Deck 2: Viruses, Worms, and Malicious Software
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/86
Play
Full screen (f)
Deck 2: Viruses, Worms, and Malicious Software
1
Organizational policy works best when users are included in the process, so that they know the importance of security.
True
2
In Netware, the startup.ncf file contains commands used by the server.exe startup program.
True
3
A(n) stealth virus uses defenses to make itself hard to find and detect.
True
4
The W32.Pinfi virus is an example of a destructive virus that can infect Mac OS systems.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
5
The Digispid.B. Worm targets systems running the SQL Server database on Windows-based workstations and servers.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
6
Cookie snarfing is an attack where a spyware operator can reconstruct a user's every move on the Internet by capturing cookies or the information contained in the cookies.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
7
Windows 2000 Server allows you to create an ERD, which enables you to fix problems that may arise with the server, such as corrupted system files.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
8
The Netware 6.x operating system has a software update tool that connects to the Internet to obtain patches.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
9
A(n) macro virus, worm, or Trojan horse is a file that contains lines of computer code that can be run.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
10
The first stage of virus spread that occurs is replication within the infected system.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
11
Boot or partition sector viruses particularly affect Windows and Netware systems.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
12
Batch files and scripts are files that contain code or instructions that are run by a(n) interpreter .

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
13
Software exploitation is particularly aimed at new software and new software versions.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
14
File infector viruses can infect systems through multiple means, particularly through boot or partition sectors and through executable files.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
15
A(n) boot sector virus typically infects or replaces the instructions in the MBR or the Partition Boot Sector.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
16
A benign virus is one that replicates but does not inflict harm on a computer.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
17
Backdoor.Egghead is an example of a worm that is spread by buffer overflows.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
18
Mac OS and NetWare automatically display the boot load information to the screen each time one of these systems is booted.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
19
The Windows 2003 Server ASR set backs up all system files, system settings, and application data files.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
20
The Code Red worm replicates for the first 23 days of the month and then stops.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
21
A(n) _____ virus uses defenses to make itself hard to find and detect.
A) polymorphic
B) stealth
C) companion
D) heuristic
A) polymorphic
B) stealth
C) companion
D) heuristic

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
22
Which anti-virus software is available for use on Macintosh, NetWare, UNIX/Linux, and Windows-based systems?
A) AntiVir Personal Edition
B) HandyBits VirusScan
C) McAfee VirusScan
D) Sophos Anti-Virus
A) AntiVir Personal Edition
B) HandyBits VirusScan
C) McAfee VirusScan
D) Sophos Anti-Virus

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
23
How many copies of the ASR set should you have for a server?
A) 1
B) 2
C) 3
D) 4
A) 1
B) 2
C) 3
D) 4

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
24
What do you need to have for Red Hat Linux if a system file on the hard disk is corrupted?
A) An ERD
B) An ASR set
C) A boot disk
D) An MBR
A) An ERD
B) An ASR set
C) A boot disk
D) An MBR

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
25
A _____ virus appends to program files such as system files, executable files, driver files, and supplementary files, including .dlls.
A) partition sector
B) file infector
C) macro
D) multipartite
A) partition sector
B) file infector
C) macro
D) multipartite

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
26
A _____ virus can infect systems through multiple means, particularly through boot or partition sectors and through executable files.
A) boot sector
B) multipartite
C) macro
D) file infector
A) boot sector
B) multipartite
C) macro
D) file infector

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
27
Which anti-virus software is available for use on only Windows and Mac OS systems?
A) Central Command Vexira AntiVirus
B) F-Prot AV
C) Norton AntiVirus
D) McAfee VirusScan
E) Both c and d
A) Central Command Vexira AntiVirus
B) F-Prot AV
C) Norton AntiVirus
D) McAfee VirusScan
E) Both c and d

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
28
Which of the following operating systems uses an emergency repair disk?
A) Windows 2000 Server
B) Windows 2000 Pro
C) Windows XP Pro
D) Windows 2003 Server
E) Both a and b
A) Windows 2000 Server
B) Windows 2000 Pro
C) Windows XP Pro
D) Windows 2003 Server
E) Both a and b

