Deck 1: Blue Coat Certified ProxySG Administrator
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/135
Play
Full screen (f)
Deck 1: Blue Coat Certified ProxySG Administrator
1
The default policy for ProxySG is DENY. Network administrator creates a VPM policy allowing access to some Web host only for certain users (see picture). When installing this policy, ProxySG issues a warning that this rule will be ignored. What change can be applied in order to fix this? 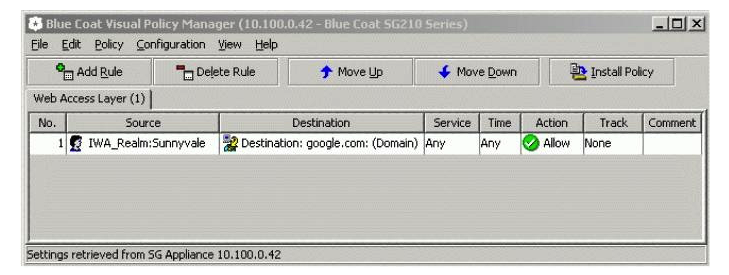
A) Add another rule to the Web Access layer creating an exception for users NOT allowed to access the host.
B) Add another Web Access layer and set its default action to Allow.
C) Add Web Authentication layer with a rule having Force Authenticate action.
D) Add Web content layer with a rule preventing serving content from ProxySG cache to unauthorized users.

A) Add another rule to the Web Access layer creating an exception for users NOT allowed to access the host.
B) Add another Web Access layer and set its default action to Allow.
C) Add Web Authentication layer with a rule having Force Authenticate action.
D) Add Web content layer with a rule preventing serving content from ProxySG cache to unauthorized users.
C
2
A ProxySG is designed to do which of the following? (Choose all that apply) (a) Enhance security through authentication, virus scanning, and logging. (b) Increase performance through TCP optimization, HTTP caching and pipelining. (c) Control content with URL filtering, content stripping, and HTTP header analysis.
A) a & b only
B) b & c only
C) a & c only
D) All of the above
A) a & b only
B) b & c only
C) a & c only
D) All of the above
D
3
What can be concluded about this request processing order?
A) ProxyAV Is accessed in ICAP REQMOD mode
B) ProxyAV is accessed ICAP RESPMOO mode
C) ProxySG with ProxyAV is deployed as a forward proxy
A) ProxyAV Is accessed in ICAP REQMOD mode
B) ProxyAV is accessed ICAP RESPMOO mode
C) ProxySG with ProxyAV is deployed as a forward proxy
A
4
Forward proxy of SSL allows applying policies to encrypted SSL data.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
5
What acceleration techniques are NOT part of MACHS?
A) Bandwidth management (traffic shaping)
B) Protocol optimization and compression
C) IP layer route optimization
D) Object caching
E) Byte caching
A) Bandwidth management (traffic shaping)
B) Protocol optimization and compression
C) IP layer route optimization
D) Object caching
E) Byte caching

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
6
Which ProxySG technology uses the data processing pipeline similar to the one shown in the picture? 
A) Blue Coat Reporter
B) MACH5
C) BCWF
D) ProxySG Services

A) Blue Coat Reporter
B) MACH5
C) BCWF
D) ProxySG Services

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
7
Which of the following Authentication Realms are supported by Blue Coat in SGOS 5.3? (Choose all that apply) (a) IWA (b) RADIUS (C) LDAP (d) TACACS+
A) a, b & d only
B) b, c & d only
C) a, b &c only
D) All of the above
A) a, b & d only
B) b, c & d only
C) a, b &c only
D) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
8
A single ProxySG appliance can act as a Gateway Proxy and WAN Acceleration Proxy at the same time.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
9
An administrator created a PIN for the ProxySG front panel, disabled the built-in administrative account and introduced policy-based admin authoritarian, and secured die serial port. After this was done, all the PINs, passwords and policy settings were lost. What options are available to regain access to the appliance? (Choose all that apply) (a) Return ProxySG appliance to Blue Coat to restore a default SGCS image (b) Restore the factory settings by pressing and holding a reset button for 5 seconds, configure the appliance anew or restore its configuration from a backup (c) Try out all 10000 combinations of PIN for the front panel until you find the right one (d) Remove the hard disk from the ProxySG, connect it as an external SAT A disk to any Windows or Linux computer; clear the admin entry in the /etc/ pssswd file on that disk. Put the hard disk back in ProxySG, start it up and reset the admin's password.
A) a only
B) a & b only
C) a & c only
D) a & d only
E) All of the above
A) a only
B) a & b only
C) a & c only
D) a & d only
E) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
10
Which option is NOT available to upload logfiles from ProxySG?
A) HTTP server
B) FTP server
C) Blue Coat Reporter server
D) CIFS/SAMBA file server
A) HTTP server
B) FTP server
C) Blue Coat Reporter server
D) CIFS/SAMBA file server

