Deck 8: Security
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال
سؤال

فتح الحزمة
قم بالتسجيل لفتح البطاقات في هذه المجموعة!
Unlock Deck
Unlock Deck
1/40
العب
ملء الشاشة (f)
Deck 8: Security
1
If you receive an email that says it is from Sam Johnson, your boss, with an odd EXE file as an attachment, it could be dangerous for all of the following reasons except:
A) It could be dangerous because the email might not really be from Sam.
B) It could be dangerous because the email might be from Sam's computer without his or her knowledge.
C) It could be dangerous even if it was sent knowingly because Sam didn't know a virus might be attached.
D) It could be dangerous because Sam gave someone his password once a long time ago
E) None of the above (indicating that all are true).
A) It could be dangerous because the email might not really be from Sam.
B) It could be dangerous because the email might be from Sam's computer without his or her knowledge.
C) It could be dangerous even if it was sent knowingly because Sam didn't know a virus might be attached.
D) It could be dangerous because Sam gave someone his password once a long time ago
E) None of the above (indicating that all are true).
E
2
An "evil twin" in the context of computer security is:
A) A virus-laden attachment that looks just like a sincere attachment
B) A duplicate badge that allows a nasty person entry into a data center
C) Someone who looks just like the Chief Information Officer, but steals data
D) An operating system that is not genuine
E) A counterfeit wifi connection in a hotel or coffee shop that appears to be genuine
A) A virus-laden attachment that looks just like a sincere attachment
B) A duplicate badge that allows a nasty person entry into a data center
C) Someone who looks just like the Chief Information Officer, but steals data
D) An operating system that is not genuine
E) A counterfeit wifi connection in a hotel or coffee shop that appears to be genuine
E
3
On the black market, stolen data in a "kit" that contains credit card information plus social security number and medical information is worth:
A) between $13 and $18 per record
B) between $43 and 65 per record
C) between $145 and $154 per record
D) between $100 and $1,000 per record
E) between $4,520 and $4,580 per record
A) between $13 and $18 per record
B) between $43 and 65 per record
C) between $145 and $154 per record
D) between $100 and $1,000 per record
E) between $4,520 and $4,580 per record
D
4
___ of breaches are caused by stealing a password
A) A very low percentage (somewhere around 1%)
B) A low percentage (around 10%)
C) A moderate percentage (around 25%)
D) A high percentage (around 50%)
E) A very high percentage (around 80%)
A) A very low percentage (somewhere around 1%)
B) A low percentage (around 10%)
C) A moderate percentage (around 25%)
D) A high percentage (around 50%)
E) A very high percentage (around 80%)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
5
Thanks to tightened security in operating systems, it is more difficult than ever before for hackers to break into systems, compared to the early 1990s, when people were much less often protected, less aware of risks, and more easily fooled.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
6
Examples of multi-factor authentication are:
A) passwords and text messages
B) passwords with longer than one character
C) a human will chat with you to see who you are
D) using two badges to allow you into a building
E) none of the above
A) passwords and text messages
B) passwords with longer than one character
C) a human will chat with you to see who you are
D) using two badges to allow you into a building
E) none of the above

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
7
In the Office of Personnel Management's case, the security breach made many people vulnerable to this.
A) Loss of personal property
B) Inaccurate personal data
C) Identity theft
D) Loss of access to personal data
E) Credit card fees
A) Loss of personal property
B) Inaccurate personal data
C) Identity theft
D) Loss of access to personal data
E) Credit card fees

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
8
It usually takes ____ for someone in a firm to discover a security compromise in a system, after the evidence shows up in logs or alerts
A) Several seconds
B) Several minutes
C) Several hours
D) Several days
E) Several months
A) Several seconds
B) Several minutes
C) Several hours
D) Several days
E) Several months

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
9
Over time, attackers have had to increase their skills to be able to attack systems or create viruses.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
10
The cost of a data breach in 2015 is estimated to be:
A) between $13 and $18 per record
B) between $43 and 65 per record
C) between $145 and $154 per record
D) between $100 and $1,000 per record
E) between $4,520 and $4,580 per record
A) between $13 and $18 per record
B) between $43 and 65 per record
C) between $145 and $154 per record
D) between $100 and $1,000 per record
E) between $4,520 and $4,580 per record

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
11
Many organizations and even consumers use this to control access to a network like the Internet, allowing only authorized traffic to pass.
A) Encryption
B) VPN
C) Firewall
D) Anonymizing tools
E) Filtering
A) Encryption
B) VPN
C) Firewall
D) Anonymizing tools
E) Filtering

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
12
Included in the five critical elements that are used to raise security in a firm are all of the following except:
A) Infrastructure
B) Law enforcement
C) Policies
D) Training
E) Investments
A) Infrastructure
B) Law enforcement
C) Policies
D) Training
E) Investments

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
13
All of the following are classic signs of a phishing message except:
A) Your email in-box is full and you must click on a link to increase storage
B) You just won a lottery or contest, and you need to click on a link to claim your prize
C) Poor grammar or spelling in a note that purports to be from a large company
D) Goods or services are offered at an impossibly low price
E) An emailed ad oddly does not provide any active links
A) Your email in-box is full and you must click on a link to increase storage
B) You just won a lottery or contest, and you need to click on a link to claim your prize
C) Poor grammar or spelling in a note that purports to be from a large company
D) Goods or services are offered at an impossibly low price
E) An emailed ad oddly does not provide any active links

