Deck 22: Computer Benefits and Risks
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/75
العب
ملء الشاشة (f)
Deck 22: Computer Benefits and Risks
1
A(n) ____________________ or "Web bug" is a 1x1 pixel graphic on a Web page.
clear GIF
2
The marketing firms that distribute ad-serving cookies claim that this data is simply used to select and display ads that might interest you.
True
3
Copyright law prohibits all copying.
False
4
You can violate your own privacy by unintentionally releasing information about yourself that can be exploited by aggressive marketing companies, hackers, and criminals.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
5
____________________ occurs when someone obtains your personal information and uses it without your permission to commit fraud or other crimes.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
6
A copyright notice, such as "Copyright 2010 eCourse Inc." is required by law in order to be protected by copyright.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
7
____________________ refers to any physical method used to prevent works from being copied.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
8
Personal information can be defined as any data that is associated with you as an individual.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
9
____________________ is the use of fraudulent Web sites and e-mail links to trick people into revealing sensitive, personal, and financial information.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
10
____________________ is any technology that surreptitiously gathers information.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
11
Web site ____________________, the process of intentionally blocking access to certain sites, is controversial.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
12
The material published on Web sites, in blogs, and in other online forums is protected by copyright.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
13
You can make copies for your own use and you can make copies under ____________________ regulations, which allow you to copy small excerpts of copyrighted works for use in educational materials and critical reviews.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
14
Viruses spread themselves from one computer to another.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
15
____________________ refers to intangibles, such as ideas, music, art, photos, logos, movies, and programs, that are the result of creativity and intellectual effort.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
16
Personal information about your health, grades, charitable donations, and purchases is stored in a very limited number of places.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
17
A(n) ____________________ is issued by a certificate authority that essentially vouches for the certificate holder's identity.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
18
Legitimate macros are used to automate common word processing or spreadsheet tasks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
19
Unfortunately, there is no software available to block banner and pop-up ads altogether.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
20
In order to gain access to a(n) ____________________ Web site, you typically have to register for an account and password.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
21
____ software is designed to analyze the flow of traffic entering your computer from a network.
A)Port connection
B)Wireless connection
C)Encryption
D)Firewall
A)Port connection
B)Wireless connection
C)Encryption
D)Firewall

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
22
A ____ uses a home-based computer and telecommunications equipment to perform work-related tasks.
A)telecommuter
B)teleworker
C)either a.or b.
D)neither a.nor b.
A)telecommuter
B)teleworker
C)either a.or b.
D)neither a.nor b.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
23
Small ____ tags sewn into clothing communicate with inventory tracking systems.
A)Radio Frequency Identification
B)Wireless Frequency Identification
C)Radio Signal
D)Wireless Signal
A)Radio Frequency Identification
B)Wireless Frequency Identification
C)Radio Signal
D)Wireless Signal

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
24
The original wireless encryption was called ____ and was designed to provide a level of confidentiality similar to that of a wired network.
A)WAP
B)WEP
C)WIP
D)WOP
A)WAP
B)WEP
C)WIP
D)WOP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
25
Most malicious code is stored in executable files, usually with ____ file name extensions.
A)exe
B)doc
C)xls
D)mp3
A)exe
B)doc
C)xls
D)mp3

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
26
____ is the study of work and work environments, with the goal being to make work environments safer and healthier.
A)Robotics
B)Telecommunications
C)Ergonomics
D)Economics
A)Robotics
B)Telecommunications
C)Ergonomics
D)Economics

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
27
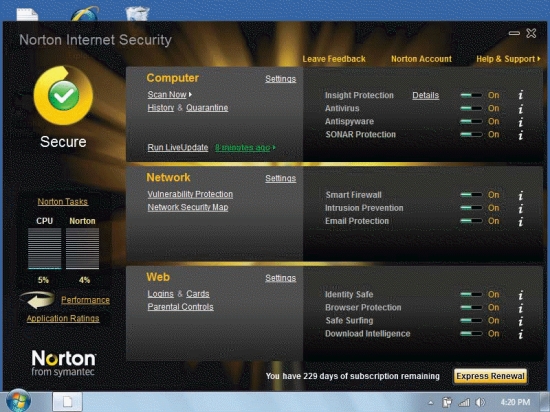
Referring to the figure above, if these were your settings, ____ would be scanned for viruses.
A)all of your e-mail messages
B)none of your e-mail messages
C)all of your e-mail attachments only
D)all of your outgoing e-mail only

