Deck 12: Security Through Monitoring and Auditing
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/86
Play
Full screen (f)
Deck 12: Security Through Monitoring and Auditing
1
SYSCON is a Server Console command that is carried forward from earlier versions of NetWare.
False
2
Network-based intrusion-detection software is categorized as host wrappers or host-based agents.
False
3
In Red Hat Linux 9.x, by default, each log file has four rotation levels, to enable the retention of up to four weeks of information.
True
4
In Windows Server 2003 event viewer, an informational message such as a notice that a service has been started is prefaced by a black "!" (exclamation point) that appears on a yellow caution symbol.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
5
The device log records information about system-related events such as hardware errors, driver problems, and hard drive errors.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
6
At minimum, active intrusion detection alerts a server or network administrator about an attack or intrusion, so the administrator can take action.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
7
In Mac OS X, the FTP Log keeps track of file uploads, downloads, and communications with FTP servers.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
8
If % Network utilization is frequently over 90 percent, that means the network is experiencing collisions and there may be bottlenecks due to the network design, possibly indicating the need to create more or different subnets.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
9
The Netware 6.x Console Log enables you to trace information, such as NLMs that have been loaded or unloaded, and to trace other activities that have been performed from the console.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
10
Network Monitor is a utility which comes with Windows 2000 Server and Windows Server 2003.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
11
In Red Hat Linux, the Emacs and vi editors can be used to configure the syslog.conf file.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
12
SNMP enables network agents to gather information about network performance and send that information to a network management station.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
13
An inspector is an IDS that tracks a full range of data and events related to an operating system or network.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
14
Active intrusion detection is effective as long as the server or network administrator regularly checks the logs and recorded information for possible intrusion attempts.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
15
In Network Monitor the capture store is the amount of RAM and virtual memory that is used to store captured data.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
16
The default folder for saved Network Monitor capture information in Windows Server 2003 is \WINNT\system32\NETMON\CAPTURES .

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
17
Understanding the normal conditions for operating systems and a network is accomplished by establishing baselines .

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
18
File locks are open communication links between two processes on the server or between the server and a client.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
19
The who command provides information about who is logged on to Red Hat Linux 9.x.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
20
Network Monitor supports event management , which enables a server administrator to set up filters to capture a certain event or type of network activity.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
21
Which passive intrusion-detection tool provides a listing of open files, including suspicious open files?
A) klaxon
B) lsof
C) Dragon Squire
D) PreCis
A) klaxon
B) lsof
C) Dragon Squire
D) PreCis

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
22
Which type of IDS looks for excessive use of a computer's resources, such as the CPU or memory?
A) Passive
B) Network-based
C) Inspector
D) Auditor
A) Passive
B) Network-based
C) Inspector
D) Auditor

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
23
Which event log records events that are associated with Active Directory?
A) Active Directory
B) Directory Service
C) System
D) None of the above
A) Active Directory
B) Directory Service
C) System
D) None of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
24
Which type of intrusion detection focuses on monitoring network traffic associated with a specific network segment?
A) Host-based
B) System-based
C) Network-based
D) LAN-based
A) Host-based
B) System-based
C) Network-based
D) LAN-based

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
25
Which active intrusion-detection tool monitors for intruders and can take action on the basis of preestablished security policies?
A) Entercept
B) Symantec Intruder Alert
C) SecureHost
D) Storm Watch
A) Entercept
B) Symantec Intruder Alert
C) SecureHost
D) Storm Watch

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
26
What type of computer is placed on a network to attract attackers?
A) Dummy
B) Honeypot
C) Fake
D) Both a and b
E) Both b and c
A) Dummy
B) Honeypot
C) Fake
D) Both a and b
E) Both b and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
27
What type of intrusion detection monitors the system on which it is loaded?
A) Host-based
B) System-based
C) Network-based
D) Local-based
A) Host-based
B) System-based
C) Network-based
D) Local-based

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
28
What are the three principle event logs in Windows 2000 Server and Windows Server 2003?
A) System, Security, Application
B) System, Security, Directory Service
C) System, Directory Service, DNS
D) Security, Directory Service, Application
A) System, Security, Application
B) System, Security, Directory Service
C) System, Directory Service, DNS
D) Security, Directory Service, Application

