Deck 1: Operating Systems Security: Keeping Computers and Networks Secure
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/86
Play
Full screen (f)
Deck 1: Operating Systems Security: Keeping Computers and Networks Secure
1
Hardening involves taking specific actions to block or prevent attacks by means of operating system and network security methods.
True
2
WEP is a wireless communications authentication method.
True
3
NDS is a directory service used by Windows 2003 Server to provide a central listing of resources.
False
4
Remote access security involves requiring a user account and password to access a particular operating system or to be validated to access a network through a directory service.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
5
Strobe and Nmap are two popular port-scanning programs that are used to find open ports on a remote system.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
6
The Trojan horse program Trojan.Idly is designed to give the attacker command line access to the remote operating system.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
7
A(n) socket is like a virtual circuit between two services or processes communicating between two different computers or network devices.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
8
Using spoofing , an attacker can initiate access to a computer or can appear as just another transmission to a computer from a legitimate source that is already connected.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
9
Directories or folders and network printers are two important examples of resources that can be shared.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
10
Employing disaster recovery is vital when a hard disk is damaged or crashes and must be replaced.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
11
Attacks on wireless networks are sometimes called auto-jacks , because the attacker may drive around an area in a car, using a portable computer to attempt to pick up a wireless signal.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
12
Source routing attacks are used to interfere with normal access to a network host, Web site, or service by flooding a network with useless information.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
13
In the world of computers and networks, the operating system provides both the lock and the key to information.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
14
In LinkState routing, the sender of a packet specifies the precise path that the packet will take to reach its destination.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
15
Many systems use datasets to store data until it is ready to be used.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
16
The API is software that resides between the application software and the operating system kernel.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
17
When new operating system software is purchased, it should be tested rigorously for security and reliability.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
18
A MAN typically goes up to a distance of about 50 miles.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
19
Ping is a utility that network users and administrators frequently use to test a network connection.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
20
In order to successfully use logon security, users must be taught to keep their passwords confidential and to choose passwords that are difficult to guess.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
21
What type of attack occurs when the computer originating the attack causes several other computers to send attack packets?
A) Distributed denial of service
B) Dormant denial of service
C) Duplicated denial of service
D) Distributed destruction of service
A) Distributed denial of service
B) Dormant denial of service
C) Duplicated denial of service
D) Distributed destruction of service

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
22
Which of the following information about us should be kept private?
A) Family information
B) Employment information
C) Student information
D) Both a and b
E) a, b, and c
A) Family information
B) Employment information
C) Student information
D) Both a and b
E) a, b, and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
23
One WAN is composed of two or more LANs or MANs that are connected across a distance of more than approximately _____ miles.
A) 10
B) 30
C) 50
D) 100
A) 10
B) 30
C) 50
D) 100

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
24
The traceroute troubleshooting utility can be used by which of the following operating systems?
A) UNIX
B) Mac OS
C) Netware
D) Windows
E) All of the above
A) UNIX
B) Mac OS
C) Netware
D) Windows
E) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
25
_____ can translate an IP address from a private network to a different address used on a public network or the Internet.
A) Routers
B) Proxy servers
C) Network address translation
D) Packet filters
A) Routers
B) Proxy servers
C) Network address translation
D) Packet filters

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
26
Which of the following is part of the total cost of ownership of a computer network?
A) Hardware
B) Software
C) User support costs
D) Maintenance
E) All of the above
A) Hardware
B) Software
C) User support costs
D) Maintenance
E) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
27
Most of the first computer networks transmitted data over _____.
A) telephone lines
B) fiber optics
C) copper wires
D) frame relay
A) telephone lines
B) fiber optics
C) copper wires
D) frame relay

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
28
A _ ____ is software or hardware placed between two or more networks that selectively allows or denies access.
A) gateway
B) filter
C) firewall
D) DMZ
A) gateway
B) filter
C) firewall
D) DMZ

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
29
Operating system and network security is the ability to do which of the following reliably to information?
A) Store
B) Modify
C) Protect
D) Grant access to
E) All of the above
A) Store
B) Modify
C) Protect
D) Grant access to
E) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
30
According to a recent survey performed by the CSI, what percentage of computer security professionals have reported security breaches in their systems?
A) 50
B) 65
C) 80
D) 90
A) 50
B) 65
C) 80
D) 90

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
31
What type of attack has occurred when a logged-on computer is used when that person is not present?
A) Spoofing
B) Denial of service
C) Buffer
D) Standalone workstation
A) Spoofing
B) Denial of service
C) Buffer
D) Standalone workstation

