Deck 3: Operating Systems
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/48
Play
Full screen (f)
Deck 3: Operating Systems
1
Which of the following identifies the application to which a message arriving from the Internet should be given?
A) Protocol
B) Port number
C) Domain
D) Hop count
A) Protocol
B) Port number
C) Domain
D) Hop count
B
2
The primary purpose of which of the following is not the enhancement of security?
A) ICANN
B) Firewall
C) Encryption
D) CERT
A) ICANN
B) Firewall
C) Encryption
D) CERT
A
3
Which layer of the TCP/IP hierarchy presents incoming messages to the computer user?
A) Application
B) Transport
C) Network
D) Link
A) Application
B) Transport
C) Network
D) Link
A
4
Which layer of the TCP/IP hierarchy is responsible for obtaining the correct address for a message's destination?
A) Application
B) Transport
C) Network
D) Link
A) Application
B) Transport
C) Network
D) Link

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
5
Which layer of the TCP/IP hierarchy reassembles messages as their pieces arrive at the destination?
A) Application
B) Transport
C) Network
D) Link
A) Application
B) Transport
C) Network
D) Link

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
6
Which layer of the TCP/IP hierarchy decides the direction in which message segments are transferred across the Internet?
A) Application
B) Transport
C) Network
D) Link
A) Application
B) Transport
C) Network
D) Link

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
7
Ethernet is a means of implementing which of the following network topologies?
A) Star
B) WiFi
C) Bus
A) Star
B) WiFi
C) Bus

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
8
Which of the following is not a way of classifying networks?
A) WAN versus LAN
B) Closed versus open
C) Router versus bridge
D) Star versus bus
A) WAN versus LAN
B) Closed versus open
C) Router versus bridge
D) Star versus bus

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
9
Which of the following connects existing networks to form an internet?
A) Bridge
B) Router
C) Switch
D) Repeater
A) Bridge
B) Router
C) Switch
D) Repeater

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following is assigned the task of providing individual users access to the Internet?
A) Tier-1 ISPs
B) Tier-2 ISPs
C) Access ISPs
D) ICANN
A) Tier-1 ISPs
B) Tier-2 ISPs
C) Access ISPs
D) ICANN

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
11
Which of the following is not a means of connecting networks?
A) Switch
B) Server
C) Router
D) Bridge
A) Switch
B) Server
C) Router
D) Bridge

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
12
Which layer of the TCP/IP hierarchy chops messages into units whose size is compatible with the Internet?
A) Application
B) Transport
C) Network
D) Link
A) Application
B) Transport
C) Network
D) Link

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
13
Which of the following is used to translate between IP addresses and mnemonic addresses?
A) File server
B) Mail server
C) Name server
D) FTP server
A) File server
B) Mail server
C) Name server
D) FTP server

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
14
Which of the following is an Internet application that is named after its underlying protocol?
A) Email
B) World Wide Web
C) FTP
D) UDP
A) Email
B) World Wide Web
C) FTP
D) UDP

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
15
Which layer of the TCP/IP hierarchy decides which application should receive an incoming message?
A) Application
B) Transport
C) Network
D) Link
A) Application
B) Transport
C) Network
D) Link

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
16
Which of the following is not an application of the Internet?
A) FTP
B) Email
C) Telnet
D) CERT
A) FTP
B) Email
C) Telnet
D) CERT

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
17
Which of the following is a protocol for controlling the right to transmit a message in a network?
A) UDP
B) CSMA/CD
C) TCP
D) FTP
A) UDP
B) CSMA/CD
C) TCP
D) FTP

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
18
Which of the following is not a means of performing interprocess communication over a network?
A) Client/server
B) ICANN
C) Peer-to-peer
A) Client/server
B) ICANN
C) Peer-to-peer

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
19
Which standards organization produced the OSI reference model for internet communication?
A) ANSI
B) IEEE
C) ISO
A) ANSI
B) IEEE
C) ISO

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
20
Which layer of the TCP/IP hierarchy actually transmits a message?
A) Application
B) Transport
C) Network
D) Link
A) Application
B) Transport
C) Network
D) Link

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
21
Write the entire URL required to retrieve the Web document named bulldogs.html from the Web server at animals.org assuming that the document is stored in the directory named dogs.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
22
What is the difference between hubs, switches, and routers?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
23
Identify two types of VoIP devices.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
24
What are some distinctions between UDP and TCP?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
25
What are HTML and XML?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
26
Draw a circle the portion of the URL below that identifies the directory containing the file being addressed. Underline the portion that identifies the protocol that should be used when accessing the file. Draw a rectangle around the portion that identifies the file name itself.
http://batcave.metropolis.com/heroes/superheroes/batpage.html
http://batcave.metropolis.com/heroes/superheroes/batpage.html

