Deck 2: Check Point Certified Security Administrator (CCSA R80)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/676
Play
Full screen (f)
Deck 2: Check Point Certified Security Administrator (CCSA R80)
1
Fill in the blank: A _________ VPN deployment is used to provide remote users with secure access to internal corporate resources by authenticating the user through an internet browser.
A) Clientless remote access
B) Clientless direct access
C) Client-based remote access
D) Direct access
A) Clientless remote access
B) Clientless direct access
C) Client-based remote access
D) Direct access
A
Explanation: Clientless - Users connect through a web browser and use HTTPS connections. Clientless solutions usually supply access to web-based corporate resources.
Explanation: Clientless - Users connect through a web browser and use HTTPS connections. Clientless solutions usually supply access to web-based corporate resources.
2
Two administrators Dave and Jon both manage R80 Management as administrators for ABC Corp. Jon logged into the R80 Management and then shortly after Dave logged in to the same server. They are both in the Security Policies view. From the screenshots below, why does Dave not have the rule no.6 in his SmartConsole view even though Jon has it his in his SmartConsole view? 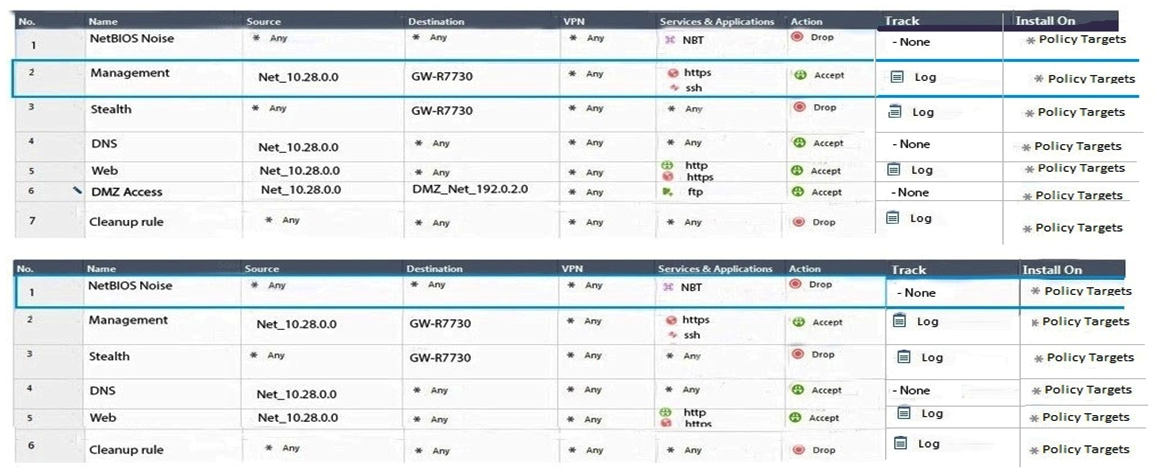
A) Jon is currently editing rule no.6 but has Published part of his changes.
B) Dave is currently editing rule no.6 and has marked this rule for deletion.
C) Dave is currently editing rule no.6 and has deleted it from his Rule Base.
D) Jon is currently editing rule no.6 but has not yet Published his changes.

A) Jon is currently editing rule no.6 but has Published part of his changes.
B) Dave is currently editing rule no.6 and has marked this rule for deletion.
C) Dave is currently editing rule no.6 and has deleted it from his Rule Base.
D) Jon is currently editing rule no.6 but has not yet Published his changes.
D
Explanation: When an administrator logs in to the Security Management Server through SmartConsole, a new editing session starts. The changes that the administrator makes during the session are only available to that administrator. Other administrators see a lock icon on object and rules that are being edited. To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
Explanation: When an administrator logs in to the Security Management Server through SmartConsole, a new editing session starts. The changes that the administrator makes during the session are only available to that administrator. Other administrators see a lock icon on object and rules that are being edited. To make changes available to all administrators, and to unlock the objects and rules that are being edited, the administrator must publish the session.
3
Which of the following Automatically Generated Rules NAT rules have the lowest implementation priority?
A) Machine Hide NAT
B) Address Range Hide NAT
C) Network Hide NAT
D) Machine Static NAT
A) Machine Hide NAT
B) Address Range Hide NAT
C) Network Hide NAT
D) Machine Static NAT
B,C
Explanation: SmartDashboard organizes the automatic NAT rules in this order: Static NAT rules for Firewall, or node (computer or server) objects Hide NAT rules for Firewall, or node objects Static NAT rules for network or address range objects Hide NAT rules for network or address range objects
Explanation: SmartDashboard organizes the automatic NAT rules in this order: Static NAT rules for Firewall, or node (computer or server) objects Hide NAT rules for Firewall, or node objects Static NAT rules for network or address range objects Hide NAT rules for network or address range objects
4
In R80 spoofing is defined as a method of:
A) Disguising an illegal IP address behind an authorized IP address through Port Address Translation.
B) Hiding your firewall from unauthorized users.
C) Detecting people using false or wrong authentication logins
D) Making packets appear as if they come from an authorized IP address.
A) Disguising an illegal IP address behind an authorized IP address through Port Address Translation.
B) Hiding your firewall from unauthorized users.
C) Detecting people using false or wrong authentication logins
D) Making packets appear as if they come from an authorized IP address.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
5
Fill in the blank: Gaia can be configured using the _______ or ______ .
A) Gaia; command line interface
B) WebUI; Gaia Interface
C) Command line interface; WebUI
D) Gaia Interface; GaiaUI
A) Gaia; command line interface
B) WebUI; Gaia Interface
C) Command line interface; WebUI
D) Gaia Interface; GaiaUI

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
6
By default, which port does the WebUI listen on?
A) 80
B) 4434
C) 443
D) 8080
A) 80
B) 4434
C) 443
D) 8080

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
7
Review the following screenshot and select the BEST answer. 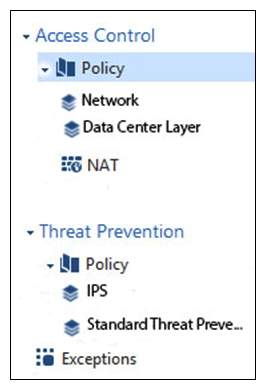
A) Data Center Layer is an inline layer in the Access Control Policy.
B) By default all layers are shared with all policies.
C) If a connection is dropped in Network Layer, it will not be matched against the rules in Data Center Layer.
D) If a connection is accepted in Network-layer, it will not be matched against the rules in Data Center Layer.

