Deck 9: Data Design
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/112
Play
Full screen (f)
Deck 9: Data Design
1
In a file-oriented information system, a security file ____.
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task
B
2
A data ____, which is a framework for organizing and storing data, consists of one or more files or tables.
A) structure
B) roster
C) index
D) integral
A) structure
B) roster
C) index
D) integral
A
3
A(n) ____ is a collection of tools, features, and interfaces that enables users to add, update, manage, access, and analyze the contents of a database.
A) RMS
B) DBMS
C) scale set
D) HCI
A) RMS
B) DBMS
C) scale set
D) HCI
B
4
A(n) ____, which is used to access stored data, allows a user to specify a task without specifying how the task will be accomplished.
A) machine language
B) assembly language
C) query language
D) markup language
A) machine language
B) assembly language
C) query language
D) markup language

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
5
HTML uses formatting codes called ____, which specify how the text and visual elements on a Web page will be displayed in a Web browser.
A) entities
B) schema
C) tags
D) blocks
A) entities
B) schema
C) tags
D) blocks

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
6
A data ____ language controls database operations, including storing, retrieving, updating, and deleting data.
A) manipulation
B) manufacturing
C) schema
D) dynamic
A) manipulation
B) manufacturing
C) schema
D) dynamic

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
7
In a file-oriented information system, a master file ____.
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
8
In a file-oriented information system, a work file ____.
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
9
JDBC enables ____ applications to exchange data with any database that uses SQL statements and is compliant with the standard.
A) HTML
B) Web
C) Perl
D) Java
A) HTML
B) Web
C) Perl
D) Java

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
10
The complete definition of a database, including descriptions of all fields, tables, and relationships, is called a(n) ____.
A) connective
B) schema
C) exchange
D) collective
A) connective
B) schema
C) exchange
D) collective

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
11
Many database programs generate ____, which is a language that allows PC client workstations to communicate with servers and mainframe computers.
A) DDE
B) DBL
C) DML
D) SQL
A) DDE
B) DBL
C) DML
D) SQL

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
12
In a typical file processing environment, ____ problems can occur if updates are not applied in every file.
A) rigid data structure
B) data integrity
C) referential integrity
D) data redundancy
A) rigid data structure
B) data integrity
C) referential integrity
D) data redundancy

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
13
In a file-oriented information system, a transaction file ____.
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task
A) stores relatively permanent data about an entity
B) is created and saved for backup and recovery purposes
C) stores records that contain day-to-day business and operational data
D) is a temporary file created by an information system for a single task

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
14
One problem in a file processing environment is ____, which means that data common to two or more information systems is stored in several places.
A) rigid data structure
B) data integrity
C) referential integrity
D) data redundancy
A) rigid data structure
B) data integrity
C) referential integrity
D) data redundancy

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
15
____ means that a system can be expanded, modified, or downsized easily to meet the rapidly changing needs of a business enterprise.
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
16
During the systems design phase, ____ fields are used to organize, access, and maintain data structures.
A) glossary
B) tabular
C) content
D) key
A) glossary
B) tabular
C) content
D) key

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
17
With a(n) ____ language, the user provides an example of the data requested.
A) SQL
B) IDE
C) QBE
D) interpolated
A) SQL
B) IDE
C) QBE
D) interpolated

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
18
To bridge the gap between a database and the Web and enable data to be viewed and updated, it is necessary to use ____, which is software that integrates different applications and allows them to exchange data.
A) middleware
B) hardware
C) shareware
D) freeware
A) middleware
B) hardware
C) shareware
D) freeware

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
19
A ____ is a text document written in HTML.
A) Web browser
B) Web page
C) Web server
D) Web site
A) Web browser
B) Web page
C) Web server
D) Web site

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
20
____ is an industry-standard protocol that makes it possible for software from different vendors to interact and exchange data
A) JDBC
B) JVC
C) ODBC
D) OEC
A) JDBC
B) JVC
C) ODBC
D) OEC

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
21
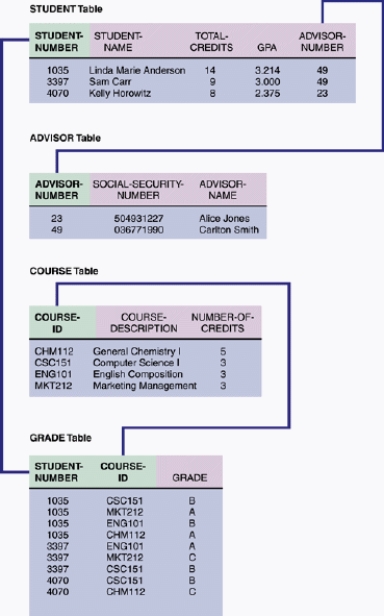
In the accompanying figure, a ____ is a field or combination of fields that uniquely and minimally identifies a particular member of an entity.
A) primary key
B) common key
C) secondary key
D) combination key