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
11
The Connect HTTP method is reserved for use with a proxy that can dynamically switch to being a tunnel (e.g. SSL tunneling)

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
12
Which of the following types of traffic are not scanned with ICAP REQMOD?
A) HTTP PUT data
B) FTP uploads
C) FTP responses
D) HTTP POST data
A) HTTP PUT data
B) FTP uploads
C) FTP responses
D) HTTP POST data

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
13
In SGOS 5.3, what are the two versions that you can opt for? (Choose all that apply) (a) Proxy Edition (b) Full Edition (c)WAN Opt Edition (d) MACH5 Edition
A) b & c only
B) a, c & d only
C) c & d only
D) a & d only
A) b & c only
B) a, c & d only
C) c & d only
D) a & d only

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
14
Which is NOT a support- related site for Blue Coat products?
A) http://forums.bluecoot.com
B) http://services.bluecoat.com
C) http://download.bluecoat.com
D) http://webpulse.bluecoat.com
A) http://forums.bluecoot.com
B) http://services.bluecoat.com
C) http://download.bluecoat.com
D) http://webpulse.bluecoat.com

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
15
Which of the following methods is NOT appropriate for the initial setup for a ProxySG 2010 series?
A) Serial console Cable
B) LCD Panel
C) Web Wizard accessing HTTPS port 8083
D) Blue Coat Director applying a profile
A) Serial console Cable
B) LCD Panel
C) Web Wizard accessing HTTPS port 8083
D) Blue Coat Director applying a profile

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
16
What are the types of challenges that can be authenticated by ProxySG? (Choose all that apply) (a) Administrator attempts to access Management console (b) user attempts to access the internet (c) Administrator attempts to access SG via SSH (d) User attempts to access a CIFS file server
A) All of the above
B) b, c &d only
C) a, c & d only
D) a, b & c only
A) All of the above
B) b, c &d only
C) a, c & d only
D) a, b & c only

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
17
Which streaming services are supported by ProxySG?
A) QuickTime, Windows Media, and Real Media
B) Windows Media, Real Media, and Flash
C) QuickTime, Flash, and MP4
A) QuickTime, Windows Media, and Real Media
B) Windows Media, Real Media, and Flash
C) QuickTime, Flash, and MP4

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
18
The ProxySG gives you the ability to write policies through.
A) the graphical visual Policy Manager and/or the command-line interface
B) Visual Policy Manager only
C) the graphical visual Policy Manager, the command-line interface and/or imported text file
A) the graphical visual Policy Manager and/or the command-line interface
B) Visual Policy Manager only
C) the graphical visual Policy Manager, the command-line interface and/or imported text file

