Deck 2: Administration of Symantec Email Security.cloud (v1)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/113
Play
Full screen (f)
Deck 2: Administration of Symantec Email Security.cloud (v1)
1
The security status on the console home page is failing to alert a Symantec Endpoint Protection (SEP) administrator when virus definitions are out of date. How should the SEP administrator enable the Security Status alert?
A) Change the Notifications setting to "Show all notifications"
B) Raise the Security Status thresholds
C) Change the Action Summary display to "By number of computers"
D) Lower the Security Status thresholds
A) Change the Notifications setting to "Show all notifications"
B) Raise the Security Status thresholds
C) Change the Action Summary display to "By number of computers"
D) Lower the Security Status thresholds
Lower the Security Status thresholds
2
Which option is a characteristic of a Symantec Endpoint Protection (SEP) domain?
A) Every administrator from one domain can view data in other domains.
B) Each domain has its own management server and database.
C) Data for each domain is stored in its own separate SEP database.
D) Domains share the same management server and database.
A) Every administrator from one domain can view data in other domains.
B) Each domain has its own management server and database.
C) Data for each domain is stored in its own separate SEP database.
D) Domains share the same management server and database.
Domains share the same management server and database.
3
Which action can an administrator take to improve the Symantec Endpoint Protection Manager (SEPM) dashboard performance and report accuracy?
A) Rebuilding database indexes
B) Lowering the client installation log entries
C) Limiting the number of backups to keep
D) Decreasing the number of content revisions to keep
A) Rebuilding database indexes
B) Lowering the client installation log entries
C) Limiting the number of backups to keep
D) Decreasing the number of content revisions to keep
Rebuilding database indexes
4
An administrator is troubleshooting a Symantec Endpoint Protection (SEP) replication. Which component log should the administrator check to determine whether the communication between the two sites is working correctly?
A) Tomcat
B) Apache Web Server
C) Group Update Provider (GUP)
D) SQL Server
A) Tomcat
B) Apache Web Server
C) Group Update Provider (GUP)
D) SQL Server

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
5
A Symantec Endpoint Protection Manager (SEPM) administrator notices performance issues with the SEPM server. The Client tab becomes unresponsive in the SEPM console and .DAT files accumulate in the "agentinfo" folder. Which tool should the administrator use to gather log files to submit to Symantec Technical Support?
A) collectLog.cmd
B) LogExport.exe
C) smc.exe
D) ExportLog.vbs
A) collectLog.cmd
B) LogExport.exe
C) smc.exe
D) ExportLog.vbs

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
6
Which two criteria should an administrator use when defining Location Awareness for the Symantec Endpoint Protection (SEP) client? (Select two.)
A) SEP domain
B) WINS server
C) Network Speed
D) NIC description
E) geographic location
A) SEP domain
B) WINS server
C) Network Speed
D) NIC description
E) geographic location

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
7
An administrator is using the SylinkDrop tool to update a Symantec Endpoint Protection client install on a system. The client fails to migrate to the new Symantec Endpoint Protection Manager (SEPM), which is defined correctly in the Sylink.xml file that was exported from the SEPM. Which settings must be provided with SylinkDrop to ensure the successful migration to a new Symantec Endpoint Protection environment with additional Group Level Security Settings?
A) -s "silent"
B) -t "Tamper Protect"
C) -p "password"
D) -r "reboot"
A) -s "silent"
B) -t "Tamper Protect"
C) -p "password"
D) -r "reboot"

