Deck 12: Monitoring and Auditing AIS
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/48
العب
ملء الشاشة (f)
Deck 12: Monitoring and Auditing AIS
1
Which of the following is not an approach used for the online analytical processing (OLAP).
A) Exception reports
B) What-if simulations
C) Consolidation
D) Data mining
A) Exception reports
B) What-if simulations
C) Consolidation
D) Data mining
D
2
Computer-assisted audit techniques (CAAT)are often used when auditing a company's IT infrastructure.
False
3
Which of the following describes a group of computers that connects the internal users of a company distributed over an office building?
A) Internet
B) LAN
C) Virtual private network (VPN)
D) Decentralized network
A) Internet
B) LAN
C) Virtual private network (VPN)
D) Decentralized network
B
4
The data in a data warehouse are updated when transactions are processed.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
5
Parallel simulation attempts to simulate the firm's key features or processes.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
6
Accountants increasingly participate in designing internal controls and improving business and IT processes in a database environment.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
7
A wireless network is comprised access points and stations.Access points logically connect stations to a firm's network.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
8
Parallel simulation uses an independent program to simulate a part of an existing application program,and is designed to test the validity and to verify the accuracy of an existing application program.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
9
The Generally Accepted Auditing Standards (GAAS)issued by PCAOB provide guidelines for conducting an IS/IT audit.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
10
A data warehouse is for daily operations and often includes data for the current fiscal year only.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
11
Integrated test facility (ITF)is an automated technique that enables test data to be continually evaluated during the normal operation of a system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
12
Data governance is the convergence of data quality,data management,data policies,business process management,and risk management surrounding the handling of data in a company.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
13
Data mining is the process of searching for patterns in the data in a data warehouse and to analyze the patterns for decision making.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
14
Virtual private network (VPN)is a private network,provided by a third party,for exchanging information through a high capacity connection.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
15
Embedded audit module is a programmed audit module that is added to the system under review.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
16
Which of the statements regarding the data warehouse is incorrect?
A) It is a centralized collection of firm-wide data
B) The purpose of a data warehouse is to provide a rich data set for management to identify patterns and to examine trends of business events
C) Includes data for the current fiscal year only
D) The data in a data warehouse is pulled from each of the operational databases periodically
A) It is a centralized collection of firm-wide data
B) The purpose of a data warehouse is to provide a rich data set for management to identify patterns and to examine trends of business events
C) Includes data for the current fiscal year only
D) The data in a data warehouse is pulled from each of the operational databases periodically

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
17
Which of the following statements about switches is correct?
A) Hub is smarter than Switch.
B) Switches provide more security protections than hubs do for a company's internal network.
C) Switch is widely used in WANs.
D) A Switch contains multiple ports.
A) Hub is smarter than Switch.
B) Switches provide more security protections than hubs do for a company's internal network.
C) Switch is widely used in WANs.
D) A Switch contains multiple ports.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
18
A continuous audit is to perform audit-related activities on a continuous basis.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
19
The purpose of a company's firewall is to:
A) Guard against spoofing
B) Filtering packets
C) Deny computer hackers access to sensitive data
D) All of the above
A) Guard against spoofing
B) Filtering packets
C) Deny computer hackers access to sensitive data
D) All of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
20
Firewalls are security systems comprised of hardware and software that is built using routers,servers,and a variety of software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
21
Which of the following statements about firewalls is wrong?
A) A firewall is a security system comprised of hardware and software that is built using routers, servers, and a variety of software
B) A firewall allows individuals on the corporate network to send and receive data packets from the Internet
C) A firewall can filter through packets coming from outside networks to prevent unauthorized access
D) A firewall connects different LANs, software-based intelligent devices, examines IP addresses
A) A firewall is a security system comprised of hardware and software that is built using routers, servers, and a variety of software
B) A firewall allows individuals on the corporate network to send and receive data packets from the Internet
C) A firewall can filter through packets coming from outside networks to prevent unauthorized access
D) A firewall connects different LANs, software-based intelligent devices, examines IP addresses