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
19
What are the possible configurable options when configuring destination address in proxy services? (Choose all that apply) (a) All (b) Any (c) Explicit (d) Transparent
A) a, c & d only
B) a, b & c only
C) b, c &d only
D) All of the above
A) a, c & d only
B) a, b & c only
C) b, c &d only
D) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
20
The goal of creating and using Notify User objects is (Choose all that apply) (a) to deny access to a URL (b) to deliver a splash page to the clients (c) to warn a user before allowing access to a URL
A) a & b only
B) b & c only
C) All of the above
A) a & b only
B) b & c only
C) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
21
Which best describes the role of a proxy server?
A) A device that inspects Layer 2 - Layer 4 traffic running through it and denies or permits based on a set of policies.
B) An intermediary program, which acts as both a server and a client for the purpose of making requests on behalf of other clients.
C) An intermediary program that protects the resources of a private network from users on other networks.
D) A device that extracts the destination address of a packet, selects ten best path for the packet and forwards the packet the next device in the path.
A) A device that inspects Layer 2 - Layer 4 traffic running through it and denies or permits based on a set of policies.
B) An intermediary program, which acts as both a server and a client for the purpose of making requests on behalf of other clients.
C) An intermediary program that protects the resources of a private network from users on other networks.
D) A device that extracts the destination address of a packet, selects ten best path for the packet and forwards the packet the next device in the path.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
22
If an error occurs during Proxy AV request or response processing, which of the following will occur?
A) The connection will be allowed
B) The connection will be denied
C) The response is determined by the ICAP object properties in policy
D) The response is determined by the ICAP configuration properties in the management console
A) The connection will be allowed
B) The connection will be denied
C) The response is determined by the ICAP object properties in policy
D) The response is determined by the ICAP configuration properties in the management console

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
23
The ProxySG acts as both an ICAP client and ICAP server.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
24
What is in NTLM Type 2 Message?
A) Domain + Workstation Name
B) Challenge for the Client
C) Usemame and Password
D) Client Response for the challenge
A) Domain + Workstation Name
B) Challenge for the Client
C) Usemame and Password
D) Client Response for the challenge

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
25
Which protocol and port is used by Blue Coat Reporter service to display results?
A) HTTP port 8987
B) HTTP port 8443
C) FTP port 8021
D) SNMP port 161
A) HTTP port 8987
B) HTTP port 8443
C) FTP port 8021
D) SNMP port 161

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
26
Which of the following console services are enabled by default? (Choose all that apply) (a) HTTP port 8081 (b) HTTPS port 8082 (c) HTTPS port 8083 (d) SSH port 22
A) a & c only
B) b & d only
C) c & d only
D) a & b only
A) a & c only
B) b & d only
C) c & d only
D) a & b only

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
27
Which of the following policies can be applied to Instant Messaging traffic? (Choose all that apply) (a) A policy to deny the transfer of specific file types or file sizes (b) A policy to deny a specific IM request method (c) A policy to deny a key word or words using a regular expression (d) A policy to deny a specific IM buddy or IM chat room
A) a, b & c only
B) b, c & d only
C) a, c & d only
D) All of the above
A) a, b & c only
B) b, c & d only
C) a, c & d only
D) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
28
HTTP/1.1 supports pipelining - multiple related requests are written to a single TCP socket without waiting for the responses to come back - i.e. the requests are done asynchronously in-parallel, instead of doing them sequentially as usual (see picture). Some Web clients such as Opera and Firefox with FasterFox plugin use HTTP pipelining. Assume that ProxySG Is deployed as a forward proxy listening on port 8080.
A) If an HTTP client tries to use pipelining, the use of proxy will break the HTTP protocol.
B) For those HTTP clients that use pipelining, the use of forward proxy would ensure faster response time compared to the clients that do not use pipelining.
A) If an HTTP client tries to use pipelining, the use of proxy will break the HTTP protocol.
B) For those HTTP clients that use pipelining, the use of forward proxy would ensure faster response time compared to the clients that do not use pipelining.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
29
What is the default time to cache authentication credentials in ProxySG for an authentication realm?
A) 15 minutes
B) 30 minutes
C) 60 minutes
D) 90 minutes
A) 15 minutes
B) 30 minutes
C) 60 minutes
D) 90 minutes

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
30
What ProxySG appliance has these default settings? (a) Default policy is ALLOW (b) Trust client destination IP is ON (c) Tolerate HTTP errors is ON;
A) Proxy Edition
B) Reverse Proxy Edition
C) MACH5 Edition
D) Trial Edition
A) Proxy Edition
B) Reverse Proxy Edition
C) MACH5 Edition
D) Trial Edition

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
31
To implement ProxySG as a default gateway, which of the following options has to be enabled?
A) Early intercept
B) Reflect Client IP
C) IP Forwarding
D) Detect Protocol
A) Early intercept
B) Reflect Client IP
C) IP Forwarding
D) Detect Protocol