A) Data Center Layer is an inline layer in the Access Control Policy.
B) By default all layers are shared with all policies.
C) If a connection is dropped in Network Layer, it will not be matched against the rules in Data Center Layer.
D) If a connection is accepted in Network-layer, it will not be matched against the rules in Data Center Layer.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
8
DLP and Geo Policy are examples of what type of Policy?
A) Standard Policies
B) Shared Policies
C) Inspection Policies
D) Unified Policies
A) Standard Policies
B) Shared Policies
C) Inspection Policies
D) Unified Policies

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
9
Which of the following is NOT a component of a Distinguished Name?
A) Organization Unit
B) Country
C) Common name
D) User container
A) Organization Unit
B) Country
C) Common name
D) User container

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
10
Which VPN routing option uses VPN routing for every connection a satellite gateway handles?
A) To satellites through center only
B) To center only
C) To center and to other satellites through center
D) To center, or through the center to other satellites, to internet and other VPN targets
A) To satellites through center only
B) To center only
C) To center and to other satellites through center
D) To center, or through the center to other satellites, to internet and other VPN targets

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
11
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
A) UserCheck
B) Active Directory Query
C) Account Unit Query
D) User Directory Query
A) UserCheck
B) Active Directory Query
C) Account Unit Query
D) User Directory Query

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
12
You are working with multiple Security Gateways enforcing an extensive number of rules. To simplify security administration, which action would you choose?
A) Eliminate all possible contradictory rules such as the Stealth or Cleanup rules.
B) Create a separate Security Policy package for each remote Security Gateway.
C) Create network object that restrict all applicable rules to only certain networks.
D) Run separate SmartConsole instances to login and configure each Security Gateway directly.
A) Eliminate all possible contradictory rules such as the Stealth or Cleanup rules.
B) Create a separate Security Policy package for each remote Security Gateway.
C) Create network object that restrict all applicable rules to only certain networks.
D) Run separate SmartConsole instances to login and configure each Security Gateway directly.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
13
Fill in the blanks: VPN gateways authenticate using ___________ and ___________ .
A) Passwords; tokens
B) Certificates; pre-shared secrets
C) Certificates; passwords
D) Tokens; pre-shared secrets
A) Passwords; tokens
B) Certificates; pre-shared secrets
C) Certificates; passwords
D) Tokens; pre-shared secrets

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
14
You have enabled "Full Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
A) Logging has disk space issues. Change logging storage options on the logging server or Security Management Server properties and install database.
B) Data Awareness is not enabled.
C) Identity Awareness is not enabled.
D) Logs are arriving from Pre-R80 gateways.
A) Logging has disk space issues. Change logging storage options on the logging server or Security Management Server properties and install database.
B) Data Awareness is not enabled.
C) Identity Awareness is not enabled.
D) Logs are arriving from Pre-R80 gateways.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
15
Which Check Point feature enables application scanning and the detection?
A) Application Dictionary
B) AppWiki
C) Application Library
D) CPApp
A) Application Dictionary
B) AppWiki
C) Application Library
D) CPApp

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
16
What will be the effect of running the following command on the Security Management Server? 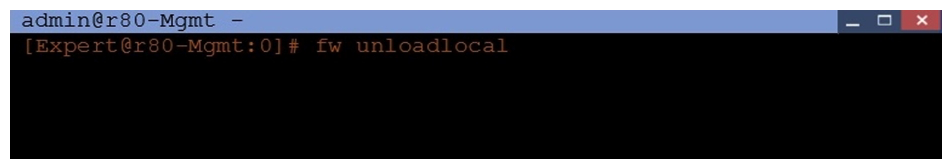
A) Remove the installed Security Policy.
B) Remove the local ACL lists.
C) No effect.
D) Reset SIC on all gateways.

A) Remove the installed Security Policy.
B) Remove the local ACL lists.
C) No effect.
D) Reset SIC on all gateways.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
17
Which utility allows you to configure the DHCP service on GAIA from the command line?
A) ifconfig
B) dhcp_cfg
C) sysconfig
D) cpconfig
A) ifconfig
B) dhcp_cfg
C) sysconfig
D) cpconfig

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
18
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp. 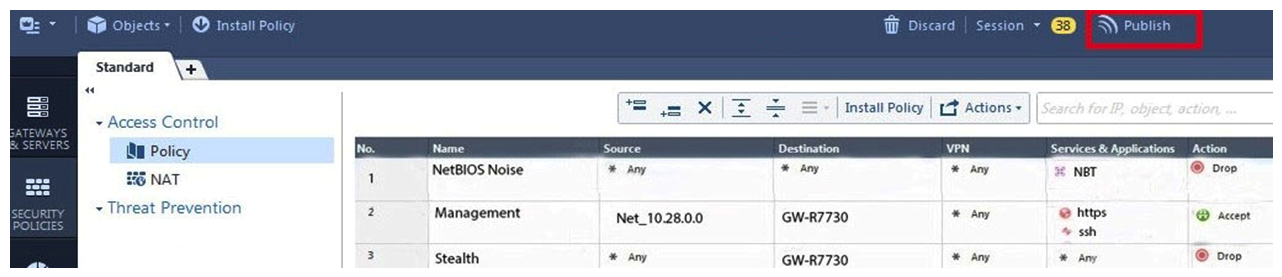 How will you describe the new " Publish " button in R80 Management Console?
How will you describe the new " Publish " button in R80 Management Console?
A) The Publish button takes any changes an administrator has made in their management session, publishes a copy to the Check Point of R80, and then saves it to the R80 database.
B) The Publish button takes any changes an administrator has made in their management session and publishes a copy to the Check Point Cloud of R80 and but does not save it to the R80
C) The Publish button makes any changes an administrator has made in their management session visible to all other administrator sessions and saves it to the Database.
D) The Publish button makes any changes an administrator has made in their management session visible to the new Unified Policy session and saves it to the Database.
 How will you describe the new " Publish " button in R80 Management Console?
How will you describe the new " Publish " button in R80 Management Console?A) The Publish button takes any changes an administrator has made in their management session, publishes a copy to the Check Point of R80, and then saves it to the R80 database.
B) The Publish button takes any changes an administrator has made in their management session and publishes a copy to the Check Point Cloud of R80 and but does not save it to the R80
C) The Publish button makes any changes an administrator has made in their management session visible to all other administrator sessions and saves it to the Database.
D) The Publish button makes any changes an administrator has made in their management session visible to the new Unified Policy session and saves it to the Database.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
19
What is the order of NAT priorities?
A) Static NAT, IP pool NAT, hide NAT
B) IP pool NAT, static NAT, hide NAT
C) Static NAT, automatic NAT, hide NAT
D) Static NAT, hide NAT, IP pool NAT
A) Static NAT, IP pool NAT, hide NAT
B) IP pool NAT, static NAT, hide NAT
C) Static NAT, automatic NAT, hide NAT
D) Static NAT, hide NAT, IP pool NAT

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
20
Which of the following ClusterXL modes uses a non-unicast MAC address for the cluster IP address.
A) High Availability
B) Load Sharing Multicast
C) Load Sharing Pivot
D) Master/Backup
A) High Availability
B) Load Sharing Multicast
C) Load Sharing Pivot
D) Master/Backup

