Deck 2: Lan/Wan Interconnectivity
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/82
Play
Full screen (f)
Deck 2: Lan/Wan Interconnectivity
1
Taken together, the set of layers of the OSI model is called a stack.
True
2
All MAUs must have terminators.
False
3
The OSI is the product of which standards organization?
A)ISO
B)ANSI
C)IEEE
D)Both A and B.
A)ISO
B)ANSI
C)IEEE
D)Both A and B.
D
4
Discovery is the process of checking communication cable for a specific voltage level indicating the presence of a data-carrying signal.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
5
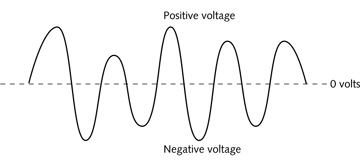 The figure above is a representation of a(n)digital signal.
The figure above is a representation of a(n)digital signal.
Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
6
When data is transmitted in Ethernet communications, it is encapsulated in frames.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
7
A(n)backbone is a high-capacity communications medium that joins networks and central network devices on the same floor in a building, on different floors, and across long distances.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
8
The number, size, and frequency of packets transmitted on a network in a given amount of time is referred to as network usage .

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
9
A(n)broadcast frame is one that is sent to all points on the network.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
10
A(n)T-carrier line is a dedicated telephone line that can be used for data communications to connect two different locations for continuous point-to-point communications.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
11
Typically, if a network has a low startup cost, there will be a low cost to maintain it.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
12
SSL is a data encryption technique employed between a server and a client.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
13
When using FDDI, it is possible for several frames from several nodes to be on the network at a given time.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
14
Throughput is the transmission capacity of a communications medium, which is typically measured in bits per second or hertz, and which is determined by the maximum minus the minimum transmission capacity.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
15
The telephone companies were the earliest source of WAN connectivity.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
16
It is okay to use Ethernet II and standard 802.3 frames among the same communicating nodes on the same network.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
17
The token ring transport method uses a physical star topology along with the logic of a(n)ring topology.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
18
In a traditional ring design, there are two terminators.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
19
____ encoding assigns a binary value to the presence of a particular signal state.
A)Binary
B)Current-state
C)State-transition
D)Basic
A)Binary
B)Current-state
C)State-transition
D)Basic

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
20
Flow control ensures that one device does not send information faster than it can be received by another device.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
21
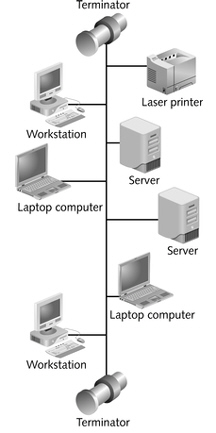 The figure above shows a ____ network.
The figure above shows a ____ network.A)bus
B)ring
C)star
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
22
EMI is a source of ____ layer interference.
A)Data Link
B)Network
C)Physical
D)Transport
A)Data Link
B)Network
C)Physical
D)Transport

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
23
Which is not true about bus networks?
A)They are relatively inexpensive to implement.
B)It is easy to isolate a single malfunctioning node or cable segment.
C)They work well for small networks.
D)None of the above.
A)They are relatively inexpensive to implement.
B)It is easy to isolate a single malfunctioning node or cable segment.
C)They work well for small networks.
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
24
The P in PDU stands for ____.
A)protocol
B)peer
C)prototype
D)primitive
A)protocol
B)peer
C)prototype
D)primitive

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
25
____ is a process used by routers that involves gathering information about how many nodes are on a network and where they are located.
A)Encryption
B)Broadcasting
C)Beaconing
D)Discovery
A)Encryption
B)Broadcasting
C)Beaconing
D)Discovery

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
26
A device's MAC address is coded as a ____ number.
A)binary
B)decimal
C)hexadecimal
D)None of the above.
A)binary
B)decimal
C)hexadecimal
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
27
The ____ layer offers a way to set up half- and full-duplex communications.
A)Communications
B)Network
C)Session
D)Transport
A)Communications
B)Network
C)Session
D)Transport

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
28
Flow control software and capabilities are found in the ____ layer of the OSI model.
A)Network
B)Session
C)Transport
D)Data Link
A)Network
B)Session
C)Transport
D)Data Link

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
29
____ are used least frequently on networks.
A)Gateways
B)Bridges
C)Routers
D)Switches
A)Gateways
B)Bridges
C)Routers
D)Switches