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
22
A(n) ____ is a graphical model of an information system that depicts the relationships among system entities.
A) SQL
B) OCE
C) ODBC
D) ERD
A) SQL
B) OCE
C) ODBC
D) ERD

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
23
One type of validity check, called ____ integrity, is a set of rules that avoids data inconsistency and quality problems.
A) candidate
B) combinatorial
C) referential
D) foreign
A) candidate
B) combinatorial
C) referential
D) foreign

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
24
Some abbreviation codes are called ____ codes because they use a specific combination of letters that are easy to remember.
A) harmonic
B) sequence
C) mnemonic
D) rhapsodic
A) harmonic
B) sequence
C) mnemonic
D) rhapsodic

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
25

In the accompanying figure, any field that could serve as a primary key is called a ____.
A) secondary key
B) candidate key
C) combination key
D) foreign key

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
26
____ is the process of creating table designs by assigning specific fields or attributes to each table in a database.
A) Encapsulation
B) Normalization
C) Standardization
D) Encryption
A) Encapsulation
B) Normalization
C) Standardization
D) Encryption

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
27
____ describes how instances of one entity relate to instances of another entity.
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality
A) Scalability
B) Compatibility
C) Cardinality
D) Functionality

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
28
Any field that is not a primary key or a candidate key is called a ____ key.
A) combination
B) nonkey
C) secondary
D) foreign
A) combination
B) nonkey
C) secondary
D) foreign

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
29
Most date formats now are based on the model established by the International Organization for Standardization (ISO), which requires a format of ____.
A) two digits for the year, two for the month, and two for the day (YYMMDD)
B) two digits for the year, four for the month, and two for the day (YYMMMMDD)
C) four digits for the year, two for the month, and two for the day (YYYYMMDD)
D) four digits for the year, two for the month, and four for the day (YYYYMMDDDD)
A) two digits for the year, two for the month, and two for the day (YYMMDD)
B) two digits for the year, four for the month, and two for the day (YYMMMMDD)
C) four digits for the year, two for the month, and two for the day (YYYYMMDD)
D) four digits for the year, two for the month, and four for the day (YYYYMMDDDD)

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
30
When a system reads a physical record, it loads the data from storage into a ____, which is a segment of computer memory.
A) client
B) table
C) password
D) buffer
A) client
B) table
C) password
D) buffer

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
31
____ codes use a keyword to encode a number.
A) Cipher
B) Identifier
C) Encryption
D) Associative
A) Cipher
B) Identifier
C) Encryption
D) Associative

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
32
A(n) ____ is a set of letters or numbers that represents a data item.
A) syntax
B) data dictionary
C) mnemonic
D) code
A) syntax
B) data dictionary
C) mnemonic
D) code

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
33

In the accompanying figure, a ____ is a field in one table that must match a primary key value in another table in order to establish the relationship between the two tables.
A) secondary key
B) candidate key
C) combination key
D) foreign key

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
34
____ codes are numbers or letters assigned in a specific order.
A) Sequence
B) Category
C) Significant digit
D) Derivation
A) Sequence
B) Category
C) Significant digit
D) Derivation

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
35
____ is the process of converting readable data into unreadable characters to prevent unauthorized access to the data.
A) Encapsulation
B) Normalization
C) Standardization
D) Encryption
A) Encapsulation
B) Normalization
C) Standardization
D) Encryption

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
36
In an entity-relationship diagram, entities are represented as ____.
A) triangles
B) circles
C) rectangles
D) hexagons
A) triangles
B) circles
C) rectangles
D) hexagons

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
37
When a primary key combines two or more fields, it is called any of the following EXCEPT a ____ key.
A) constructed
B) composite
C) combination
D) concatenated
A) constructed
B) composite
C) combination
D) concatenated

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
38
In the event of a file catastrophe, ____ can be used to restore the file or database to its current state at the time of the last backup.
A) recovery procedures
B) crow's foot notation
C) audit log files
D) standard notation format
A) recovery procedures
B) crow's foot notation
C) audit log files
D) standard notation format

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
39
____ codes combine data from different item attributes, or characteristics, to build the code.
A) Sequence
B) Category
C) Significant digit
D) Derivation
A) Sequence
B) Category
C) Significant digit
D) Derivation

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
40
One common method of indicating ____ is called crow's foot notation because of the shapes, which include circles, bars, and symbols that indicate various possibilities.
A) scalability
B) compatibility
C) cardinality
D) functionality
A) scalability
B) compatibility
C) cardinality
D) functionality

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
41
A ____ contains data about people, places, things, or events that interact with a system.
A) record
B) column
C) table
D) file
A) record
B) column
C) table
D) file

