Deck 11: Computer Security and Safety, Ethics, and Privacy
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/181
Play
Full screen (f)
Deck 11: Computer Security and Safety, Ethics, and Privacy
1
Which of the following is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network?
A) Rebuking
B) Spoofing
C) Transmitting
D) Victimizing
A) Rebuking
B) Spoofing
C) Transmitting
D) Victimizing
B
2
Which of the following is someone who uses the Internet or network to destroy or damage computers for political reasons?
A) hacker
B) script kiddie
C) cyberextortionist
D) cyberterrorist
A) hacker
B) script kiddie
C) cyberextortionist
D) cyberterrorist
D
3
 Many Web sites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
Many Web sites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?A) PIN
B) password
C) secure key
D) passterm
B
4
Which of the following is the term for any unwanted signal, usually varying quickly, that is mixed with the normal voltage entering a computer?
A) Undervoltage
B) Noise
C) Overvoltage
D) A spike
A) Undervoltage
B) Noise
C) Overvoltage
D) A spike

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
5
Which of the following occurs when the incoming electrical power increases significantly above the normal 120 volts?
A) overvoltage
B) undervoltage
C) spike
D) unstable flow
A) overvoltage
B) undervoltage
C) spike
D) unstable flow

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
6
To read encrypted data, the recipient must decipher it into a readable form. What is the term for this process?
A) re-securing
B) decryption
C) assessment
D) digitization
A) re-securing
B) decryption
C) assessment
D) digitization

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
7
Which of the following software automatically analyzes all network traffic, assesses system vulnerabilities, identifies any unauthorized access (intrusions), and notifies a network administrator of suspicious behavior patterns or system breaches?
A) Violation assessment
B) Password authentication
C) Intrusion detection
D) Traffic management
A) Violation assessment
B) Password authentication
C) Intrusion detection
D) Traffic management

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
8
What is the term for the prolonged malfunction of a computer?
A) dynamic collapse
B) online hash
C) processor spike
D) system failure
A) dynamic collapse
B) online hash
C) processor spike
D) system failure

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
9
Which of the following kinds of certificate is a notice that guarantees a user or Web site is legitimate?
A) assigned
B) secure
C) protected
D) digital
A) assigned
B) secure
C) protected
D) digital

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following occurs when the electrical supply drops?
A) overvoltage
B) undervoltage
C) spike
D) unstable flow
A) overvoltage
B) undervoltage
C) spike
D) unstable flow

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
11
Which of the following is an authorized person or company that issues and verifies digital certificates?
A) certificate authority
B) certificate agency
C) certificate office
D) certificate bureau
A) certificate authority
B) certificate agency
C) certificate office
D) certificate bureau

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
12
Which of the following is a device that contains surge protection circuits and one or more batteries that can provide power during a temporary or permanent loss of power?
A) PGP
B) DoS
C) UPS
D) DDos
A) PGP
B) DoS
C) UPS
D) DDos

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
13
A particularly devastating type of DoS attack is which kind of DoS attack, in which multiple unsuspecting computers are used to attack multiple computer networks?
A) distributed
B) delayed
C) limited
D) staggered
A) distributed
B) delayed
C) limited
D) staggered

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
14
Which of the following is the unit of energy a surge protection device can absorb before it can be damaged?
A) Joule
B) spike
C) hash
D) macro
A) Joule
B) spike
C) hash
D) macro

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
15
Which of the following has the same intent as a cracker, but does not have the technical skills and knowledge?
A) hacker
B) script kiddie
C) cyberextortionist
D) cyberterrorist
A) hacker
B) script kiddie
C) cyberextortionist
D) cyberterrorist

