Deck 7: The Web and E-mail
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/150
العب
ملء الشاشة (f)
Deck 7: The Web and E-mail
1
If you turn off cookies,you may not be able to make online purchases at some sites.
True
2
Any server that creates a cookie on your hard drive can request that cookie the next time your browser is accessing a Web page from the Web site server.
True
3
E-mail is based on store-and-forward technology.
True
4
The framework for an HTML document consists of two sections: a head and a body.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
5
When configuring local e-mail,the incoming and outgoing servers must have the same settings.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
6
The term player is sometimes used to refer to plug-ins,but it also can refer to standalone software that does not require a host program.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
7
HTTP is a protocol that works with TCP/IP to get Web resources to your desktop.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
8
Many search engines keep records of your queries.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
9
As users are frequently deleting or blocking conventional cookies,marketers are turning to Flash cookies to track and target customers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
10
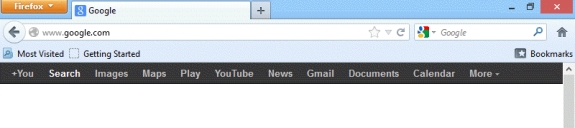
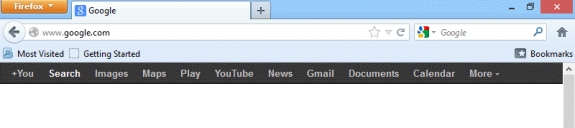
The two applications shown in the accompanying figure are examples of Web browser software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
11
Scripts were designed to replace normal HTML.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
12
Netiquette is online jargon for Internet etiquette.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
13
Adobe Acrobat is a multimedia technology that can be used to create animation and interactive modules.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
14
Researchers estimate that the most extensive search engines cover less than 20% of the Web.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
15
Pharming is less surreptitious and easier to detect than most other hacker schemes.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
16
A C2C e-commerce transaction occurs when individual consumers purchase goods and services from online merchants.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
17
A conversion process called MIME provides a clever way of disguising digital photos,sounds,and other media as plain ASCII code that can travel over the Internet as e-mail attachments.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
18


Older versions of software like the kind shown in the accompanying figure,typically will support new HTML features,so upgrading browsers to the latest version is not essential or recommended.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
19
HTML is called a markup language because authors mark up their documents by inserting HTML tags.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
20
HTTP provides a secure connection for Web-based transactions.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
21
A(n) (spam filter) captures unsolicited e-mail messages before they reach your inbox._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
22
HTML documents use special instructions,called HTML (logos),that specify how the document should appear when displayed on a computer screen or printed._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
23
In a(n) (POP3) e-mail system,your messages remain on a Web server,rather than being downloaded to your computer._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
24
Examples of Uniform Resource Identifiers include ____.
A) URLs
B) Social Security numbers
C) ISBNs
D) all of the above
A) URLs
B) Social Security numbers
C) ISBNs
D) all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
25
Which of the following Web-based applications is NOT sometimes characterized as Web 2.0?
A) wikis
B) blogs
C) social networking
D) cloud computing
A) wikis
B) blogs
C) social networking
D) cloud computing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
26
Flash,once the dominant tool for interactive Web pages,is gradually being replaced by (PerlScript) and new features available in HTML5._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
27
Online auctions are examples of (B2G) e-commerce._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
28
A(n) (Flash cookie) is typically a 1x1 pixel graphic embedded in a Web page or e-mail message designed to track who is reading the Web page or e-mail message._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
29
A(n)____ is a collection of related information organized and formatted so it can be accessed using software called a browser.
A) Web site
B) Internet
C) podcast
D) tag
A) Web site
B) Internet
C) podcast
D) tag

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
30
Visitors to a Web site are sometimes called Web ____.
A) browsers
B) servers
C) surfers
D) users
A) browsers
B) servers
C) surfers
D) users