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
29
A(n) _____ virus appears to run from a file other than the one to which it is actually appended.
A) stealth
B) armored
C) polymorphic
D) companion
A) stealth
B) armored
C) polymorphic
D) companion

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
30
In Red Hat Linux, what command do you need to use to create a boot disk?
A) mkboot
B) makebootdisk
C) mkbootdisk
D) makebtdsk
A) mkboot
B) makebootdisk
C) mkbootdisk
D) makebtdsk

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
31
The _____ virus can only become destructive if the user executes an infected file on a Friday the thirteenth.
A) Linux.Millen.Worm
B) INIT 1984
C) W32.Pinfi
D) Code Red II
A) Linux.Millen.Worm
B) INIT 1984
C) W32.Pinfi
D) Code Red II

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
32
What process does the Linux.Millen.Worm use on the attacked operating system?
A) Telnet
B) FTP
C) DNS
D) SMTP
A) Telnet
B) FTP
C) DNS
D) SMTP

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
33
Which of the following worms uses buffer overflows to do damage?
A) Code Red
B) Code Red II
C) Linux.Millen.Worm
D) Both a and b
E) a, b, and c
A) Code Red
B) Code Red II
C) Linux.Millen.Worm
D) Both a and b
E) a, b, and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
34
_____ is designed so that it does not infect all of these file types at once, but only a limited number each time Windows Explorer runs.
A) INIT 1984
B) Code Red
C) Slammer worm
D) W32.Pinfi
A) INIT 1984
B) Code Red
C) Slammer worm
D) W32.Pinfi

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
35
A _____ virus spreads to instruction set files typically used by word processors, spreadsheets, databases, and other programs.
A) boot sector
B) file infector
C) macro
D) multipartite
A) boot sector
B) file infector
C) macro
D) multipartite

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
36
A(n) _____ virus changes each time it is replicated, making it more difficult to create a defense against it.
A) armored
B) multipartite
C) polymorphic
D) heuristic
A) armored
B) multipartite
C) polymorphic
D) heuristic

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
37
Which of the following virus programs is available for purchase on a Windows-based workstation?
A) AntiVir Personal Edition
B) Handybits Viruscan
C) VCatch Basic
D) Sophos Anti-virus
E) Both b and d
A) AntiVir Personal Edition
B) Handybits Viruscan
C) VCatch Basic
D) Sophos Anti-virus
E) Both b and d

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following Microsoft operating systems uses driver signing?
A) Windows XP
B) Windows ME
C) Windows 98
D) Windows 95
E) Both a and c
A) Windows XP
B) Windows ME
C) Windows 98
D) Windows 95
E) Both a and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
39
How many days of the month does the Code Red worm replicate?
A) 15
B) 19
C) 23
D) 29
A) 15
B) 19
C) 23
D) 29

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
40
What is another name for malicious software?
A) malsoft
B) malware
C) scriptware
D) scriptsoft
A) malsoft
B) malware
C) scriptware
D) scriptsoft

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
41
Which of the following is an example of a Trojan horse on a Mac OS system?
A) Simpsons AppleScript Virus
B) AOL4FREE
C) Backdoor.Egghead
D) Code Red
A) Simpsons AppleScript Virus
B) AOL4FREE
C) Backdoor.Egghead
D) Code Red

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
42
In Red Hat Linux, what mode do you need to be in to run the fdisk/mbr utility which replaces the MBR?
A) Safe
B) Rescue
C) Recovery
D) MBR
A) Safe
B) Rescue
C) Recovery
D) MBR

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
43
How was the Melissa virus transported?
A) File sharing
B) Floppy disk
C) Buffer overflow
D) E-mail
A) File sharing
B) Floppy disk
C) Buffer overflow
D) E-mail