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
22
Which of the following statements regarding the purposes of an operating system is correct?
A) To ensure the integrity of a system
B) To control the flow of multiprogramming and tasks of scheduling in the computer
C) To allocate computer resources to users and applications
D) All of the above are correct
A) To ensure the integrity of a system
B) To control the flow of multiprogramming and tasks of scheduling in the computer
C) To allocate computer resources to users and applications
D) All of the above are correct

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
23
What is data mining?
A) A particular attribute of information.
B) A common term for the representation of multidimensional data.
C) The process of analyzing data to extract of information that is not affected by the raw data alone.
D) None of the above is correct.
A) A particular attribute of information.
B) A common term for the representation of multidimensional data.
C) The process of analyzing data to extract of information that is not affected by the raw data alone.
D) None of the above is correct.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
24
Which of the following statements is wrong regarding continuous audit?
A) Continuous audit is to perform audit-related activities on a continuous basis
B) Testing in continuous audits often consists of continuous controls monitoring and continuous data assurance
C) Technology plays a key role in continuous audit in analyzing trends and patterns of transactions, identifying exceptions and anomalies, and testing controls
D) Continuous audit is frequently used to perform substantive tests and is used for testing of controls through transactional-data analysis
A) Continuous audit is to perform audit-related activities on a continuous basis
B) Testing in continuous audits often consists of continuous controls monitoring and continuous data assurance
C) Technology plays a key role in continuous audit in analyzing trends and patterns of transactions, identifying exceptions and anomalies, and testing controls
D) Continuous audit is frequently used to perform substantive tests and is used for testing of controls through transactional-data analysis

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
25
LAN is the abbreviation for
A) Large Area Network.
B) Local Area Network.
C) Longitudinal Analogue Network.
D) Low Analytical Nets.
A) Large Area Network.
B) Local Area Network.
C) Longitudinal Analogue Network.
D) Low Analytical Nets.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
26
Which of the following strategies will a CPA most likely consider in auditing an entity that processes most of its financial data only in electronic form,such as a paperless system?
A) Continuous monitoring and analysis of transaction processing with an embedded audit module.
B) Increased reliance on internal control activities that emphasize the segregation of duties.
C) Verification of encrypted digital certificates used to monitor the authorization of transactions.
D) Extensive testing of firewall boundaries that restrict the recording of outside network traffic.
A) Continuous monitoring and analysis of transaction processing with an embedded audit module.
B) Increased reliance on internal control activities that emphasize the segregation of duties.
C) Verification of encrypted digital certificates used to monitor the authorization of transactions.
D) Extensive testing of firewall boundaries that restrict the recording of outside network traffic.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
27
Which of the following statements regarding the black-box approach for systems auditing is correct?
A) The auditors need to gain detailed knowledge of the systems' internal logic
B) The black-box approach could be adequate when automated systems applications are complicated
C) The auditors first calculating expected results from the transactions entered into the system. Then, the auditors compare these calculations to the processing or output results.
D) All of the above are correct
A) The auditors need to gain detailed knowledge of the systems' internal logic
B) The black-box approach could be adequate when automated systems applications are complicated
C) The auditors first calculating expected results from the transactions entered into the system. Then, the auditors compare these calculations to the processing or output results.
D) All of the above are correct

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
28
What is the test data technique?
A) It uses a set of input data to validate system integrity.
B) It requires auditors to prepare both valid and invalid data to examine critical logics and controls of the system
C) It is an automated technique that enables test data to be continually evaluated during the normal operation of a system
D) A and B are correct
E) None of the above is correct
A) It uses a set of input data to validate system integrity.
B) It requires auditors to prepare both valid and invalid data to examine critical logics and controls of the system
C) It is an automated technique that enables test data to be continually evaluated during the normal operation of a system
D) A and B are correct
E) None of the above is correct