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
21
What does the "unknown" SIC status shown on SmartConsole mean?
A) The SMS can contact the Security Gateway but cannot establish Secure Internal Communication.
B) SIC activation key requires a reset.
C) The SIC activation key is not known by any administrator.
D) There is no connection between the Security Gateway and SMS.
A) The SMS can contact the Security Gateway but cannot establish Secure Internal Communication.
B) SIC activation key requires a reset.
C) The SIC activation key is not known by any administrator.
D) There is no connection between the Security Gateway and SMS.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
22
The security Gateway is installed on GAiA R80 The default port for the WEB User Interface is _______ .
A) TCP 18211
B) TCP 257
C) TCP 4433
D) TCP 443
A) TCP 18211
B) TCP 257
C) TCP 4433
D) TCP 443

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
23
Fill in the blank: The tool _______ generates a R80 Security Gateway configuration report.
A) infoCP
B) infoview
C) cpinfo
D) fw cpinfo
A) infoCP
B) infoview
C) cpinfo
D) fw cpinfo

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
24
Which of the following is TRUE regarding Gaia command line?
A) Configuration changes should be done in mgmt_cli and use CLISH for monitoring, Expert mode is used only for OS level tasks.
B) Configuration changes should be done in expert-mode and CLISH is used for monitoring.
C) Configuration changes should be done in mgmt-cli and use expert-mode for OS-level tasks.
D) All configuration changes should be made in CLISH and expert-mode should be used for OS-level tasks.
A) Configuration changes should be done in mgmt_cli and use CLISH for monitoring, Expert mode is used only for OS level tasks.
B) Configuration changes should be done in expert-mode and CLISH is used for monitoring.
C) Configuration changes should be done in mgmt-cli and use expert-mode for OS-level tasks.
D) All configuration changes should be made in CLISH and expert-mode should be used for OS-level tasks.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
25
When you upload a package or license to the appropriate repository in SmartUpdate, where is the package or license stored
A) Security Gateway
B) Check Point user center
C) Security Management Server
D) SmartConsole installed device
A) Security Gateway
B) Check Point user center
C) Security Management Server
D) SmartConsole installed device

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
26
Tom has been tasked to install Check Point R80 in a distributed deployment. Before Tom installs the systems this way, how many machines will he need if he does NOT include a SmartConsole machine in his calculations?
A) One machine, but it needs to be installed using SecurePlatform for compatibility purposes.
B) One machine
C) Two machines
D) Three machines
A) One machine, but it needs to be installed using SecurePlatform for compatibility purposes.
B) One machine
C) Two machines
D) Three machines

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
27
Which feature is NOT provided by all Check Point Mobile Access solutions?
A) Support for IPv6
B) Granular access control
C) Strong user authentication
D) Secure connectivity
A) Support for IPv6
B) Granular access control
C) Strong user authentication
D) Secure connectivity

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
28
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
A) INSPECT Engine
B) Stateful Inspection
C) Packet Filtering
D) Application Layer Firewall
A) INSPECT Engine
B) Stateful Inspection
C) Packet Filtering
D) Application Layer Firewall

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
29
Which one of the following is the preferred licensing model? Select the Best answer.
A) Local licensing because it ties the package license to the IP-address of the gateway and has no dependency of the Security Management Server.
B) Central licensing because it ties the package license to the IP-address of the Security Management Server and has no dependency of the gateway.
C) Local licensing because it ties the package license to the MAC-address of the gateway management interface and has no Security Management Server dependency.
D) Central licensing because it ties the package license to the MAC-address of the Security Management Server Mgmt-interface and has no dependency of the gateway.
A) Local licensing because it ties the package license to the IP-address of the gateway and has no dependency of the Security Management Server.
B) Central licensing because it ties the package license to the IP-address of the Security Management Server and has no dependency of the gateway.
C) Local licensing because it ties the package license to the MAC-address of the gateway management interface and has no Security Management Server dependency.
D) Central licensing because it ties the package license to the MAC-address of the Security Management Server Mgmt-interface and has no dependency of the gateway.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
30
What are the three essential components of the Check Point Security Management Architecture?
A) SmartConsole, Security Management Server, Security Gateway
B) SmartConsole, SmartUpdate, Security Gateway
C) Security Management Server, Security Gateway, Command Line Interface
D) WebUI, SmartConsole, Security Gateway
A) SmartConsole, Security Management Server, Security Gateway
B) SmartConsole, SmartUpdate, Security Gateway
C) Security Management Server, Security Gateway, Command Line Interface
D) WebUI, SmartConsole, Security Gateway

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
31
Fill in the blank: Each cluster has __________ interfaces.
A) Five
B) Two
C) Three
D) Four
A) Five
B) Two
C) Three
D) Four

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
32
On the following graphic, you will find layers of policies. 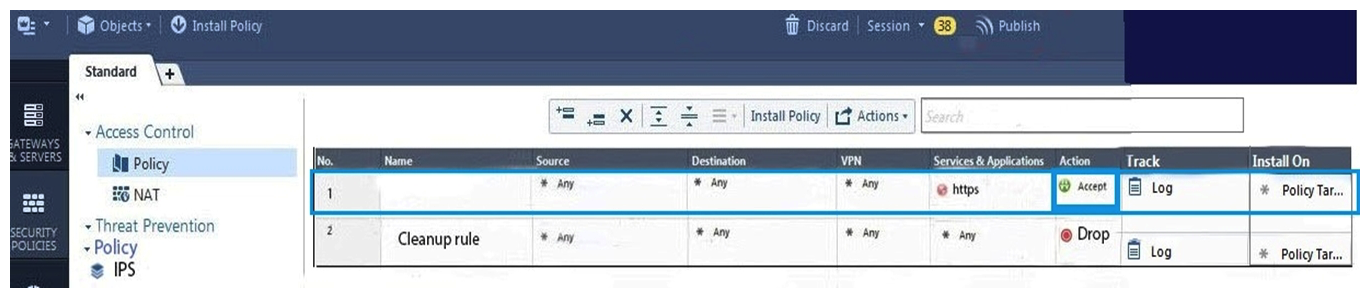 What is a precedence of traffic inspection for the defined polices?
What is a precedence of traffic inspection for the defined polices?
A) A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if implicit Drop Rule drops the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer.
B) A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer
C) A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to Threat Prevention layer and then after accepting the packet it passes to IPS layer.
D) A packet arrives at the gateway, it is checked against the rules in IPS policy layer and then it comes next to the Network policy layer and then after accepting the packet it passes to Threat Prevention layer.
 What is a precedence of traffic inspection for the defined polices?
What is a precedence of traffic inspection for the defined polices?A) A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if implicit Drop Rule drops the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer.
B) A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to IPS layer and then after accepting the packet it passes to Threat Prevention layer
C) A packet arrives at the gateway, it is checked against the rules in the networks policy layer and then if there is any rule which accepts the packet, it comes next to Threat Prevention layer and then after accepting the packet it passes to IPS layer.
D) A packet arrives at the gateway, it is checked against the rules in IPS policy layer and then it comes next to the Network policy layer and then after accepting the packet it passes to Threat Prevention layer.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
33
Fill in the blank: The command __________ provides the most complete restoration of a R80 configuration.
A) upgrade_import
B) cpconfig
C) fwm dbimport -p
D) cpinfo -recover
A) upgrade_import
B) cpconfig
C) fwm dbimport -p
D) cpinfo -recover