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
8
An administrator needs to add an Application Exception. When the administrator accesses the Application Exception dialog window, applications fail to appear. What is the likely problem?
A) The Symantec Endpoint Protection Manager is installed on a Domain Controller
B) The client computers already have exclusions for the applications.
C) The Learn applications that run on the client computers setting is disabled.
D) The clients are in a trusted Symantec Endpoint Protection domain.
A) The Symantec Endpoint Protection Manager is installed on a Domain Controller
B) The client computers already have exclusions for the applications.
C) The Learn applications that run on the client computers setting is disabled.
D) The clients are in a trusted Symantec Endpoint Protection domain.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
9
A company receives a high number of reports from users that files being downloaded from internal web servers are blocked. The Symantec Endpoint Protection administrator verifies that the Automatically trust any file downloaded from an intranet website option is enabled. Which configuration can cause Insight to block the files being downloaded from the internal web servers?
A) Virus and Spyware definitions are out of date.
B) Local intranet zone is configured incorrectly on the Mac clients browser settings.
C) Intrusion prevention is disabled.
D) Local intranet zone is configured incorrectly on the Windows clients browser settings.
A) Virus and Spyware definitions are out of date.
B) Local intranet zone is configured incorrectly on the Mac clients browser settings.
C) Intrusion prevention is disabled.
D) Local intranet zone is configured incorrectly on the Windows clients browser settings.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
10
Which two considerations must an administrator make when enabling Application Learning in an environment? (Select two.)
A) Application Learning should be deployed on a small group of systems in the enterprise.
B) Application Learning can generate significant CPU or memory use on a Symantec Endpoint Protection Manager.
C) Application Learning is dependent on Insight.
D) Application Learning requires a file fingerprint list to be created in advance.
E) Application Learning can generate increased false positives.
A) Application Learning should be deployed on a small group of systems in the enterprise.
B) Application Learning can generate significant CPU or memory use on a Symantec Endpoint Protection Manager.
C) Application Learning is dependent on Insight.
D) Application Learning requires a file fingerprint list to be created in advance.
E) Application Learning can generate increased false positives.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
11
An administrator notices that some entries list that the Risk was partially removed. The administrator needs to determine whether additional steps are necessary to remediate the threat. Where in the Symantec Endpoint Protection Manager console can the administrator find additional information on the risk?
A) Infected and At Risk Computers report
B) Risk log
C) Notifications
D) Computer Status report
A) Infected and At Risk Computers report
B) Risk log
C) Notifications
D) Computer Status report

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
12
What does SONAR use to reduce false positives?
A) Virus and Spyware definitions
B) Extended File Attributes (EFA) table
C) File Fingerprint list
D) Symantec Insight
A) Virus and Spyware definitions
B) Extended File Attributes (EFA) table
C) File Fingerprint list
D) Symantec Insight

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
13
Which two settings does an administrator enable to use the Risk Tracer Feature in the Virus and Spyware Protection policy? (Select two.)
A) Firewall Policy
B) Application and Device Control Policy
C) Application Learning
D) Tamper Protection
E) IPS active response
A) Firewall Policy
B) Application and Device Control Policy
C) Application Learning
D) Tamper Protection
E) IPS active response

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
14
An administrator is reviewing an Infected Clients Report and notices that a client repeatedly shows the same malware detection. Although the client remediates the files, the infection continues to display in the logs. Which two functions should be enabled to automate enhanced remediation of a detected threat and its related side effects? (Select two.)
A) Stop Service Automatically
B) Stop and Reload AutoProtect
C) Terminate Processes Automatically
D) Risk Tracer
E) Early Launch Anti-Malware Driver
A) Stop Service Automatically
B) Stop and Reload AutoProtect
C) Terminate Processes Automatically
D) Risk Tracer
E) Early Launch Anti-Malware Driver

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
15
An administrator reports that the Home, Monitors, and Report pages are absent in the Symantec Endpoint Protection Management console when the administrator logs on. Which action should the administrator perform to correct the problem?
A) Grant the Administrator Full Access to Root group of the organization
B) Configure proxy settings for each server in the site
C) Configure External Logging to Enable Transmission of Logs to a Syslog Server
D) Grant View Reports permission to the administrator
A) Grant the Administrator Full Access to Root group of the organization
B) Configure proxy settings for each server in the site
C) Configure External Logging to Enable Transmission of Logs to a Syslog Server
D) Grant View Reports permission to the administrator

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
16
An administrator changes the Virus and Spyware Protection policy for a specific group that disables Auto-Protect. The administrator assigns the policy and the client systems apply the corresponding policy serial number. Upon visual inspection of a physical client system, the policy serial number is correct. However, Auto-Protect is still enabled on the client system. Which action should the administrator take to ensure that the desired setting is in place on the client?
A) Restart the client system.
B) Enable the padlock next to the setting in the policy.
C) Run a command on the computer to Update Content
D) Withdraw the Virus and Spyware Protection policy
A) Restart the client system.
B) Enable the padlock next to the setting in the policy.
C) Run a command on the computer to Update Content
D) Withdraw the Virus and Spyware Protection policy

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
17
Which task should an administrator perform to troubleshoot operation of the Symantec Endpoint Protection embedded database?
A) Verify the sqlserver.exe service is running on port 1433
B) Verify that dbsrv11.exe is listening on port 2638
C) Check the database transaction logs in X:\Program Files\Microsoft SQL Server
D) Check whether the MSSQLSERVER service is running
A) Verify the sqlserver.exe service is running on port 1433
B) Verify that dbsrv11.exe is listening on port 2638
C) Check the database transaction logs in X:\Program Files\Microsoft SQL Server
D) Check whether the MSSQLSERVER service is running