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
29
Common IT techniques that are needed to implement continuous auditing include
A) Data warehouse and data mining
B) Transaction logging and query tools
C) Computer-assisted audit techniques.
D) All of the above.
A) Data warehouse and data mining
B) Transaction logging and query tools
C) Computer-assisted audit techniques.
D) All of the above.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
30
Which of the following is not a management control for wireless networks?
A) Assigning roles and responsibilities of employees for access control
B) Conducting risk assessment on a regular basis
C) Conducting appropriate awareness training on wireless networks
D) Creating policies and procedures
A) Assigning roles and responsibilities of employees for access control
B) Conducting risk assessment on a regular basis
C) Conducting appropriate awareness training on wireless networks
D) Creating policies and procedures

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
31
Within a WAN,a router would perform which of the following functions?
A) Provide the communication within the network
B) Select network pathways within a network for the flow of data packets.
C) Amplify and rebroadcast signals in a network
D) Forward data packets to their internal network destination
A) Provide the communication within the network
B) Select network pathways within a network for the flow of data packets.
C) Amplify and rebroadcast signals in a network
D) Forward data packets to their internal network destination

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
32
Which of the following statements is not correct?
A) The IP address of a desktop computer often changes
B) The MAC address of a desktop computer often changes
C) The IP address of a Web server does not change
D) Each hardware device must have a MAC address
A) The IP address of a desktop computer often changes
B) The MAC address of a desktop computer often changes
C) The IP address of a Web server does not change
D) Each hardware device must have a MAC address

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
33
The results of a generalized audit software simulation of the aging of accounts receivable revealed substantial differences in the aging contribution,even though grand totals reconciled.Which of the following should the IS auditor do first to resolve the discrepancy?
A) Recreate the test, using different software.
B) List a sample of actual data to verify the accuracy of the test program.
C) Ignore the discrepancy because the grand totals reconcile and instruct the controller to correct program.
D) Create test transactions and run test data on both the production and simulation program.
A) Recreate the test, using different software.
B) List a sample of actual data to verify the accuracy of the test program.
C) Ignore the discrepancy because the grand totals reconcile and instruct the controller to correct program.
D) Create test transactions and run test data on both the production and simulation program.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
34
Which of the following is not a benefit of using wireless technology?
A) Mobility
B) Rapid deployment
C) Flexibility and Scalability
D) Security
A) Mobility
B) Rapid deployment
C) Flexibility and Scalability
D) Security

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
35
Which of the following is not a use of CAATs in auditing?
A) Test of details of transactions and balances
B) Analytical review procedures
C) Fraud examination
D) Produce terms and conditions of employment
A) Test of details of transactions and balances
B) Analytical review procedures
C) Fraud examination
D) Produce terms and conditions of employment

