Deck 3: Computer Software
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/139
Play
Full screen (f)
Deck 3: Computer Software
1
If you purchase software, it belongs to you and you can do what you want including copying it.
False
2
CAD software is designed to be used by architects.
True
3
There are no advantages to purchasing software in a box rather than downloading.
False
4
A virus signature is a digitally signed certificate that certifies the file is virus free.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
5
Desktop widgets come with a computer and are not available from other sources.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
6
A quarantined file is generally encrypted before storing.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
7
Antivirus software does not require any updates.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
8
Product activation and registration represent the same function with different names.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
9
Utility software includes diagnostics that track down and fix disk errors.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
10
Files that are zipped contain consolidated files that are compressed and ready to execute.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
11
You may purchase third party utility programs but they are really a waste of money. All the needed utility programs come preloaded.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
12
A zombie is a computer under the control of a bad bot.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
13
When you update your computer, it overrides the existing program files.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
14
You can usually start application software on most personal computers from the Start menu or a desktop icon.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
15
Productivity software is designed to make the operating system run more effectively.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
16
Open source software is copyrighted.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
17
Spreadsheets have built-in formulas.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
18
By using spell checkers and grammar checkers you are assured your document will be error free.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
19
Payroll software is an example of vertical market software.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
20
Executable files have a .exe extension.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
21
Utilities are an example of application software.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
22
Software considered utility software is ____.
A) Windows
B) Word processing
C) Spell check
D) Setup-Wizards
A) Windows
B) Word processing
C) Spell check
D) Setup-Wizards

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
23
Application software is designed to accomplish ____ tasks.
A) real-world
B) computer-centric tasks
C) gaming tasks
D) only operating systems tasks
A) real-world
B) computer-centric tasks
C) gaming tasks
D) only operating systems tasks

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
24
A security package integrates several security modules to protect against malware.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
25
A(n) startup file is designed to be started by users or automatically launched by the operating system.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
26
System software is designed to accomplish ____ tasks.
A) real-world
B) computer-centric
C) gaming
D) only operating systems
A) real-world
B) computer-centric
C) gaming
D) only operating systems

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
27
Public domain software has restriction on its use.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
28
Production software refers to any type of application software that has the potential to help people do their work more efficiently.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
29
A device driver is software that helps a peripheral device establish communication with a computer.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
30
Some web applications such as Google Earth require a client-side program to be installed on your local computer.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
31
Vertical market software is designed to automate specialized tasks in a specific market or business.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
32
A typical software package contains one file.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
33
A virus hoax usually arrives as an attachment .

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
34
A group of utility programs that can help you recover files include ____.
A) Recover My Files
B) VirtualLab
C) R-Undelete
D) all of the above
A) Recover My Files
B) VirtualLab
C) R-Undelete
D) all of the above

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
35
You can automatically create personalized letters by using templates .

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
36
CD ripper software is designed to pull a track off an audio CD and store it in an encoded format.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
37
Software most commonly associated with productivity software is ____.
A) Windows
B) Real-time players
C) Word processing
D) Browsers
A) Windows
B) Real-time players
C) Word processing
D) Browsers

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
38
Hackers can use rootkits to hide their work.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
39
A s oftware license defines the ways you may use a computer program.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
40
A trademark is a form of legal protection that grants the author of the original work exclusive rights to copy, distribute, sell and modify.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
41
Popular presentation software products includes all of the following except ____.
A) Microsoft PowerPoint
B) Apple Keynote
C) Open Office Impress
D) Movie Maker
A) Microsoft PowerPoint
B) Apple Keynote
C) Open Office Impress
D) Movie Maker

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
42
3-D graphics software provides a set of tools for creating ____ that represents three-dimensional objects.
A) models
B) protypes
C) wireframes
D) photos
A) models
B) protypes
C) wireframes
D) photos

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
43
When creating a formula in a spreadsheet, for flexibility, each operand is a ____.
A) number
B) cell number
C) cell reference
D) location
A) number
B) cell number
C) cell reference
D) location