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
31
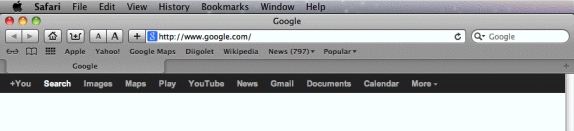
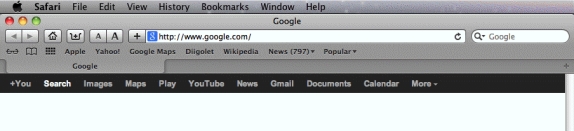
A(n) (control) is a program that extends the ability of the kind of applications shown in the accompanying figure to work with file formats._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
32
The current version of HTML,HTML (4.01),was introduced in 2010._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
33
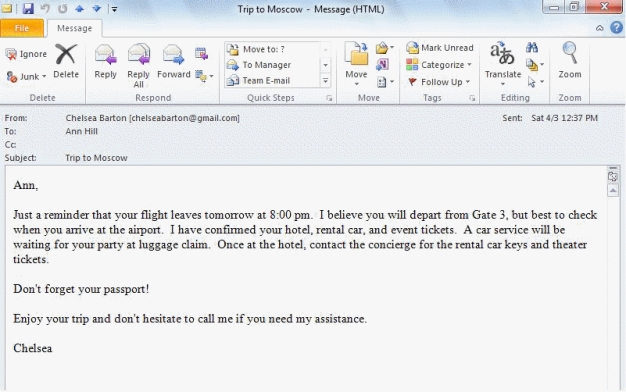
The recipient of the e-mail in the accompanying figure is (Ann Hill)._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
34
The (file name) for a Web site's main page,like www.cnn.com,is usually short and to the point._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
35
(Phishing) is an e-mail based scam that's designed to persuade you to reveal confidential information such as your bank account number or Social Security number._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
36
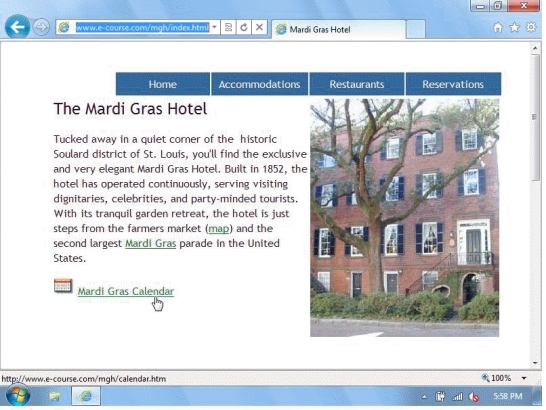
The hand icon shown in the accompanying figure is pointing to a ____.
A) cookie
B) key
C) link
D) tunnel

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
37
(Web 3.0) refers to innovations like cloud computing and other new technologies likely to further change the way we use the Web._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
38
A Web (indexer) is a computer program that is automated to methodically visit Web sites._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
39
Every Web page has a unique address called a(n) (Uniform Resource Locator)._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
40


The applications shown in the accompanying figure are examples of (Web browsers)._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
41

In the URL found in the accompanying figure,www.cnn.com is the ____.
A) Web protocol standard
B) Web server name
C) folder name
D) file extension

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
42
A ____ HTTP connection reuses the same HTTP connection to send and receive multiple requests.
A) status
B) port-based
C) server
D) persistent
A) status
B) port-based
C) server
D) persistent

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
43
____ is the most frequently used HTTP method.
A) FTP
B) THIS
C) POST
D) GET
A) FTP
B) THIS
C) POST
D) GET

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
44
____ provides tools specifically designed to enter and format Web page text,graphics,and links.
A) A text editor
B) Web authoring software
C) Web Creator
D) W3C
A) A text editor
B) Web authoring software
C) Web Creator
D) W3C

