Deck 12: Managing Systems Support and Security
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/112
العب
ملء الشاشة (f)
Deck 12: Managing Systems Support and Security
1
Which of the following is not an advantage of the release methodology?
A)all changes are tested together before a new system version is released
B)costs are reduced because only one set of system tests is needed
C)documentation changes are coordinated and become effective simultaneously
D)new features or upgrades are available more often
A)all changes are tested together before a new system version is released
B)costs are reduced because only one set of system tests is needed
C)documentation changes are coordinated and become effective simultaneously
D)new features or upgrades are available more often
D
2
If significant changes take place in an existing system or if a new version is released, the IT department might develop a ____.
A)user training package
B)documentation process
C)maintenance module
D)utility index
A)user training package
B)documentation process
C)maintenance module
D)utility index
A
3
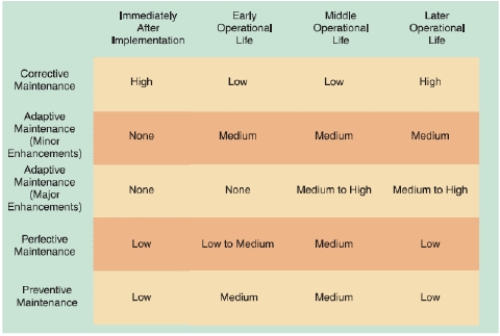
Perfective maintenance ____.
A)adds enhancements to an operational system and makes the system easier to use
B)diagnoses and corrects errors in an operational system
C)involves changing an operational system to make it more efficient, reliable, or maintainable
D)requires analysis of areas where trouble is likely to occur in order to avoid problems
C
4
____ means examining the whole in order to learn about the individual elements.
A)Synthesis
B)Risk management
C)Analysis
D)Risk identification
A)Synthesis
B)Risk management
C)Analysis
D)Risk identification

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
5

As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor ____ maintenance.
A)corrective
B)adaptive
C)perfective
D)preventive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
6
The ____ is responsible for assigning maintenance tasks to individuals or to a maintenance team.
A)user
B)programmer
C)systems review committee
D)system administrator
A)user
B)programmer
C)systems review committee
D)system administrator

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
7

Adaptive maintenance ____.
A)adds enhancements to an operational system and makes the system easier to use
B)diagnoses and corrects errors in an operational system
C)involves changing an operational system to make it more efficient, reliable, or maintainable
D)requires analysis of areas where trouble is likely to occur in order to avoid problems

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
8
____ costs include expenses for items such as supplies, equipment rental, and software leases.
A)Operational
B)Corrective
C)Maintenance
D)Adaptive
A)Operational
B)Corrective
C)Maintenance
D)Adaptive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
9
____ expenses vary significantly during a system's operational life and include spending to support maintenance activities.
A)Preventive
B)Maintenance
C)Corrective
D)Adaptive
A)Preventive
B)Maintenance
C)Corrective
D)Adaptive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
10

As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by ____ maintenance.
A)corrective
B)adaptive
C)perfective
D)preventive

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
11

As shown in the accompanying figure, ____ when it becomes clear that the company plans to replace the system.
A)adaptive, corrective, and perfective maintenance expenses all increase rapidly
B)perfective maintenance expenses increase rapidly, but adaptive and corrective maintenance typically decrease
C)adaptive and corrective maintenance expenses increase rapidly, but perfective maintenance typically decreases
D)adaptive, corrective, and perfective maintenance expenses all decrease rapidly

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
12
____ involves studying the parts to understand the overall system.
A)Synthesis
B)Risk management
C)Analysis
D)Risk identification
A)Synthesis
B)Risk management
C)Analysis
D)Risk identification

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
13
In a typical system, the initial version of the system is 1.0, and the release that includes the first set of maintenance changes is version ____.
A)1.0
B)1.1
C)2.0
D)2.1
A)1.0
B)1.1
C)2.0
D)2.1

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
14
____ activities include changing programs, procedures, or documentation to ensure correct system performance; adapting the system to changing requirements; and making the system operate more efficiently.
A)Procedural
B)Documented
C)Maintenance
D)Programmatic
A)Procedural
B)Documented
C)Maintenance
D)Programmatic