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
42
In a file-oriented information system, a table file is a file created for historical or archiving purposes.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
43
Which of the following is a problem found with 1NF (first normal form) design that does not exist in 2NF (second normal form)?
A) adding a new record creates difficulties
B) 1NF tables always contain consistent data
C) deleting a record creates difficulties
D) changing a particular entity's description is cumbersome and expensive
A) adding a new record creates difficulties
B) 1NF tables always contain consistent data
C) deleting a record creates difficulties
D) changing a particular entity's description is cumbersome and expensive

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
44
In a file-oriented information system, a history file contains reference data used by the information system.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
45
A table design that does not contain repeating groups is called unnormalized. _________________________

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
46
In a Web-based database design, the Internet serves as the ____ for the database management system.
A) front end
B) back end
C) middleware
D) interface
A) front end
B) back end
C) middleware
D) interface

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
47
In a client/server design, tasks are divided between servers, which are workstations that users interact with, and clients, which are computers that supply data, processing, and services to the server workstations.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
48
An intranet is an extension of a company Web site that allows access by external users, such as customers and suppliers. _________________________

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
49
Like a primary key, a foreign key must be unique.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
50
A database system stores and manages data in separate files using a method called file processing.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
51
Web pages are stored on a Web server, which is a computer that receives requests and makes Web pages available to users.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
52
In a DBMS, the file-oriented tables form a unified data structure. _________________________

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
53
In a table or file, each column represents a record, which is an individual instance, or occurrence of an entity, and each row represents a field, or characteristic of the entity.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following is a data coding and storage scheme?
A) EBCDIC
B) binary
C) ASCII
D) primary
A) EBCDIC
B) binary
C) ASCII
D) primary

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
55
Which of the following is the advantage of a DBMS (database management system)?
A) economy of scale
B) flexible data sharing
C) increased programmer productivity
D) data dependence
A) economy of scale
B) flexible data sharing
C) increased programmer productivity
D) data dependence

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
56
Intranets and extranets are called Web-centric because they use different protocols, or data transmission standards, than the Internet.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
57
A common field is an attribute that appears in only one entity.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
58
The three normal forms constitute a progression in which the first normal form represents the best design. _________________________

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
59
In a client/server system, processing is isolated in one part of the organization.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
60
One problem in a typical file-processing environment is the rigid data structure. _________________________

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
61
The ____________________ for database design, which was introduced in the 1970s and became popular because it was flexible and powerful, uses common fields to establish relationships between tables.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
62
In an M:N relationship, the two entities are linked by an event or transaction called an associative entity, which has its own set of attributes and characteristics.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
63
Normal forms beyond 3NF exist, but they rarely are used in business-oriented systems.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
64
A table design is in third normal form (3NF) if it is in 2NF and if all nonkey fields are dependent on other nonkey fields.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
65
A repeating group is a set of one or more fields that can occur only once in a single record, with each occurrence having the same value.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
66
A popular rule of thumb is that a design is in 3NF if every nonkey field depends on the key, the whole key, and nothing but the key.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
67
A table is in first normal form (1NF) if it contains a repeating group.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
68
Relational databases can run on many platforms, including personal computers.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
69
A data warehouse allows users to specify certain dimensions, or characteristics.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
70
The basic elements of logical data are alphabetic or numeric characters, such as the letter A or the number 9.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
71
To protect stored data, users can be asked to furnish a proper user ID and password to access a file or database.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
72
The inherent efficiency of high-volume processing on larger computers is called ____________________.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
73
Relational databases are poorly suited to client/server computing because they are so powerless and rigid.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
74
Field X is functionally dependent on field Y if the value of field X depends on the value of field Y.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
75
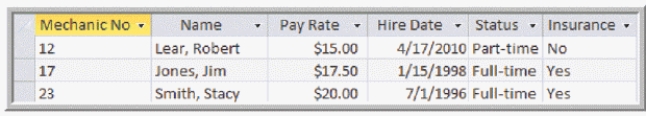
A(n) ____________________, such as that shown in the accompanying figure, contains a set of related records that store data about a specific entity.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
76
Typically, a DBMS is managed by a person called a(n) ____________________, who assesses overall requirements and maintains the database for the benefit of an entire organization rather than a single department or user.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
77
Three main types of relationships that can exist between entities are a one-to-one relationship, abbreviated 1:1; a one-to-many relationship, abbreviated 1:M; and a many-to-many relationship, abbreviated M:N.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
78
To access information on the Internet, a person uses a(n) ____________________, which is an application that enables the user to navigate, or browse, the Internet and display Web pages on his or her local computer.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
79
A table design specifies the fields and identifies the primary key in a particular table or file.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck
80
A table design is in second normal form (2NF) if it is in 1NF and if all fields that are not part of the primary key are functionally independent of part of the primary key.

Unlock Deck
Unlock for access to all 112 flashcards in this deck.
Unlock Deck
k this deck