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
44
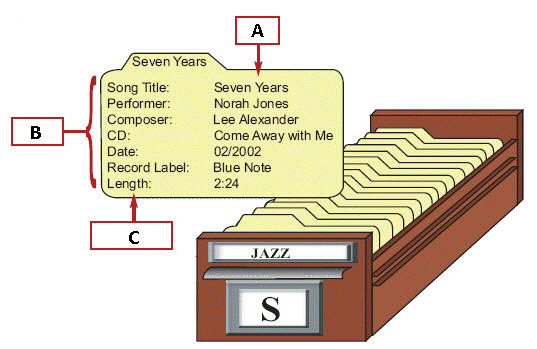 In the figure above, the box with a C represents a ____.
In the figure above, the box with a C represents a ____.A) data
B) field
C) record
D) item

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
45
It is illegal to do all the following expect ____.
A) copy and sell to a friend
B) copy and give to a friend
C) copy and keep as backup
D) modify
A) copy and sell to a friend
B) copy and give to a friend
C) copy and keep as backup
D) modify

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
46
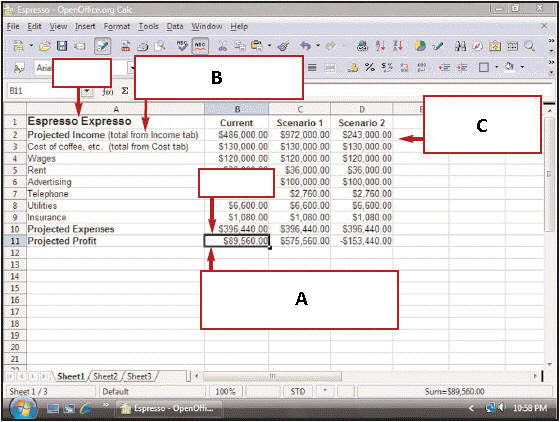 In the figure above, the box with an A is pointing to a(n) ____.
In the figure above, the box with an A is pointing to a(n) ____.A) formula
B) active cell
C) value
D) label

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
47
A page layout includes ____.
A) headers and footers
B) page numbers
C) a & b
D) none of the above
A) headers and footers
B) page numbers
C) a & b
D) none of the above

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
48
An example of number-crunching software includes ____.
A) SPSS
B) Mathcad
C) Quicken
D) all of the above
A) SPSS
B) Mathcad
C) Quicken
D) all of the above

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
49
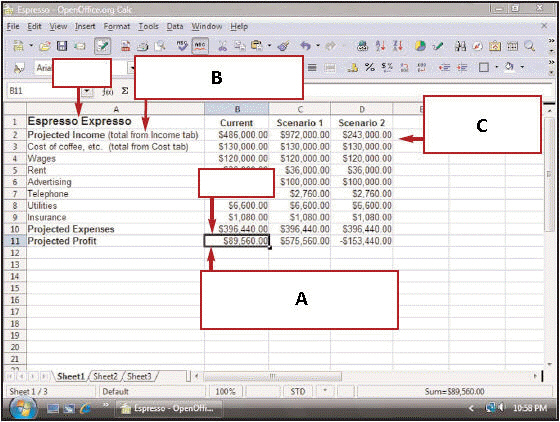 In the figure above, the box with a B is pointing to a(n) ____.
In the figure above, the box with a B is pointing to a(n) ____.A) formula
B) active cell
C) value
D) label

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
50
A shrink wrap license goes into effect as soon as ____.
A) you use it
B) you purchase it
C) you open it
D) you register it
A) you use it
B) you purchase it
C) you open it
D) you register it

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
51
In order to find a particular record or group of records in a database you use a ____.
A) find
B) query
C) inquiry
D) search
A) find
B) query
C) inquiry
D) search

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
52
____ is a type of application software designed to help several people collaborate.
A) Shareware
B) Groupware
C) Together
D) E-Mail
A) Shareware
B) Groupware
C) Together
D) E-Mail

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
53
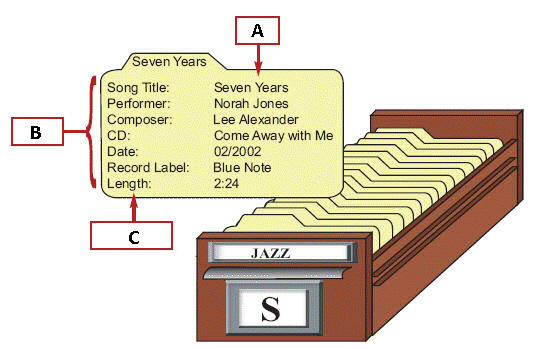 In the figure above, the box with an A represents ____.
In the figure above, the box with an A represents ____.A) data
B) fields
C) records
D) items

