Deck 10: Accounting Information Systems and Internal Controls
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/57
العب
ملء الشاشة (f)
Deck 10: Accounting Information Systems and Internal Controls
1
Corporate governance is a set of processes and policies in managing an organization with sound ethics to safeguard the interests of its stakeholders.
True
2
Processing controls are IT general controls.
False
3
Which of the following is the best way to compensate for the lack of adequate segregation of duties in a small organization?
A) Disclosing lack of segregation of duties to external auditors during the annual review.
B) Replacing personnel every three or four years.
C) Requiring accountants to pass a yearly background check.
D) Allowing for greater management oversight of incompatible activities.
A) Disclosing lack of segregation of duties to external auditors during the annual review.
B) Replacing personnel every three or four years.
C) Requiring accountants to pass a yearly background check.
D) Allowing for greater management oversight of incompatible activities.
D
4
Which of the following items is one of the eight components of COSO's enterprise risk management framework?
A) Operations.
B) Reporting.
C) Monitoring.
D) Compliance.
A) Operations.
B) Reporting.
C) Monitoring.
D) Compliance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
5
COBIT (Control Objectives for Information and related Technology)is a generally accepted framework for IT governance in the U.S.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
6
Public Company Accounting Oversight Board (PCAOB)Auditing Standard No.5 (AS 5)encourages auditors to start from the basic/bottom of financial records to identify the key controls.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
7
The chief executive officer is ultimately responsible for enterprise risk management.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
8
Internal control is a process consisting of ongoing tasks and activities.It is a means to an end,not an end in itself.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
9
Segregation of duties reduces the risk of errors and irregularities in accounting records.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
10
According to COSO,which of the following components of the enterprise risk management addresses an entity's integrity and ethical values?
A) Information and communication
B) Internal environment.
C) Risk assessment.
D) Control activities.
A) Information and communication
B) Internal environment.
C) Risk assessment.
D) Control activities.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
11
According to the Sarbanes-Oxley Act of 2002,it is the responsibility of the Board of Directors to establish and maintain the effectiveness of internal control.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
12
A firm must establish control policies,procedures,and practices that ensure the firm's business objectives are achieved and its risk mitigation strategies are carried out.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
13
The main objective of the ISO 27000 series is to provide a model for establishing,implementing,operating,monitoring,maintaining,and improving information security.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
14
The Sarbanes-Oxley Act of 2002 (SOX)2002 requires the management of all companies and their auditors to assess and report on the design and effectiveness of internal control over financial reporting annually.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
15
Given the requirement of the Sarbanes-Oxley Act of 2002 (SOX),the Public Company Accounting Oversight Board (PCAOB)established the Securities and Exchange Commission (SEC)to provide independent oversight of public accounting firms.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
16
Internal controls guarantee the accuracy and reliability of accounting records.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
17
Which of the following represents an inherent limitation of internal controls?
A) Bank reconciliations are not performed on a timely basis.
B) The CEO can request a check with no purchase order.
C) Customer credit check not performed.
D) Shipping documents are not matched to sales invoices.
A) Bank reconciliations are not performed on a timely basis.
B) The CEO can request a check with no purchase order.
C) Customer credit check not performed.
D) Shipping documents are not matched to sales invoices.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
18
In a computerized environment,internal controls can be categorized as general controls and application controls.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
19
The risk of a company's internal auditing processes failing to catch the misstated dollar amount of revenue on the company's income statement is classified as inherent risk.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
20
In a large pubic corporation,evaluating internal control procedures should be responsibility of:
A) Accounting management staff who report to the CFO.
B) Internal audit staff who report to the board of directors.
C) Operations management staff who report to the chief operation officer.
D) Security management staff who report to the chief facilities officer.
A) Accounting management staff who report to the CFO.
B) Internal audit staff who report to the board of directors.
C) Operations management staff who report to the chief operation officer.
D) Security management staff who report to the chief facilities officer.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
21
Which of the following most likely would not be considered as an inherent limitation of the effectiveness of a firm's internal control?
A) Incompatible duties.
B) Management override.
C) Mistakes in judgment.
D) Collusion among employees.
A) Incompatible duties.
B) Management override.
C) Mistakes in judgment.
D) Collusion among employees.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
22
Which of the following control activities should be taken to reduce the risk of incorrect processing in a newly installed computerized accounting system?
A) Segregation of duties.
B) Ensure proper authorization of transactions.