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
16
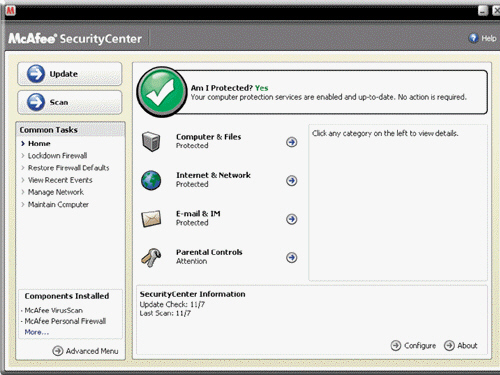 As shown in the accompanying figure, which of the following kinds of program protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media, or on incoming files?
As shown in the accompanying figure, which of the following kinds of program protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media, or on incoming files?A) hoax
B) secure
C) antivirus
D) antispyware

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
17
Computer viruses, worms, Trojan horses, and rootkits are classified as which of the following, or programs that act without a user's knowledge and deliberately alter the computer's operations?
A) malware
B) untrusted sources
C) threats
D) cybermals
A) malware
B) untrusted sources
C) threats
D) cybermals

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
18
Which of the following is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability?
A) computer security risk
B) information liability
C) technical terrorism
D) network compromise
A) computer security risk
B) information liability
C) technical terrorism
D) network compromise

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
19
Which of the following is someone who uses e-mail as a vehicle for extortion?
A) hacker
B) script kiddie
C) cyberextortionist
D) cyberterrorist
A) hacker
B) script kiddie
C) cyberextortionist
D) cyberterrorist

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
20
Which of the following kinds of suppressors uses special electrical components to smooth out minor noise, provide a stable current flow, and keep an overvoltage from reaching a computer and other electronic equipment?
A) Joule
B) spike
C) surge
D) hash
A) Joule
B) spike
C) surge
D) hash

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
21
Which of the following terms means in a location separate from the computer site?
A) Offscope
B) Offshore
C) Offline
D) Offsite
A) Offscope
B) Offshore
C) Offline
D) Offsite

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
22
To do this to a file means to make a copy of it. What is the term in question?
A) restore
B) back up
C) concatenate
D) decipher
A) restore
B) back up
C) concatenate
D) decipher

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
23
Which of the following refers to the right of individuals and companies to deny or restrict the collection and use of information about them?
A) data rights
B) acceptable use
C) social restrictions
D) information privacy
A) data rights
B) acceptable use
C) social restrictions
D) information privacy

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following copies all of the files in a computer?
A) full backup
B) incremental backup
C) differential backup
D) selective backup
A) full backup
B) incremental backup
C) differential backup
D) selective backup

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
25
Web sites use which of the following to keep track of items in a user's shopping cart?
A) session cookie
B) zombie
C) adware
D) shopping bot
A) session cookie
B) zombie
C) adware
D) shopping bot

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
26
Which of the following occurs when a computer consumes someone's entire social life?
A) online craving
B) social consumption
C) computer addiction
D) information railroading
A) online craving
B) social consumption
C) computer addiction
D) information railroading

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
27
Users may have this disorder if they have sore, tired, burning, itching or dry eyes; blurred or double vision; or difficulty focusing on a screen image. What is the name of this disorder?
A) OMS
B) EMV
C) CVS
D) VCS
A) OMS
B) EMV
C) CVS
D) VCS

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
28
In the case of system failure or the discovery of corrupted files, users do this to the files by copying the backed up files to their original location on a computer. What is the term in question?
A) reset
B) index
C) restore
D) resource
A) reset
B) index
C) restore
D) resource

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
29
Which of the following is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed?
A) restored file
B) bot
C) IP file
D) backup
A) restored file
B) bot
C) IP file
D) backup

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
30
Which of the following is a small text file that a Web server stores on a user's computer?
A) worm
B) spike
C) cookie
D) payload
A) worm
B) spike
C) cookie
D) payload

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
31
With a three-generation backup policy, the grandparent is which of the following?
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file
A) most recent copy of the file
B) second oldest copy of the file
C) oldest copy of the file
D) original file