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
54
In order for software to work on a given computer, it must meet ____.
A) computer configuration
B) operating specifications
C) software requirements
D) system requirements
A) computer configuration
B) operating specifications
C) software requirements
D) system requirements

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
55
You can use the results from a search on a database in all of these ways except ____.
A) print reports
B) export data
C) convert formats
D) create record
A) print reports
B) export data
C) convert formats
D) create record

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
56
A ____ is a legal contract that defines the ways in which you may use a computer program.
A) software license
B) software agreement
C) software copyright
D) purchase agreement
A) software license
B) software agreement
C) software copyright
D) purchase agreement

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
57
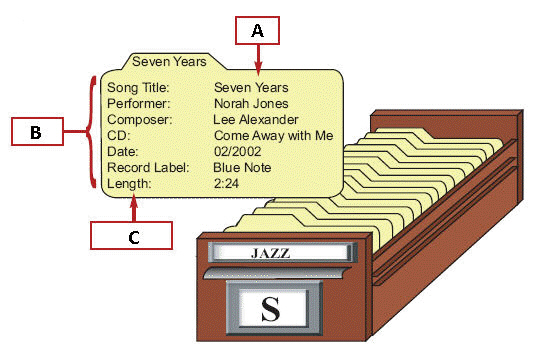
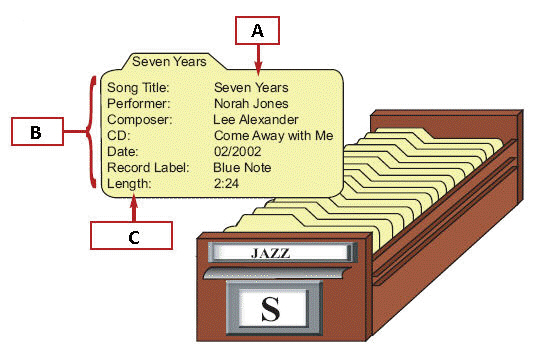 In the figure above, the index card represents a single database ____.
In the figure above, the index card represents a single database ____.A) data
B) field
C) record
D) item

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
58
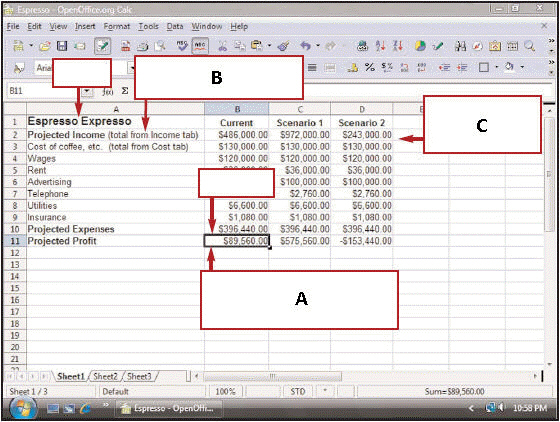 In the figure above, the box with a C is pointing to a(n) ____.
In the figure above, the box with a C is pointing to a(n) ____.A) formula
B) label
C) value
D) active cell

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
59
The intersection of a column and a row on a spreadsheet is called a ____.
A) formula
B) value
C) number
D) cell
A) formula
B) value
C) number
D) cell

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
60
 In the figure above, the box with a B represents the ____.
In the figure above, the box with a B represents the ____.A) data
B) fields
C) records
D) items

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
61
____ software is typically copy-righted software that is marketed under try-before-you buy policy.
A) Commercial
B) Open source
C) Shareware
D) Freeware
A) Commercial
B) Open source
C) Shareware
D) Freeware

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
62
Portable software is ____.
A) designed for portable devices
B) licensed only for portable devices
C) designed to run from removable storage
D) designed to run on portable devices
A) designed for portable devices
B) licensed only for portable devices
C) designed to run from removable storage
D) designed to run on portable devices