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
28
A ____ is a snapshot of your computer settings and are essentially backups of the Windows Registry.
A)help point
B)defragmentation history
C)backup
D)restore point
A)help point
B)defragmentation history
C)backup
D)restore point

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
29
A ____ worm makes use of information on an infected computer to mail itself to everyone listed in the e-mail address book.
A)mass-mailing
B)friendly
C)post office
D)hello
A)mass-mailing
B)friendly
C)post office
D)hello

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
30

Referring to the figure above, you have 229 days of the Norton subscription remaining, and LiveUpdate was run eight minutes ago.To stay current, always make sure your ____ is/are up-to-date.
A)antivirus software subscription
B)virus definitions
C)both a.and b.
D)neither a.nor b.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
31
A computer ____ is a set of program instructions that can attach itself to a file, reproduce itself, and spread to other files.
A)worm
B)virus
C)Trojan horse
D)phishing scam
A)worm
B)virus
C)Trojan horse
D)phishing scam

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
32

In the figure above, the Norton Smart firewall is marked on.If Windows Firewall is also turned on, you would ____.
A)leave this one on too, for double security
B)turn this one off, you should not have two firewalls running
C)do nothing, your system will turn the firewalls on and off automatically
D)none of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
33
Some Trojan horses contain a virus or a worm, which can replicate and spread.Virus experts call this a ____ threat because it combines more than one type of malicious code.
A)blended
B)combo
C)confused
D)mixed-up
A)blended
B)combo
C)confused
D)mixed-up

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
34
A ____ attack is designed to generate a lot of activity on a network by flooding it with useless traffic-enough traffic to overwhelm the network's processing capability and essentially bring all communications to a halt.
A)stampede
B)denial of service
C)rampage
D)buzz
A)stampede
B)denial of service
C)rampage
D)buzz

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
35
____ makes it possible for shoppers to purchase merchandise using their computers.
A)E-world
B)E-commerce
C)E-spend
D)E-business
A)E-world
B)E-commerce
C)E-spend
D)E-business

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
36
Often hackers transmit ____ that circulate over the Internet looking for unsecured computer systems.
A)phish feelers
B)phish felons
C)port jets
D)port probes
A)phish feelers
B)phish felons
C)port jets
D)port probes

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
37
To access Windows Firewall when using Windows, type "____" in the Start menu's Search box.
A)Security
B)Firewall
C)Help
D)Start
A)Security
B)Firewall
C)Help
D)Start

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
38
When setting up wireless encryption, you will create an encryption ____, which works like a password.
A)key
B)number
C)password
D)name
A)key
B)number
C)password
D)name

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
39
____ key, also referred to as "personal mode," is a type of WPA used on most home networks.
A)Authorized
B)Pre-authorized
C)Shared
D)Pre-shared
A)Authorized
B)Pre-authorized
C)Shared
D)Pre-shared

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
40
Unlike a virus, which is designed to spread from file to file, a worm is designed to spread from computer to computer over ____.
A)local area networks
B)the Internet
C)both a.and b.
D)neither a.nor b.
A)local area networks
B)the Internet
C)both a.and b.
D)neither a.nor b.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
41
When you publish your own material online, it is automatically covered by ____.
A)trademark
B)copyright
C)patent
D)libel insurance
A)trademark
B)copyright
C)patent
D)libel insurance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
42
The term ____ refers to any program or set of program instructions designed to surreptitiously enter a computer and disrupt its normal operations.
A)virus code
B)malicious code
C)virus script
D)malicious script
A)virus code
B)malicious code
C)virus script
D)malicious script