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
30
Which is not true when comparing the ring and bus topologies?
A)The ring topology is less expensive to implement than the bus topology.
B)The ring topology is easier to manage than the bus topology.
C)The ring topology enables more reliable communications than the bus.
D)None of the above.
A)The ring topology is less expensive to implement than the bus topology.
B)The ring topology is easier to manage than the bus topology.
C)The ring topology enables more reliable communications than the bus.
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
31
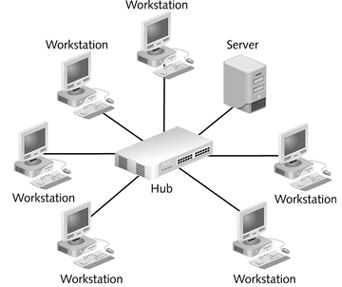 The figure above shows a ____ network.
The figure above shows a ____ network.A)bus
B)ring
C)star
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
32
The MAC sublayer of the Data Link layer does not ____.
A)ensure reliable communications by initiating a communications link between two nodes and then guarding them against interruptions to the link
B)examine the physical or device address information contained in each frame
C)regulate how multiple devices share communications on the same network
D)None of the above.
A)ensure reliable communications by initiating a communications link between two nodes and then guarding them against interruptions to the link
B)examine the physical or device address information contained in each frame
C)regulate how multiple devices share communications on the same network
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
33
After the PDU is received by the next layer, the control information and transfer instructions are stripped out, and the resulting packet is called the ____.
A)stripped data unit
B)single data unit
C)service data unit
D)secure data unit
A)stripped data unit
B)single data unit
C)service data unit
D)secure data unit

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
34
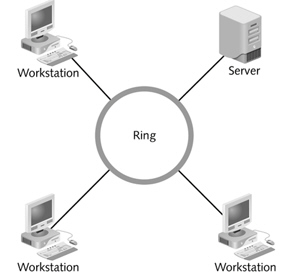 The figure above shows a ____ network.
The figure above shows a ____ network.A)bus
B)ring
C)star
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
35
____ generates the least amount of network traffic.
A)Network users primarily accessing word-processing software
B)Networks on which there is frequent exchange of database information
C)Scientific and publications software
D)Both A and B.
A)Network users primarily accessing word-processing software
B)Networks on which there is frequent exchange of database information
C)Scientific and publications software
D)Both A and B.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
36
The ____ topology is the oldest communications design method, with roots in telephone switching systems.
A)bus
B)ring
C)star
D)None of the above.
A)bus
B)ring
C)star
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
37
____ protocols enable an OSI layer on a sending node to communicate with the same layer on the receiving node.
A)Layer
B)Peer
C)Link
D)Transfer
A)Layer
B)Peer
C)Link
D)Transfer

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
38
Network interface cards, intelligent hubs, and bridges are found in the ____ layer of the OSI model.
A)Network
B)Physical
C)Transport
D)Data Link
A)Network
B)Physical
C)Transport
D)Data Link

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
39
A primitive is ____.
A)a command used to transfer information from one layer in an OSI stack to another layer
B)the smallest unit of data allowed in the Physical layer
C)a command used to transfer information from an OSI layer on the sending node to the same layer on the receiving node
D)Both A and B.
A)a command used to transfer information from one layer in an OSI stack to another layer
B)the smallest unit of data allowed in the Physical layer
C)a command used to transfer information from an OSI layer on the sending node to the same layer on the receiving node
D)Both A and B.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
40
____ encoding simply checks for a change in the signal state, from low to high or high to low.
A)Binary
B)Current-state
C)State-transition
D)Basic
A)Binary
B)Current-state
C)State-transition
D)Basic

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
41
The ____ part in a frame synchronizes frame transmission and consists of an alternating pattern of zeros and ones.
A)preamble
B)SFD
C)FCS
D)destination address
A)preamble
B)SFD
C)FCS
D)destination address

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
42
The Ethernet protocol permits ____ node(s)to transmit at any time.
A)one
B)two
C)three
D)There is no limit.
A)one
B)two
C)three
D)There is no limit.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
43
____ is the most efficient method.
A)TDMA
B)FDMA
C)Statistical multiple access
D)Both A and B.
A)TDMA
B)FDMA
C)Statistical multiple access
D)Both A and B.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
44
____ does not guarantee the most efficient use of the network medium, because transmission occurs on only one channel at a time.
A)TDMA
B)FDMA
C)Statistical multiple access
D)Both A and B.
A)TDMA
B)FDMA
C)Statistical multiple access
D)Both A and B.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
45
High-speed capability is especially important when images, graphics, and other large files need to be transported over long distance or onto WANs.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
46
____ is an error condition on a token ring network that indicates one or more nodes is not functioning.
A)Broadcasting
B)Switching
C)Redirecting
D)Beaconing
A)Broadcasting
B)Switching
C)Redirecting
D)Beaconing