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
32
When the ProxySG 200's power LED indicator alternates between green and amber, it means that the system is booting.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
33
A parent exception can provide the default values for a child exception.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
34
What happens to ProxySG logging, when uploading them to a remote FTP server becomes impossible?
A) When there is no more space for logging, ProxySG switches on dynamic bypass for TCP connections - stops intercepting traffic
B) When there is no more space for logging, ProxySG will process policy, but will ignore any logging-related policies or configuration settings
C) ProxySG erases old logs but continues writing the more recent ones
D) Either logging stops or older log files are erased - depending on the ProxySG configuration
A) When there is no more space for logging, ProxySG switches on dynamic bypass for TCP connections - stops intercepting traffic
B) When there is no more space for logging, ProxySG will process policy, but will ignore any logging-related policies or configuration settings
C) ProxySG erases old logs but continues writing the more recent ones
D) Either logging stops or older log files are erased - depending on the ProxySG configuration

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
35
After the initial boot-up. Blue Coat SGOS will automatically boot into a trial license. What is the duration of that period?
A) 30 days - trial can be prolonged by CLI command reset-trial
B) 60 days-trial can be prolonged by CU command reset-trial
C) 90 days
D) 120 days
A) 30 days - trial can be prolonged by CLI command reset-trial
B) 60 days-trial can be prolonged by CU command reset-trial
C) 90 days
D) 120 days

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
36
What is true immediately after the initial setup of ProxySG?
A) None of the content filtering databases is set up
B) Only the default Blue Coat WebFilter database is set up and available
C) Blue Coat WebFilter database and 3rd party databases are set up and available
A) None of the content filtering databases is set up
B) Only the default Blue Coat WebFilter database is set up and available
C) Blue Coat WebFilter database and 3rd party databases are set up and available

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
37
What is returned to the HTTP request" GET / HTTP/ 1.1 "?
A) The listing of the webroot directory of the Web server
B) The file index.html
C) A file that is configured as a default/welcome file for that Web server
A) The listing of the webroot directory of the Web server
B) The file index.html
C) A file that is configured as a default/welcome file for that Web server

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
38
Which HTTP error code corresponds to the ProxySG default exception identifier icap_error?
A) 403
B) 404
C) 503
D) 401
A) 403
B) 404
C) 503
D) 401

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
39
Which software product provides Web content filtering for windows and Mac OS computers, is locally configurable, and can produce a barking sound, when user violates a filtering policy.
A) ProxyAV
B) Blue coat WebFilter
C) Blue Coat k9
D) Blue Coat Director
A) ProxyAV
B) Blue coat WebFilter
C) Blue Coat k9
D) Blue Coat Director

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
40
What are "unmanaged endpoints' which make the Blue Coat RA (Remote Access) appliance useful?
A) TCP connection sources or destinations, which are outside our LAN
B) Workstations, which need to be in a virtual private network, but VPN clients cannot be installed on them
C) Mobile user laptops, which are used in places not protected by ProxySG
D) Hosts without installed ProxyClient or with disabled ProxyClient
A) TCP connection sources or destinations, which are outside our LAN
B) Workstations, which need to be in a virtual private network, but VPN clients cannot be installed on them
C) Mobile user laptops, which are used in places not protected by ProxySG
D) Hosts without installed ProxyClient or with disabled ProxyClient

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
41
Blue coat Director functions include the following (Choose all that apply) (a) Provide centralized initial setup and policy management (b) Configure secure gateway and WAN acceleration (c) Monitor hardware and software metrics and events on ProxySG appliances (d) Enable proxying and filtering of multicast UDP traffic
A) a, b & c only
B) a, b & d only
C) a, c & d only
D) b, c & d only
A) a, b & c only
B) a, b & d only
C) a, c & d only
D) b, c & d only