C) Adequately safeguard assets.
D) Independently verify the transactions.
A) Segregation of duties.
B) Ensure proper authorization of transactions.
C) Adequately safeguard assets.
D) Independently verify the transactions.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
23
Which of the following is not a component of internal control as defined by COSO?
A) Control environment.
B) Control activities.
C) Inherent risk
D) Monitoring.
A) Control environment.
B) Control activities.
C) Inherent risk
D) Monitoring.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
24
A manufacturing firm identified that it would have difficulty sourcing raw materials locally,so it decided to relocate its production facilities.According to COSO,this decision represents which of the following response to the risk?
A) Risk reduction.
B) Prospect theory.
C) Risk sharing.
D) Risk acceptance.
A) Risk reduction.
B) Prospect theory.
C) Risk sharing.
D) Risk acceptance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
25
Review of the audit log is an example of which of the following types of security control?
A) Governance.
B) Detective.
C) Preventive.
D) Corrective.
A) Governance.
B) Detective.
C) Preventive.
D) Corrective.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
26
The overall attitude and awareness of a firm's top management and board of directors concerning the importance of internal control is often reflected in its
A) Computer-based controls.
B) System of segregation of duties.
C) Control environment.
D) Safeguards over access to assets.
A) Computer-based controls.
B) System of segregation of duties.
C) Control environment.
D) Safeguards over access to assets.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
27
Which of the following statement is correct regarding internal control?
A) A well-designed internal control environment ensures the achievement of an entity's control objectives.
B) An inherent limitation to internal control is the fact that controls can be circumvented by management override.
C) A well-designed and operated internal control environment should detect collusion perpetrated by two people.
D) Internal control in a necessary business function and should be designed and operated to detect errors and fraud.
A) A well-designed internal control environment ensures the achievement of an entity's control objectives.
B) An inherent limitation to internal control is the fact that controls can be circumvented by management override.
C) A well-designed and operated internal control environment should detect collusion perpetrated by two people.
D) Internal control in a necessary business function and should be designed and operated to detect errors and fraud.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
28
Obtaining an understanding of an internal control involves evaluating the design of the control and determining whether the control has been:
A) Authorized.
B) Implemented.
C) Tested.
D) Monitored.
A) Authorized.
B) Implemented.
C) Tested.
D) Monitored.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
29
An entity's ongoing monitoring activities often include
A) Periodic audits by the audit committee.
B) Reviewing the purchasing function.
C) The audit of the annual financial statements.
D) Control risk assessment in conjunction with quarterly reviews.
A) Periodic audits by the audit committee.
B) Reviewing the purchasing function.
C) The audit of the annual financial statements.
D) Control risk assessment in conjunction with quarterly reviews.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
30
Which of the following is considered an application input control?
A) Run control total.
B) Edit check.
C) Reporting distribution log.
D) Exception report.
A) Run control total.
B) Edit check.
C) Reporting distribution log.
D) Exception report.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
31
An auditor assesses control risk because it
A) is relevant to the auditor's understanding of the control environment.
B) provides assurance that the auditor's materiality levels are appropriate.
C) indicates to the auditor where inherent risk may be the greatest.
D) affects the level of detection risk that the auditor may accept.
A) is relevant to the auditor's understanding of the control environment.
B) provides assurance that the auditor's materiality levels are appropriate.
C) indicates to the auditor where inherent risk may be the greatest.
D) affects the level of detection risk that the auditor may accept.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
32
When considering internal control,an auditor should be aware of reasonable assurance,which recognizes that
A) Internal control may be ineffective due to mistakes in judgment and personal carelessness.
B) Adequate safeguards over access to assets and records should permit an entity to maintain proper accountability.
C) Establishing and maintaining internal control is an important responsibility of management.
D) The cost of an entity's internal control should not exceed the benefits expected to be derived.
A) Internal control may be ineffective due to mistakes in judgment and personal carelessness.
B) Adequate safeguards over access to assets and records should permit an entity to maintain proper accountability.
C) Establishing and maintaining internal control is an important responsibility of management.
D) The cost of an entity's internal control should not exceed the benefits expected to be derived.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
33
Proper segregation of duties calls for separation of the following functions:
A) Authorization, execution, and payment.
B) Authorization, recording, and custody.
C) Custody, execution, and reporting.
D) Authorization, payment, and recording.
A) Authorization, execution, and payment.
B) Authorization, recording, and custody.