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
27
The client/server model refers to a form of interprocess communication in which one process, known as the ________________ , runs continuously so that it can be contacted by other processes, known as ________________ , as needed. In contrast is the ____________________ model of interprocess communication in which two processes communicate as equals.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
28
Draw a rectangle around the portion of the email address below that identifies the "person" who should receive the message. Underline the portion that identifies the location of the mail server that handles the mail for that person.
Fido@dogmail.zoo.org
Fido@dogmail.zoo.org

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
29
As an encryption system, what is unique about public-key encryption (that is, why is public-key encryption so named)?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
30
Which generation of wireless network technology uses the packet-switched IP network?
A) 3G
B) 4G
C) 5G
D) All of the above
A) 3G
B) 4G
C) 5G
D) All of the above

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
31
What terms in the following HTML document are linked to other documents? 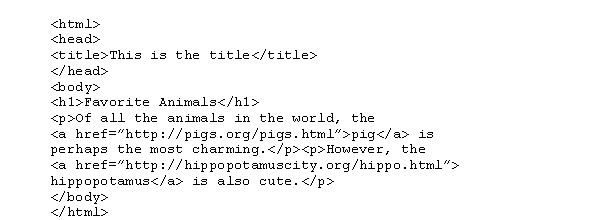


Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
32
Fill in the blanks with the missing tags to the following HTML document. 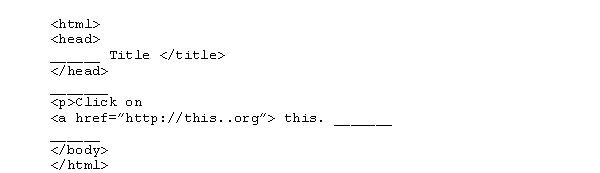


Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
33
Identify a protocol used in the implementation of the network layer in the TCP/IP hierarchy.
______________
______________

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
34
A ___________________ consists of software units that execute as processes on different computers.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
35
What is the difference between a repeater and a bridge?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
36
Many people use the terms Internet and world-wide web interchangeably. What is the difference between the Internet and the world-wide web?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
37
Which of the following is not a means of implementing server-side activities?
A) CGI
B) JSP
C) ASP
D) Applets
A) CGI
B) JSP
C) ASP
D) Applets

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
38
Underline the portion of the URL below that identifies the classification (top-level domain) of the registered domain in which the pertinent Web server resides. Draw a rectangle around the portion that indicates the directory path the server should follow to find the designated document.
http://batcave.metropolis.com/heroes/superheroes/batpage.html
http://batcave.metropolis.com/heroes/superheroes/batpage.html

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following is not a protocol used in the basic TCP/IP software hierarchy?
A) POP3
B) UDP
C) TCP
D) IP
A) POP3
B) UDP
C) TCP
D) IP

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
40
Identify two protocols used in networks to determine the right to transmit an original message.
A) _________________
B) _________________
A) _________________
B) _________________

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
41
What assumptions are made when a URL is denoted by merely zoo.org?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
42
What would happen if a user clicked the mouse on the term "pig" while viewing the HTML document shown below? 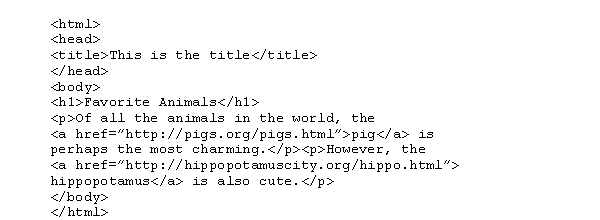


Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
43
To what do the terms "server side" and "client side" refer?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
44
Briefly summarize the steps performed by each of the four layers in the TCP/IP hierarchy at the computer at which a message originates.

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
45
Draw a sketch showing how the following HTML document would appear on the computer screen when displayed by a browser. 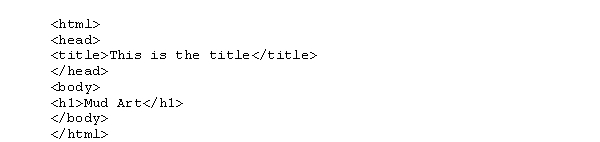


Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
46
Briefly summarize what is meant by the term "cloud computing."

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
47
What is the primary difference between using Telnet and SSH to connect to a remote server?

Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck
48
Draw a sketch showing how the following HTML document would appear on the computer screen when displayed by a browser. 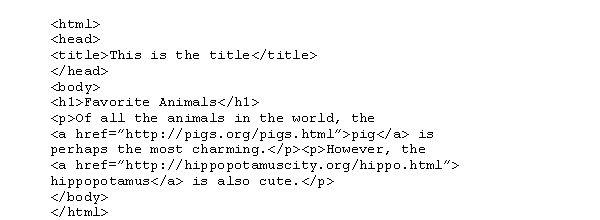


Unlock Deck
Unlock for access to all 48 flashcards in this deck.
Unlock Deck
k this deck



