Deck 10: Using Information Technology for Fraud Examination and Financial Forensics
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/57
العب
ملء الشاشة (f)
Deck 10: Using Information Technology for Fraud Examination and Financial Forensics
1
An association matrix is not useful for identifying major players who are central to an investigation and to identify linkages between those players.
False
2
Generally, a warrant or subpoena is not required to obtain digital evidence.
False
3
IDEA can read, display, analyze, manipulate, sample, and extract data from files obtained from many sources in only one format.
False
4
An activity that can enhance the ability to recover deleted files is the "Defrag" command.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
5
Case management software can be used in a number of situations to manage cases and case data.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
6
The acronym MICE signifies fraud motivations such as money, intellectualism, coercion, and ego.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
7
Data mining and knowledge discovery software is generally classified into two general categories: public domain and commercial applications.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
8
Record validation can include reasonableness checks, sequences checks, and other checks.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
9
Benford's Law can be used as an indicator of potential fraud.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
10
Validation controls detest input errors by flagging those transactions that fall within accepted ranges.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
11
Preparing link charts is a way to represent the associations, linkages, and other important relationship graphically.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
12
ACL and IDEA are examples of commercially available data mining software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
13
The simple act of turning on a confiscated computer, digital camera, cell phone, PDA, etc. may make all the evidence on that digital device inadmissible in a courtroom.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
14
Output controls address how to monitor waste and how to identify who is responsible for data accuracy, report distribution, and end-user controls.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
15
Once data sectors on computer files have been overwritten, generally a computer forensic specialist can still recover the files.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
16
Recovering deleted files is not considered difficult, provided that the file has not been overwritten or corrupted and that the drive has not been repartitioned or reformatted.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
17
Restoring data and files is a more sophisticated approach to recovering deleted files.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
18
An information technology IT audit consists of 1 planning, 2 tests of controls, and 3 substantive tests.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
19
There are two major ways to test IT systems - the "black-box" approach, and the "white-box" approach, which utilizes a relatively small dataset to test the system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
20
The source documents that support the electronic data systems do not need to be pre-numbered and used in sequence.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
21
Which of the following is NOT a tool to collect digital evidence?
A) Road MASSter
B) Encase
C) HDD Regenerator
D) Microsoft Dynamics GP
A) Road MASSter
B) Encase
C) HDD Regenerator
D) Microsoft Dynamics GP

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
22
Duplicate searches in data extraction and analysis software could be used to discover:
A) Invoices that have been paid twice
B) Missing employees
C) Missing invoices
D) Stolen inventory
A) Invoices that have been paid twice
B) Missing employees
C) Missing invoices
D) Stolen inventory

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
23
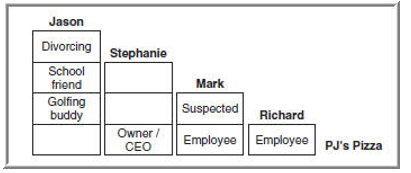
MC Graphic 10-5
-The graphic 10-5 is called an:
A) Association matrix
B) Link chart
C) Familial chart
D) Grouping chart

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
24
In data analysis and extraction software, the types of queries conducted on accounts receivable would includes everything EXCEPT:
A) Identifying debits to expense accounts
B) Create a list of customer limit increases
C) Age accounts receivable in various formats
D) Identify gaps in the sequence of invoice numbers
A) Identifying debits to expense accounts
B) Create a list of customer limit increases
C) Age accounts receivable in various formats
D) Identify gaps in the sequence of invoice numbers

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
25
An example of an input error that would likely be caught by a validation control in payroll processing would be:
A) Overtime hours above 10 hours for an individual.
B) Zero hours for a long time employee.
C) 90 hours worked by one employee in one week.
D) The addition of a new employee
A) Overtime hours above 10 hours for an individual.
B) Zero hours for a long time employee.
C) 90 hours worked by one employee in one week.
D) The addition of a new employee

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
26
Which of the following would be considered a batch control for payroll?
A) A total on FICA taxes withheld.
B) A total on Federal Income taxes withheld.
C) A total on employee hours.
D) A total on state income tax withheld.
A) A total on FICA taxes withheld.
B) A total on Federal Income taxes withheld.
C) A total on employee hours.
D) A total on state income tax withheld.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
27
Which of the following would be normally be detected as an input error in payroll processing?
A) An alphabetic character in the employee hours field.
B) Overtime hours above 10 hours for an individual employee.
C) Zero hours for a long time employee.
D) The addition of a new employee.
A) An alphabetic character in the employee hours field.
B) Overtime hours above 10 hours for an individual employee.
C) Zero hours for a long time employee.
D) The addition of a new employee.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
28
The assertions of management related to financial statements include all of the these EXCEPT:
A) The existence of assets and transactions.
B) The completeness of the transactions.
C) Proper disclosure of all rights and obligations.
D) Assurance of future profitability.
A) The existence of assets and transactions.
B) The completeness of the transactions.
C) Proper disclosure of all rights and obligations.
D) Assurance of future profitability.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
29
The general framework for viewing IT risks and controls include all the following EXCEPT
A) IT Operations
B) Systems Maintenance
C) Human Resource Management
D) Electric Commerce
A) IT Operations
B) Systems Maintenance
C) Human Resource Management
D) Electric Commerce