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
18
A company deploys Symantec Endpoint Protection (SEP) to50 virtual machines running on a single ESXi host. Which configuration change can the administrator make to minimize sudden IOPS impact on the ESXi server while each SEP endpoint communicates with the Symantec Endpoint Protection Manager?
A) Reduce number of content revisions to keep
B) Increase download randomization window
C) Reduce the heartbeat interval
D) Increase Download Insight sensitivity level
A) Reduce number of content revisions to keep
B) Increase download randomization window
C) Reduce the heartbeat interval
D) Increase Download Insight sensitivity level

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
19
Which protection engine should an administrator enable in order to drop malicious vulnerability scans against a client system?
A) SONAR
B) Intrusion Prevention
C) Application and Device Control
D) Tamper Protection
A) SONAR
B) Intrusion Prevention
C) Application and Device Control
D) Tamper Protection

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
20
An administrator is designing a new single site Symantec Endpoint Protection environment. Due to perimeter firewall bandwidth restrictions, the design needs to minimize the amount of traffic from content passing through the firewall. Which source must the administrator avoid using?
A) Group Update Provider (GUP)
B) LiveUpdate Administrator (LUA)
C) Symantec Endpoint Protection Manager
D) Shared Insight Cache (SIC)
A) Group Update Provider (GUP)
B) LiveUpdate Administrator (LUA)
C) Symantec Endpoint Protection Manager
D) Shared Insight Cache (SIC)

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
21
A Symantec Endpoint Protection (SEP) administrator receives multiple reports that machines are experiencing performance issues. The administrator discovers that the reports happen about the same time as the scheduled LiveUpdate. Which setting should the SEP administrator configure to minimize I/O when LiveUpdate occurs?
A) Disable Allow user-defined scans to run when the scan author is logged off
B) Change the LiveUpdate schedule
C) Disable Run an Active Scan when new definitions arrive
D) Change the Administrator-defined scan schedule
A) Disable Allow user-defined scans to run when the scan author is logged off
B) Change the LiveUpdate schedule
C) Disable Run an Active Scan when new definitions arrive
D) Change the Administrator-defined scan schedule

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
22
An administrator is responsible for the Symantec Endpoint Protection architecture of a large, multi-national company with three regionalized data centers. The administrator needs to collect data from clients; however, the collected data must stay in the local regional data center. Communication between the regional data centers is allowed 20 hours a day. How should the administrator architect this organization?
A) Set up 3 domains
B) Set up 3 sites
C) Set up 3 groups
D) Set up 3 locations
A) Set up 3 domains
B) Set up 3 sites
C) Set up 3 groups
D) Set up 3 locations

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
23
Which action must a Symantec Endpoint Protection administrator take before creating custom Intrusion Prevention signatures?
A) Define signature variables
B) Enable signature logging
C) Change the custom signature order
D) Create a Custom Intrusion Prevention Signature library
A) Define signature variables
B) Enable signature logging
C) Change the custom signature order
D) Create a Custom Intrusion Prevention Signature library

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
24
A company has 10,000 Symantec Endpoint Protection (SEP) clients deployed using two Symantec Endpoint Protection Managers (SEPMs). Which configuration is recommended to ensure that each SEPM is able to effectively handle the communications load with the SEP clients?
A) Pull mode
B) Push mode
C) Server control mode
D) Client control mode
A) Pull mode
B) Push mode
C) Server control mode
D) Client control mode

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
25
An administrator configures the scan duration for a scheduled scan. The scan fails to complete in the specified time period. When will the next scheduled scan occur on the computer?
A) When the computer restarts
B) At the next scheduled scan period
C) Within the next hour
D) When the user restarts the scan
A) When the computer restarts
B) At the next scheduled scan period
C) Within the next hour
D) When the user restarts the scan

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
26
What happens when the license expires in Symantec Endpoint Protection 14 Enterprise Edition?
A) Group Update Providers (GUP) stop
B) Symantec Insight is disabled
C) Content updates continue
D) LiveUpdate stops
A) Group Update Providers (GUP) stop
B) Symantec Insight is disabled
C) Content updates continue
D) LiveUpdate stops

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
27
Which option is unavailable in the Symantec Endpoint Protection console to run a command on the group menu item?
A) Disable SONAR
B) Scan
C) Disable Network Threat Protection
D) Update content and scan
A) Disable SONAR
B) Scan
C) Disable Network Threat Protection
D) Update content and scan

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
28
How are Insight results stored?
A) Encrypted on the Symantec Endpoint Protection Client
B) Unencrypted on the Symantec Endpoint Protection Manager
C) Encrypted on the Symantec Endpoint Protection Manager
D) Unencrypted on the Symantec Endpoint Protection Client
A) Encrypted on the Symantec Endpoint Protection Client
B) Unencrypted on the Symantec Endpoint Protection Manager
C) Encrypted on the Symantec Endpoint Protection Manager
D) Unencrypted on the Symantec Endpoint Protection Client