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
32
Which of the following category of rights are the rights to which creators are entitled for their work?
A) Community property
B) Intellectual property
C) Creative
D) Ethical
A) Community property
B) Intellectual property
C) Creative
D) Ethical

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
33
Which of the following gives authors and artists the exclusive rights to duplicate, publish, and sell their materials?
A) intellectual property deed
B) content license
C) access right
D) copyright
A) intellectual property deed
B) content license
C) access right
D) copyright

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
34
Some perpetrators use a technique in which they attempt to connect to wireless networks via their notebook computers while driving a vehicle through areas they suspect have a wireless network. What is the term this technique?
A) cyberforensics
B) war driving
C) war flying
D) wire cruising
A) cyberforensics
B) war driving
C) war flying
D) wire cruising

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
35
Which of the following refers to unique and original works such as ideas, inventions, writings, art, processes, company and product names, and logos?
A) PGP
B) DoS
C) IP
D) TCP
A) PGP
B) DoS
C) IP
D) TCP

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
36
Which of the following is an injury or disorder of the muscles, nerves, tendons, ligaments, and joints?
A) DoS
B) ISP
C) PGP
D) RSI
A) DoS
B) ISP
C) PGP
D) RSI

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
37
Personal computers, display devices, and printers should comply with guidelines of which of the following programs?
A) ENERGY STAR
B) SECURE ELECTRONICS
C) ACCEPTABLE USE
D) GREEN COMPUTING
A) ENERGY STAR
B) SECURE ELECTRONICS
C) ACCEPTABLE USE
D) GREEN COMPUTING

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
38
An IT code of conduct is a written guideline that helps determine whether a specific computer action is which of the following?
A) practical
B) permissible
C) acceptable
D) ethical
A) practical
B) permissible
C) acceptable
D) ethical

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
39
With which of the following do users choose which folders and files to include in a backup?
A) full backup
B) incremental backup
C) differential backup
D) selective backup
A) full backup
B) incremental backup
C) differential backup
D) selective backup

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
40
Which of the following is an applied science devoted to incorporating comfort, efficiency, and safety into the design of items in the workplace?
A) Ergonomics
B) Eurhythmics
C) Epidemics
D) Econometrics
A) Ergonomics
B) Eurhythmics
C) Epidemics
D) Econometrics

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
41
Which of the following 1986 laws provides the same protection that covers mail and telephone communications to electronic communications such as voice mail?
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
42
COGNITIVE ASSESSMENT Which of the following terms refers to someone who accesses a computer or network illegally with the intent of malicious action?
A) script kiddie
B) cracker
C) cyberextortionist
D) cyberterrorist
A) script kiddie
B) cracker
C) cyberextortionist
D) cyberterrorist

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
43
COGNITIVE ASSESSMENT Which of the following terms refers to someone who uses the Internet or network to destroy or damage computers for political reasons?
A) script kiddie
B) cracker
C) cyberextortionist
D) cyberterrorist
A) script kiddie
B) cracker
C) cyberextortionist
D) cyberterrorist

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
44
COGNITIVE ASSESSMENT Which of the following best describes the term, cybercrime?
A) online or Internet-based illegal acts
B) any illegal act involving a computer
C) a type of gaming software that simulates criminal acts
D) using the Internet to apprehend and prosecute criminals
A) online or Internet-based illegal acts
B) any illegal act involving a computer
C) a type of gaming software that simulates criminal acts
D) using the Internet to apprehend and prosecute criminals

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
45
Which of the following involves the use of computers to observe, record, and review an employee's use of a computer, including communications such as e-mail messages, keyboarding activity, and Web sites visited?
A) manager filtering
B) employee monitoring
C) job spamming
D) employee indexing
A) manager filtering
B) employee monitoring
C) job spamming
D) employee indexing