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
43
The information that your antivirus software uses to identify and eradicate malicious code is stored in one or more files usually referred to as "virus ____."
A)medicines
B)definitions
C)antidotes
D)scripts
A)medicines
B)definitions
C)antidotes
D)scripts

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
44
The Software Information Industry Association (SIIA) is trying to stop illegal software ____.
A)distribution
B)development
C)encryption
D)archiving
A)distribution
B)development
C)encryption
D)archiving

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
45
The process of eradicating a virus-sometimes called "____"-might include deleting the virus code from files or deleting infected files.
A)disinfecting
B)spraying
C)exterminating
D)erasing
A)disinfecting
B)spraying
C)exterminating
D)erasing

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
46
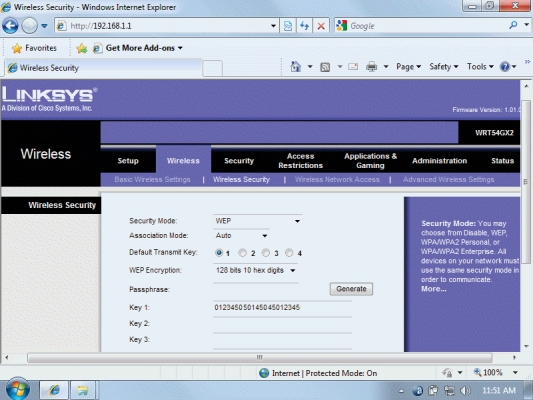
In the figure above, the "Key 1:" that is shown is also referred to as a(n) ____ key.
A)encryption
B)part-time
C)password
D)portal

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
47
Although ____ property can be fixed in tangible media the underlying "property" is not necessarily tied to a particular media.
A)smart
B)intellectual
C)mathematical
D)performance
A)smart
B)intellectual
C)mathematical
D)performance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
48
In the United States, ____ prevents health care organizations from distributing patient information without written permission, and gives patients the right to amend incorrect or missing information in their records.
A)HIPAA
B)LIPAA
C)MIPAA
D)KIPAA
A)HIPAA
B)LIPAA
C)MIPAA
D)KIPAA

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
49
A typical ____ scam begins with a faked e-mail message that seems to be an official notice from a trusted source, such as a credit card company, online payment service, software vendor, or bank.
A)spam
B)phishing
C)fox
D)virus
A)spam
B)phishing
C)fox
D)virus

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
50
You can check the list of cookies on your computer to look for ad-serving cookies.They are typically generated by sites you have never visited and sometimes contain the word "ad" or "____."
A)dog
B)log
C)bog
D)cog
A)dog
B)log
C)bog
D)cog

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
51
____ use allows you to insert fragments of literary works in research papers without first gaining permission from their authors.
A)Intellectual
B)Fair
C)Educational
D)Part-time
A)Intellectual
B)Fair
C)Educational
D)Part-time

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
52

The figure above shows the ____ configuration software.
A)router's
B)computer's
C)Internet connection
D)operating system

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
53
In the United States, the Digital Millennium Copyright Act of ____ updated many key aspects of intellectual property law to meet the challenges of new digital realities.
A)1998
B)2002
C)2006
D)2008
A)1998
B)2002
C)2006
D)2008

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
54
____ usually protect inventions from being used without permission from the inventor.
A)Trademarks
B)Copyrights
C)Patents
D)Privacy Policies
A)Trademarks
B)Copyrights
C)Patents
D)Privacy Policies

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
55
____ typically protect corporate logos and product names.
A)Trademarks
B)Patents
C)Copyrights
D)Privacy Policies
A)Trademarks
B)Patents
C)Copyrights
D)Privacy Policies

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
56
____ typically protect works such as software, photos, movies, and music.
A)Copyrights
B)Trademarks
C)Patents
D)Privacy Policies
A)Copyrights
B)Trademarks
C)Patents
D)Privacy Policies

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
57
A data file with a .doc or .xls extension can sometimes contain a ____ virus.
A)formula
B)function
C)micro
D)macro
A)formula
B)function
C)micro
D)macro