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
42
What are 'unmanaged endpoints" which make the ProxyRA appliance useful?
A) TCP connection sources of destinations, which are outside our LAN
B) Workstations, which need to be in a virtual private network, but VPN clients cannot be installed on them
C) TCP and UDP ports that are unprotected by the enterprise firewall.
D) Hosts without ProxyClient installed on them.
A) TCP connection sources of destinations, which are outside our LAN
B) Workstations, which need to be in a virtual private network, but VPN clients cannot be installed on them
C) TCP and UDP ports that are unprotected by the enterprise firewall.
D) Hosts without ProxyClient installed on them.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
43
Which function is NOT a characteristic feature of proxy servers?
A) Making requests in the Internet, using HTTP, FTP, SOCKS on behalf of other clients
B) IP Masquerading - replacing original requestor's address with it's own
C) Encapsulating one protocol into another protocol
D) Caching previously requested resources
A) Making requests in the Internet, using HTTP, FTP, SOCKS on behalf of other clients
B) IP Masquerading - replacing original requestor's address with it's own
C) Encapsulating one protocol into another protocol
D) Caching previously requested resources

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
44
Which virus-scanning engine is NOT supported by ProxyAV?
A) MCAfee
B) Sophos
C) Norton
D) Kaspersky E.Panda
A) MCAfee
B) Sophos
C) Norton
D) Kaspersky E.Panda

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
45
Reporter creates reports that can be saved in the following formats (choose all that apply) (a) CSV (comma-separated-values) to be opened by Excel (b) Adobe PDF (c) HTML (d) XML
A) a, b & c only
B) a, b & d only
C) a, c & d only
D) b, c & d only
E) All of the above
A) a, b & c only
B) a, b & d only
C) a, c & d only
D) b, c & d only
E) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
46
Which of the following is a free software based Blue Coat product for home users?
A) Web Filter
B) k9
C) SiteAdvisot
A) Web Filter
B) k9
C) SiteAdvisot

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
47
What are the best practices using anti-virus software on a windows machine running Blue Coat Reporter?
A) Do not use anti-virus software as the log files cannot contain viruses
B) Perform scans as you would for any windows server
C) Perform scans only during low activity of ProxySG
D) Perform scans, but bypass certain directories containing frequently changing files
A) Do not use anti-virus software as the log files cannot contain viruses
B) Perform scans as you would for any windows server
C) Perform scans only during low activity of ProxySG
D) Perform scans, but bypass certain directories containing frequently changing files

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
48
When virus scanning functionality is enabled, ProxySG acts as an ICAP server, and ProxyAV as an ICAP client.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
49
What is the name of the Technical SupportWeb site where service requests can be reported?
A) WebPulse
B) BlueTouch Online
C) Blue Coat Professional Services
D) Services@BC
A) WebPulse
B) BlueTouch Online
C) Blue Coat Professional Services
D) Services@BC

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
50
HTTP Access log format bcreportermain_vl includes the time of the request, URL requested, and MIME type of content, but does not include whether it is cache hit or miss.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
51
Is Management Console accessible over HTTP?
A) Yes, it is enabled by default, except in FIPS mode
B) It can be explicitly enabled, the default port is 8081
C) It can be explicitly enabled, the default port is 8082
D) A new service has to be created with port selected by the administrator
A) Yes, it is enabled by default, except in FIPS mode
B) It can be explicitly enabled, the default port is 8081
C) It can be explicitly enabled, the default port is 8082
D) A new service has to be created with port selected by the administrator

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
52
What kind of object should be selected from button New in the New Action dialogue in the VPM that returns a coaching or splash page?
A) Return Exception
B) Return Redirect
C) Notify User
D) Acceptable Usage Policy
A) Return Exception
B) Return Redirect
C) Notify User
D) Acceptable Usage Policy

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
53
When the DRTR successfully categorizes a site, the site is_________ (Choose all that apply) (a) Added to the static BCWF database on the ProxySG (b) Added to the local database on the ProxySG (c) Added to the DRTR database on the ProxySG (d) Added to a DRTR cache that resides on the ProxySG
A) a & b only
B) b & c only
C) d only
D) None of the above
A) a & b only
B) b & c only
C) d only
D) None of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
54
If a proxy server is seen in the external Internet as Web server, it is a forward proxy.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
55
What changes, when FIPS mode for Management Console is enabled?
A) FIPS mode improves browser support
B) Management Console can be accessed via TLS-based HTTPS only; some device certification options are changed
C) FIPS mode makes Management Console application faster as the rich client download size decreases
A) FIPS mode improves browser support
B) Management Console can be accessed via TLS-based HTTPS only; some device certification options are changed
C) FIPS mode makes Management Console application faster as the rich client download size decreases