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
47
The token ring access method was developed by ____.
A)HP
B)IBM
C)3Com
D)Intel
A)HP
B)IBM
C)3Com
D)Intel

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
48
The ____ field uses a cyclic redundancy check in a token ring frame.
A)frame check sequence
B)PAD
C)start delimiter
D)end delimiter
A)frame check sequence
B)PAD
C)start delimiter
D)end delimiter

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
49
____ is the process of transmitting a data-carrying packet over radio waves through short bursts.
A)Bursting
B)Packet radio
C)Beaconing
D)Broadcasting
A)Bursting
B)Packet radio
C)Beaconing
D)Broadcasting

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
50
Which is not true about FDDI?
A)It uses token passing for network communications.
B)It uses fiber-optic cable as the communications medium.
C)It was developed in the mid-1980s to provide higher-speed data communications than that offered by Ethernet or token ring.
D)None of the above.
A)It uses token passing for network communications.
B)It uses fiber-optic cable as the communications medium.
C)It was developed in the mid-1980s to provide higher-speed data communications than that offered by Ethernet or token ring.
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
51
In a connectionless protocol a logical connection is established between sending and receiving nodes before full communications begin.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
52
____ establishes a dedicated logical circuit between the two transmitting nodes.
A)Packet switching
B)Primitive switching
C)Message switching
D)Circuit switching
A)Packet switching
B)Primitive switching
C)Message switching
D)Circuit switching

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
53
____ uses a store-and-forward communication method to transmit data from sending to receiving node.
A)Packet switching
B)Primitive switching
C)Message switching
D)Circuit switching
A)Packet switching
B)Primitive switching
C)Message switching
D)Circuit switching

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
54
Two computers can communicate within a LAN or across a WAN even if they are not both operating under the same communication model.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
55
The ____ field is not a field in a token.
A)access control
B)starting delimiter
C)ending delimiter
D)None of the above.
A)access control
B)starting delimiter
C)ending delimiter
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
56
Ethernet currently enjoys more popularity than token ring because there are many Ethernet network equipment options and because it is well-suited for high-speed WAN connectivity.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
57
The ____ topology is the most popular topology in use.
A)bus
B)ring
C)star
D)None of the above.
A)bus
B)ring
C)star
D)None of the above.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
58
Ethernet uses a control method known as CSMA/CD.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
59
Token ring is defined through the IEEE 802.3 specifications.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
60
____ divides the channels into frequencies, and each channel has its own broadcast frequency and bandwidth.
A)TDMA
B)FDMA
C)Statistical multiple access
D)Both A and B.
A)TDMA
B)FDMA
C)Statistical multiple access
D)Both A and B.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
61
What is a redirector? What OSI layer is it used in?

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
62
The ____________________ is the total amount of communications cable that makes up a network.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
63
What is a MAU? With which type of access method are MAUs associated?

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
64
Modern networks combine the logical communications of a(n)____________________ with the physical layout of a(n)____________________.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
65
Regional telephone companies are also called ____________________ or regional bell operating companies (RBOCs).

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
66
What is encryption? Which OSI layer is responsible for encryption?

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
67
What are the two types of packets that can be sent by FDDI? When is each type used?

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
68
Each token ring network designates one node as the ____________________, which is responsible for packet timing on the network and for issuing new token frames if problems occur.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
69
An ordinary radio or telephone signal is an example of a(n)____________________ transmission.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
70
List three ways in which the OSI model, over the years, has facilitated the growth in network communications.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
71
____________________ are logical communication paths set up to send and receive data.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
72
FDDI employs two rings, so that if one ring malfunctions, data can reach its destination on the other ring.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
73
What is a hub? With which network topology are hubs associated?

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
74
Satellite is the most expensive way to build a wireless WAN that connects LANs.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
75
____________________ is a network communication technique that uses a dedicated channel to transmit information between two nodes.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
76
____________________ is used to provide a way to quickly adapt protocols that are not fully compliant with 802.2 standards, such as AppleTalk and DEC's LAT protocols.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
77
Broadcast storms are more common on token ring networks than on Ethernet networks.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
78
What is a cyclic redundancy check, and at which OSI layer is it performed?

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
79
A bus network has a(n)____________________ at each end.

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck
80
What is a collision? How are collisions detected?

Unlock Deck
Unlock for access to all 82 flashcards in this deck.
Unlock Deck
k this deck