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
29
The LiveUpdate Download Schedule is set to the default on the Symantec Endpoint Protection Manager (SEPM). How many content revisions must the SEPM keep to ensure clients that check in to the SEPM every 10 days receive delta content packages instead of full content packages?
A) 10
B) 30
C) 20
D) 60
A) 10
B) 30
C) 20
D) 60

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
30
Which two are policy types within the Symantec Endpoint Protection Manager? (Select two.)
A) Intrusion Prevention
B) Exceptions
C) Process Control
D) Shared Insight
E) Host Protection
A) Intrusion Prevention
B) Exceptions
C) Process Control
D) Shared Insight
E) Host Protection

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
31
Which option is a function of the Symantec Endpoint Protection client?
A) Sends and receives application reputation ratings from LiveUpdate
B) Uploads logs to the Shared Insight Cache
C) Downloads virus content updates from Symantec Insight
D) Provides a Lotus Notes email scanner
A) Sends and receives application reputation ratings from LiveUpdate
B) Uploads logs to the Shared Insight Cache
C) Downloads virus content updates from Symantec Insight
D) Provides a Lotus Notes email scanner

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
32
What is a function of Symantec Insight?
A) Provides reputation ratings for binary executables.
B) Enhances the capability of Group Update Providers (GUP)
C) Provides reputation ratings for structured data
D) Increases the efficiency and effectiveness of LiveUpdate
A) Provides reputation ratings for binary executables.
B) Enhances the capability of Group Update Providers (GUP)
C) Provides reputation ratings for structured data
D) Increases the efficiency and effectiveness of LiveUpdate

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
33
Which two criteria can an administrator use to determine hosts in a host group? (Select two.)
A) Network Adapters
B) Network Services
C) Subnet
D) Application Protocol
E) DNS Domain
A) Network Adapters
B) Network Services
C) Subnet
D) Application Protocol
E) DNS Domain

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
34
Which two instances could cause Symantec Endpoint Protection to be unable to remediate a file? (Select two.)
A) Another scan is in progress.
B) The detected file is in use.
C) The file has good reputation.
D) There are insufficient file permissions.
E) The file is marked for deletion by Windows on restart.
A) Another scan is in progress.
B) The detected file is in use.
C) The file has good reputation.
D) There are insufficient file permissions.
E) The file is marked for deletion by Windows on restart.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
35
A Symantec Endpoint Protection administrator must block traffic from an attacking computer for a specific time period. Where should the administrator adjust the time to block the attacking computer?
A) In the group policy, under External Communication settings
B) In the group policy, under Communication settings
C) In the firewall policy, under Protection and Stealth
D) In the firewall policy, under Built in Rules
A) In the group policy, under External Communication settings
B) In the group policy, under Communication settings
C) In the firewall policy, under Protection and Stealth
D) In the firewall policy, under Built in Rules

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
36
Which two options are available when configuring DNS change detections for SONAR? (Select two.)
A) Log
B) Quarantine
C) Block
D) Active Response
E) Trace
A) Log
B) Quarantine
C) Block
D) Active Response
E) Trace

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
37
A company has a small number of systems in their Symantec Endpoint Protection Manager (SEPM) group with federal mandates that AntiVirus definitions undergo a two week testing period. After being loaded on the client, the tested virus definitions must remain unchanged on the client systems until the next set of virus definitions have completed testing. All other clients must remain operational on the most recent definition sets. An internal LiveUpdate Server has been considered as too expensive to be a solution for this company. What should be modified on the SEPM to meet this mandate?
A) The LiveUpdate Content policy for this group should be modified to use a specific definition revision.
B) The LiveUpdate Settings policy for this group should be modified to use an Explicit Group Update Provider.
C) The SEPM site LiveUpdate settings should be modified so the Number of content revisions to keep is set to 14.
D) The SEPM site LiveUpdate settings should be modified so the Number of content revisions to keep is set to 1.
A) The LiveUpdate Content policy for this group should be modified to use a specific definition revision.
B) The LiveUpdate Settings policy for this group should be modified to use an Explicit Group Update Provider.
C) The SEPM site LiveUpdate settings should be modified so the Number of content revisions to keep is set to 14.
D) The SEPM site LiveUpdate settings should be modified so the Number of content revisions to keep is set to 1.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
38
Which tool should the administrator run before starting the Symantec Endpoint Protection Manager upgrade according to best practices?
A) CollectLog.cmd
B) DBValidator.bat
C) LogExport.cmd
D) Upgrade.exe
A) CollectLog.cmd
B) DBValidator.bat
C) LogExport.cmd
D) Upgrade.exe