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
34
Which options are given on features, when editing a Role on Gaia Platform?
A) Read/Write, Read Only
B) Read/Write, Read only, None
C) Read/Write, None
D) Read Only, None
A) Read/Write, Read Only
B) Read/Write, Read only, None
C) Read/Write, None
D) Read Only, None

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
35
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer.
A) Publish or discard the session.
B) Revert the session.
C) Save and install the Policy.
D) Delete older versions of database.
A) Publish or discard the session.
B) Revert the session.
C) Save and install the Policy.
D) Delete older versions of database.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
36
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point products protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
A) IPS and Application Control
B) IPS, anti-virus and anti-bot
C) IPS, anti-virus and e-mail security
D) SandBlast
A) IPS and Application Control
B) IPS, anti-virus and anti-bot
C) IPS, anti-virus and e-mail security
D) SandBlast

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
37
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ________ .
A) The license is attached to the wrong Security Gateway
B) The existing license expires
C) The license is upgraded
D) The IP address of the Security Management or Security Gateway has changed
A) The license is attached to the wrong Security Gateway
B) The existing license expires
C) The license is upgraded
D) The IP address of the Security Management or Security Gateway has changed

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
38
Fill in the blank: To build an effective Security Policy, use a ________ and _______ rule.
A) Cleanup; stealth
B) Stealth; implicit
C) Cleanup; default
D) Implicit; explicit
A) Cleanup; stealth
B) Stealth; implicit
C) Cleanup; default
D) Implicit; explicit

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
39
What is the default shell for the command line interface?
A) Expert
B) Clish
C) Admin
D) Normal
A) Expert
B) Clish
C) Admin
D) Normal

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
40
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
A) None, Security Management Server would be installed by itself.
B) SmartConsole
C) SecureClient
D) Security Gateway
A) None, Security Management Server would be installed by itself.
B) SmartConsole
C) SecureClient
D) Security Gateway

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
41
Which Check Point software blade prevents malicious files from entering a network using virus signatures and anomaly-based protections from ThreatCloud?
A) Firewall
B) Application Control
C) Anti-spam and Email Security
D) Antivirus
A) Firewall
B) Application Control
C) Anti-spam and Email Security
D) Antivirus

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
42
Where can administrator edit a list of trusted SmartConsole clients in R80?
A) cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server. cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server.
B) Only using SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients.
C) In cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients . In on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings > Permissions and Administrators Advanced Trusted Clients .
D) WebUI client logged to Security Management Server, SmartDashboard: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients , via cpconfig on a Security Gateway. WebUI client logged to Security Management Server, SmartDashboard: , via on a Security Gateway.
A) cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server. cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server.
B) Only using SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients.
C) In cpconfig on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients . In on a Security Management Server, in the WebUI logged into a Security Management Server, in SmartConsole: Manage and Settings > Permissions and Administrators Advanced Trusted Clients .
D) WebUI client logged to Security Management Server, SmartDashboard: Manage and Settings > Permissions and Administrators > Advanced > Trusted Clients , via cpconfig on a Security Gateway. WebUI client logged to Security Management Server, SmartDashboard: , via on a Security Gateway.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
43
Which type of the Check Point license ties the package license to the IP address of the Security Management Server?
A) Local
B) Central
C) Corporate
D) Formal
A) Local
B) Central
C) Corporate
D) Formal

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
44
Fill in the blank: The R80 utility fw monitor is used to troubleshoot _____________
A) User data base corruption
B) LDAP conflicts
C) Traffic issues
D) Phase two key negotiation
A) User data base corruption
B) LDAP conflicts
C) Traffic issues
D) Phase two key negotiation

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
45
What is the purpose of Captive Portal?
A) It provides remote access to SmartConsole
B) It manages user permission in SmartConsole
C) It authenticates users, allowing them access to the Internet and corporate resources
D) It authenticates users, allowing them access to the Gaia OS
A) It provides remote access to SmartConsole
B) It manages user permission in SmartConsole
C) It authenticates users, allowing them access to the Internet and corporate resources
D) It authenticates users, allowing them access to the Gaia OS

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
46
What does it mean if Bob gets this result on an object search? Refer to the image below. Choose the BEST answer. 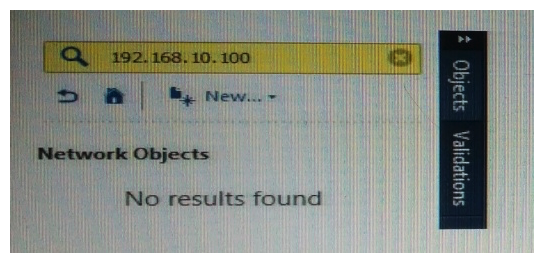
A) Search detailed is missing the subnet mask.
B) There is no object on the database with that name or that IP address.
C) There is no object on the database with that IP address.
D) Object does not have a NAT IP address.

A) Search detailed is missing the subnet mask.
B) There is no object on the database with that name or that IP address.
C) There is no object on the database with that IP address.
D) Object does not have a NAT IP address.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
47
View the rule below. What does the lock-symbol in the left column mean? Select the BEST answer. 
A) The current administrator has read-only permissions to Threat Prevention Policy.
B) Another user has locked the rule for editing.
C) Configuration lock is present. Click the lock symbol to gain read-write access.
D) The current administrator is logged in as read-only because someone else is editing the policy.