C) Custody, execution, and reporting.
D) Authorization, payment, and recording.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
34
All of the following are examples of internal control procedures except
A) Using pre-numbered documents
B) Reconciling the bank statement
C) Customer satisfaction surveys
D) Insistence that employees take vacations
A) Using pre-numbered documents
B) Reconciling the bank statement
C) Customer satisfaction surveys
D) Insistence that employees take vacations

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
35
Control risk should be assessed in terms of
A) Specific controls.
B) Types of potential fraud.
C) Financial statement assertions.
D) Control environment factors.
A) Specific controls.
B) Types of potential fraud.
C) Financial statement assertions.
D) Control environment factors.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
36
Each of the following types of controls is considered to be an entity-level control,except those:
A) Relating to the control environment.
B) Pertaining to the company's risk assessment process.
C) Regarding the company's annual stockholder meeting.
D) Addressing policies over significant risk management practices
A) Relating to the control environment.
B) Pertaining to the company's risk assessment process.
C) Regarding the company's annual stockholder meeting.
D) Addressing policies over significant risk management practices

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
37
Controls in the information technology area are classified into preventive,detective,and corrective categories.Which of the following is preventive control?
A) Contingency planning.
B) Hash total.
C) Echo check.
D) Access control software.
A) Contingency planning.
B) Hash total.
C) Echo check.
D) Access control software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
38
According to COSO which of the following is not a component of internal control?
A) Control risk.
B) Control activities.
C) Monitoring.
D) Control environment.
A) Control risk.
B) Control activities.
C) Monitoring.
D) Control environment.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
39
Management philosophy and operating style would have a relatively less significant influence on a firm's control environment when
A) The internal auditor reports directly to the controller.
B) Management is dominated by one individual.
C) Accurate management job descriptions delineate specific duties.
D) The audit committee does not have regular meetings.
A) The internal auditor reports directly to the controller.
B) Management is dominated by one individual.
C) Accurate management job descriptions delineate specific duties.
D) The audit committee does not have regular meetings.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
40
The Public Company Accounting Oversight Board (PCAOB)is not responsible for standards related to:
A) Accounting practice.
B) Attestation.
C) Auditing.
D) Quality control over attestation and/or assurance.
A) Accounting practice.
B) Attestation.
C) Auditing.
D) Quality control over attestation and/or assurance.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
41
The information system of Company ABC is deemed to be 90% reliable.A major threat has been identified with an exposure of $5,000,000.Two control procedures exist to deal with the threat.Implementation of control A would cost of $140,000 and reduce the risk to 4%.Implementation of control B would cost $100,000 and reduce the risk to 6%.Implementation of both controls would cost $220,000 and reduce the risk to 2%.Given the data and based solely on an economic analysis of costs and benefits,which control procedure should you choose?
C.
C.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
42
What are the definitions of "governance" and "management" in the COBIT 5.0 framework?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
43
The internal control provisions of SOX apply to which companies in the United States?
A) All companies.
B) SEC registrants.
C) All issuer (public) companies and nonissuer (nonpublic) companies with more than $100,000,000 of net worth.
D) All nonissuer companies.
A) All companies.
B) SEC registrants.
C) All issuer (public) companies and nonissuer (nonpublic) companies with more than $100,000,000 of net worth.
D) All nonissuer companies.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
44
What are the three main functions of COSO ERM?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
45
Tracing shipping documents to pre-numbered sales invoices provides evidence that
A) No duplicate shipments or billings occurred.
B) Shipments to customers were properly invoiced.
C) All goods ordered by customers were shipped.
D) All pre-numbered sales invoices were accounted for.
A) No duplicate shipments or billings occurred.
B) Shipments to customers were properly invoiced.
C) All goods ordered by customers were shipped.
D) All pre-numbered sales invoices were accounted for.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
46
Which of the following is an example of a validity check?
A) The computer ensures that a numerical amount in a record does not exceed some predetermined amount.
B) As the computer corrects errors and data are successfully resubmitted to the system, the causes of the errors are printed out.
C) The computer flags any transmission for which the control field value did not match that of an existing file record.
D) After data for a transaction are entered, the computer sends certain data back to the terminal for comparison with data originally sent.
A) The computer ensures that a numerical amount in a record does not exceed some predetermined amount.
B) As the computer corrects errors and data are successfully resubmitted to the system, the causes of the errors are printed out.
