Deck 17: Understaning Essential Unit Concepts
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Match between columns

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/62
Play
Full screen (f)
Deck 17: Understaning Essential Unit Concepts
1
One of the most important components of personal computer hardware is ____, which stores instructions and data.
A) the processor
B) optical storage
C) the cloud
D) memory
A) the processor
B) optical storage
C) the cloud
D) memory
D
2
Which of the following is NOT an example of optical storage?
A) CD
B) hard disk
C) Blu-ray
D) DVD
A) CD
B) hard disk
C) Blu-ray
D) DVD
B
3
____ computers are used by large businesses, government agencies, and in science and education to provide centralized storage and processing and to manipulate tremendous amounts of data.
A) Subnotebook
B) Optical
C) External
D) Mainframe
A) Subnotebook
B) Optical
C) External
D) Mainframe
D
4
The computer needs additional components called ____ to accomplish its input, output, and storage functions.
A) mice
B) peripheral devices
C) architecture
D) ports
A) mice
B) peripheral devices
C) architecture
D) ports

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
5
____ memory is a chip on the motherboard that stores the date, time, and system parameters.
A) ROM
B) RAM
C) CPU
D) CMOS
A) ROM
B) RAM
C) CPU
D) CMOS

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
6
Which of the following is NOT a personal computer?
A) laptop
B) desktop
C) mainframe
D) All of the above.
A) laptop
B) desktop
C) mainframe
D) All of the above.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
7
What temporarily holds programs and data while the computer is on and allows the computer to access that information randomly?
A) cache
B) RAM
C) ROM
D) CMOS
A) cache
B) RAM
C) ROM
D) CMOS

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
8
Which of the following is a personal computer?
A) supercomputer
B) mainframe
C) desktop
D) All of the above.
A) supercomputer
B) mainframe
C) desktop
D) All of the above.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
9
____ are thin computers that do not have an external keyboard or mouse.
A) Laptops
B) Desktops
C) Tablets
D) Mainframes
A) Laptops
B) Desktops
C) Tablets
D) Mainframes

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
10
Megahertz is a measurement of ____.
A) the speed of the microprocessor
B) the amount of RAM
C) RAM speed
D) cache memory
A) the speed of the microprocessor
B) the amount of RAM
C) RAM speed
D) cache memory

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
11
Processing tasks occur on the ____.
A) mouse
B) keyboard
C) motherboard
D) operating system
A) mouse
B) keyboard
C) motherboard
D) operating system

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
12
Most ____ devices, like keyboards, for example, connect to a computer either with cables or wirelessly.
A) storage
B) touch
C) recording
D) input
A) storage
B) touch
C) recording
D) input

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
13
You are running two programs at once that each require 10 megabytes on a computer that only has 16 megabytes of RAM. What makes this possible?
A) CMOS
B) ROM
C) cache
D) virtual memory
A) CMOS
B) ROM
C) cache
D) virtual memory

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
14



Which of the following is NOT shown in the accompanying figures?
A) touch screen
B) trackball
C) touch pad
D) mouse

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
15
Special high-speed memory located on or near the microprocessor's is called ____.
A) ROM
B) storage
C) virtual memory
D) cache memory
A) ROM
B) storage
C) virtual memory
D) cache memory

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
16
RAM is often referred to as ____ memory.
A) permanent
B) semipermanent
C) volatile
D) None of the above.
A) permanent
B) semipermanent
C) volatile
D) None of the above.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
17
____ refers to the number of bits that are processed at one time.
A) Characters per second
B) Quad core
C) Clock speed
D) Word size
A) Characters per second
B) Quad core
C) Clock speed
D) Word size

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
18
A file that tells a computer how to perform a specific task is called a(n) ____ file.
A) executable
B) instruction
C) data
D) configuration
A) executable
B) instruction
C) data
D) configuration

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
19
The physical components of a computer are referred to as ____.
A) operating systems
B) specifications
C) configurations
D) hardware
A) operating systems
B) specifications
C) configurations
D) hardware

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
20
A(n) ____ is based on flash memory, but is intended as a replacement for traditional hard disk drives.
A) CMOS
B) SSD
C) GUI
D) RAM cache
A) CMOS
B) SSD
C) GUI
D) RAM cache

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
21
An example of an output device is a ____.
A) printer
B) keyboard
C) mouse
D) touch pad
A) printer
B) keyboard
C) mouse
D) touch pad

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
22
DVD+Rs are rewritable.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
23
An input device is any hardware peripheral that communicates the results of data processing.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
24