A) The current administrator has read-only permissions to Threat Prevention Policy.
B) Another user has locked the rule for editing.
C) Configuration lock is present. Click the lock symbol to gain read-write access.
D) The current administrator is logged in as read-only because someone else is editing the policy.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
48
Fill in the blank: The R80 feature ________ permits blocking specific IP addresses for a specified time period.
A) Block Port Overflow
B) Local Interface Spoofing
C) Suspicious Activity Monitoring
D) Adaptive Threat Prevention
A) Block Port Overflow
B) Local Interface Spoofing
C) Suspicious Activity Monitoring
D) Adaptive Threat Prevention

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
49
At what point is the Internal Certificate Authority (ICA) created?
A) Upon creation of a certificate
B) During the primary Security Management Server installation process.
C) When an administrator decides to create one.
D) When an administrator initially logs into SmartConsole.
A) Upon creation of a certificate
B) During the primary Security Management Server installation process.
C) When an administrator decides to create one.
D) When an administrator initially logs into SmartConsole.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
50
Why would an administrator see the message below? 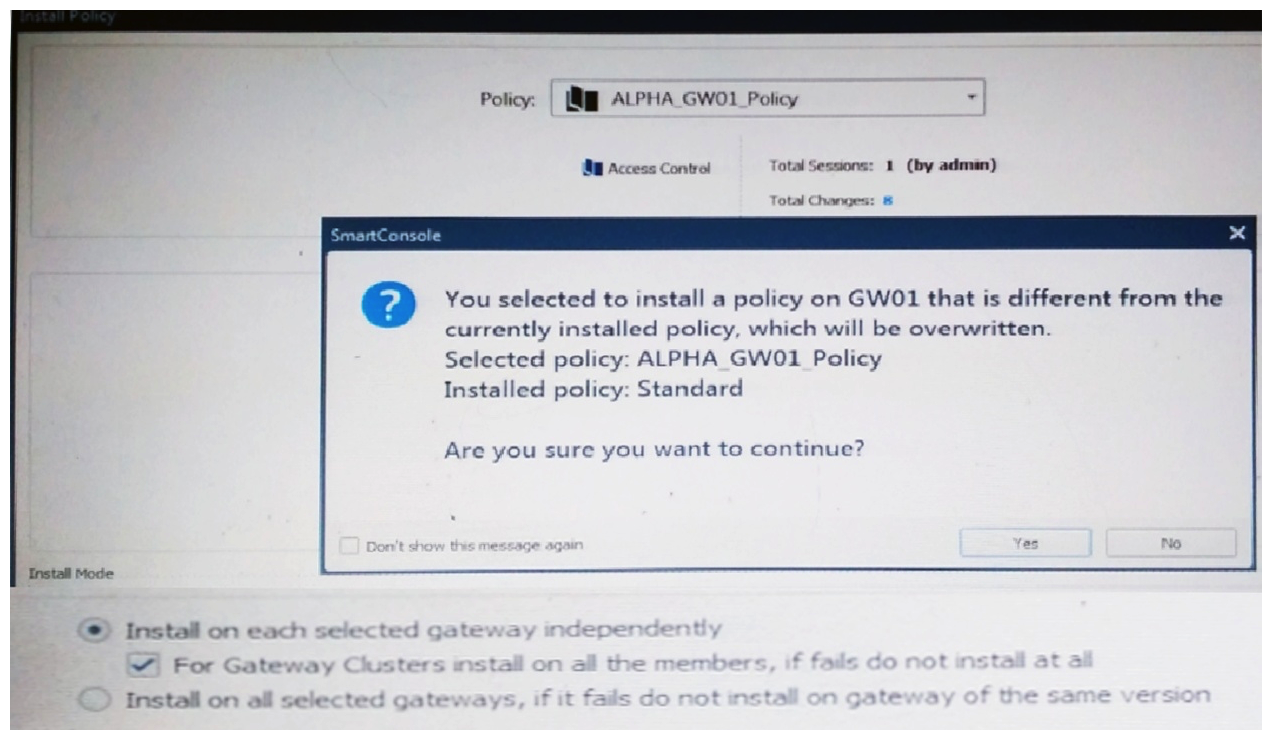
A) A new Policy Package created on both the Management and Gateway will be deleted and must be packed up first before proceeding.
B) A new Policy Package created on the Management is going to be installed to the existing Gateway.
C) A new Policy Package created on the Gateway is going to be installed on the existing Management.
D) A new Policy Package created on the Gateway and transferred to the management will be overwritten by the Policy Package currently on the Gateway but can be restored from a periodic backup on the Gateway.

A) A new Policy Package created on both the Management and Gateway will be deleted and must be packed up first before proceeding.
B) A new Policy Package created on the Management is going to be installed to the existing Gateway.
C) A new Policy Package created on the Gateway is going to be installed on the existing Management.
D) A new Policy Package created on the Gateway and transferred to the management will be overwritten by the Policy Package currently on the Gateway but can be restored from a periodic backup on the Gateway.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
51
Choose what BEST describes a Session.
A) Starts when an Administrator publishes all the changes made on SmartConsole.
B) Starts when an Administrator logs in to the Security Management Server through SmartConsole and ends when it is published.
C) Sessions ends when policy is pushed to the Security Gateway.
D) Sessions locks the policy package for editing.
A) Starts when an Administrator publishes all the changes made on SmartConsole.
B) Starts when an Administrator logs in to the Security Management Server through SmartConsole and ends when it is published.
C) Sessions ends when policy is pushed to the Security Gateway.
D) Sessions locks the policy package for editing.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following is NOT a back up method?
A) Save backup
B) System backup
C) snapshot
D) Migrate
A) Save backup
B) System backup
C) snapshot
D) Migrate

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
53
What does ExternalZone represent in the presented rule? 
A) The Internet.
B) Interfaces that administrator has defined to be part of External Security Zone.
C) External interfaces on all security gateways.
D) External interfaces of specific gateways.