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
56
What are requirements for client's browser for notification and coaching pages to work properly?
A) Pop-up windows should not be blocked
B) JavaScript has to be enabled
C) Cookies have to be enabled
D) Both JavaScript and cookies have to be enabled
A) Pop-up windows should not be blocked
B) JavaScript has to be enabled
C) Cookies have to be enabled
D) Both JavaScript and cookies have to be enabled

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
57
Which of the following tracks client-server requests and server responses?
A) Event logs
B) Sys logs
C) Report logs
D) Access logs
A) Event logs
B) Sys logs
C) Report logs
D) Access logs

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
58
When Proxy server settings in a browser are configured using WPAD (web Proxy Auto Discovery) protocol, what has to be specifically guaranteed to ensure security?
A) JavaScript on client's browser must be enabled, otherwise it will not allow to execute proxy configuration script.
B) Hosts (e.g. wpad.mydepartment.mycompany.com, wpad.mycompany.com) should be trusted not to serve malicious wpad.dat files
C) Internet Explorer browser should receive security updates more often than twice a year
D) DHCP must be accessible at the time, when user starts a browser
A) JavaScript on client's browser must be enabled, otherwise it will not allow to execute proxy configuration script.
B) Hosts (e.g. wpad.mydepartment.mycompany.com, wpad.mycompany.com) should be trusted not to serve malicious wpad.dat files
C) Internet Explorer browser should receive security updates more often than twice a year
D) DHCP must be accessible at the time, when user starts a browser

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
59
What does the Blue Coat WebFilter do to classify sites not found in the WebFilter on-box database?
A) Sends classification requests to WebPulse
B) Runs Bayes classification algorithm on ProxySG
C) Forwards categorization requests to other ProsySG
D) Matches against a list of forbidden keywords
A) Sends classification requests to WebPulse
B) Runs Bayes classification algorithm on ProxySG
C) Forwards categorization requests to other ProsySG
D) Matches against a list of forbidden keywords

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
60
What preconditions should be satisfied in order to do initial configuration from a client computer via the URL https://proxysg.bluecodt.com:8083? (choose all that apply) (a) Client computer should be directly connected to ProxySG with a cross-over cable (b) ProxySG should have a pass-through card (c) ProxySG should be deployed in the bridging mode
A) a & b only
B) a & c only
C) b & c only
D) All of the above
A) a & b only
B) a & c only
C) b & c only
D) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
61
The SSL certificate returned by the Management Console upon HTTPS access____.
A) is birth certificate, which depends on the device serial number only; it can be cached for the whole lifetime of the ProxySG
B) is generated anew automatically every time ProxySG performs initial setup
C) has to be generated explicitly from the CLI
A) is birth certificate, which depends on the device serial number only; it can be cached for the whole lifetime of the ProxySG
B) is generated anew automatically every time ProxySG performs initial setup
C) has to be generated explicitly from the CLI

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
62
Management Console of ProxySG (SGOS v. 5.4- or earlier) is based on the following client-side technology:
A) FIPS mode improves browser support
B) Java servlet application
C) JVM applet embedded in the Web page
D) Adobe Flex
E) AJAX and JavaScript
A) FIPS mode improves browser support
B) Java servlet application
C) JVM applet embedded in the Web page
D) Adobe Flex
E) AJAX and JavaScript

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
63
Which console services are NOT available on the ProxySG?
A) SSH
B) HTTP
C) HTTPS
D) Serial
E) All the above are available
A) SSH
B) HTTP
C) HTTPS
D) Serial
E) All the above are available

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
64
Which HTTP error code corresponds to the ProxySG default exception identifier policy_denied?
A) 403
B) 404
C) 503
D) 401
A) 403
B) 404
C) 503
D) 401

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
65
Which of the following tracks client-server transactions going through the ProxySG?
A) Event logs
B) Sys logs
C) Report logs
D) Access logs
A) Event logs
B) Sys logs
C) Report logs
D) Access logs