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
39
A company deploys Symantec Endpoint Protection client to its sales staff who travel across the country. Which deployment method should the company use to notify its sales staff to install the client?
A) Unmanaged Detector
B) Client Deployment Wizard
C) Pull mode
D) Push mode
A) Unmanaged Detector
B) Client Deployment Wizard
C) Pull mode
D) Push mode

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
40
A company allows users to create firewall rules. During the course of business, users are accidentally adding rules that block a custom internal application. Which steps should the Symantec Endpoint Protection administrator take to prevent users from blocking the custom application?
A) Create an Allow All Firewall rule for the fingerprint of the file and place it at the bottom of the firewall rules above the blue line
B) Create an Allow firewall rule for the application and place it at the bottom of the firewall rules below the blue line
C) Create an Allow for the network adapter type used by the application and place it at the top of the firewall rules below the blue line.
D) Create an Allow Firewall rule for the application and place it at the top of the firewall rules above the blue line.
A) Create an Allow All Firewall rule for the fingerprint of the file and place it at the bottom of the firewall rules above the blue line
B) Create an Allow firewall rule for the application and place it at the bottom of the firewall rules below the blue line
C) Create an Allow for the network adapter type used by the application and place it at the top of the firewall rules below the blue line.
D) Create an Allow Firewall rule for the application and place it at the top of the firewall rules above the blue line.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
41
Which action does the Shared Insight Cache (SIC) server take when the whitelist reaches maximum capacity?
A) The SIC server allocates additional memory for the whitelist as needed.
B) The SIC server will remove items with the fewest number of votes.
C) The SIC server will remove the least recently used items based on the prune size.
D) The SIC server will start writing the cache to disk.
A) The SIC server allocates additional memory for the whitelist as needed.
B) The SIC server will remove items with the fewest number of votes.
C) The SIC server will remove the least recently used items based on the prune size.
D) The SIC server will start writing the cache to disk.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
42
Which policy should an administrator modify to enable Virtual Image Exception (VIE) functionality?
A) Host Integrity Policy
B) Exceptions Policy
C) Virus and Spyware Protection Policy
D) Application and Device Control Policy
A) Host Integrity Policy
B) Exceptions Policy
C) Virus and Spyware Protection Policy
D) Application and Device Control Policy

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
43
A Symantec Endpoint Protection (SEP) client uses a management server list with three management servers in the priority 1 list. Which mechanism does the SEP client use to select an alternate management server if the currently selected management server is unavailable?
A) The client chooses the next server alphabetically by server name.
B) The client chooses another server alphabetically in the list randomly.
C) The client chooses a server with the next highest IP address.
D) The client chooses a server based on the lowest server load.
A) The client chooses the next server alphabetically by server name.
B) The client chooses another server alphabetically in the list randomly.
C) The client chooses a server with the next highest IP address.
D) The client chooses a server based on the lowest server load.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
44
A Symantec Endpoint Protection (SEP) administrator creates a firewall policy to block FTP traffic and assigns the policy to all of the SEP clients. The network monitoring team informs the administrator that a client system is making an FTP connection to a server. While investigating the problem from the SEP client GUI, the administrator notices that there are zero entries pertaining to FTP traffic in the SET Traffic log or Packet log. While viewing the Network Activity dialog, there is zero inbound/outbound traffic for the FTP process. What is the most likely reason?
A) The server is in the IPS policy excluded hosts list.
B) The block rule is below the blue line.
C) Peer-to-peer authentication is allowing the traffic.
D) The server has an IPS exception for that traffic.
A) The server is in the IPS policy excluded hosts list.
B) The block rule is below the blue line.
C) Peer-to-peer authentication is allowing the traffic.
D) The server has an IPS exception for that traffic.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
45
An administrator needs to increase the access speed for client files that are stored on a file server. Which configuration should the administrator review to address the read speed from the server?
A) Enable Network Cache in the client's Virus and Spyware Protection policy
B) Add the applicable server to a trusted host group
C) Enable download randomization in the client group's communication settings
D) Create a Firewall allow rule for the server's IP address.
A) Enable Network Cache in the client's Virus and Spyware Protection policy
B) Add the applicable server to a trusted host group
C) Enable download randomization in the client group's communication settings
D) Create a Firewall allow rule for the server's IP address.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
46
Which feature reduces the impact of Auto-Protect on a virtual client guest operating system?
A) Network Shared Insight Cache
B) Scan Randomization
C) Virtual Shared Insight Cache
D) Virtual Image Exception
A) Network Shared Insight Cache
B) Scan Randomization
C) Virtual Shared Insight Cache
D) Virtual Image Exception