A) The Internet.
B) Interfaces that administrator has defined to be part of External Security Zone.
C) External interfaces on all security gateways.
D) External interfaces of specific gateways.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
54
Web Control Layer has been set up using the settings in the following dialogue: 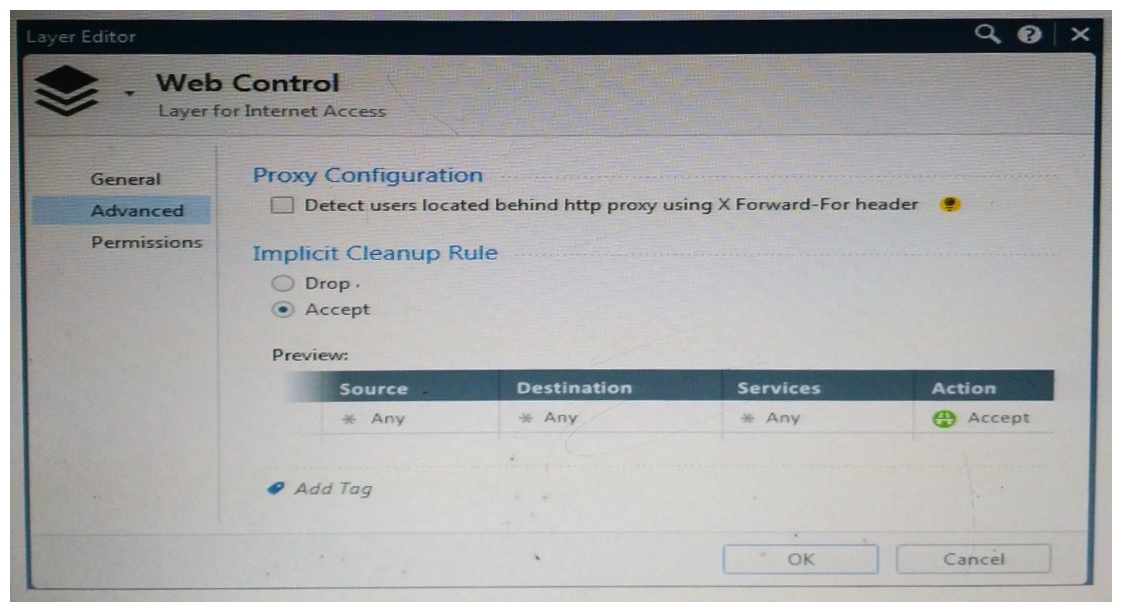 Consider the following policy and select the BEST answer.
Consider the following policy and select the BEST answer. 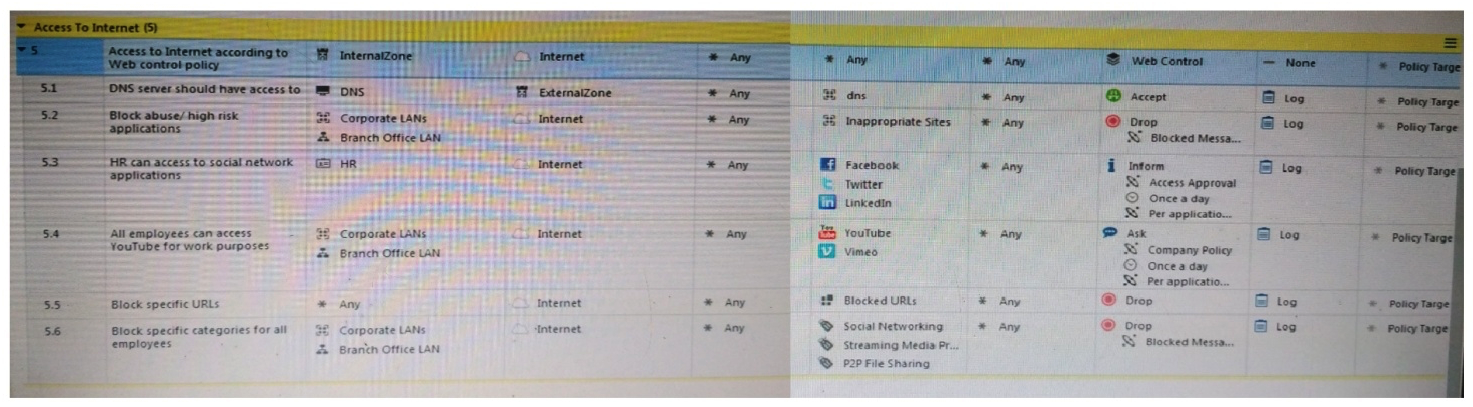
A) Traffic that does not match any rule in the subpolicy is dropped.
B) All employees can access only Youtube and Vimeo.
C) Access to Youtube and Vimeo is allowed only once a day.
D) Anyone from internal network can access the internet, expect the traffic defined in drop rules 5.2, 5.5 and 5.6.
 Consider the following policy and select the BEST answer.
Consider the following policy and select the BEST answer. 
A) Traffic that does not match any rule in the subpolicy is dropped.
B) All employees can access only Youtube and Vimeo.
C) Access to Youtube and Vimeo is allowed only once a day.
D) Anyone from internal network can access the internet, expect the traffic defined in drop rules 5.2, 5.5 and 5.6.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
55
You are the administrator for Alpha Corp. You have logged into your R80 Management server. You are making some changes in the Rule Base and notice that rule No.6 has a pencil icon next to it. 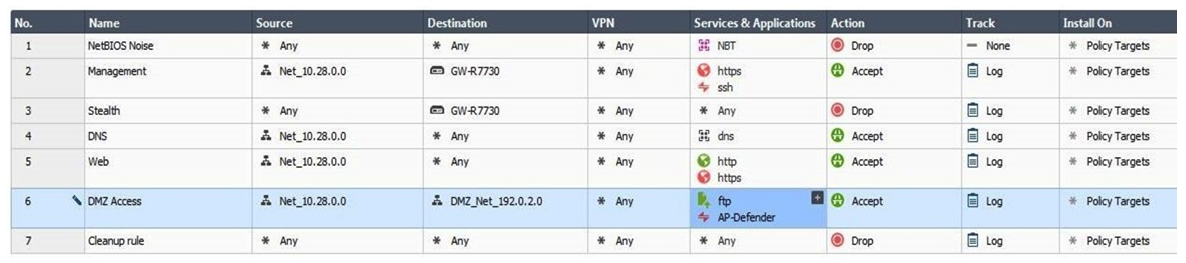 What does this mean?
What does this mean?
A) The rule No.6 has been marked for deletion in your Management session.
B) The rule No.6 has been marked for deletion in another Management session.
C) The rule No.6 has been marked for editing in your Management session.
D) The rule No.6 has been marked for editing in another Management session.
 What does this mean?
What does this mean?A) The rule No.6 has been marked for deletion in your Management session.
B) The rule No.6 has been marked for deletion in another Management session.
C) The rule No.6 has been marked for editing in your Management session.
D) The rule No.6 has been marked for editing in another Management session.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
56
Administrator wishes to update IPS from SmartConsole by clicking on the option " update now " under the IPS tab. Which device requires internet access for the update to work?
A) Security Gateway
B) Device where SmartConsole is installed
C) SMS
D) SmartEvent
A) Security Gateway
B) Device where SmartConsole is installed
C) SMS
D) SmartEvent

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
57
Which of the following is NOT a VPN routing option available in a star community?
A) To satellites through center only
B) To center, or through the center to other satellites, to Internet and other VPN targets
C) To center and to other satellites through center
D) To center only
A) To satellites through center only
B) To center, or through the center to other satellites, to Internet and other VPN targets
C) To center and to other satellites through center
D) To center only

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
58
Which of the following licenses are considered temporary?
A) Perpetual and Trial
B) Plug-and-play and Evaluation
C) Subscription and Perpetual
D) Evaluation and Subscription
A) Perpetual and Trial
B) Plug-and-play and Evaluation
C) Subscription and Perpetual
D) Evaluation and Subscription