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
15

Corrective maintenance ____.
A)adds enhancements to an operational system and makes the system easier to use
B)diagnoses and corrects errors in an operational system
C)involves changing an operational system to make it more efficient, reliable, or maintainable
D)requires analysis of areas where trouble is likely to occur in order to avoid problems

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
16

Perfective maintenance usually is cost effective ____ the system's operational life.
A)early in
B)during the middle of
C)late in
D)throughout

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
17

Preventive maintenance ____.
A)adds enhancements to an operational system and makes the system easier to use
B)diagnoses and corrects errors in an operational system
C)involves changing an operational system to make it more efficient, reliable, or maintainable
D)requires analysis of areas where trouble is likely to occur in order to avoid problems

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
18
When setting priorities, many IT managers believe that evaluating all projects together leads to the best possible decisions because ____.
A)maintenance and new development require similar IT department resources
B)in IT departments organized into separate maintenance and development groups, it makes no sense to evaluate requests separately
C)maintenance is more likely to receive a proportional share of IT department resources
D)all of the above
A)maintenance and new development require similar IT department resources
B)in IT departments organized into separate maintenance and development groups, it makes no sense to evaluate requests separately
C)maintenance is more likely to receive a proportional share of IT department resources
D)all of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
19
____ is a process for controlling changes in system requirements during software development.
A)EM
B)DM
C)CM
D)TM
A)EM
B)DM
C)CM
D)TM

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
20
In most organizations, ____ IT department effort goes into supporting existing systems and making them more valuable to users.
A)no
B)less than half of all
C)more than half of all
D)all
A)no
B)less than half of all
C)more than half of all
D)all

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
21
A ____ is an internal or external entity that could endanger an asset.
A)menace
B)strike
C)malware
D)threat
A)menace
B)strike
C)malware
D)threat

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
22
____ ensures that authorized users have timely and reliable access to necessary information.
A)Availability
B)Integrity
C)Confidentiality
D)Risk management
A)Availability
B)Integrity
C)Confidentiality
D)Risk management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
23
____ prevents unauthorized users from creating, modifying, or deleting information.
A)Availability
B)Integrity
C)Confidentiality
D)Risk management
A)Availability
B)Integrity
C)Confidentiality
D)Risk management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
24
The ____ is the configuration of a system documented at the beginning of the project and consists of all necessary system requirements and design constraints.
A)functional baseline
B)operational baseline
C)allocated baseline
D)product baseline
A)functional baseline
B)operational baseline
C)allocated baseline
D)product baseline

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
25
Preset ____ determine whether a firewall will allow network traffic to pass.
A)adaptations
B)rules
C)port scans
D)super-users
A)adaptations
B)rules
C)port scans
D)super-users

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
26
____ means that in risk control, nothing is done.
A)Acceptance
B)Avoidance
C)Mitigation
D)Transference
A)Acceptance
B)Avoidance
C)Mitigation
D)Transference

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
27
To measure system performance, companies use ____ testing, which uses a set of standard tests on one system to compare its performance and capacity to that of other systems.
A)metric
B)benchmark
C)threat
D)allocation
A)metric
B)benchmark
C)threat
D)allocation

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
28
____ shifts the risk to another asset or party, such as an insurance company, in risk control.
A)Acceptance
B)Avoidance
C)Mitigation
D)Transference
A)Acceptance
B)Avoidance
C)Mitigation
D)Transference

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
29
The ____ documents a system at the end of the design phase, identifies any changes since the beginning of the project, and includes testing and verification of all system requirements and features.
A)functional baseline
B)operational baseline
C)allocated baseline
D)product baseline
A)functional baseline
B)operational baseline
C)allocated baseline
D)product baseline

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
30
____ include the volume of online data, the number of records accessed, and the number of transactions processed in a given time period.
A)Metrics
B)Risk assessments
C)Allocations
D)Baselines
A)Metrics
B)Risk assessments
C)Allocations
D)Baselines