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
47
Which settings can impact the Files trusted count? 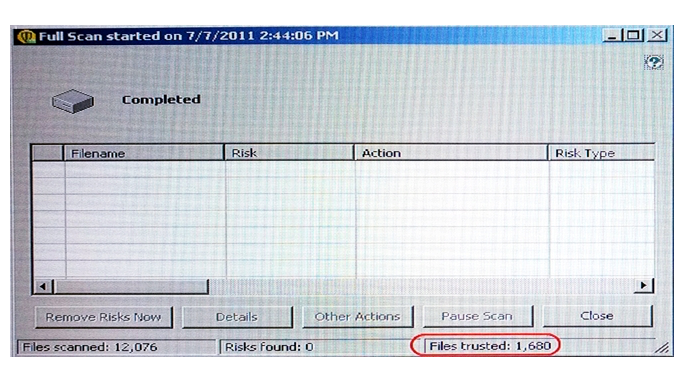
A) System Lockdown Whitelist in the Application and Device Control Policy
B) File Cache settings in the Virus and Spyware Protection policy
C) Insight settings in the Virus and Spyware Protection policy
D) SONAR settings in the Virus and Spyware Protection policy

A) System Lockdown Whitelist in the Application and Device Control Policy
B) File Cache settings in the Virus and Spyware Protection policy
C) Insight settings in the Virus and Spyware Protection policy
D) SONAR settings in the Virus and Spyware Protection policy

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
48
Where in the Symantec Endpoint Protection (SEP) management console will a SEP administrator find the option to allow all users to enable and disable the client firewall?
A) Settings in Intrusion Prevention Policy
B) Overview in Firewall Policy
C) Client User Interface Control Settings
D) System Lockdown in Group Policy
A) Settings in Intrusion Prevention Policy
B) Overview in Firewall Policy
C) Client User Interface Control Settings
D) System Lockdown in Group Policy

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
49
In addition to performance improvements, which two benefits does Insight provide? (Select two)
A) Reputation scoring for documents.
B) False positive migration.
C) Zero-day threat detection.
D) Blocks malicious websites.
E) Protects against malicious java scripts.
A) Reputation scoring for documents.
B) False positive migration.
C) Zero-day threat detection.
D) Blocks malicious websites.
E) Protects against malicious java scripts.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
50
In the virus and Spyware Protection policy, an administrator sets the First action to Clean risk and sets If first action fails to Delete risk? Which two factors should the administrator consider? (Select two.)
A) The deleted file may still be in the Recycle Bin.
B) IT Analytics may keep a copy of the file for investigation.
C) False positives may delete legitimate files.
D) Insights may back up the file before sending it to Symantec.
E) A copy of the threat may still be in the quarantine.
A) The deleted file may still be in the Recycle Bin.
B) IT Analytics may keep a copy of the file for investigation.
C) False positives may delete legitimate files.
D) Insights may back up the file before sending it to Symantec.
E) A copy of the threat may still be in the quarantine.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
51
A Symantec Endpoint Protection administrator is using System Lockdown in blacklist mode with a file fingerprint list. When testing a client, the administrator notices that at least one of the files is allowed to execute. What is the likely cause of the problem?
A) The application has been upgraded.
B) The Application and Device Control policy is in the test mode.
C) A file exception has been added to the Exceptions policy.
D) The Application and Device Control policy is allowing the file to execute.
A) The application has been upgraded.
B) The Application and Device Control policy is in the test mode.
C) A file exception has been added to the Exceptions policy.
D) The Application and Device Control policy is allowing the file to execute.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
52
A company plans to install six Symantec Endpoint Protection Managers (SEPMs) spread evenly across two sites. The administrator needs to direct replication activity to SEPM3 server in Site 1 and SEPM4 in Site 2. Which two actions should the administrator take to direct replication activity to SEPM3 and SEPM4? (Select two.)
A) Install the SQL Server databases on SEPM3 and SEPM4
B) Ensure SEPM3 and SEPM4 are in the same time zone
C) Ensure SEPM3 and SEPM4 are defined as remote servers in the replication partner configuration
D) Install SEPM3 and SEPM4 after the other SEPMs
E) Ensure SEPM3 and SEPM4 are defined as the top priority server in in the Site Settings
A) Install the SQL Server databases on SEPM3 and SEPM4
B) Ensure SEPM3 and SEPM4 are in the same time zone
C) Ensure SEPM3 and SEPM4 are defined as remote servers in the replication partner configuration
D) Install SEPM3 and SEPM4 after the other SEPMs
E) Ensure SEPM3 and SEPM4 are defined as the top priority server in in the Site Settings