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
59
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server (Security Management Server)?
A) Display policies and logs on the administrator's workstation.
B) Verify and compile Security Policies.
C) Processing and sending alerts such as SNMP traps and email notifications.
D) Store firewall logs to hard drive storage.
A) Display policies and logs on the administrator's workstation.
B) Verify and compile Security Policies.
C) Processing and sending alerts such as SNMP traps and email notifications.
D) Store firewall logs to hard drive storage.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
60
Jack works for a managed service provider and he has been tasked to create 17 new policies for several new customers. He does not have much time. What is the BEST way to do this with R80 security management?
A) Create a text-file with mgmt_cli script that creates all objects and policies. Open the file in SmartConsole Command Line to run it. Create a text-file with mgmt_cli script that creates all objects and policies. Open the file in SmartConsole Command Line to run it.
B) Create a text-file with Gaia CLI -commands in order to create all objects and policies. Run the file in CLISH with command load configuration . Create a text-file with Gaia CLI -commands in order to create all objects and policies. Run the file in CLISH with command load configuration .
C) Create a text-file with DBEDIT script that creates all objects and policies. Run the file in the command line of the management server using command dbedit -f . Create a text-file with DBEDIT script that creates all objects and policies. Run the file in the command line of the management server using command dbedit -f
D) Use Object Explorer in SmartConsole to create the objects and Manage Policies from the menu to create the policies.
A) Create a text-file with mgmt_cli script that creates all objects and policies. Open the file in SmartConsole Command Line to run it. Create a text-file with mgmt_cli script that creates all objects and policies. Open the file in SmartConsole Command Line to run it.
B) Create a text-file with Gaia CLI -commands in order to create all objects and policies. Run the file in CLISH with command load configuration . Create a text-file with Gaia CLI -commands in order to create all objects and policies. Run the file in CLISH with command load configuration .
C) Create a text-file with DBEDIT script that creates all objects and policies. Run the file in the command line of the management server using command dbedit -f . Create a text-file with DBEDIT script that creates all objects and policies. Run the file in the command line of the management server using command dbedit -f
D) Use Object Explorer in SmartConsole to create the objects and Manage Policies from the menu to create the policies.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
61
The IT Management team is interested in the new features of the Check Point R80 Management and wants to upgrade but they are concerned that the existing R77.30 Gaia Gateways cannot be managed by R80 because it is so different. As the administrator responsible for the Firewalls, how can you answer or confirm these concerns?
A) R80 Management contains compatibility packages for managing earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
B) R80 Management requires the separate installation of compatibility hotfix packages for managing the earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
C) R80 Management was designed as a completely different Management system and so can only monitor Check Point Gateways prior to R80.
D) R80 Management cannot manage earlier versions of Check Point Gateways prior to R80. Only R80 and above Gateways can be managed. Consult the R80 Release Notes for more information.
A) R80 Management contains compatibility packages for managing earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
B) R80 Management requires the separate installation of compatibility hotfix packages for managing the earlier versions of Check Point Gateways prior to R80. Consult the R80 Release Notes for more information.
C) R80 Management was designed as a completely different Management system and so can only monitor Check Point Gateways prior to R80.
D) R80 Management cannot manage earlier versions of Check Point Gateways prior to R80. Only R80 and above Gateways can be managed. Consult the R80 Release Notes for more information.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
62
You are going to upgrade from R77 to R80. Before the upgrade, you want to back up the system so that, if there are any problems, you can easily restore to the old version with all configuration and management files intact. What is the BEST backup method in this scenario?
A) backup
B) Database Revision
C) snapshot
D) migrate export
A) backup
B) Database Revision
C) snapshot
D) migrate export

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
63
If there is an Accept Implied Policy set to "First", what is the reason Jorge cannot see any logs?
A) Log Implied Rule was not selected on Global Properties.
B) Log Implied Rule was not set correctly on the track column on the rules base.
C) Track log column is set to none.
D) Track log column is set to Log instead of Full Log.
A) Log Implied Rule was not selected on Global Properties.
B) Log Implied Rule was not set correctly on the track column on the rules base.
C) Track log column is set to none.
D) Track log column is set to Log instead of Full Log.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
64
Fill in the blank: When LDAP is integrated with Check Point Security Management, it is then referred to as _______
A) UserCheck
B) User Directory
C) User Administration
D) User Center
A) UserCheck
B) User Directory
C) User Administration
D) User Center

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
65
In which VPN community is a satellite VPN gateway not allowed to create a VPN tunnel with another satellite VPN gateway?
A) Pentagon
B) Combined
C) Meshed
D) Star
A) Pentagon
B) Combined
C) Meshed
D) Star

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
66
In the R80 SmartConsole, on which tab are Permissions and Administrators defined?
A) Security Policies
B) Logs and Monitor
C) Manage and Settings
D) Gateway and Servers
A) Security Policies
B) Logs and Monitor
C) Manage and Settings
D) Gateway and Servers

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
67
Which Check Point software blade provides protection from zero-day and undiscovered threats?
A) Firewall
B) Threat Emulation
C) Application Control
D) Threat Extraction
A) Firewall
B) Threat Emulation
C) Application Control
D) Threat Extraction

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
68
Provide very wide coverage for all products and protocols, with noticeable performance impact. 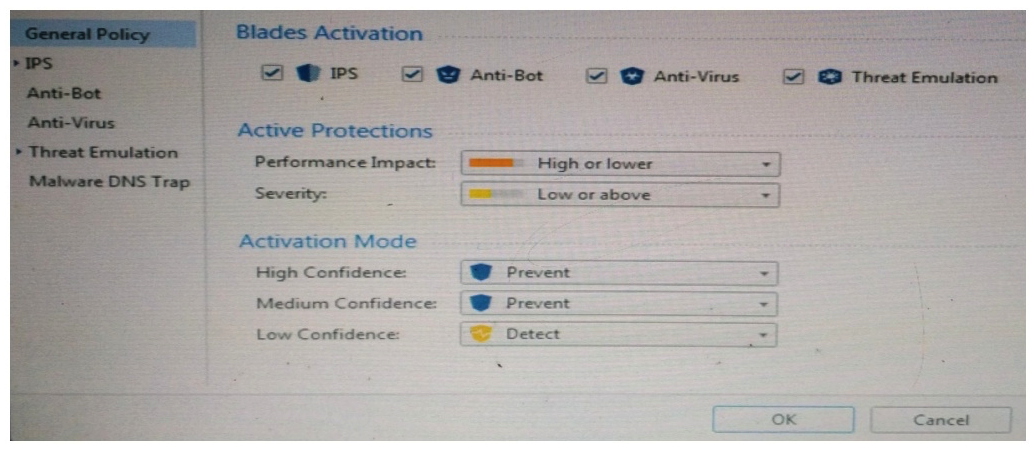 How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
A) Set High Confidence to Low and Low Confidence to Inactive.
B) Set the Performance Impact to Medium or lower.
C) The problem is not with the Threat Prevention Profile. Consider adding more memory to the appliance.
D) Set the Performance Impact to Very Low Confidence to Prevent.
 How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.A) Set High Confidence to Low and Low Confidence to Inactive.
B) Set the Performance Impact to Medium or lower.
C) The problem is not with the Threat Prevention Profile. Consider adding more memory to the appliance.
D) Set the Performance Impact to Very Low Confidence to Prevent.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
69
There are two R77.30 Security Gateways in the Firewall Cluster. They are named FW_A and FW_B. The cluster is configured to work as HA (High availability) with default cluster configuration. FW_A is configured to have higher priority than FW_B. FW_A was active and processing the traffic in the morning. FW_B was standby. Around 1100 am, its interfaces went down and this caused a failover. FW_B became active. After an hour, FW_A's interface issues were resolved and it became operational. When it re-joins the cluster, will it become active automatically?
A) No, since "maintain current active cluster member" option on the cluster object properties is enabled by default
B) No, since "maintain current active cluster member" option is enabled by default on the Global Properties
C) Yes, since "Switch to higher priority cluster member" option on the cluster object properties is enabled by default
D) Yes, since "Switch to higher priority cluster member" option is enabled by default on the Global Properties
A) No, since "maintain current active cluster member" option on the cluster object properties is enabled by default
B) No, since "maintain current active cluster member" option is enabled by default on the Global Properties
C) Yes, since "Switch to higher priority cluster member" option on the cluster object properties is enabled by default
D) Yes, since "Switch to higher priority cluster member" option is enabled by default on the Global Properties

