Deck 6: Protecting Files
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/75
Play
Full screen (f)
Deck 6: Protecting Files
1
The incidence of computer theft is increasing.
True
2
A type of malicious software is snakes.
False
3
One of the most disastrous events that can strike a computer is a head crash.
True
4
Hardware failures that affect your computer circuitry and storage devices can be caused by defective components or by unfortunate events.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
5
Worms are a type of malicious software that can spread from one computer to another.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
6
Computer files can become corrupted when they are not opened properly.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
7
Spyware is another term for malicious software and refers to any computer program designed to surreptitiously enter a computer, gain unauthorized access to data, or disrupt normal processing operations.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
8
You can often set the autosave option to specify where and how frequently data is stored.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
9
The autosave option automatically makes copies of files as you are working on them.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
10
A virus program is a series of unique bytes that uniquely identifies a virus and distinguishes it from legitimate files on your PC.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
11
The best time to make a system repair disc is when you first set up your computer.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
12
Virus software works in the background whenever your computer is on.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
13
Restore software is/are designed to back up and restore files from a computer's primary storage device.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
14
A system image is an exact copy of all the files stored on a drive.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
15
A malicious file is damaged and either won't open, doesn't work properly, or interferes with other software.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
16
File backups ensure(s) that files in two or more locations contain the same data.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
17
The restore process retrieves files from a backup.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
18
A copy of one or more files that is made in case the originals become damaged is generally referred to as a restore.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
19
Files from File History must be accessed and restored in groups.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
20
A system recovery drive boots your computer from an external hard drive or USB flash drive, and helps you reinstall Windows along with the device drivers and utilities needed to get your computer up and running.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
21
If a drive malfunctions or gets knocked about, its read-write ____ might literally crash into the disk surface and damage the sectors that hold your data.
A) head
B) brain
C) arm
D) memory
A) head
B) brain
C) arm
D) memory

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
22
____ utilities are designed to back up and restore files from a computer's primary storage device.
A) Operating system
B) Application
C) Backup
D) Restore
A) Operating system
B) Application
C) Backup
D) Restore

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
23
____ can attach themselves to a legitimate computer file, replicate to other programs, and deliver various payloads.
A) Snakes
B) Viruses
C) Bacteria
D) Worms
A) Snakes
B) Viruses
C) Bacteria
D) Worms

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
24
An exact copy of all the files stored on a drive is a(n) ____.
A) ghost
B) system image
C) image
D) exact image
A) ghost
B) system image
C) image
D) exact image

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
25
Which of the following can damage files to the point where the data they contain is no longer accessible?
A) power jacks
B) fires and floods
C) plugging a computer into a surge protector
D) an uncharged battery
A) power jacks
B) fires and floods
C) plugging a computer into a surge protector
D) an uncharged battery

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
26
If an application hangs up, you can use the ____ to close a non-responding program.
A) Task Manager
B) Help window
C) Project Manager
D) virus software
A) Task Manager
B) Help window
C) Project Manager
D) virus software

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
27
The first time you set up the system recovery drive, choose the ____ option.
A) Create a recovery drive
B) Establish backup
C) Create backup
D) Backup
A) Create a recovery drive
B) Establish backup
C) Create backup
D) Backup

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
28
When your computer's hard drive malfunctions, you will need a(n) ____ to get your computer started and access the tools necessary to start the restore process.
A) system recovery drive
B) system maintenance disc
C) operating system CD
D) restore repair disc
A) system recovery drive
B) system maintenance disc
C) operating system CD
D) restore repair disc

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
29
The option that automatically makes copies of files as you are working on them is ____.
A) Save As
B) Save
C) autosave
D) automatic
A) Save As
B) Save
C) autosave
D) automatic

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
30
A corrupted file is ____ and either won't open, doesn't work properly, or interferes with other software.
A) broken
B) damaged
C) surged
D) crashed
A) broken
B) damaged
C) surged
D) crashed

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
31
A series of unique bytes that identifies a virus and distinguishes it from legitimate files on your PC is called a ____.
A) signature
B) virus signature
C) stamp
D) worm
A) signature
B) virus signature
C) stamp
D) worm