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
31
A(n) ____ is an unauthorized attempt to increase permission levels.
A)privilege escalation attack
B)denial-of-service attack
C)Trojan horse
D)identity management invasion
A)privilege escalation attack
B)denial-of-service attack
C)Trojan horse
D)identity management invasion

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
32
____ describes the amount of data that a system can transfer in a fixed time period.
A)Throughput
B)Resolution
C)Dimensionality
D)Bandwidth
A)Throughput
B)Resolution
C)Dimensionality
D)Bandwidth

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
33
____ protects information from unauthorized disclosure and safeguards privacy.
A)Availability
B)Integrity
C)Confidentiality
D)Risk management
A)Availability
B)Integrity
C)Confidentiality
D)Risk management

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
34
Risk ____ measures risk likelihood and impact.
A)assessment
B)management
C)identification
D)control
A)assessment
B)management
C)identification
D)control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
35
Risk ____ analyzes the organization's assets, threats, and vulnerabilities.
A)assessment
B)management
C)identification
D)control
A)assessment
B)management
C)identification
D)control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
36
Risk ____ develops safeguards that reduce risks and their impact.
A)assessment
B)management
C)identification
D)control
A)assessment
B)management
C)identification
D)control

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
37
The ____ describes the system at the beginning of system operation and includes the results of performance and acceptance tests for the operational system.
A)functional baseline
B)operational baseline
C)allocated baseline
D)product baseline
A)functional baseline
B)operational baseline
C)allocated baseline
D)product baseline

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
38
Bandwidth will not be measured in which of the following units?
A)Kbps (kilobits per second)
B)Mbps (megabits per second)
C)Dbps (decibits per second)
D)Gbps (gigabits per second)
A)Kbps (kilobits per second)
B)Mbps (megabits per second)
C)Dbps (decibits per second)
D)Gbps (gigabits per second)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
39
____ also can be used to measure the quality of IT support or services by measuring the time from a user request for help to the resolution of the problem.
A)Bandwidth
B)Turnaround time
C)Throughput
D)Response time
A)Bandwidth
B)Turnaround time
C)Throughput
D)Response time

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
40
A ____ is a formal reference point that measures system characteristics at a specific time.
A)feature line
B)baseline
C)product point
D)risk point
A)feature line
B)baseline
C)product point
D)risk point

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
41
Response time is affected by the____.
A)system design
B)capabilities
C)system vulnerabilities
D)processing methods
A)system design
B)capabilities
C)system vulnerabilities
D)processing methods

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
42
Perfective maintenance can improve system reliability.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
43
The systems support and security phase is an important component of TCO (total cost of ownership) because ongoing maintenance expenses can determine the economic life of a system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
44
The main objective of user training is to show users how to become service desk staff members.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
45
When planning capacity, detailed information is needed about ____.
A)the number of transactions and the number of queries
B)the number of threats and critical risks posed to a system
C)the number, type, and size of all generated reports
D)the daily, weekly, or monthly transaction patterns
A)the number of transactions and the number of queries
B)the number of threats and critical risks posed to a system
C)the number, type, and size of all generated reports
D)the daily, weekly, or monthly transaction patterns

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
46
Using a release methodology increases the documentation burden. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
47
Indications that a system has reached the end of its economically useful life include ____.
A)adaptive and corrective maintenance is increasing rapidly
B)operational costs and execution times are decreasing rapidly
C)maintenance changes or additions are difficult and expensive to perform
D)users request significant new features to support business requirements
A)adaptive and corrective maintenance is increasing rapidly
B)operational costs and execution times are decreasing rapidly
C)maintenance changes or additions are difficult and expensive to perform
D)users request significant new features to support business requirements