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
45
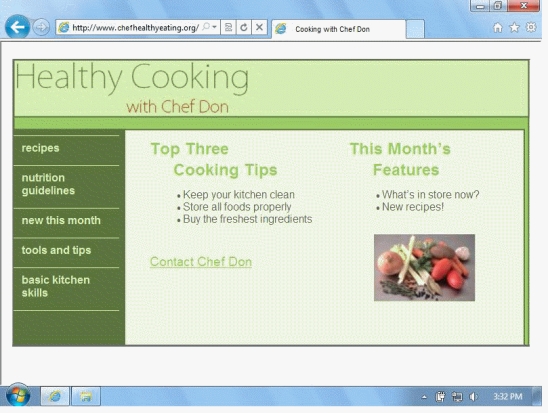
The image of the vegetables in the accompanying figure is produced by a(n)____ HTML tag when the Web page is displayed by a browser.
A)
B)
C)
D)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
46
For HTTP,____ usually are associated with port 80 on the client and server.
A) exchanges
B) methods
C) sockets
D) actions
A) exchanges
B) methods
C) sockets
D) actions

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
47
Which of the following is a Web resource?
A) an HTML document
B) a sound file
C) a graphic
D) any of the above
A) an HTML document
B) a sound file
C) a graphic
D) any of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
48
A ____ enables a Web server to keep track of your activity and compile a list of your purchases.
A) cookie
B) plug-in
C) socket
D) style sheet
A) cookie
B) plug-in
C) socket
D) style sheet

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
49

In the URL found in the accompanying figure,http is the ____.
A) Web protocol standard
B) Web server name
C) folder name
D) file extension

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
50
____ is a protocol that works in conjunction with TCP/IP to get Web resources to your desktop.
A) HTML
B) URL
C) HTTP
D) FTP
A) HTML
B) URL
C) HTTP
D) FTP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
51
When your browser fetches pages and graphics to form a Web page,it stores them in temporary files on your hard drive called a Web ____.
A) cache
B) plug-in
C) converter
D) source
A) cache
B) plug-in
C) converter
D) source

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
52
____ allow a Web site to store information on the client computer for later retrieval.
A) Tags
B) Cookies
C) Biscuits
D) Labels
A) Tags
B) Cookies
C) Biscuits
D) Labels

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
53
A Web server's response to a browser's request includes an HTTP ____ that indicates whether the browser's request could be fulfilled.
A) socket code
B) protocol code
C) status code
D) completion code
A) socket code
B) protocol code
C) status code
D) completion code

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
54

In the URL found in the accompanying figure,.htm is the ____.
A) Web protocol standard
B) Web server name
C) folder name
D) file extension

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
55
____ consists of a series of instructions that is embedded directly into an HTML document that instruct the browser to carry out specific actions or to respond to specific user actions.
A) An HTML tag
B) JavaScript
C) A podcast
D) A cookie
A) An HTML tag
B) JavaScript
C) A podcast
D) A cookie

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
56
A(n)____ adds HTML tags to a document,spreadsheet,or other text-based file to create an HTML document that can be displayed by a browser.
A) online Web authoring tool
B) Web authoring software program
C) HTML conversion utility
D) wiki
A) online Web authoring tool
B) Web authoring software program
C) HTML conversion utility
D) wiki

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
57
An HTTP exchange takes place over a pair of ____.
A) sockets
B) packets
C) switches
D) networks
A) sockets
B) packets
C) switches
D) networks

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
58
All of the following are currently popular browsers EXCEPT ____.
A) Firefox
B) Chrome
C) Safari
D) Netscape Navigator
A) Firefox
B) Chrome
C) Safari
D) Netscape Navigator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
59

In the URL found in the accompanying figure,showbiz is a ____.
A) Web protocol standard
B) Web server name
C) folder name
D) file extension

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
60
A(n)____ is client software that displays Web page elements and handles links between pages.
A) explorer
B) browser
C) navigator
D) manager
A) explorer
B) browser
C) navigator
D) manager

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
61
Server-side scripts can be written using any of the following EXCEPT ____.
A) Perl
B) C#
C) Java
D) Ada
A) Perl
B) C#
C) Java
D) Ada

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
62
A Web ____,automated to methodically visit Web sites,can be programmed to perform various activities as it visits those sites.
A) converter
B) crawler
C) archive
D) glossary
A) converter
B) crawler
C) archive
D) glossary