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
66
Which of the following statements are true? (Choose all that apply) (a) Exceptions and notifications can be configured to use specific HTTP response codes. (b) Exceptions and notify user objects can be created through the VPM. (c) Exceptions and notify user objects can be utilized as action objects in the VPM. (d) Exceptions and notify user objects can include substitutions such as the IP address, username or category.
A) a & b only
B) a, c & d only
C) b & c only
D) a, b & c only
A) a & b only
B) a, c & d only
C) b & c only
D) a, b & c only

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
67
ProxySG has to be deployed inline (in bridging mode) or virtually inline (using WCCP or an L4 switch) in order to block IM traffic.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
68
The ProxySG operating system is based on________.
A) a customized, object oriented version of FreeBSD
B) a custom built operating system with integrated caching and compression
C) a Linux Kernel 2.6.x with byte caching and compression
A) a customized, object oriented version of FreeBSD
B) a custom built operating system with integrated caching and compression
C) a Linux Kernel 2.6.x with byte caching and compression

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
69
Can server initiate an HTTP transaction?
A) It cannot
B) It can for e.g. Web-based instant messaging, AJAX and similar server-push applications
C) It can only for some HTTP request methods
A) It cannot
B) It can for e.g. Web-based instant messaging, AJAX and similar server-push applications
C) It can only for some HTTP request methods

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
70
When accessing Management Console from the Web, the built in admin account uses the regular password of CLI access (NOT the enable password of admin account)

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
71
The following authentication realms will be used in a sequence realm. Which realm should go first?
A) Local
B) IWA
C) Radius
D) LDAP
A) Local
B) IWA
C) Radius
D) LDAP

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
72
Which of the following policies CANNOT be implemented on the ProxyAV? (Choose all that apply) (a) Blocking viruses, worms, spyware and trojans (b) Blocking file types using apparent data type (file signature) (c) Blocking files that exceed a size limit set by the administrator (d) Blocking password protected archive files
A) a only
B) b only
C) c only
D) d only
E) All of the above can be implemented with the Proxy AV
A) a only
B) b only
C) c only
D) d only
E) All of the above can be implemented with the Proxy AV

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
73
What happens, if there are multiple listeners to the same TCP port, and destination IP address belongs to multiple IP address ranges?
A) Such configuration is Inherently ambiguous and wrong
B) Such cases cause built-in exceptions to be thrown during policy processing
C) The most specific IP address range is always used
A) Such configuration is Inherently ambiguous and wrong
B) Such cases cause built-in exceptions to be thrown during policy processing
C) The most specific IP address range is always used

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
74
The ProxySG ICAP implementation is fully compatible with which of the following applications? (Choose all that apply) (a) Finjan SurfinGate (b) Webwasher (c) Antivirus Scan Engine (SAVSE) (d) Trend Micro InterScan
A) a & b only
B) b & c only
C) c & d only
D) All of the above
A) a & b only
B) b & c only
C) c & d only
D) All of the above

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
75
Which layer can be used to block a particular URL?
A) Authentication
B) Web Access
C) Forwarding
D) Web Content
A) Authentication
B) Web Access
C) Forwarding
D) Web Content

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
76
The ProxySG can create configurable access logs for FTP, HTTP, and Telnet but not for Peer-to-Peer or Real Media

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
77
If you set a service attribute on the ProxySG to "Reflect Client IP", what must you make sure is not going to happen in the network?
A) The service destination IP is set to "transparent" and Action is set to "Intercept".
B) Force Authentication through policy.
C) Asymmetric routing directly from client to OCS.
A) The service destination IP is set to "transparent" and Action is set to "Intercept".
B) Force Authentication through policy.
C) Asymmetric routing directly from client to OCS.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
78
All of the following are software based Blue Coat solutions: Blue Coat Reporter, Blue Coat WebFilter, Blue Coat K9, ProxyClient

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
79
Which appliance does not need any licensing and is fully operable after deployment?
A) ProxyAV
B) ProxySG
C) ProxyRA
D) Blue Coat Director
A) ProxyAV
B) ProxySG
C) ProxyRA
D) Blue Coat Director

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck
80
ProxySG can provide all these services to IM clients - client authentication at a proxy, message reflection, policy enforcement and logging.

Unlock Deck
Unlock for access to all 135 flashcards in this deck.
Unlock Deck
k this deck