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
46
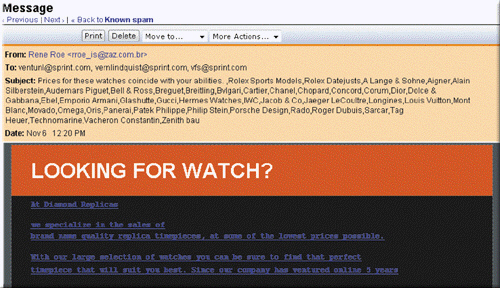 An alternative to e-mail filtering is to purchase which of the following kinds of program that attempts to remove a message, like the one in the accompanying figure, before it reaches a user's inbox?
An alternative to e-mail filtering is to purchase which of the following kinds of program that attempts to remove a message, like the one in the accompanying figure, before it reaches a user's inbox?A) email
B) sieve
C) filtering
D) anti-spam

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
47
Many businesses use which of the following to limit employees' Web access?
A) content filtering
B) Web bugs
C) honeypots
D) spyware
A) content filtering
B) Web bugs
C) honeypots
D) spyware

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
48
COGNITIVE ASSESSMENT Define the term, payload, as it pertains to computer crime.
A) the money a criminal receives from extortion or other computer crimes
B) the amount of data loss to a company or individual who is a victim of a computer crime
C) the destructive event or prank the program is intended to deliver
D) the financial burden computer crime places on its victims
A) the money a criminal receives from extortion or other computer crimes
B) the amount of data loss to a company or individual who is a victim of a computer crime
C) the destructive event or prank the program is intended to deliver
D) the financial burden computer crime places on its victims

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
49
COGNITIVE ASSESSMENT Which of the following terms is used to describe a program that copies itself repeatedly, using up resources and possibly shutting down the computer or network?
A) a virus
B) a worm
C) a Trojan horse
D) a rootkit
A) a virus
B) a worm
C) a Trojan horse
D) a rootkit

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
50
COGNITIVE ASSESSMENT What is the general term for programs that act without a user's knowledge and deliberately alter the computer's operations?
A) malware
B) cybersoft
C) evilapp
D) viralware
A) malware
B) cybersoft
C) evilapp
D) viralware

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
51
Which of the following 1988 laws regulates the use of government data to determine the eligibility of individuals for federal benefits?
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act
A) Electronic Communications Privacy Act (ECPA)
B) Fair Credit Reporting Act
C) Computer Fraud and Abuse Act
D) Computer Matching and Privacy Protection Act

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
52
One type of spyware is hidden on Web pages or in e-mail messages in the form of graphical images. What is the term for this type of spyware?
A) Web bug
B) forensic element
C) content filter
D) integrated bot
A) Web bug
B) forensic element
C) content filter
D) integrated bot

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
53
COGNITIVE ASSESSMENT Which of the following statements is not true about Internet and network attacks?
A) The CERT/CC is a federally funded Internet security research and development center.
B) It is usually the responsibility of the network administrators to take measures to protect a network from security risks.
C) Information kept on an organization's premises has a higher security risk than information transmitted over networks.
D) An online security service is a Web site that evaluates your computer to check for Internet and e-mail vulnerabilities.
A) The CERT/CC is a federally funded Internet security research and development center.
B) It is usually the responsibility of the network administrators to take measures to protect a network from security risks.
C) Information kept on an organization's premises has a higher security risk than information transmitted over networks.
D) An online security service is a Web site that evaluates your computer to check for Internet and e-mail vulnerabilities.