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
63
To avoid security threats a user can ____.
A) store all data on a thumb drive
B) enable the Hide extensions
C) read email as soon as it comes in
D) avoid opening suspicious email attachments.
A) store all data on a thumb drive
B) enable the Hide extensions
C) read email as soon as it comes in
D) avoid opening suspicious email attachments.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
64
____ software may be sold or distributed free of charge in compiled form but almost always includes the source code.
A) Commercial
B) Open source
C) Shareware
D) Sourceware
A) Commercial
B) Open source
C) Shareware
D) Sourceware

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
65
A ____ is any software that can automate a task or automatically execute a task.
A) virus
B) worm
C) Trojan horse
D) bot
A) virus
B) worm
C) Trojan horse
D) bot

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
66
During product activation you must ____.
A) run the program
B) create a password
C) enter a product key
D) none of the above
A) run the program
B) create a password
C) enter a product key
D) none of the above

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
67
If you are installing a local application from a distribution CD and it does not automatically run, you should ____.
A) return it immediately
B) reboot the computer
C) look for a file called setup.exe
D) call the manufacturer
A) return it immediately
B) reboot the computer
C) look for a file called setup.exe
D) call the manufacturer

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
68
A service pack ____.
A) updates the services your computer performs
B) requires a service call to a technician
C) fixes and updates the operating system
D) repairs and fixes the hardware
A) updates the services your computer performs
B) requires a service call to a technician
C) fixes and updates the operating system
D) repairs and fixes the hardware

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
69
Data files supplied with a software package support ____ file extensions.
A) .exe
B) .hlp
C) .doc
D) .xls
A) .exe
B) .hlp
C) .doc
D) .xls

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
70
Support programs have a ____ extension.
A) .exe
B) .hlp
C) .dll
D) .spt
A) .exe
B) .hlp
C) .dll
D) .spt

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
71
____ applications are software that is designed to reside on a computer's hard disk.
A) help
B) setup
C) data
D) local
A) help
B) setup
C) data
D) local

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
72
All of the following are application or utility software except ____.
A) Wordpad
B) Paint
C) SecurityCenter
D) Windows
A) Wordpad
B) Paint
C) SecurityCenter
D) Windows

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
73
Downloadable software can be provided in different formats such as ____.
A) self -installing
B) self-executing zip
C) non-executing zip
D) all of the above
A) self -installing
B) self-executing zip
C) non-executing zip
D) all of the above

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
74
Web applications are ____.
A) installed locally and run on the Web
B) accessed and run on the Web
C) installed on the Web and run locally
D) all the above
A) installed locally and run on the Web
B) accessed and run on the Web
C) installed on the Web and run locally
D) all the above

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
75
When installing software, you should ____.
A) always select the full installation
B) always select the custom installation
C) always select minimum installation
D) select custom when you don't need all the features.
A) always select the full installation
B) always select the custom installation
C) always select minimum installation
D) select custom when you don't need all the features.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
76
An end user license agreement is ____.
A) purchased separate from the software
B) really pirated software
C) displayed on-screen when you first install
D) licensed only to a single person
A) purchased separate from the software
B) really pirated software
C) displayed on-screen when you first install
D) licensed only to a single person

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
77
____ software is typically available as a trial version.
A) Commercial
B) Open source
C) Demoware
D) Shareware
A) Commercial
B) Open source
C) Demoware
D) Shareware

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
78
To get rid of software you no longer want, you ____.
A) delete the icon
B) delete the files
C) run uninstall
D) a & b
A) delete the icon
B) delete the files
C) run uninstall
D) a & b

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
79
____ software is typically sold in a store or online.
A) Commercial
B) Open source
C) Shareware
D) Freeware
A) Commercial
B) Open source
C) Shareware
D) Freeware

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck
80
The term rootkit refers to ____.
A) a program that repairs the computer's hardware core
B) a program that repairs the kernel
C) Software tools used to conceal malware
D) Software tools used to conceal security tools.
A) a program that repairs the computer's hardware core
B) a program that repairs the kernel
C) Software tools used to conceal malware
D) Software tools used to conceal security tools.

Unlock Deck
Unlock for access to all 139 flashcards in this deck.
Unlock Deck
k this deck



