level password
B) application-level password
C) BIOS-level password
D) power-on password

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
70
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
A risk control strategy that reduces the impact of a risk by careful planning and preparation
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
A risk control strategy that reduces the impact of a risk by careful planning and preparation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
71
As another one of his responsibilities, George captures information from clients about attacks they have borne and from their description, he identifies the kind of attack they have experienced.
One of George's clients reports that the traffic on their network is being intercepted and scanned for valuable information. How does George categorize this incident?
A) Spoofing
B) Man in the middle
C) Dumpster diving
D) Sniffing
One of George's clients reports that the traffic on their network is being intercepted and scanned for valuable information. How does George categorize this incident?
A) Spoofing
B) Man in the middle
C) Dumpster diving
D) Sniffing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
72
George's firm contracts to provide risk management services for a wide range of smaller companies that cannot provide the service for themselves. One of George's responsibilities at the end of each month is to review the threats encountered by the companies and put them into the appropriate categories.
One of his firm's clients details an incident in which a hacker - a former employee - thieved trade secrets from the client and threatened to release them to the competition if he was not paid. In which of the following categories should George place this incident?
A) Vandalism
B) Trespass and espionage
C) Extortion
D) Software attack
One of his firm's clients details an incident in which a hacker - a former employee - thieved trade secrets from the client and threatened to release them to the competition if he was not paid. In which of the following categories should George place this incident?
A) Vandalism
B) Trespass and espionage
C) Extortion
D) Software attack

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
73
List at least eight different tasks a service desk staff member might have to perform during a typical day.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
74
Response time is affected by _____.
A) system design
B) capabilities
C) follow-up messages
D) processing methods
A) system design
B) capabilities
C) follow-up messages
D) processing methods

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
75
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
An asymmetric kind of encryption
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
An asymmetric kind of encryption

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
76
A _____ is the main line of defense between a local network, or intranet, and the Internet.
A) malware
B) firewall
C) spyware
D) threat
A) malware
B) firewall
C) spyware
D) threat

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
77
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Hostile act that targets systems or a company itself
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Hostile act that targets systems or a company itself

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
78
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
A risk control strategy that shifts risks to another asset or party
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
A risk control strategy that shifts risks to another asset or party

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
79
Matching
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Combination of hardware and software that allows computers to interact with a network
Identify the letters of the choices that best match the phrases or definitions.
a. Private key encryption
b. Public key encryption
c. Network interface
d. Asset
e. Mitigation
f. Transference
g. Attack
h. Security
i. Keystroke logger
j. Software reengineering
Combination of hardware and software that allows computers to interact with a network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck
80
Typically, an intruder accesses a system using a compromised account, and may attempt a(n) _____, which is an unauthorized attempt to increase permission levels.
A) privilege escalation attack
B) denial-of-service attack
C) malware penetration attack
D) identity management invasion
A) privilege escalation attack
B) denial-of-service attack
C) malware penetration attack
D) identity management invasion

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 81 في هذه المجموعة.
فتح الحزمة
k this deck