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
36
Which of the following is the primary reason that many auditors hesitate to use embedded audit modules?
A) Embedded audit modules cannot be protected from computer viruses.
B) Auditors are required to monitor embedded audit modules continuously to obtain valid results.
C) Embedded audit modules can easily be modified through management tampering.
D) Auditors are required to be involved in the system design of the application to be monitored.
A) Embedded audit modules cannot be protected from computer viruses.
B) Auditors are required to monitor embedded audit modules continuously to obtain valid results.
C) Embedded audit modules can easily be modified through management tampering.
D) Auditors are required to be involved in the system design of the application to be monitored.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
37
What is the man-in-the-middle threat for wireless LANs?
A) The attacker impersonates an authorized user and gains certain unauthorized privileges to the wireless network
B) The attacker passively monitors wireless networks for data, including authentication credentials
C) The attacker steals or makes unauthorized use of a service
D) The attacker actively intercepts communications between wireless clients and access points to obtain authentication credentials and data.
A) The attacker impersonates an authorized user and gains certain unauthorized privileges to the wireless network
B) The attacker passively monitors wireless networks for data, including authentication credentials
C) The attacker steals or makes unauthorized use of a service
D) The attacker actively intercepts communications between wireless clients and access points to obtain authentication credentials and data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
38
Which statements are incorrect about virtual private network (VPN)?
A) It is a way to use the public telecommunication infrastructure in providing secures access to an organization's network.
B) It enables the employees to work remotely by accessing their firm's network securely using the Internet
C) The packets sent through VPN are encrypted and with authentication technology.
D) The expensive cost is one major disadvantage of VPN.
A) It is a way to use the public telecommunication infrastructure in providing secures access to an organization's network.
B) It enables the employees to work remotely by accessing their firm's network securely using the Internet
C) The packets sent through VPN are encrypted and with authentication technology.
D) The expensive cost is one major disadvantage of VPN.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
39
Which of the following is least likely to be considered a component of a computer network?
A) Application programs.
B) Computers.
C) Servers.
D) Routers.
A) Application programs.
B) Computers.
C) Servers.
D) Routers.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
40
Masquerading threat for wireless LANs is:
A) The attacker actively intercepts communications between wireless clients and access points to obtain authentication credentials and data
B) The attacker alters a legitimate message sent via wireless networks by deleting, adding to, changing, or reordering it
C) The attacker passively monitors wireless networks for data, including authentication credentials
D) The attacker impersonates an authorized user and gains certain unauthorized privileges to the wireless network
A) The attacker actively intercepts communications between wireless clients and access points to obtain authentication credentials and data
B) The attacker alters a legitimate message sent via wireless networks by deleting, adding to, changing, or reordering it
C) The attacker passively monitors wireless networks for data, including authentication credentials
D) The attacker impersonates an authorized user and gains certain unauthorized privileges to the wireless network

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
41
Categorize the following scenarios as management,operational,or technical controls for wireless networks' security controls. 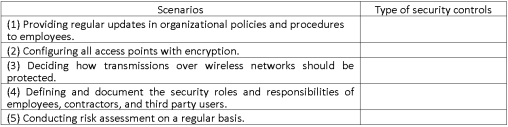


فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
42
What are the differences between LANs and WANs? Have you ever used any LANs and WANS?
1)LANs covers a small area while WANs covers a significantly larger area.
2)LANs speeds are also significantly faster than WANs.
3)LANs is more secure than WANs.
4)WANs are much more expensive to implement than LANs.
The Internet is the most popular WAN.A local area network is often used in a computer lab on campus.(Students' answers may vary.)
1)LANs covers a small area while WANs covers a significantly larger area.
2)LANs speeds are also significantly faster than WANs.
3)LANs is more secure than WANs.
4)WANs are much more expensive to implement than LANs.
The Internet is the most popular WAN.A local area network is often used in a computer lab on campus.(Students' answers may vary.)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
43
What are the general security objectives for both wired LANs and wireless LANs?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
44
What are the benefits of conducting continuous audits (or monitoring)?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
45
List common security threats for wireless LANs.Find a specific case in which the security of wireless LANs was threatened.Given the case you find,comment on how to prevent or mitigate the threats?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
46
Discuss five significant barriers that are often encountered in implementing continuous auditing?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
47
What are the two approaches of CAATs in auditing systems? What are the differences between them?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck
48
Identify each of the following statements with one of the five fundamental control objectives of operating systems.
Control objectives:
(a)Protect operations systems from users.
(b)The operating system must protect users from each other.
(c)The operating system must be protected from itself.
(d)The operating system must be protected from its environment.
(e)The operating system must protect users from themselves.

Control objectives:
(a)Protect operations systems from users.
(b)The operating system must protect users from each other.
(c)The operating system must be protected from itself.
(d)The operating system must be protected from its environment.
(e)The operating system must protect users from themselves.


فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 48 في هذه المجموعة.
فتح الحزمة
k this deck