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
53
In which two areas can host groups be used? (Select two.)
A) Locations
B) Download Insight
C) IPS
D) Application and Device Control
E) Firewall
A) Locations
B) Download Insight
C) IPS
D) Application and Device Control
E) Firewall

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
54
Catastrophic hardware failure has occurred on a single Symantec Endpoint Protection Manager (SEPM) in an environment with two SEPMs. What is the quickest way an administrator can restore the environment to its original state?
A) Install a new SEPM into the existing site
B) Reinstall the entire SEPM environment
C) Clone the still functioning SEPM and change the server.properties file
D) Build a new site and configure replication with the still functioning SEPM
A) Install a new SEPM into the existing site
B) Reinstall the entire SEPM environment
C) Clone the still functioning SEPM and change the server.properties file
D) Build a new site and configure replication with the still functioning SEPM

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
55
Which action does SONAR take before convicting a process?
A) Checks the reputation of the process.
B) Restarts the system.
C) Quarantines the process.
D) Blocks suspicious behavior.
A) Checks the reputation of the process.
B) Restarts the system.
C) Quarantines the process.
D) Blocks suspicious behavior.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
56
Which Symantec Endpoint Protection defense mechanism provides protection against threats that propagate from system to system through the use of autorun.inf files?
A) Host Integrity
B) SONAR
C) Application and Device Control
D) Emulator
A) Host Integrity
B) SONAR
C) Application and Device Control
D) Emulator

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
57
Which setting can an administrator configure in the LiveUpdate policy?
A) Linux Settings
B) Frequency to download content.
C) Specific content revision to download from a Group Update Provider (GUP)
D) Specific content policies to download
A) Linux Settings
B) Frequency to download content.
C) Specific content revision to download from a Group Update Provider (GUP)
D) Specific content policies to download

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
58
Which action should an administrator take to prevent users from using Windows Security Center?
A) Set Disable antivirus alert within Windows Security Center to Disable
B) Set Disable Windows Security Center to Always
C) Set Disable Windows Security Center to Disable
D) Set Disable antivirus alert within Windows Security Center to Never
A) Set Disable antivirus alert within Windows Security Center to Disable
B) Set Disable Windows Security Center to Always
C) Set Disable Windows Security Center to Disable
D) Set Disable antivirus alert within Windows Security Center to Never

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
59
A large-scale virus attack is occurring and a notification condition is configured to send an email whenever viruses infect five computers on the network. A Symantec Endpoint Protection administrator has set a one hour damper period for that notification condition. How many notifications dos the administrator receive after 30 computers are infected in two hours?
A) 1
B) 15
C) 6
D) 2
A) 1
B) 15
C) 6
D) 2

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
60
An administrator is re-adding an existing Replication Partner to the local Symantec Endpoint Protection Manager site. Which two parameters are required to re-establish this replication partnership? (Select two.)
A) Remote site Encryption Password
B) Remote server IP Address and port
C) Remote SQL database account credentials
D) Remote server Administrator credentials
E) Remote site Domain ID
A) Remote site Encryption Password
B) Remote server IP Address and port
C) Remote SQL database account credentials
D) Remote server Administrator credentials
E) Remote site Domain ID

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
61
Which technology can prevent an unknown executable from being downloaded through a browser session?
A) Insight
B) Advanced Machine Learning
C) Application Control
D) Intrusion Prevention
A) Insight
B) Advanced Machine Learning
C) Application Control
D) Intrusion Prevention

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
62
Why does Power Eraser need Internet access?
A) Validate root certificates on all portable executables (PXE) files
B) Leverage Symantec Insight
C) Ensure the Power Eraser tool is the latest release
D) Look up CVE vulnerabilities
A) Validate root certificates on all portable executables (PXE) files
B) Leverage Symantec Insight
C) Ensure the Power Eraser tool is the latest release
D) Look up CVE vulnerabilities

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
63
Why is Notepad unable to save the changes to the file in the image below? 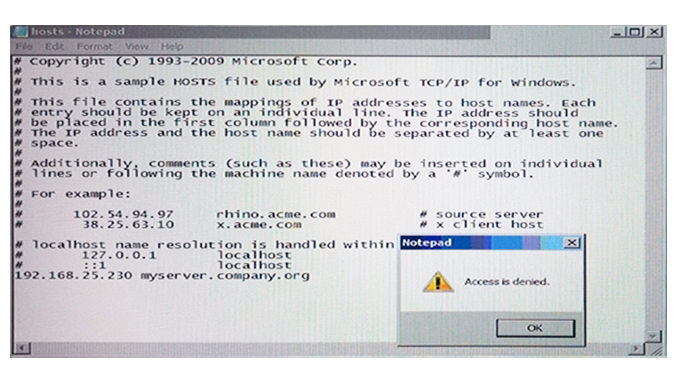
A) SONAR High Risk detection is set to Block
B) SONAR is set to block host file modifications.
C) Tamper Protection is preventing Notepad from modifying the host file.
D) System Lockdown is enabled.