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
14
Who is responsible for developing security education, awareness, and training programs?
A) IT people
B) Shared: IT leaders and business leaders
C) Business leaders
D) Consultants
E) Team of consultants and IT people
A) IT people
B) Shared: IT leaders and business leaders
C) Business leaders
D) Consultants
E) Team of consultants and IT people

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
15
Spoofing is:
A) When someone makes fun of you for falling for a phishing scam
B) When the "from" address says the name/email address of a person different from who really sent it
C) When hackers snoop around in a system
D) When a person from IT unlocks your email account
E) When you receive a notice of an inheritance
A) When someone makes fun of you for falling for a phishing scam
B) When the "from" address says the name/email address of a person different from who really sent it
C) When hackers snoop around in a system
D) When a person from IT unlocks your email account
E) When you receive a notice of an inheritance

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
16
The most common password of all in 2014 is:
A) Something complex that is hard to remember
B) None at all-they most commonly skip passwords and just press ENTER to continue
C) "password"
D) "123456"
E) "Rihanna"
A) Something complex that is hard to remember
B) None at all-they most commonly skip passwords and just press ENTER to continue
C) "password"
D) "123456"
E) "Rihanna"

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
17
When the Office of Personnel Management was hacked, all of the following are true except:
A) The hackers gained access to the building to steal the records
B) It took the Office of Personnel Management many months to detect the break-in
C) The hackers likely exploited a stolen password
D) The hackers did not need to escape in the blue turbocharged vehicle
E) None of the above (indicating that all are true)
A) The hackers gained access to the building to steal the records
B) It took the Office of Personnel Management many months to detect the break-in
C) The hackers likely exploited a stolen password
D) The hackers did not need to escape in the blue turbocharged vehicle
E) None of the above (indicating that all are true)

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
18
Who is responsible for decisions about security strategy?
A) IT people
B) Shared: IT leaders and business leaders
C) Business leaders
D) Consultants
E) Team of consultants and IT people
A) IT people
B) Shared: IT leaders and business leaders
C) Business leaders
D) Consultants
E) Team of consultants and IT people

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
19
In the Anthem Blue Cross breach, where 80 million names, birthdays, social security numbers, etc., were stolen, the hackers got in by:
A) Breaking into the building where they were stored
B) Obtaining passwords of five or more high-level employees
C) Making phone calls to insiders posing as IT people needing to log into their accounts
D) Emailing each of the 80 million patients asking for their private information
E) Recovering patient records from a large recycling bin
A) Breaking into the building where they were stored
B) Obtaining passwords of five or more high-level employees
C) Making phone calls to insiders posing as IT people needing to log into their accounts
D) Emailing each of the 80 million patients asking for their private information
E) Recovering patient records from a large recycling bin

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
20
It is estimated that ___ % of all firms have been breached:
A) 5% or less
B) 10% to 20%
C) 40% to 60%
D) 70% to 90%
E) Over 95%
A) 5% or less
B) 10% to 20%
C) 40% to 60%
D) 70% to 90%
E) Over 95%

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
21
According to the late L. Dain Gary, "You cannot make a computer secure."

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
22
What is Poulson's Law?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
23
You can purchase stolen credit cards on the "deep web" using a browser called "Tor."

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
24
A hacker who buys credit card information from hackers receives a short-term guarantee in case the card is declined.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
25
Two factor authentication is when you use two different methods for people trying to use the system. For instance, you can use a password and a challenge question

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
26
What are the shortcomings of passwords?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
27
The deep web is a part of the internet that includes unindexed websites offering both legal and illegal items, such as passports, citizenship, and even murders for hire.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
28
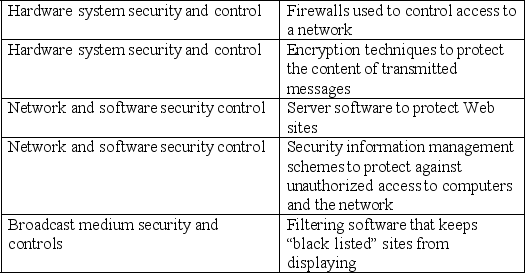
Match the security tool to its security category.


فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
29
What security and controls should a company use to protect its computer infrastructure? Why do managers need to be involved in the decisions about security and control measures?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
30
In the Target breach, the HVAC systems were actually attached to the retail sales system.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
31
Of the seven security policies noted in Chapter 7 (Figure 7.5), name at least three.
Matching
Matching

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
32
If you receive an email from your son, and the body of the email tells you to open an attachment because it is funny, the risk is pretty close to zero because it came from your son.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
33
Firewalls can be either in hardware or software form.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
34
A challenge question is when you are stopped at the gate and the guard asks who you are.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
35
The Deep Web is reputed to be 400 times larger than the public web.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
36
What is a piece of software that traps keystrokes and stores them for hackers to inspect later?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
37
Internal threats are considered the most lethal threat. What are they, why are they so lethal and what can a company do to protect against them?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
38
In the Target breach, the IT department was warned on or about the time the files were transferred.

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
39
This is a situation in which the thief counterfeits a different person's address

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck
40
What is a challenge question?

فتح الحزمة
افتح القفل للوصول البطاقات البالغ عددها 40 في هذه المجموعة.
فتح الحزمة
k this deck