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following is the process of restricting access to certain material on the Web?
A) text remastering
B) content filtering
C) indexing
D) material masking
A) text remastering
B) content filtering
C) indexing
D) material masking

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
55
Internet advertising firms often use which of the following to collect information about users Web browsing habits?
A) comware
B) postware
C) spyware
D) billware
A) comware
B) postware
C) spyware
D) billware

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
56
COGNITIVE ASSESSMENT Which term is used to describe software used by cybercriminals?
A) cyberware
B) conware
C) criminalware
D) crimeware
A) cyberware
B) conware
C) criminalware
D) crimeware

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
57
COGNITIVE ASSESSMENT Which of the following terms is used to describe a program that hides in a computer and allows someone from a remote location to take full control of the computer?
A) a virus
B) a worm
C) a Trojan horse
D) a rootkit
A) a virus
B) a worm
C) a Trojan horse
D) a rootkit

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
58
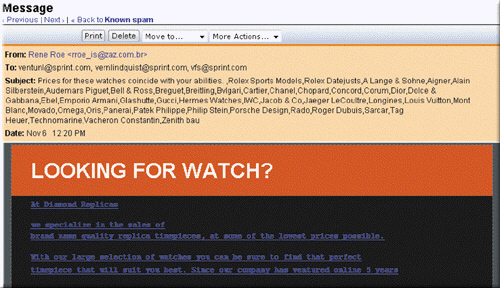 As shown in the accompanying figure, which of the following is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once?
As shown in the accompanying figure, which of the following is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once?A) Hash
B) Spam
C) Worm
D) Spike

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following is a scam in which a perpetrator sends an official looking e-mail that attempts to obtain a user's personal and financial information?
A) Spam
B) Spit
C) Phishing
D) Spyware
A) Spam
B) Spit
C) Phishing
D) Spyware

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
60
COGNITIVE ASSESSMENT Antivirus programs look for a specific pattern of virus code. What is this pattern called?
A) virus map
B) virus signature
C) virus index
D) virus identifier
A) virus map
B) virus signature
C) virus index
D) virus identifier

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
61
COGNITIVE ASSESSMENT The term, PIN, is an acronym for which of the following?
A) personal identification number
B) private Internet notification
C) possessed information number
D) personal information network
A) personal identification number
B) private Internet notification
C) possessed information number
D) personal information network

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
62
COGNITIVE ASSESSMENT What is an EULA intended to do?
A) license software for individual use
B) outline computer activities for which the computer and network may or may not be used
C) contract with an outside organization to provide security and recovery services for a network
D) establish a network of computers, such as a homegroup
A) license software for individual use
B) outline computer activities for which the computer and network may or may not be used
C) contract with an outside organization to provide security and recovery services for a network
D) establish a network of computers, such as a homegroup

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
63
COGNITIVE ASSESSMENT What term is used to describe the discovery, collection, and analysis of evidence found on computers and networks?
A) cybersleuthing
B) digital forensics
C) system analysis
D) data mining
A) cybersleuthing
B) digital forensics
C) system analysis
D) data mining

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
64
COGNITIVE ASSESSMENT What is an AUP intended to do?
A) license software for individual use
B) outline computer activities for which the computer and network may or may not be used
C) contract with an outside organization to provide security and recovery services for a network
D) establish a network of computers, such as a homegroup
A) license software for individual use
B) outline computer activities for which the computer and network may or may not be used
C) contract with an outside organization to provide security and recovery services for a network
D) establish a network of computers, such as a homegroup

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
65
COGNITIVE ASSESSMENT Which of the following refers to a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network?
A) spoofing
B) phishing
C) veiling
D) costuming
A) spoofing
B) phishing
C) veiling
D) costuming

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
66
COGNITIVE ASSESSMENT Define the term CAPTCHA.
A) a private combination of words associated with a user name that allows access to computer resources
B) the average time it takes a computer to discover a password based on the number of characters
C) a digital image used to help decipher a faded or blurry word in digitized news archives
D) a series of distorted characters that a user is required to enter correctly to continue using a Web site
A) a private combination of words associated with a user name that allows access to computer resources
B) the average time it takes a computer to discover a password based on the number of characters
C) a digital image used to help decipher a faded or blurry word in digitized news archives
D) a series of distorted characters that a user is required to enter correctly to continue using a Web site

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
67
COGNITIVE ASSESSMENT What happens during a DDoS attack?
A) An unsuspecting computer is used to sent an influx of confusing data messages or useless network traffic.
B) Antivirus software disables a virus and protects the computer or network from unauthorized access.
C) The police use a virus and other measures to take down a network of computer criminals.
D) A zombie army is used to attack computers or computer networks.
A) An unsuspecting computer is used to sent an influx of confusing data messages or useless network traffic.
B) Antivirus software disables a virus and protects the computer or network from unauthorized access.
C) The police use a virus and other measures to take down a network of computer criminals.
D) A zombie army is used to attack computers or computer networks.