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
32
Statistics from the CSI suggest that the number of people working as computer security professionals has been increasing by _____ percent a year since 1998.
A) 30
B) 50
C) 75
D) 100
A) 30
B) 50
C) 75
D) 100

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
33
A _____ attack is used to interfere with normal access to a network host, Web site, or service, by flooding a network with useless information or with frames or packets containing errors that are not identified by a particular network service.
A) virus
B) buffer
C) denial of service
D) port scanning
A) virus
B) buffer
C) denial of service
D) port scanning

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
34
Which of the following is a reason for the failure to fully use the security features of an operating system or network?
A) Lack of time
B) Inadequate training or knowledge of the features
C) A history of doing things only in a specific way
D) All of the above
A) Lack of time
B) Inadequate training or knowledge of the features
C) A history of doing things only in a specific way
D) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
35
The _____ translates information from the kernel and device drivers so the application can use it.
A) RPC
B) API
C) BIOS
D) resource manager
A) RPC
B) API
C) BIOS
D) resource manager

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
36
Which of the following is a cost of deploying security within an organization?
A) Testing security systems
B) Training users
C) Training consultants
D) Both a and b
E) Both a and c
A) Testing security systems
B) Training users
C) Training consultants
D) Both a and b
E) Both a and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
37
At a minimum, how many groups does training involve within an organization?
A) 1
B) 2
C) 3
D) 4
A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
38
What type of attack has occurred when an attacker gains access to a computer through the use of a hidden program?
A) Trojan horse
B) Buffer
C) Worm
D) Source routing
A) Trojan horse
B) Buffer
C) Worm
D) Source routing

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
39
_____ consists of a chain of activities that is necessary to complete a task, such as filling out and transmitting forms, entering data, updating databases, and creating new files.
A) Ensuring privacy
B) Workflow
C) Protecting information
D) Compensating for human error
A) Ensuring privacy
B) Workflow
C) Protecting information
D) Compensating for human error

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
40
In a source routing attack, the attacker modifies the _____ and routing information to make a packet appear to come from a different source, such as one that is already trusted for communications on a network.
A) destination address
B) source address
C) destination header
D) source data
A) destination address
B) source address
C) destination header
D) source data

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
41
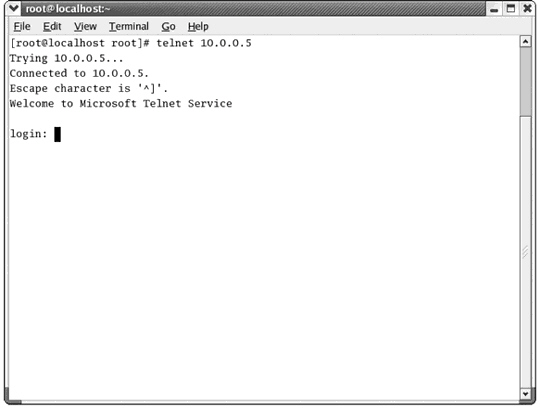 What application protocol is being used in the figure above?
What application protocol is being used in the figure above?A) TCP
B) Telnet
C) Ping
D) Traceroute

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
42
Do the operating system device drivers coordinate operating system functions such as control of memory and storage?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
43
A _____ is a fundamental component or container that holds information about all network resources that are grouped within it.
A) workgroup
B) directory service
C) domain
D) forest
A) workgroup
B) directory service
C) domain
D) forest

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
44
Using _____, an attacker can initiate access to a computer or can appear as just another transmission to a computer from a legitimate source that is already connected.
A) buffering
B) denial of service
C) worms
D) spoofing
A) buffering
B) denial of service
C) worms
D) spoofing

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
45
How many ports are there in UDP and TCP?
A) 6,550
B) 63,353
C) 65,535
D) 165,550
A) 6,550
B) 63,353
C) 65,535
D) 165,550

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
46
Which of the following is a key element used in a wireless attack?
A) Omnidirectional antenna
B) Wireless NIC
C) Passwords
D) Only a and b
E) a, b, and c
A) Omnidirectional antenna
B) Wireless NIC
C) Passwords
D) Only a and b
E) a, b, and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
47
Is using the monitoring software that comes with an operating system one of the best places to start when determining the performance and use of an operating system or network?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
48
Should security or system patches be installed immediately upon their release?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
49
What port does DNS use?
A) 21
B) 23
C) 53
D) 110
A) 21
B) 23
C) 53
D) 110