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
58
____ violations take place when your personal information is distributed or your online activities are tracked without your permission.
A)Virus
B)Trojan
C)Privacy
D)Encryption
A)Virus
B)Trojan
C)Privacy
D)Encryption

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
59
Several software publishers offer tools that filter out inappropriate Web sites.____ typically comes pre-loaded with a long list of sites that are not child-friendly.
A)Net Nanny
B)Windows Parental Controls
C)both a.and b.
D)neither a.nor b.
A)Net Nanny
B)Windows Parental Controls
C)both a.and b.
D)neither a.nor b.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
60
The music industry, the Recording Industry Association of America (RIAA) is attempting to stop rampant ____ music sharing on the Internet.
A)DVD
B)Radio signal
C)MP3
D)CD
A)DVD
B)Radio signal
C)MP3
D)CD

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
61
Case 22-1
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
A professor contacts Genevieve saying that he thinks he has a computer virus, but he has been on vacation for a month, and has not used his computer.Genevieve explains that ____.
A)it can be a virus because viruses can lurk for days or months inside a computer
B)it can be a virus, caught by the computer while it was turned off
C)it cannot be a virus as he would have known about the virus before he left on vacation
D)none of the above
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
A professor contacts Genevieve saying that he thinks he has a computer virus, but he has been on vacation for a month, and has not used his computer.Genevieve explains that ____.
A)it can be a virus because viruses can lurk for days or months inside a computer
B)it can be a virus, caught by the computer while it was turned off
C)it cannot be a virus as he would have known about the virus before he left on vacation
D)none of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
62
HIPAA helps keep your medical information private and prevents abusive practices, such as when a cash-strapped health care organization sells a list of its pregnant patients to a baby-formula marketing company._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
63
A Trojan ant is a computer program that seems to perform one function while actually doing something else, and is not designed to make copies of itself._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
64
Gossip is defined as false and malicious statements published for the purpose of damaging the reputation of a living person._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
65
Explain how you can use a router instead of a firewall to protect your computer from intrusions.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
66
Coded software scrambles your data by using a multi-digit key._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
67
Copyright law makes it illegal to copy and distribute protected works without the permission of the author or the author's representative._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
68
One of the forms of malicious code is worms.Please briefly describe a worm, a mass-mailing worm, and a denial of service attack.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
69
Many businesses that collect data online offer a(n) privacy policy that describes how your personal data might be used, whether it might be sold or distributed, and how it might be protected from unauthorized access._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
70
Some Web sites feature banner ads supplied by third-party marketing firms.If you click the ad, this third party can create an ad-serving virus and use it to track your activities at any site containing banner ads from that third party._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
71
Case 22-1
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
Genevieve has received three reports today, from students, about a computer virus that is spreading from one computer to another automatically with the name "Hello Friend." Genevieve knows the problem is not a virus because computer viruses ____.
A)are never found on a college campus
B)don't spread from one computer to another automatically
C)never have names
D)none of the above
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
Genevieve has received three reports today, from students, about a computer virus that is spreading from one computer to another automatically with the name "Hello Friend." Genevieve knows the problem is not a virus because computer viruses ____.
A)are never found on a college campus
B)don't spread from one computer to another automatically
C)never have names
D)none of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
72
Virus software is a set of utility programs that looks for and eradicates viruses and worms._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
73
A virus clue is a section of code, such as a unique series of instructions, that can be used to identify a known virus or worm, much as a fingerprint is used to identify an individual._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
74
Information security refers to the techniques used to protect information from unauthorized access, damage, disclosure, loss, modification, or use._________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck
75
Case 22-1
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
Genevieve drafts a letter to the student body saying to be careful about opening executable files.Genevieve also states that malicious code can be included in ____ files.
A)sys or .com
B)bin or .vbs
C)scr or .ovl
D)any of the above
Genevieve is in charge of Internet Security for a small New England college. Please answer the questions below.
Genevieve drafts a letter to the student body saying to be careful about opening executable files.Genevieve also states that malicious code can be included in ____ files.
A)sys or .com
B)bin or .vbs
C)scr or .ovl
D)any of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 75 في هذه المجموعة.
فتح الحزمة
k this deck