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
32
If you delete a file inadvertently from your hard drive, it resides ____.
A) on the hard disk
B) in the Recycle Bin
C) on USB flash drive
D) on the desktop
A) on the hard disk
B) in the Recycle Bin
C) on USB flash drive
D) on the desktop

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
33
A restore point is a snapshot of your computer settings, essentially a backup of the ____.
A) Windows Registry
B) Windows Image
C) Windows Restore
D) Windows Ghost
A) Windows Registry
B) Windows Image
C) Windows Restore
D) Windows Ghost

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
34
Antivirus software scans virus signatures in e-mail attachments, ____, and files that you access from USB flash drives, CDs, DVDs, or the Web.
A) uploads
B) copies
C) backups
D) downloads
A) uploads
B) copies
C) backups
D) downloads

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
35
To protect your computer from malicious attacks, experts recommend you practice "safe computing" by installing ____ software.
A) operating system
B) antivirus
C) application
D) Web-based
A) operating system
B) antivirus
C) application
D) Web-based

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
36
A(n) ____ backup makes backup copies of files as they are added or changed.
A) auto
B) manual
C) system
D) incremental
A) auto
B) manual
C) system
D) incremental

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
37
Popular antivirus software products are available from all but the following ____.
A) AVAST
B) McAfee
C) Snag It
D) Kaspersky
A) AVAST
B) McAfee
C) Snag It
D) Kaspersky

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following is an example of malicious software that can alter data on your computer?
A) worms
B) snakes
C) Microsoft Word
D) Internet Explorer
A) worms
B) snakes
C) Microsoft Word
D) Internet Explorer

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
39
____ files are usually stored on a different storage medium than the original files.
A) Restored
B) Backup
C) Private
D) Corrupted
A) Restored
B) Backup
C) Private
D) Corrupted

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
40
Another strategy for protecting important files is to ____ copy them to a USB flash drive, external hard disk, CD, or DVD.
A) hard
B) soft
C) manually
D) auto
A) hard
B) soft
C) manually
D) auto

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
41
____ storage services such as Microsoft SkyDrive offer remote storage space on an internet-based server.
A) Sky
B) Data backup
C) Cloud
D) Space usage
A) Sky
B) Data backup
C) Cloud
D) Space usage

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
42
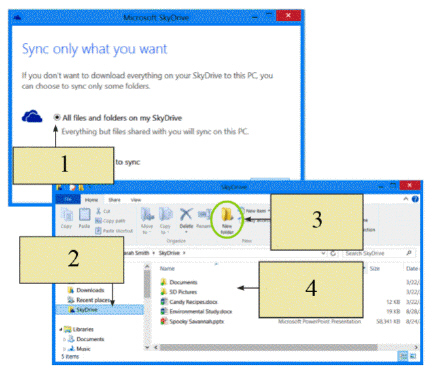 In the figure above, which item sets up SkyDrive and makes sure it is synced with your computer?
In the figure above, which item sets up SkyDrive and makes sure it is synced with your computer?A) Item 1
B) Item 2
C) Item 3
D) Item 4

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
43
A(n) ____ is the best insurance against a total hard disk failure because the image can be streamed onto a new hard disk, which restores your complete computing environment in one operation.
A) virus
B) system image
C) system recovery drive
D) rootkit
A) virus
B) system image
C) system recovery drive
D) rootkit

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
44
Malware is another term for ____ and refers to any computer program designed to surreptitiously enter a computer, gain unauthorized access to data, or disrupt normal processing operations.
A) malicious software
B) virus signatures
C) corrupted files
D) backup utilities
A) malicious software
B) virus signatures
C) corrupted files
D) backup utilities

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
45
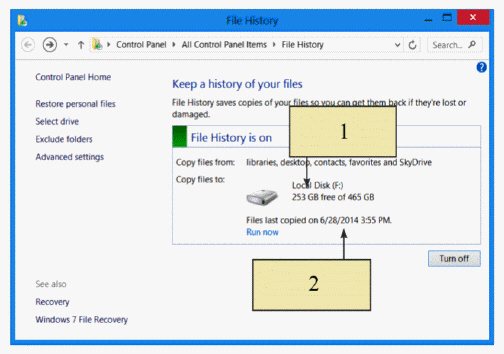 In the figure above, Item 2 points to the date of your most recent ____.
In the figure above, Item 2 points to the date of your most recent ____.A) backup
B) settings change
C) restored files
D) created folder