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
29
Which of the following network activities may be monitored by a personal firewall?
A) Remote logon attempts
B) Port scanning
C) Dial-in attempts
D) All of the above
E) None of the above
A) Remote logon attempts
B) Port scanning
C) Dial-in attempts
D) All of the above
E) None of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
30
Which passive intrusion-detection tool monitors network activity and includes a proprietary programming language to customize the way it captures and analyzes information?
A) klaxon
B) Real Secure
C) Dragon Squire
D) Network Flight Recorder
A) klaxon
B) Real Secure
C) Dragon Squire
D) Network Flight Recorder

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
31
Gathering performance statistics each time a new software application is installed, on slow, average, and peak periods during its use, and tracking how many users are on that software is an example of acquiring a _____.
A) baseline
B) framework
C) foundation
D) utilization level
A) baseline
B) framework
C) foundation
D) utilization level

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
32
Which of the following activities are usually looked for using passive intrusion-detection tools?
A) Unusual or excessive e-mail traffic
B) Changes to security
C) Unplanned system shutdowns
D) Port scans
E) All of the above
A) Unusual or excessive e-mail traffic
B) Changes to security
C) Unplanned system shutdowns
D) Port scans
E) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
33
Which active intrusion-detection tool is a distributed system that works on servers and clients and denies application requests that are not permitted, on the basis of a security policy applying to the servers and clients?
A) Entercept
B) AppShield
C) SecureHost
D) Storm Watch
A) Entercept
B) AppShield
C) SecureHost
D) Storm Watch

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
34
In the event log, what type of event is indicated with a white "x" that appears inside a red circle?
A) Information
B) Warning
C) Standby
D) Error
A) Information
B) Warning
C) Standby
D) Error

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
35
Which active intrusion-detection tool monitors HTML activity and blocks attacks?
A) Entercept
B) AppShield
C) Snort
D) StormWatch
A) Entercept
B) AppShield
C) Snort
D) StormWatch

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
36
Which of the following options is a common approach to intrusion detection?
A) Archive
B) System-based
C) Host-based
D) Both a and b
E) Both b and c
A) Archive
B) System-based
C) Host-based
D) Both a and b
E) Both b and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
37
Which type of intrusion detection system looks for intrusion signatures on ports, through frame and packet headers, and through commands?
A) Network-based
B) Host-based
C) Auditor
D) Inspector
A) Network-based
B) Host-based
C) Auditor
D) Inspector

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following are examples of active intrusion-detection tools?
A) klaxon
B) lsof
C) AppShield
D) RealSecure
A) klaxon
B) lsof
C) AppShield
D) RealSecure

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
39
Which type of IDS automatically records information to a log?
A) Network-based
B) Host-based
C) Auditor
D) Inspector
A) Network-based
B) Host-based
C) Auditor
D) Inspector

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
40
Which passive intrusion-detection tool audits activities on multiple operating systems, filters them, and collects the information into one large database for analysis of intrusions?
A) loginlog
B) lsof
C) PreCis
D) RealSecure
A) loginlog
B) lsof
C) PreCis
D) RealSecure

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
41
In Mac OS X, which log contains information about printing activities?
A) /var/log/lookupd.log
B) /var/log/lpr.log
C) /var/log/secure.log
D) /var/log/system.log
A) /var/log/lookupd.log
B) /var/log/lpr.log
C) /var/log/secure.log
D) /var/log/system.log

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
42
What directory are the default logs kept in Red Hat Linux 9.x?
A) /etc/log
B) /var/log
C) /bin/log
D) /conf/log
A) /etc/log
B) /var/log
C) /bin/log
D) /conf/log

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
43
Does the Netware 6.x Console log contain error information recorded for the NetWare server?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
44
In event log, a warning that a CD-ROM is not loaded would be indicated by what type of symbol?
A) A blue "i" displayed in a white comment bubble
B) A black "!" that appears on a yellow caution symbol
C) A white "x" that appears inside a red circle
D) A red "x" that appears inside a white circle
A) A blue "i" displayed in a white comment bubble
B) A black "!" that appears on a yellow caution symbol
C) A white "x" that appears inside a red circle
D) A red "x" that appears inside a white circle