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
68
COGNITIVE ASSESSMENT Which of the following terms is used to describe a file a computer creates that records successful and unsuccessful access attempts?
A) an access control
B) an attempt log
C) an attack index
D) an audit trail
A) an access control
B) an attempt log
C) an attack index
D) an audit trail

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
69
COGNITIVE ASSESSMENT Which of the following term is used to describe a vulnerable computer that is set up to entice an intruder to break into it?
A) a honeypot
B) a magnet
C) a mole
D) flypaper
A) a honeypot
B) a magnet
C) a mole
D) flypaper

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
70
COGNITIVE ASSESSMENT Define the term, botnet.
A) a program that performs a repetitive task on a network
B) spam sent via e-mail to spread viruses or commit a distributed denial of service attack
C) a group of compromised computers connected to a network that attacks other networks
D) a computer whose owner is unaware that the computer is being controlled remotely by an outsider
A) a program that performs a repetitive task on a network
B) spam sent via e-mail to spread viruses or commit a distributed denial of service attack
C) a group of compromised computers connected to a network that attacks other networks
D) a computer whose owner is unaware that the computer is being controlled remotely by an outsider

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
71
COGNITIVE ASSESSMENT Define the term back door, as it refers to computer crime.
A) the area of memory where information about a virus or attempted attack is sent by the antivirus software in order to prevent similar attacks in the future
B) a program or set of instructions that allows users to bypass security controls when accessing a program, computer, or network
C) the vulnerabilities of a computer criminal or criminal network that enable them to be tracked and caught
D) a weakness in a computer or network's security system that enables criminals to gain unauthorized access
A) the area of memory where information about a virus or attempted attack is sent by the antivirus software in order to prevent similar attacks in the future
B) a program or set of instructions that allows users to bypass security controls when accessing a program, computer, or network
C) the vulnerabilities of a computer criminal or criminal network that enable them to be tracked and caught
D) a weakness in a computer or network's security system that enables criminals to gain unauthorized access

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
72
COGNITIVE ASSESSMENT Define the term firewall.
A) the access point a hacker uses to intrude on a computer or network
B) a program that searches for cybercriminals by looking for patterns in attacks
C) hardware and/or software that protect's a network's resources from intrusion
D) a virus that prevents the computer or network from accessing outside resources
A) the access point a hacker uses to intrude on a computer or network
B) a program that searches for cybercriminals by looking for patterns in attacks
C) hardware and/or software that protect's a network's resources from intrusion
D) a virus that prevents the computer or network from accessing outside resources

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
73
COGNITIVE ASSESSMENT Define the term, zombie.
A) a program that performs a repetitive task on a network
B) spam sent via e-mail to spread viruses or commit a distributed denial of service attack
C) a group of compromised computers connected to a network that attacks other networks
D) a computer whose owner is unaware that the computer is being controlled remotely by an outsider
A) a program that performs a repetitive task on a network
B) spam sent via e-mail to spread viruses or commit a distributed denial of service attack
C) a group of compromised computers connected to a network that attacks other networks
D) a computer whose owner is unaware that the computer is being controlled remotely by an outsider

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
74
COGNITIVE ASSESSMENT Which of the following statements is not true about biometric devices?
A) Personal characteristics are unique and cannot be forgotten or misplaced.
B) Biometric devices are an unreliable method of identification and notification.
C) Examples include fingerprint readers and hand geometry systems.
D) Biometric devices translate a personal characteristic into a digital code.
A) Personal characteristics are unique and cannot be forgotten or misplaced.
B) Biometric devices are an unreliable method of identification and notification.
C) Examples include fingerprint readers and hand geometry systems.
D) Biometric devices translate a personal characteristic into a digital code.