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
46
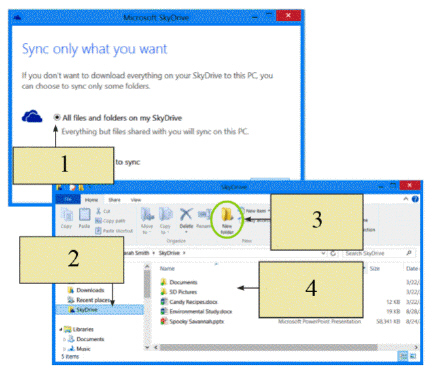 In the figure above, which item displays all the folders and files stored in the cloud?
In the figure above, which item displays all the folders and files stored in the cloud?A) Item 1
B) Item 2
C) Item 3
D) Item 4

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
47
____ are set automatically when you install new software.
A) System Recovery Drive
B) Malware
C) System images
D) Restore points
A) System Recovery Drive
B) Malware
C) System images
D) Restore points

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
48
When you save files to ____, you will have a copy stored locally and in the cloud.
A) SkyDrive
B) SkyHawk
C) AutoRecovery
D) Task Manager
A) SkyDrive
B) SkyHawk
C) AutoRecovery
D) Task Manager

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
49
The system recovery drive provides an option for ____ a system image previously created.
A) scanning
B) booting
C) backing up
D) restoring
A) scanning
B) booting
C) backing up
D) restoring

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
50
Windows is able to restore a single file, folder, or ____ from an incremental backup.
A) private folders
B) library
C) subfolders
D) icons
A) private folders
B) library
C) subfolders
D) icons

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
51
Any software that can automate a task or autonomously execute a task when commanded to do so is called a(n) ____.
A) malware
B) malicious software
C) intelligent agent
D) secret agent
A) malware
B) malicious software
C) intelligent agent
D) secret agent

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
52
The ____ option restores your computer to its like-new status, erasing all your software and data.
A) Refresh your PC
B) Create a recovery drive
C) Reset your PC
D) System recovery
A) Refresh your PC
B) Create a recovery drive
C) Reset your PC
D) System recovery

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
53
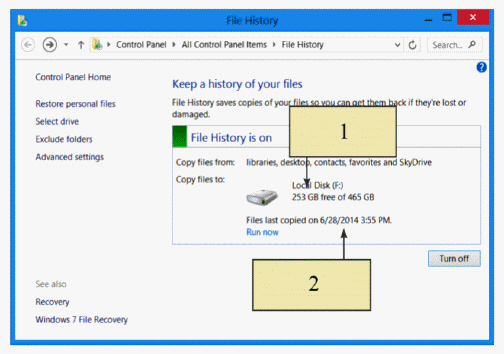 In the figure above, Item 1 points to the ____ on the backup drive.
In the figure above, Item 1 points to the ____ on the backup drive.A) file history
B) file recovery
C) free space
D) used space

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following is NOT a step in a serviceable backup plan?
A) Make a system recovery drive.
B) Make monthly backups.
C) Activate autosave.
D) Make copies of important files.
A) Make a system recovery drive.
B) Make monthly backups.
C) Activate autosave.
D) Make copies of important files.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
55
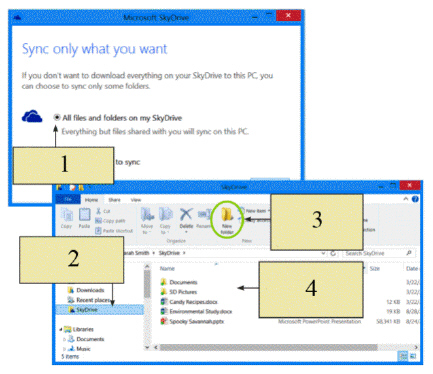 In the figure above, which item is used to create subfolders on SkyDrive to keep your files organized?
In the figure above, which item is used to create subfolders on SkyDrive to keep your files organized?A) Item 1
B) Item 2
C) Item 3
D) Item 4