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
45
Are the Mac OS X logs located in the /var/log directory?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
46
In Netware 6.x, what directory contains the Audit log and the Console log?
A) SYS:NOVONYX\SUITESPOT\ADMIN-SERV\LOGS\
B) SYS:ETC\
C) SYS:VAR\
D) SYS:NOVONYX\SUITESPOT\LOGS\
A) SYS:NOVONYX\SUITESPOT\ADMIN-SERV\LOGS\
B) SYS:ETC\
C) SYS:VAR\
D) SYS:NOVONYX\SUITESPOT\LOGS\

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
47
Is the System Log in Mac OS X contained in the file messages.x?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
48
Are the Server logs for Mac OS X automatically rotated?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
49
In Window Server 2003, does the print$ share enable you to view the number of clients currently using the server as a print server?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
50
In Netware, in which directory are the Access log and the Error log kept?
A) SYS:NOVONYX\SUITESPOT\ADMIN-SERV\LOGS\
B) SYS:ETC\
C) SYS:VAR\
D) SYS:NOVONYX\SUITESPOT\LOGS\
A) SYS:NOVONYX\SUITESPOT\ADMIN-SERV\LOGS\
B) SYS:ETC\
C) SYS:VAR\
D) SYS:NOVONYX\SUITESPOT\LOGS\

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
51
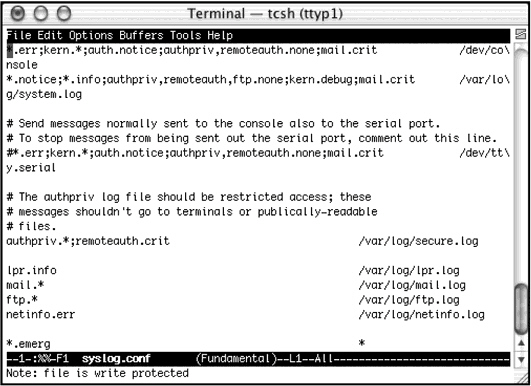 Which file is being edited in the figure above?
Which file is being edited in the figure above?A) netinfo log
B) lpr.log
C) syslog.conf
D) system.log

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
52
In the event log, a notice that a service has started would be indicated with what type of symbol?
A) A blue "i" displayed in a white comment bubble
B) A black "!" that appears on a yellow caution symbol
C) A white "x" that appears inside a red circle
D) A red "x" that appears inside a white circle
A) A blue "i" displayed in a white comment bubble
B) A black "!" that appears on a yellow caution symbol
C) A white "x" that appears inside a red circle
D) A red "x" that appears inside a white circle

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
53
Which command provides information about who is logged on to Red Hat Linux 9.x?
A) who
B) who am i
C) proc
D) login
A) who
B) who am i
C) proc
D) login

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
54
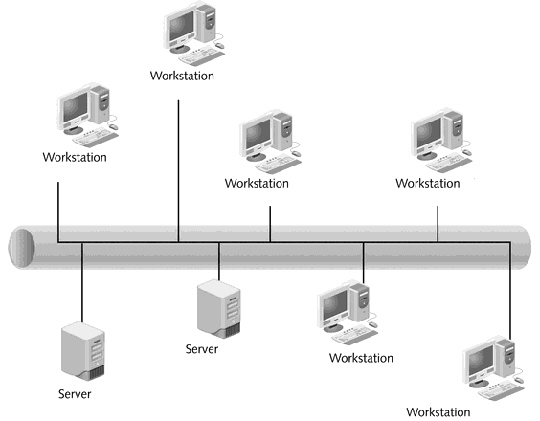 If a network administrator wants to use host-based intrusion detection, which devices in the figure above would need to be configured?
If a network administrator wants to use host-based intrusion detection, which devices in the figure above would need to be configured?A) Only the workstations
B) Only the servers
C) All workstations and servers
D) None of the workstations or servers