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
44
Which of the following executable file extensions is found only on Windows-based systems?
A) )mst
B) )msi
C) )msp
D) )btm
E) All of the above
A) )mst
B) )msi
C) )msp
D) )btm
E) All of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
45
Which of the following is an example of a Red Hat Linux file that can be the target of a virus?
A) autoexec.bat
B) inittab
C) startup.ncf
D) win.ini
A) autoexec.bat
B) inittab
C) startup.ncf
D) win.ini

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
46
Can the VCatch Basic Anti-virus program be used both in Windows and Linux environments?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
47
Is Sophos Anti-virus free software that can be used in Macintosh, Netware, UNIX/Linux, and Windows-based systems?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
48
Which of the following is notorious for enabling cookie snarfing?
A) SpyNet
B) PeepNet
C) Cookienet
D) Both a and b
E) a, b, and c
A) SpyNet
B) PeepNet
C) Cookienet
D) Both a and b
E) a, b, and c

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
49
Which file on a Windows-based system is run when a system is booted, and can be used to rename specific files at startup?
A) win.ini
B) autoexec.bat
C) wininit.ini
D) winstart.bat
A) win.ini
B) autoexec.bat
C) wininit.ini
D) winstart.bat

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
50
With which attachment was the Resume virus associated?
A) Explorer.exe
B) Explorer.msi
C) Explorer.doc
D) Explorer.com
A) Explorer.exe
B) Explorer.msi
C) Explorer.doc
D) Explorer.com

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
51
Is one advantage of a digital signature that it helps ensure the security of your system by allowing only drivers and system files that have been verified by Microsoft?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
52
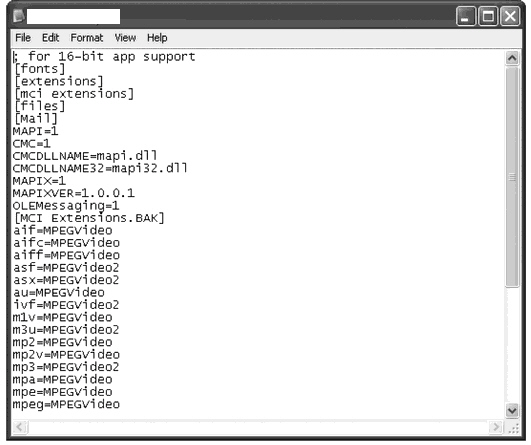 What is displayed in the figure above?
What is displayed in the figure above?A) A bashrc file in Red Hat Linux
B) A win.ini file in Windows XP
C) A startup.ncf file in Netware
D) The kernel file in Mac OS X

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
53
Which of the following executable file extensions can be found on a Netware 6.x system?
A) )pl
B) )msi
C) )wsf
D) )bin
A) )pl
B) )msi
C) )wsf
D) )bin

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
54
Which of the following is an example of a Netware 6.x file that can be the target of a virus?
A) autoexec.bat
B) startup.ncf
C) win.ini
D) Both a and b
A) autoexec.bat
B) startup.ncf
C) win.ini
D) Both a and b

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
55
Does Windows 2000 use an ASR set to recover from a system failure?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
56
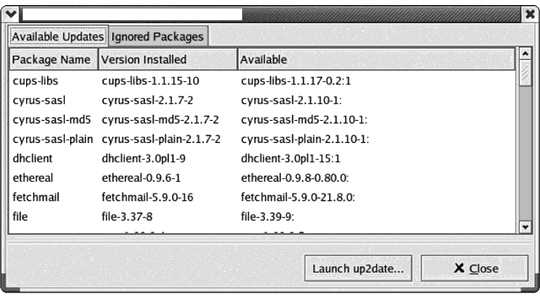 What is displayed in the figure above?
What is displayed in the figure above?A) Windows Update Setup Wizard
B) Red Hat Network Alert Notification Tool
C) Mac OS X Software Update Tool
D) None of the above