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
56
The term ____ refers to software tools used to conceal malware and backdoors that have been installed on a victim's computer.
A) computer virus
B) rootkit
C) Trojan horse
D) bot
A) computer virus
B) rootkit
C) Trojan horse
D) bot

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
57
What are considered great defense mechanisms for malware?
A) restore points
B) virus signatures
C) cloaking techniques
D) concealing techniques
A) restore points
B) virus signatures
C) cloaking techniques
D) concealing techniques

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
58
____ is ideal in situations when you want a copy of your most recent work stored in a location that you can access in the event that your main hard drive fails.
A) System Restore
B) Synchronization
C) AutoRecovery
D) System Image Recovery
A) System Restore
B) Synchronization
C) AutoRecovery
D) System Image Recovery

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following can you use to hold backups?
A) external hard disks
B) CD-Rs
C) system repair discs
D) system recovery discs
A) external hard disks
B) CD-Rs
C) system repair discs
D) system recovery discs

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
60
Retrieving files from a backup is referred to as the ____ process.
A) backup
B) system
C) application
D) restore
A) backup
B) system
C) application
D) restore

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
61
When the computer's hard drive ____________________, you need a system recovery drive that will boot your computer.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
62
____________________ is sometimes referred to as mirroring.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
63
Most applications that ____________________ files can sense when a file has been corrupted.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
64
A(n) ____________________ is a series of unique bytes that, like a fingerprint, uniquely identifies a malicious computer program and distinguishes it from legitimate files on your PC.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
65
Case-Based Critical Thinking Questions Case 6-1 Jill is concerned about the security of her computer. She is worried that her files may be in danger while being stored on her computer. To protect her computer from malicious attacks, Jill wants to practice 'safe computing,' which means she should ____.
A) move to a safer neighborhood
B) have a friend "computer sit" when she isn't home
C) avoid sources of malicious software
D) buy a heavier computer that would be harder to steal
A) move to a safer neighborhood
B) have a friend "computer sit" when she isn't home
C) avoid sources of malicious software
D) buy a heavier computer that would be harder to steal

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
66
____________________ is created and unleashed by individuals referred to as hackers, crackers, black hats, or cybercriminals.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
67
In the event your computer will not boot and your hard drive is no longer working, describe how a system recovery drive can load Windows and then restore your programs and data.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
68
Describe ways to protect files while you are working on them.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
69
A(n) ____________________ makes backup copies of files as they are added or changed.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
70
Case-Based Critical Thinking Questions Case 6-1 Jill is concerned about the security of her computer. She is worried that her files may be in danger while being stored on her computer. Jill knows that a data file is most vulnerable while you are working with it. She activated her AutoRecovery option, but she should still ____.
A) plug her computer into the wall outlet every few hours
B) specify where and how frequently automatically saved data is stored
C) let her computer run on battery power every once in a while
D) fear power surges
A) plug her computer into the wall outlet every few hours
B) specify where and how frequently automatically saved data is stored
C) let her computer run on battery power every once in a while
D) fear power surges

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
71
In the worst case, sectors damaged during a(n) ____________________ crash are part of the Registry that keeps track of file locations on your hard disk.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
72
To protect your computer from malicious attacks, experts recommend that you practice ____________________ by installing antivirus software.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
73
When you get a new computer, make a(n) ____________________ recovery drive.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
74
A(n) ____________________ spreads by sending itself to every address in the address book of an infected computer.

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck
75
Case-Based Critical Thinking Questions Case 6-1 Jill is concerned about the security of her computer. She is worried that her files may be in danger while being stored on her computer. Jill has antivirus software installed on her computer. She must make sure to ____.
A) keep her antivirus software subscription and virus definitions up to date
B) turn on her computer at least once a day
C) leave her computer on for at least five hours every day
D) buy new versions of the software every year
A) keep her antivirus software subscription and virus definitions up to date
B) turn on her computer at least once a day
C) leave her computer on for at least five hours every day
D) buy new versions of the software every year

Unlock Deck
Unlock for access to all 75 flashcards in this deck.
Unlock Deck
k this deck



