Consider the following diagram: 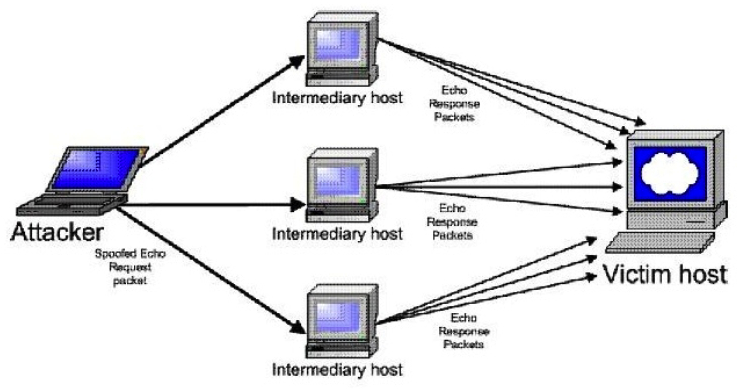 Which type of attack is occurring?
Which type of attack is occurring?
A) Polymorphic virus-based attack
B) Denial-of-service attack
C) Distributed denial-of-service attack
D) Man-in-the-middle attack using a packet sniffer
Correct Answer:
Verified
Q38: Which algorithm can use a 128-bit key,
Q39: Consider the following image of a packet
Q40: Consider the following image: Q41: Which of the following is a primary Q42: At what layer of the OSI/RM does Q43: What is the primary strength of symmetric-key Q45: Which of the following is most likely Q46: Consider the following diagram involving two firewall-protected Q47: You have been assigned to provide security Q48: Consider the following image of a packet![]()
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents