Deck 1: Background
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/49
Play
Full screen (f)
Deck 1: Background
1
A monitor is an output device. ____________________
True
2
A kilobyte is 1000 bytes.
True
3
In the 1950s Apple sold its first business computer.
False
4
Bit is another term for binary digit.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
5
Image sampling devices measure values at points called pixels on a two-dimensional grid. ____________________

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
6
A transistor is a simple device that can be in one of two states: on or off.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
7
Binary information is suitable to transmit over phone lines.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
8
Which of the following is NOT true about ENIAC?
A) It used more electricity than all the houses on an average city block.
B) It was built in the late 1950s.
C) It contained hundreds of miles of wire.
D) The meantime between failures was less than 1 hour.
A) It used more electricity than all the houses on an average city block.
B) It was built in the late 1950s.
C) It contained hundreds of miles of wire.
D) The meantime between failures was less than 1 hour.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
9
In the ____, local area networks of interconnected PCs became popular.
A) 1960s
B) 1970s
C) 1980s
D) 1990s
A) 1960s
B) 1970s
C) 1980s
D) 1990s

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
10
The first computers used methods such as punch cards and paper tape for ____.
A) input
B) output
C) programming
D) both a and b
A) input
B) output
C) programming
D) both a and b

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
11
Small text files are usually measured in gigabytes. ____________________

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
12
A compiler is an example of application software.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
13
In the ____, people began to see the advantage of connecting computers in networks.
A) 1950s
B) 1960s
C) 1970s
D) 1980s
A) 1950s
B) 1960s
C) 1970s
D) 1980s

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
14
The first IBM computer had 1/2000 the computational power of a typical 2-gigahertz laptop purchased for $1000 in 2010.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
15
Java uses the ASCII scheme, in which each character is represented by a pattern of 16 bits. ____________________

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
16
Most of the costs of developing software occur at the design phase.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
17
Second generation programming languages are called machine languages.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
18
In the twenty-first century, computing has become ubiquitous, meaning that it is ____.
A) anywhere and everywhere
B) getting smaller
C) wireless
D) less expensive
A) anywhere and everywhere
B) getting smaller
C) wireless
D) less expensive

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
19
File server disk sizes are usually measured in terabytes. ____________________

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
20
Program instructions are represented as a sequence of bits in ROM.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
21
FIGURE 1-1 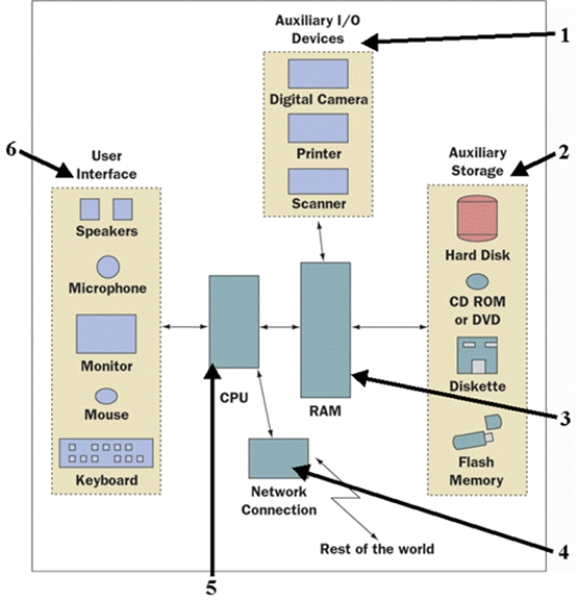
In Figure 1-1 above, which number subsystem is the high-speed internal memory?
A) 1
B) 2
C) 3
D) 4

In Figure 1-1 above, which number subsystem is the high-speed internal memory?
A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
22
Which of the following is NOT true about the information contained in sound?
A) It has a finite range of discrete values.
B) Sound information is analog.
C) Sampling reads the values on a waveform at intervals.
D) The number of cycles per second of a sound's waveform measures its pitch.
A) It has a finite range of discrete values.
B) Sound information is analog.
C) Sampling reads the values on a waveform at intervals.
D) The number of cycles per second of a sound's waveform measures its pitch.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
23
Roberto uses rules of behavior called ____.
A) instance variables
B) methods
C) classes
D) codes
A) instance variables
B) methods
C) classes
D) codes

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
24
FIGURE 1-1 
In Figure 1-1 above, which number subsystem is used for long-term storage of data and programs?
A) 1
B) 2
C) 3
D) 4

In Figure 1-1 above, which number subsystem is used for long-term storage of data and programs?
A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
25
Roberto uses the principle of ____, which provides access to services but not to data resources.
A) instance variables
B) primary memory
C) ubiquitous computing
D) information hiding
A) instance variables
B) primary memory
C) ubiquitous computing
D) information hiding

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
26
The code Margaret writes is translated into machine language using a(n) ____.
A) translator
B) I/O device
C) compiler
D) waterfall model
A) translator
B) I/O device
C) compiler
D) waterfall model

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
27
The physical devices you see on your desktop are called ____.
A) software
B) hardware
C) peripherals
D) PDAs
A) software
B) hardware
C) peripherals
D) PDAs

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
28
A(n) ____ is a convenient portable storage device with a capacity of several gigabytes.
A) PDA
B) CD
C) external hard disk
D) flash memory stick
A) PDA
B) CD
C) external hard disk
D) flash memory stick

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
29
The programs that allow your computer to function are called ____.
A) software
B) hardware
C) peripherals
D) PDAs
A) software
B) hardware
C) peripherals
D) PDAs

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
30
Margaret programs using ____ languages.
A) procedural
B) assembly
C) high-level
D) machine
A) procedural
B) assembly
C) high-level
D) machine

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
31
Numbers with a fractional part are called ____ numbers.
A) mantissa
B) floating-point
C) integer
D) string
A) mantissa
B) floating-point
C) integer
D) string

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
32
Which of the following is NOT true about first generation programming languages?
A) They only used binary digits.
B) An assembler was used to translate the program into machine language.
C) It was nearly impossible for one person to decipher another's program.
D) Each type of computer had its own unique machine language.
A) They only used binary digits.
B) An assembler was used to translate the program into machine language.
C) It was nearly impossible for one person to decipher another's program.
D) Each type of computer had its own unique machine language.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
33
Which of the following is an example of system software?
A) Multimedia software
B) Database
C) Operating systems
D) Spreadsheets
A) Multimedia software
B) Database
C) Operating systems
D) Spreadsheets

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
34
The process in which a class defines the methods and instance variables of its subclasses is called ____.
A) genetics
B) information hiding
C) inheritance
D) encapsulation
A) genetics
B) information hiding
C) inheritance
D) encapsulation

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
35
Each person using a 1960s era time-sharing machine sat at a(n) ____________________.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
36
The ____ subsystem supports communication between a user and the computer?
A) user interface
B) auxiliary input/output
C) network connection
D) RAM
A) user interface
B) auxiliary input/output
C) network connection
D) RAM

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
37
____ was one of the world's first digital electronic computers.
A) ENIAC
B) SDLC
C) RAM
D) FORTRAN
A) ENIAC
B) SDLC
C) RAM
D) FORTRAN

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
38
In the ____ scheme, each character is represented as a pattern of 8 bits.
A) floating-point
B) mantissa
C) waveform
D) ASCII
A) floating-point
B) mantissa
C) waveform
D) ASCII

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
39
Which of the following is NOT true about RAM?
A) It is also called primary memory.
B) It is slower than auxiliary storage devices.
C) The contents of RAM are lost when the computer turns off.
D) The cheapest way to improve computer performance is to install more RAM.
A) It is also called primary memory.
B) It is slower than auxiliary storage devices.
C) The contents of RAM are lost when the computer turns off.
D) The cheapest way to improve computer performance is to install more RAM.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
40
____ programming breaks code into easily handled components.
A) Object-oriented
B) Machine language
C) Assembly language
D) Procedural
A) Object-oriented
B) Machine language
C) Assembly language
D) Procedural

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
41
Identify the letter of the choice that best matches the phrase or definition.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Third generation programming languages that are easy to write, read, and understand.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Third generation programming languages that are easy to write, read, and understand.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
42
Identify the letter of the choice that best matches the phrase or definition.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Used in older languages such as COBOL and FORTRAN.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Used in older languages such as COBOL and FORTRAN.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
43
Identify the letter of the choice that best matches the phrase or definition.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Second generation programming languages, which used mnemonic symbols.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Second generation programming languages, which used mnemonic symbols.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
44
Identify the letter of the choice that best matches the phrase or definition.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Breaks code into easily handled components.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
Breaks code into easily handled components.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
45
The ____________________ system uses base 8.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
46
Identify the letter of the choice that best matches the phrase or definition.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
First generation programming languages, which used only 0s and 1s.
a.Object-oriented approach
b.Procedural approach
c.Machine language
d.Assembly language
e.High-level language
First generation programming languages, which used only 0s and 1s.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
47
____________________ is the common programming language of many of today's devices, including music players and PDAs.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
48
Whose law states that every two years the speed of computers doubles? ____________________

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck
49
A(n) ____________________ is a device that converts the digital computer information into a format for transmitting over phone lines, and vice versa.

Unlock Deck
Unlock for access to all 49 flashcards in this deck.
Unlock Deck
k this deck