The devices shown in the accompanying figure are all ____ devices.
A) output
B) pointing
C) recording
D) storage

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
25
Antivirus software protects against which of the following types of malware?
A) viruses
B) firewalls
C) phishing scams
D) spoofed sites
A) viruses
B) firewalls
C) phishing scams
D) spoofed sites

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
26
Expansion cards plug into electrical connectors on the motherboard called expansion ____.
A) ports
B) outlets
C) slots
D) buses
A) ports
B) outlets
C) slots
D) buses

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
27
A hard disk is a type of magnetic storage device.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
28
Database management software allows you to create illustrations, diagrams, graphs, and charts that can be projected before a group, printed out for quick reference, or transmitted to remote computers.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
29
A device driver is a computer program that makes communication possible between your computer and one of its peripherals.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
30
Protocols in data communication establish the countries with which data can be exchanged.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
31
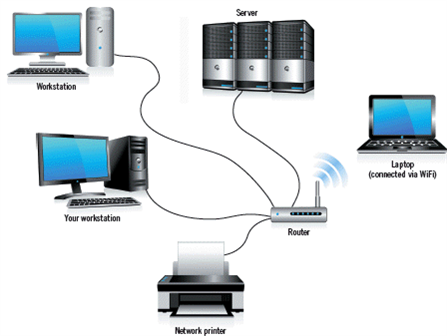
In the accompanying figure, the network shown is a ____ network.
A) WiMAX
B) client/server
C) WLAN
D) Bluetooth

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
32
The communication path between a microprocessor, RAM, and peripherals is called the data bus.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
33
A network with a computers dependent on a server is called a client/server network.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
34

In the accompanying figure, each of the items labeled "workstation" must have a network interface card installed.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
35
____ manage the system resources of a computer so programs can run properly.
A) Database management software
B) Utilities
C) Firewalls
D) Operating systems
A) Database management software
B) Utilities
C) Firewalls
D) Operating systems

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
36
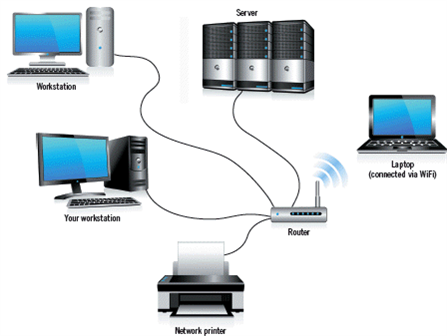
In the accompanying figure, each of the components connected by wires is called a ____.
A) client
B) node
C) workstation
D) server

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
37
Which of the following is the smallest unit of measurement?
A) a terabyte
B) a gigabyte
C) a megabyte
D) a kilobyte
A) a terabyte
B) a gigabyte
C) a megabyte
D) a kilobyte

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
38
An interface card can be plugged into an expansion slot on the motherboard of a computer.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
39
The practice of sending e-mails to customers or potential customers of a legitimate website asking them to click a link in the e-mail is called ____.
A) spoofing
B) phishing
C) pharming
D) spaming
A) spoofing
B) phishing
C) pharming
D) spaming

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
40
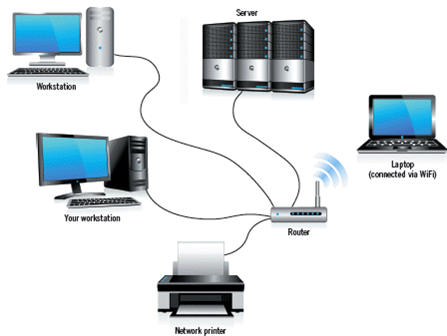
The printer in the accompanying figure is considered a client.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
41
____________________ is the flow of data from the microprocessor to memory to peripherals and back again.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
42
A(n) system resource is any part of the computer system, including memory, storage devices, and the microprocessor

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
43
Critical Thinking Questions
Case 1-2
You have been chosen to upgrade the computer system for the local volunteer association. You want to purchase a system that will still be useful for several years.
You want the computer to be able to run faster. What is the easiest thing you can add to make this happen?
a. RAM
b. CMOS
c. motherboard
d. additional operating system
Case 1-2
You have been chosen to upgrade the computer system for the local volunteer association. You want to purchase a system that will still be useful for several years.
You want the computer to be able to run faster. What is the easiest thing you can add to make this happen?
a. RAM
b. CMOS
c. motherboard
d. additional operating system