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
63
____ scripts accept data submitted by a form,process that data,and then generate a custom HTML document that is sent to the browser for display.
A) Server-side
B) Client-side
C) User-side
D) Java-side
A) Server-side
B) Client-side
C) User-side
D) Java-side

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
64
A(n)____ helps people locate information on the Web by formulating simple keyword queries.
A) navigator
B) browser
C) search engine
D) HTML tag
A) navigator
B) browser
C) search engine
D) HTML tag

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
65
____ e-commerce occurs when businesses sell to governments.
A) G2B
B) B2G
C) C2G
D) G2G
A) G2B
B) B2G
C) C2G
D) G2G

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
66
When you purchase a used digital camera directly from the owner on an online auction,you are participating in ____ e-commerce.
A) C2C
B) B2C
C) B2B
D) B2G
A) C2C
B) B2C
C) B2B
D) B2G

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
67
A search engine's ____ looks for your search terms in the search engine's indexed database and returns a list of relevant Web sites.
A) query processor
B) link
C) Web crawler
D) indexer
A) query processor
B) link
C) Web crawler
D) indexer

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
68
Many ____ sites act as relay stations to forward your searches to search engines without leaving a trail back to a cookie or IP address.
A) pharming
B) anonymizer
C) annihilator
D) phishing
A) pharming
B) anonymizer
C) annihilator
D) phishing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
69
In addition to using search engines,you can also find Web-based information using a(n)____ engine that searches a series of other search engines and compiles the search results.
A) compiled
B) stuffed
C) metasearch
D) secure
A) compiled
B) stuffed
C) metasearch
D) secure

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
70
The ____ wildcard character allows a search engine to find pages with any derivation of a basic word.
A) +
B) &
C) *
D) $
A) +
B) &
C) *
D) $

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
71
____ e-commerce involves one enterprise buying goods or services from another enterprise.
A) C2C
B) B2C
C) B2B
D) B2G
A) C2C
B) B2C
C) B2B
D) B2G

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
72
A(n)____ keyword is entered into a header section of a Web page when it is created and is supposed to describe the page contents.
A) query
B) link
C) archive
D) meta
A) query
B) link
C) archive
D) meta

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
73
HTML ____ are used to display a question and a box into which you can enter an answer.
A) bins
B) tables
C) gateways
D) forms
A) bins
B) tables
C) gateways
D) forms

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
74
A popular ____ activity is verifying billing data at an e-commerce site.
A) Server-side
B) Client-side
C) User-side
D) Java-side
A) Server-side
B) Client-side
C) User-side
D) Java-side

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
75
Search engine ____ software is designed to pull keywords from a Web page and store them in a database.
A) indexer
B) crawler
C) archive
D) tracker
A) indexer
B) crawler
C) archive
D) tracker

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
76
Keyword ____ is an unethical practice in which meta keywords are manipulated to gain high relevancy rankings.
A) packing
B) stuffing
C) archiving
D) indexing
A) packing
B) stuffing
C) archiving
D) indexing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
77
____ scripts tend to be used for interactive user interface elements.
A) Server-side
B) Client-side
C) User-side
D) Java-side
A) Server-side
B) Client-side
C) User-side
D) Java-side

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
78
When a Web page author includes meta keywords,like sex,that have little to do with the information on the page,the author is engaging in ____.
A) formulating searches
B) metasearching
C) keyword stuffing
D) e-commerce
A) formulating searches
B) metasearching
C) keyword stuffing
D) e-commerce

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
79
When you use a search engine,it stores all of the following information about your query EXCEPT ____.
A) your name
B) your IP address
C) the date and time of the query
D) the search terms you used
A) your name
B) your IP address
C) the date and time of the query
D) the search terms you used

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck
80
When you purchase a textbook online from a site like www.amazon.com,you are participating in ____ e-commerce.
A) C2C
B) B2C
C) B2B
D) B2G
A) C2C
B) B2C
C) B2B
D) B2G

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 150 في هذه المجموعة.
فتح الحزمة
k this deck