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
55
What utility can be used to clean up the Mac OS X Server logs?
A) MacJanitor
B) MacCleanUp
C) MacSweep
D) MacRotate
A) MacJanitor
B) MacCleanUp
C) MacSweep
D) MacRotate

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
56
Which Linux Red Hat 9.x "who" command option shows the amount of time each user process has been idle?
A) -a
B) -b
C) -i
D) -s
A) -a
B) -b
C) -i
D) -s

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
57
By default in Red Hat Linux 9.x , how many rotation levels does each log file have?
A) 2
B) 3
C) 4
D) 5
A) 2
B) 3
C) 4
D) 5

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
58
Which Network Monitor pane provides statistics about traffic from other computers on the network, including the MAC (device) address of each computer's NIC and data about the number of frames sent from and received by each computer?
A) Graph
B) Total Statistics
C) Session Statistics
D) Station Statistics
A) Graph
B) Total Statistics
C) Session Statistics
D) Station Statistics

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
59
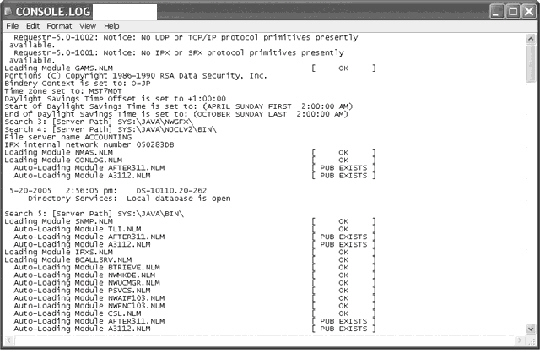 Which Netware 6.x log is displayed in the figure above?
Which Netware 6.x log is displayed in the figure above?A) Access
B) Audit
C) Module
D) Console

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
60
Which Network Monitor statistic shows total traffic in frames for broadcasts, unicasts, and multicasts?
A) % Network Utilization
B) Frames Per Second
C) Broadcasts Per Second
D) Muticasts Per Second
A) % Network Utilization
B) Frames Per Second
C) Broadcasts Per Second
D) Muticasts Per Second

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
61
At minimum, ____________________ intrusion detection alerts a server or network administrator about an attack or intrusion, so the administrator can take action.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
62
Does the Netware Remote Manager allow you to send messages to a particular user or to all users?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
63
In Windows 2000 Server, is it necessary to install Network Monitor and Network Monitor Driver separately?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
64
In Red Hat Linux, the ____________________ Log provides information about jobs that are scheduled to run or that have already run, such as information about the number of minutes until a specific job will run.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
65
List five third-party passive intrusion-detection tools.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
66
List four third-party active intrusion-detection tools.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
67
In Windows Server 2003, the ____________________ log records information about logon accesses and file, folder, and system policy changes.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
68
List eight different types of information that might be found in a log created by an auditor.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
69
What five activities are typically encompassed by host-based IDS?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
70
What five things do inspectors typically look for?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
71
Typically, an IDS ____________________ is software that automatically records information to a log.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
72
Can Network Monitor filter frames and packets on the basis of SAP or ETYPE?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
73
Is the Process Viewer used by Linux Red Hat 9.x to display a listing of processes and the users who are running those processes?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
74
Can the version of Network Monitor that comes with Windows Server 2003 capture and read the contents of any frames transported on the network segment to which the host computer is connected?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
75
Network-based intrusion-detection software is used on a computer or network device and typically places the NIC on that device in ____________________ mode.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
76
In Red Hat Linux, log files are managed through a process called ____________________ .

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
77
Host wrapper software, which may also be called a(n) ____________________, monitors network activity into or out of the computer, including protocols, packets, broadcasts, remote logon attempts, dial-in attempts, port scanning, and other activities.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
78
A(n) ____________________ is a command-line string issued remotely that is intended to weaken the security or to alter an operating system.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
79
A(n) ____________________ can be acquired by using performance monitoring to establish slow, average, and peak periods for a network, and keeping records on these periods.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
80
In Windows Server 2003, the ____________________ log records information about how software applications are performing.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck