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
70
Which of the following is NOT an element of VPN Simplified Mode and VPN Communities?
A) "Encrypt" action in the Rule Base
B) Permanent Tunnels
C) "VPN" column in the Rule Base
D) Configuration checkbox "Accept all encrypted traffic"
A) "Encrypt" action in the Rule Base
B) Permanent Tunnels
C) "VPN" column in the Rule Base
D) Configuration checkbox "Accept all encrypted traffic"

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
71
Fill in the blanks: A security Policy is created in _________ , stored in the _________ , and Distributed to the various __________ .
A) Rule base, Security Management Server, Security Gateways
B) SmartConsole, Security Gateway, Security Management Servers
C) SmartConsole, Security Management Server, Security Gateways
D) The Check Point database, SmartConsole, Security Gateways
A) Rule base, Security Management Server, Security Gateways
B) SmartConsole, Security Gateway, Security Management Servers
C) SmartConsole, Security Management Server, Security Gateways
D) The Check Point database, SmartConsole, Security Gateways

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
72
Look at the following screenshot and select the BEST answer. 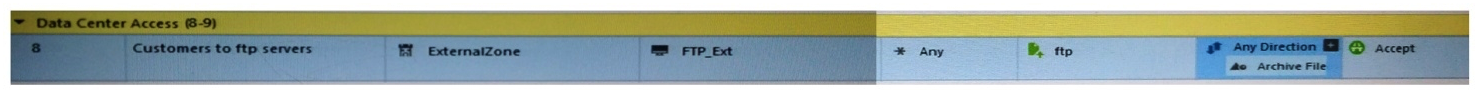
A) Clients external to the Security Gateway can download archive files from FTP_Ext server using FTP.
B) Internal clients can upload and download any-files to FTP_Ext-server using FTP.
C) Internal clients can upload and download archive-files to FTP_Ext server using FTP.
D) Clients external to the Security Gateway can upload any files to the FTP_Ext-server using FTP.

A) Clients external to the Security Gateway can download archive files from FTP_Ext server using FTP.
B) Internal clients can upload and download any-files to FTP_Ext-server using FTP.
C) Internal clients can upload and download archive-files to FTP_Ext server using FTP.
D) Clients external to the Security Gateway can upload any files to the FTP_Ext-server using FTP.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
73
What port is used for delivering logs from the gateway to the management server?
A) Port 258
B) Port 18209
C) Port 257
D) Port 981
A) Port 258
B) Port 18209
C) Port 257
D) Port 981

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
74
Which policy type is used to enforce bandwidth and traffic control rules?
A) Threat Emulation
B) Access Control
C) QoS
D) Threat Prevention
A) Threat Emulation
B) Access Control
C) QoS
D) Threat Prevention

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
75
After the initial installation the First Time Configuration Wizard should be run. Select the BEST answer.
A) First Time Configuration Wizard can be run from the Unified SmartConsole.
B) First Time Configuration Wizard can be run from the command line or from the WebUI.
C) First time Configuration Wizard can only be run from the WebUI.
D) Connection to the internet is required before running the First Time Configuration wizard.
A) First Time Configuration Wizard can be run from the Unified SmartConsole.
B) First Time Configuration Wizard can be run from the command line or from the WebUI.
C) First time Configuration Wizard can only be run from the WebUI.
D) Connection to the internet is required before running the First Time Configuration wizard.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
76
Fill in the blanks: The Application Layer Firewalls inspect traffic through the ________ layer(s) of the TCP/IP model and up to and including the ________ layer.
A) Lower; Application
B) First two; Internet
C) First two; Transport
D) Upper; Application
A) Lower; Application
B) First two; Internet
C) First two; Transport
D) Upper; Application

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
77
Bob and Joe both have Administrator Roles on their Gaia Platform. Bob logs in on the WebUI and then Joe logs in through CLI. Choose what BEST describes the following scenario, where Bob and Joe are both logged in:
A) When Joe logs in, Bob will be log out automatically.
B) Since they both are log in on different interfaces, they both will be able to make changes.
C) If Joe tries to make changes, he won't, database will be locked.
D) Bob will be prompt that Joe logged in.
A) When Joe logs in, Bob will be log out automatically.
B) Since they both are log in on different interfaces, they both will be able to make changes.
C) If Joe tries to make changes, he won't, database will be locked.
D) Bob will be prompt that Joe logged in.

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
78
Fill in the blank: A _______ is used by a VPN gateway to send traffic as if it were a physical interface.
A) VPN Tunnel Interface
B) VPN community
C) VPN router
D) VPN interface
A) VPN Tunnel Interface
B) VPN community
C) VPN router
D) VPN interface

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
79
Which of the completed statements is NOT true? The WebUI can be used to manage user accounts and:
A) assign privileges to users.
B) edit the home directory of the user.
C) add users to your Gaia system.
D) assign user rights to their home directory in the Security Management Server
A) assign privileges to users.
B) edit the home directory of the user.
C) add users to your Gaia system.
D) assign user rights to their home directory in the Security Management Server

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck
80
R80 Security Management Server can be installed on which of the following operating systems?
A) Gaia only
B) Gaia, SPLAT, Windows Server only
C) Gaia, SPLAT, Windows Server and IPSO only
D) Gaia and SPLAT only
A) Gaia only
B) Gaia, SPLAT, Windows Server only
C) Gaia, SPLAT, Windows Server and IPSO only
D) Gaia and SPLAT only

Unlock Deck
Unlock for access to all 676 flashcards in this deck.
Unlock Deck
k this deck