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
50
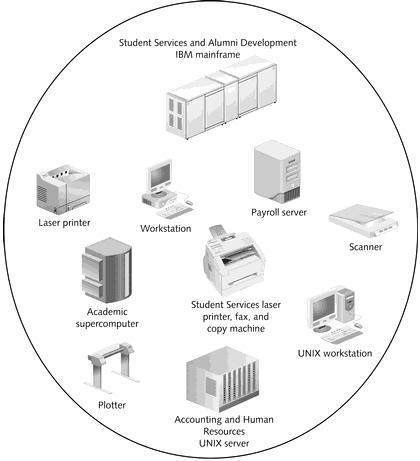 What is displayed in the figure above?
What is displayed in the figure above?A) Resources in a LAN
B) Resources in a WAN
C) Resources in a MAN
D) Resources in an enterprise network

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
51
In Linux, account security characteristics are controlled through the _____ file, which is normally available only to the system administrator.
A) /etc/shadow
B) /bin/shadow
C) /etc/hosts
D) /etc/passwd
A) /etc/shadow
B) /bin/shadow
C) /etc/hosts
D) /etc/passwd

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
52
What port do Telnet applications use for communication?
A) 20
B) 21
C) 23
D) 25
A) 20
B) 21
C) 23
D) 25

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
53
Callback security is an example of _____ security
A) filtering
B) remote access
C) object
D) user level
A) filtering
B) remote access
C) object
D) user level

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
54
Which organization was started by Coopers and Lybrand as the European Security Forum?
A) Forum of Incident Response and Security Teams
B) SysAdmin, Audit, Network, Security Institute
C) Information Security Forum
D) National Security Institute
A) Forum of Incident Response and Security Teams
B) SysAdmin, Audit, Network, Security Institute
C) Information Security Forum
D) National Security Institute

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
55
Is the goal of disaster recovery to enable you to restore systems and data without losing critical information?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
56
 Which of the following components are found in section A in the figure above?
Which of the following components are found in section A in the figure above?A) Word processors
B) Device drivers
C) Resource managers
D) Disk drives
E) APIs

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
57
What type of port might be used during a port-scanning attack?
A) Serial
B) Parallel
C) UDP
D) USB
A) Serial
B) Parallel
C) UDP
D) USB

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
58
Which organization offers training in security needs and hosts the Certified Protection Professional certification?
A) Computer Emergency Response Team Coordination Center
B) InfraGard
C) Information Systems Security Association
D) American Society for Industrial Security
A) Computer Emergency Response Team Coordination Center
B) InfraGard
C) Information Systems Security Association
D) American Society for Industrial Security

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
59
Do all networks have vulnerable points that require security?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
60
Attackers may get through a specific NAT device by using a form of source routing called _____.
A) a macro
B) spoofing
C) loose source record route
D) multiplexing
A) a macro
B) spoofing
C) loose source record route
D) multiplexing

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
61
Which three NLMs enable a workstation to remotely access the Netware system console?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
62
Is a virus hoax a virus?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
63
Once an attacker has found available IP addresses, they may then run ____________________ software to find a system on which a key port is open or not in use.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
64
____________________ is a TCP/IP protocol that provides terminal emulation services over a network or the Internet.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
65
List six features that operating systems provide for hardening a system.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
66
One way to help reduce the _________________________ is to purchase systems that are designed to work together in an environment that enables easier and faster configuration.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
67
The ____________________ allows you to set a password that governs access to the hard disk drive.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
68
A(n) ____________________ is ideal for providing security because it takes care of the computer's most basic input/output functions.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
69
Does a locked computer operations room guarantee the protection of a network server?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
70
Will a security policy help to overcome the human factors that diminish security in an organization?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
71
List five organizations that provide information, assistance, and training in types of system attacks and how to prevent them.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
72
A key characteristic of a(n) ____________________ network is the availability of different resources that enable users to fulfill business, research, and educational tasks.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
73
Is the cost of deploying security more expensive than the cost of not deploying security?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
74
List four hardening techniques that can be used with networks.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
75
____________________ security policies can often help to override politics that limit good security in an organization.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
76
In operating systems, the built-in ____________________ account is typically deactivated or has a password.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
77
List five types of VPN security that can be provided by operating systems.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
78
Do users need training in the use of security tools to help limit human failure and neglect?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
79
The ____________________ communicates with the BIOS, device drivers, and the API to perform operating system functions such as control of memory and storage.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
80
A(n) ____________________ attack is typically intended to shut down a site or service but does not usually damage information or systems.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck