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
48
The systems support and security phase begins when a system becomes operational and continues until the system reaches the end of its useful life.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
49
Attacks are hostile acts that target the system, or the company itself. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
50
A service desk is a highly effective replacement for traditional IT maintenance and support activities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
51
The procedure for minor adaptive maintenance is similar to routine corrective maintenance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
52
A main objective of a service desk is to ____.
A)show people how to use system resources more effectively
B)provide answers to technical or operational questions
C)make users more productive by teaching them how to meet their own information needs
D)choose the appropriate risk control strategy for the firm
A)show people how to use system resources more effectively
B)provide answers to technical or operational questions
C)make users more productive by teaching them how to meet their own information needs
D)choose the appropriate risk control strategy for the firm

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
53
When network traffic is encrypted, it is invisible and its content and purpose are masked. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
54
Successful, robust systems often need the most support because users want to learn the features, try all the capabilities, and discover how the system can help them perform their business functions.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
55
Adaptive maintenance requests for major errors receive a high priority and a maintenance team begins work on the problem immediately. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
56
Adaptive maintenance always is less difficult than new systems development because the enhancements need not work within the constraints of an existing system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
57
Although the procedures for corrective maintenance and adaptive maintenance are alike, minor corrective maintenance requires more IT department resources than minor adaptive maintenance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
58
Possible disadvantages of rotating IT staff from maintenance to new systems groups include ____.
A)analysts learn only one skill and the organization is less versatile
B)overhead costs increase when people move from one job to another
C)systems analysts have less opportunity to become skilled at any one job
D)some analysts must spend a substantial amount of time in a job that is less desirable to them
A)analysts learn only one skill and the organization is less versatile
B)overhead costs increase when people move from one job to another
C)systems analysts have less opportunity to become skilled at any one job
D)some analysts must spend a substantial amount of time in a job that is less desirable to them

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
59
Both adaptive and perfective maintenance activities decrease in a dynamic business environment. _________________________

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
60
Requests for corrective and adaptive maintenance normally come from the IT department, while users usually initiate perfective maintenance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
61
When performing perfective maintenance, analysts often use a technique called software ____________________.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
62
Newly hired and recently promoted IT staff members often are assigned to maintenance projects because their managers believe that maintenance work offers a valuable learning experience.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
63
When analysts learn different skills, the organization is more versatile and people can shift to meeting changing business needs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
64
With a release methodology, even when changes would improve system efficiency or user productivity, the potential savings must wait until the next release date, which might increase operational costs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
65
In a PKE environment, each user on the network has a pair of keys: a public key and a private key.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
66
COMPLETION

As shown in the accompanying figure, ____________________ maintenance is a type of maintenance that improves efficiency.

As shown in the accompanying figure, ____________________ maintenance is a type of maintenance that improves efficiency.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
67
COMPLETION

As shown in the accompanying figure, ____________________ maintenance is a type of maintenance that adds new capability and enhancements.

As shown in the accompanying figure, ____________________ maintenance is a type of maintenance that adds new capability and enhancements.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
68
Bandwidth requirements are expressed in bytes per minute.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
69
When corrective action cannot occur immediately, users appreciate feedback from the system administrator and should be kept informed of any decisions or actions that affect their maintenance requests.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
70
Retention periods can be a specific number of months or years, depending on legal requirements and company policy.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
71
Configuration management is sometimes referred to as change control.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
72
COMPLETION

As shown in the accompanying figure, ____________________ maintenance is a type of maintenance performed to fix errors.

As shown in the accompanying figure, ____________________ maintenance is a type of maintenance performed to fix errors.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
73
As enterprise-wide information systems grow more complex, configuration management becomes less and less useful.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
74
Application security requires an understanding of services, hardening, application permissions, input validation techniques, software patches and updates, and software logs.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
75
One technique that can be used in perfective maintenance is software reengineering.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
76
A(n) ____________________ is a new feature or capability added to an operational system that makes the system easier to use.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
77
In many companies, the systems review committee separates maintenance requests from new systems development requests when evaluating requests and setting priorities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
78
IT staff members usually initiate requests for perfective and preventive maintenance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
79
As the first step in capacity planning, analysts develop a current model based on the system's present workload and performance specifications.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck
80
Companies with limited resources always consider new systems development, adaptive maintenance, and corrective maintenance less important than perfective maintenance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 112 في هذه المجموعة.
فتح الحزمة
k this deck