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
57
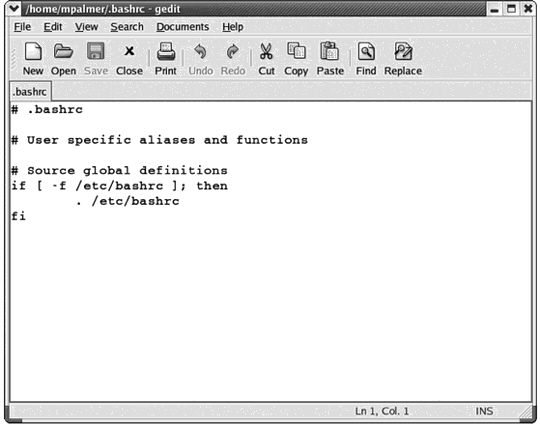 Which of the following operating systems would use the commands listed in the figure above?
Which of the following operating systems would use the commands listed in the figure above?A) Windows XP
B) Netware 6.x
C) Red Hat Linux
D) Mac OS X

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
58
What was one reason the Slammer worm was successful against SQL Server database servers in early 2003?
A) It gained access through a previously unknown vulnerability in SQL server
B) Many administrators had not installed new patches designed to block this attack
C) It was a polymorphic worm that rapidly changed signatures
D) It was a stealth worm that was difficult to detect
A) It gained access through a previously unknown vulnerability in SQL server
B) Many administrators had not installed new patches designed to block this attack
C) It was a polymorphic worm that rapidly changed signatures
D) It was a stealth worm that was difficult to detect

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
59
The _____ targets systems running the SQL Server database on Windows-based workstations and servers.
A) Digispid.B.Worm
B) Linux.Millen.Worm
C) Linux.Lion.Worm
D) Code Red II Worm
A) Digispid.B.Worm
B) Linux.Millen.Worm
C) Linux.Lion.Worm
D) Code Red II Worm

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
60
Should you create a new ASR set each time you add a protocol or install a new driver for a network interface card?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
61
Viruses, worms, and Trojan horses all represent malicious software that use _________________________ to find weaknesses or holes in operating systems and networks.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
62
Typically, eradicating boot or partition sector viruses involves recreating the ____________________ and Partition Boot Sector instructions.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
63
What is a destructive virus?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
64
Windows XP Professional and Windows Server 2003 come with the ____________________ Setup Wizard which is designed to help you remember to obtain new updates, or even to obtain them for you.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
65
One way to spread a(n) ____________________ virus is to attach it to a template that many users share, enabling it to spread each time the template is opened in a new document.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
66
____________________ may operate without being installed on a user's computer by capturing information related to the user's Internet communications.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
67
In its destructive mode, will the INIT 1984 virus rename files using random characters and delete files on hard drives?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
68
A(n) ____________________ is a program that replicates and replicates on the same computer, or one that sends itself to many other computers on a network or the Internet.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
69
____________________ are one of the most vulnerable points of attack in an organization.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
70
Does the AOL4FREE e-mail hoax contain the AOL4FREE.com attachment?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
71
In the ____________________ operating system, you can display the boot process by booting into either single user mode or verbose mode.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
72
Does an organizational policy work best if users are not included in the policy creation process?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
73
The ____________________ virus did not destroy data, but instead inserted the following line in the virus-carrying document when it was opened: "Twenty-two points, plus triple-word-score, plus fifty points for using all my letters. Game's over. I'm outta here."

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
74
What are the six typical methods used in malicious software attacks?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
75
Viruses can be classified by the way they protect themselves from detection or from a virus scanner. List the four classifications.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
76
Can a boot or partition sector virus corrupt the address of the primary partition that is specified in the partition table of a disk?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
77
Code Red and Code Red II use a buffer overflow to attack weaknesses in ____________________ Services on Microsoft servers.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
78
One way to classify viruses is by how they infect systems. List the four different classifications.

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
79
Is Windows the only operating system that is vulnerable to a macro virus?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck
80
What is a benign virus?

Unlock Deck
Unlock for access to all 86 flashcards in this deck.
Unlock Deck
k this deck