C) The computer flags any transmission for which the control field value did not match that of an existing file record.
D) After data for a transaction are entered, the computer sends certain data back to the terminal for comparison with data originally sent.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
47
A customer intended to order 100 units of a product A,but incorrectly ordered nonexistent product B. Which of the following controls most likely would detect this error?
A) Validity check
B) Record count
C) Hash total
D) Parity check
A) Validity check
B) Record count
C) Hash total
D) Parity check

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
48
Describe the three categories of objectives and five essential components of the COSO 2.0 framework.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
49
Which of the following input controls is a numeric value computed to provide assurance that the original value has not been altered in construction or transmission?
A) Hash total.
B) Parity check.
C) Encryption.
D) Check digit.
A) Hash total.
B) Parity check.
C) Encryption.
D) Check digit.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
50
The framework could be used by management in its internal control assessment under requirements of SOX is the:
A) COSO internal framework.
B) COSO enterprise risk management framework.
C) COBIT framework.
D) All of the above are correct.
A) COSO internal framework.
B) COSO enterprise risk management framework.
C) COBIT framework.
D) All of the above are correct.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
51
Reconciliation of cash accounts may be referred to as what type of control?
A) Detective.
B) Preventive.
C) Adjustive.
D) Non-routine.
A) Detective.
B) Preventive.
C) Adjustive.
D) Non-routine.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
52
Which internal control(s)would you recommend to prevent the following situations from occurring?
a.While entering the details about a large credit sale,a clerk mistakenly typed in a nonexistent account number.Consequently,the company never received the payment from this customer.
b.A customer filled in a wrong account number on the remittance advice.Consequently,a clerk entered the same number into the system,and the payment was credited to another customer's account.
c.After processing a large sales transaction,the inventory records showed negative quantities on hand for several items.
a.While entering the details about a large credit sale,a clerk mistakenly typed in a nonexistent account number.Consequently,the company never received the payment from this customer.
b.A customer filled in a wrong account number on the remittance advice.Consequently,a clerk entered the same number into the system,and the payment was credited to another customer's account.
c.After processing a large sales transaction,the inventory records showed negative quantities on hand for several items.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
53
Sound internal control dictates that immediately upon receiving checks from customers by mail,a responsible employee should
A) Add the checks to the daily cash summary.
B) Verify that each check is supported by a pre-numbered sales invoice.
C) Prepare a summary listing of checks received.
D) Record the checks in the cash receipts journal.
A) Add the checks to the daily cash summary.
B) Verify that each check is supported by a pre-numbered sales invoice.
C) Prepare a summary listing of checks received.
D) Record the checks in the cash receipts journal.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
54
Discuss the ethical values created in Starbucks.How do they help to form the firm's control environment?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
55
Put the listed steps in the corresponding parentheses in the risk assessment and response approach diagram below.
(A)Avoid,share or accept risk
(B)Reduce risk by implementing controls
(C)Is it cost beneficial to protect the firm from the risk?
(D)Estimate the likelihood of each risk occurring
(E)Identify control to mitigate the risk
(F)Estimate the costs and benefits from instituting controls
(G)Identify the risks
(H)Estimate the impact or potential loss,from each risk
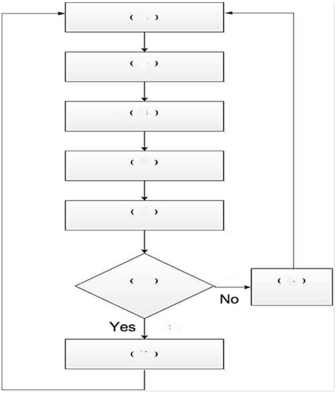
(A)Avoid,share or accept risk
(B)Reduce risk by implementing controls
(C)Is it cost beneficial to protect the firm from the risk?
(D)Estimate the likelihood of each risk occurring
(E)Identify control to mitigate the risk
(F)Estimate the costs and benefits from instituting controls
(G)Identify the risks
(H)Estimate the impact or potential loss,from each risk


فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
56
Which of the following is a computer test made to ascertain whether a given characteristic belongs to the group?
A) Check digit.
B) Validity check.
C) Echo check.
D) Limit check.
A) Check digit.
B) Validity check.
C) Echo check.
D) Limit check.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
57
What is the impact of the Sarbanes-Oxley Act of 2002 (SOX)on public companies and public accounting firms?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck