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
44
Visual Basic, C, C++, and Java are all examples of computer programming ____________________.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
45
Discuss the use of the following ways to use the Web to get your work done: searching for information, communicating with others, telecommuting, and cloud computing.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
46
Special high-speed memory located on or near the microprocessor is called ____________________.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
47
Explain the differences between a kilobyte, a megabyte, a gigabyte, and a terabyte.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
48
A(n) ____________________ prevents other computers on the Internet from accessing a computer and prevents programs on a computer from accessing the Internet without the computer user's permission.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
49
If a keyboard is _________________________, this means that is has been designed to fit the natural placement of your hands and may reduce the risk of repetitive-motion injuries.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
50
If you are working on a budget and save the spreadsheet on your hard drive, it is called a(n) executable file

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
51
Phishing is a broad term that describes any program that is designed to cause harm or transmit information to others without the computer owner's permission.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
52
Utility software helps analyze, optimize, configure, and maintain a computer

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
53
Operating software enables you to perform specific tasks such as writing letters, creating presentations, analyzing statistics, creating graphic, and enhancing photos..

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
54
Critical Thinking Questions
Case 1-1
Christina is a salon owner in Baltimore, Maryland. She wants to create a list of all her clients in order to send them information about new promotions at the salon. She needs to purchase software to help her accomplish this. She also needs to track monthly expenses for her salon and needs software to do this as well.
What type of software should Christina purchase to help her track monthly expenses?
a. spreadsheet software
b. operating system software
c. database management software
d. word processing software
Case 1-1
Christina is a salon owner in Baltimore, Maryland. She wants to create a list of all her clients in order to send them information about new promotions at the salon. She needs to purchase software to help her accomplish this. She also needs to track monthly expenses for her salon and needs software to do this as well.
What type of software should Christina purchase to help her track monthly expenses?
a. spreadsheet software
b. operating system software
c. database management software
d. word processing software

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
55
Processing data is also referred to as ____________________ data.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
56
Critical Thinking Questions
Case 1-2
You have been chosen to upgrade the computer system for the local volunteer association. You want to purchase a system that will still be useful for several years.
You want to allow volunteers to copy files and carry them with them when they leave. What is a good choice for something that can store files, is transportable, and is small enough to fit in a pocket?
a. motherboard
b. CMOS
c. flash drive
d. optical drive
Case 1-2
You have been chosen to upgrade the computer system for the local volunteer association. You want to purchase a system that will still be useful for several years.
You want to allow volunteers to copy files and carry them with them when they leave. What is a good choice for something that can store files, is transportable, and is small enough to fit in a pocket?
a. motherboard
b. CMOS
c. flash drive
d. optical drive

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
57
____________________ memory is created and used by most computers when the amount of RAM needed exceeds the RAM available.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
58
Critical Thinking Questions
Case 1-1
Christina is a salon owner in Baltimore, Maryland. She wants to create a list of all her clients in order to send them information about new promotions at the salon. She needs to purchase software to help her accomplish this. She also needs to track monthly expenses for her salon and needs software to do this as well.
What type of software should Christina purchase to create and manage her collection of customer data?
a. indexing software
b. database management software
c. word processing software
d. operating system software
Case 1-1
Christina is a salon owner in Baltimore, Maryland. She wants to create a list of all her clients in order to send them information about new promotions at the salon. She needs to purchase software to help her accomplish this. She also needs to track monthly expenses for her salon and needs software to do this as well.
What type of software should Christina purchase to create and manage her collection of customer data?
a. indexing software
b. database management software
c. word processing software
d. operating system software

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
59
Technical information about hardware components on a computer are called configurations

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
60
A(n) ____________________ is an electronic device that accepts information and instructions from a user, manipulates the information according to the instructions, displays the information in some way, and stores the information for later retrieval.

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
61
Critical Thinking Questions
Case 1-2
You have been chosen to upgrade the computer system for the local volunteer association. You want to purchase a system that will still be useful for several years.
You want the volunteers to have access to the most energy efficient type of monitor available. What is the best type of monitor technology to purchase?
a. TEM
b. fluorescent backlight
c. LED
d. LCD
Case 1-2
You have been chosen to upgrade the computer system for the local volunteer association. You want to purchase a system that will still be useful for several years.
You want the volunteers to have access to the most energy efficient type of monitor available. What is the best type of monitor technology to purchase?
a. TEM
b. fluorescent backlight
c. LED
d. LCD

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck
62
Match between columns

Unlock Deck
Unlock for access to all 62 flashcards in this deck.
Unlock Deck
k this deck