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
75
COGNITIVE ASSESSMENT Which of the following statements is not true about protecting yourself against computer viruses?
A) If a trusted source sends you an e-mail with an attachment you are not expecting, it is safe to open it because you know the sender.
B) When you purchase a new computer, it often includes anti-virus software.
C) A trusted source is an organization or person you believe will not send a virus infected file knowingly.
D) Some viruses are hidden in macros, which are instructions saved in software such as a word processing program.
A) If a trusted source sends you an e-mail with an attachment you are not expecting, it is safe to open it because you know the sender.
B) When you purchase a new computer, it often includes anti-virus software.
C) A trusted source is an organization or person you believe will not send a virus infected file knowingly.
D) Some viruses are hidden in macros, which are instructions saved in software such as a word processing program.

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
76
COGNITIVE ASSESSMENT Which of the following terms is used to describe a set of steps that can convert readable plaintext into unreadable ciphertext?
A) a decipher module
B) a translation tool
C) an encryption algorithm
D) a decryption key
A) a decipher module
B) a translation tool
C) an encryption algorithm
D) a decryption key

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
77
COGNITIVE ASSESSMENT Which of the following statements is not true about software theft?
A) A keygen distributes usernames and passwords to those who register their legally purchased copies of a software program.
B) Software piracy is the unauthorized and illegal duplication of copyrighted software.
C) With a single-user license agreement, users are permitted to make one copy of the software as a backup.
D) Software theft includes disabling or removing programs from company computers.
A) A keygen distributes usernames and passwords to those who register their legally purchased copies of a software program.
B) Software piracy is the unauthorized and illegal duplication of copyrighted software.
C) With a single-user license agreement, users are permitted to make one copy of the software as a backup.
D) Software theft includes disabling or removing programs from company computers.

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
78
COGNITIVE ASSESSMENT Which of the following statements is not true about user names and passwords?
A) Passwords typically range from 6 to 16 characters.
B) Most systems require that users select their own passwords.
C) Pass phrases are less secure because they contain words.
D) Hackers often use computer automated tools to assist them with guessing passwords.
A) Passwords typically range from 6 to 16 characters.
B) Most systems require that users select their own passwords.
C) Pass phrases are less secure because they contain words.
D) Hackers often use computer automated tools to assist them with guessing passwords.

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
79
COGNITIVE ASSESSMENT Which of the following statements is not true about hardware theft and vandalism?
A) Hardware theft is the act of stealing computer equipment.
B) The size and weight of notebook computers makes them easy to steal.
C) Home desktop computer users are especially vulnerable to hardware theft and vandalism.
D) Cutting computer cables or smashing computers in a school lab are examples of hardware vandalism.
A) Hardware theft is the act of stealing computer equipment.
B) The size and weight of notebook computers makes them easy to steal.
C) Home desktop computer users are especially vulnerable to hardware theft and vandalism.
D) Cutting computer cables or smashing computers in a school lab are examples of hardware vandalism.

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck
80
COGNITIVE ASSESSMENT What is the purpose of an RTLS?
A) to prevent unauthorized access on a stolen mobile device
B) to lock computers using cables to prevent equipment theft
C) to detect criminal activity on a network
D) to track and identify the location of high-risk or high-value items
A) to prevent unauthorized access on a stolen mobile device
B) to lock computers using cables to prevent equipment theft
C) to detect criminal activity on a network
D) to track and identify the location of high-risk or high-value items

Unlock Deck
Unlock for access to all 181 flashcards in this deck.
Unlock Deck
k this deck