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
30
The functions of data extraction and analysis software tools includes all EXCEPT:
A) Compliance verification
B) Input into inventory system
C) Duplicate searches
D) Correlation analysis
A) Compliance verification
B) Input into inventory system
C) Duplicate searches
D) Correlation analysis

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
31
The functions of data extraction and analysis software tools includes all EXCEPT:
A) Sorting
B) Input into payroll system
C) Verifying multiples of a number
D) Correlations analysis
A) Sorting
B) Input into payroll system
C) Verifying multiples of a number
D) Correlations analysis

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
32
In data analysis and extraction software, the types of queries conducted on sales analysis would include everything EXCEPT:
A) Analyze sales returns and allowances
B) Selecting specifying journal entries for analysis
C) Summarize trends by customers type
D) Create reports on customer demand
A) Analyze sales returns and allowances
B) Selecting specifying journal entries for analysis
C) Summarize trends by customers type
D) Create reports on customer demand

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
33
An information technology IT audit consists of all EXCEPT
A) planning,
B) tests of controls,
C) substantive tests,
D) qualitative tests.
A) planning,
B) tests of controls,
C) substantive tests,
D) qualitative tests.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
34
Compliance verification in data extraction and analysis software could be used to discover all EXCEPT:
A) Credit approvals for customer credit limits by credit manager
B) Excessive per diem amounts on employee expense accounts
C) Criminal background searches on prospective employees
D) Insuring that middle managers do not exceed company mandated budget limits
A) Credit approvals for customer credit limits by credit manager
B) Excessive per diem amounts on employee expense accounts
C) Criminal background searches on prospective employees
D) Insuring that middle managers do not exceed company mandated budget limits

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
35
Verifying multiples of a number in data extraction and analysis software could be used to discover all EXCEPT:
A) Recalculation of invoice totals
B) Reimbursement rates for mileage
C) Paycheck amounts for hours worked
D) Embezzled petty cash
A) Recalculation of invoice totals
B) Reimbursement rates for mileage
C) Paycheck amounts for hours worked
D) Embezzled petty cash

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
36
Which of the following is not considered CAATTs Computer-Aided Audit Tools and Techniques software:
A) Microsoft Dynamics GP
B) IDEA
C) ACL
D) Picalo
A) Microsoft Dynamics GP
B) IDEA
C) ACL
D) Picalo

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
37
In data analysis and extraction software, the types of queries conducted on the general ledger would include everything EXCEPT:
A) Calculating financial ratios
B) Select specific journal entries for analysis
C) Age counts receivable in various formats
D) Create actual to budget comparison reports
A) Calculating financial ratios
B) Select specific journal entries for analysis
C) Age counts receivable in various formats
D) Create actual to budget comparison reports

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
38
One of the major functions of data security and privacy tools such as Privacy Suite is to:
A) Copy files
B) Rename files
C) Overwrite files
D) Recycle files
A) Copy files
B) Rename files
C) Overwrite files
D) Recycle files

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
39
Correlation analysis in data extraction and analysis software could be used to discover all EXCEPT:
A) Correlations where none existed previously
B) Non-existent inventory
C) Correlations that currently exist
D) How variables move in the same direction
A) Correlations where none existed previously
B) Non-existent inventory
C) Correlations that currently exist
D) How variables move in the same direction

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
40
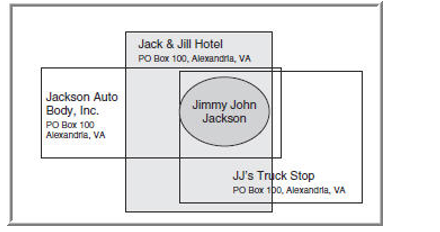
MC Graphic 10-4
-The graphic 10-4 is called an:
A) Association matrix
B) Link chart
C) Familial chart
D) Grouping chart

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
41
What functions are used by data extraction and analysis software to highlight red flags of fraud?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
42
What computer functions can make recovering deleted files more difficult?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
43
What is meant by the acronym CAATTs and what are they used for?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
44
This type of graphic allows the investigator to analyze the movement of goods services, people and money:
A) Gantt chart
B) Link chart
C) Association matrix
D) Flow diagram
A) Gantt chart
B) Link chart
C) Association matrix
D) Flow diagram

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
45
List and describe three graphical techniques used to support the forensics professional.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
46
List two commercial data extraction and analysis software and list four functions of this software.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
47
What role do graphics play in an investigation?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
48
What are the two categories of data mining and knowledge discovery software?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
49
What is the purpose of timelines in an investigation?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
50
What are the two major approaches for testing IT system controls?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
51
What is computer forensics?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
52
A married couple goes to a movie. During the movie, the husband strangles the wife. He is able to get her body home without attracting attention.
How is this possible?
How is this possible?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
53
How do e-discovery rules have an impact on the storage of e-mail and other electronic files?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
54
List five assertions of management in respect to financial statements.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
55
This type of graphic organizes information about events chronologically to determine what has occurred:
A) Link chart
B) Association matrix
C) Timeline
D) Flow diagram
A) Link chart
B) Association matrix
C) Timeline
D) Flow diagram

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
56
How is case management software used in an investigation?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck
57
The software product Analyst's Notebook I2 would be classified as:
A) Data analysis and extraction software
B) Case management software
C) Electronic spreadsheet
D) Data presentation software
A) Data analysis and extraction software
B) Case management software
C) Electronic spreadsheet
D) Data presentation software

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 57 في هذه المجموعة.
فتح الحزمة
k this deck