A) SONAR High Risk detection is set to Block
B) SONAR is set to block host file modifications.
C) Tamper Protection is preventing Notepad from modifying the host file.
D) System Lockdown is enabled.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
64
Which Symantec Endpoint Protection technology blocks a downloaded program from installing browser plugins?
A) Intrusion Prevention
B) SONAR
C) Tamper Protection
D) Application and Device Control
A) Intrusion Prevention
B) SONAR
C) Tamper Protection
D) Application and Device Control

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
65
Which object in the Symantec Endpoint Protection Manager console describes the most granular level to which a policy can be assigned?
A) Group
B) User
C) Client
D) Computer
A) Group
B) User
C) Client
D) Computer

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
66
A system running Symantec Protection is assigned to a group with client user interface control settings set to mixed mode with Auto-Protect options set to Client. The user on the system is unable to turn off Auto-Protect. What is likely cause of this problem?
A) Application and Device Control is configured.
B) System Lockdown is enabled.
C) Tamper protection is enabled.
D) The padlock on the enable Auto-Protect option is locked.
A) Application and Device Control is configured.
B) System Lockdown is enabled.
C) Tamper protection is enabled.
D) The padlock on the enable Auto-Protect option is locked.

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
67
An administrator selects the Backup files before attempting to repair the Remediations option in the Auto-Protect policies. Which two actions occur when a virus is detected? (Select two.)
A) Send the file to Symantec Insight
B) Check the reputation
C) Encrypt the file
D) Replace the file with a place holder
E) Store in Quarantine folder
A) Send the file to Symantec Insight
B) Check the reputation
C) Encrypt the file
D) Replace the file with a place holder
E) Store in Quarantine folder

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
68
Which two criteria could be used to define Location Awareness for the Symantec Endpoint Protection (SEP) client? (Choose two.)
A) geographic location
B) NIC description
C) SEP domain
D) Network Speed
E) WINS server
A) geographic location
B) NIC description
C) SEP domain
D) Network Speed
E) WINS server

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
69
An administrator receives a browser certificate warning when accessing the Symantec Endpoint Protection Manager (SEPM) Web console. Where can the administrator obtain the certificate?
A) SEPM Web Access
B) SEPM SecureID Authentication
C) SEPM console Admin Tasks
D) SEPM console Licenses section
A) SEPM Web Access
B) SEPM SecureID Authentication
C) SEPM console Admin Tasks
D) SEPM console Licenses section

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
70
A company uses a remote administration tool that is detected as Hacktool.KeyLoggPro and quarantined by Symantec Endpoint Protection (SEP). Which step can an administrator perform to continue using the remote administration tool without detection by SEP?
A) Create a Tamper Protect exception for the tool
B) Create a SONAR exception for the tool
C) Create an Application to Monitor exception for the tool
D) Create a Known Risk exception for the tool
A) Create a Tamper Protect exception for the tool
B) Create a SONAR exception for the tool
C) Create an Application to Monitor exception for the tool
D) Create a Known Risk exception for the tool

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
71
Which two criteria are used by Symantec Insight to evaluate binary executables? (Select two.)
A) Age
B) Prevalence
C) Sensitivity
D) Confidentiality
E) Content
A) Age
B) Prevalence
C) Sensitivity
D) Confidentiality
E) Content

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
72
Administrators at a company share a single terminal for configuring Symantec Endpoint Protection. The administrators want to ensure that each administrator using the console is forced to authenticate using their individual credentials. They are concerned that administrators may forget the log off the terminal, which would easily allow the others to gain access to the Symantec Endpoint Protection Manager (SEPM) console. Which setting should the administrator disable to minimize the risk of non-authorized users logging into the SEPM console?
A) Allow administrators to reset the passwords
B) Delete clients that have not connected for specified time
C) Allow users to save credentials when logging on
D) Lock account after the specified number of unsuccessful logon attempts
A) Allow administrators to reset the passwords
B) Delete clients that have not connected for specified time
C) Allow users to save credentials when logging on
D) Lock account after the specified number of unsuccessful logon attempts

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
73
Which client log shows that a client is downloading content from its designated source?
A) Log.LiveUpdate
B) System Log
C) Risk Log
D) SesmLu.log
A) Log.LiveUpdate
B) System Log
C) Risk Log
D) SesmLu.log

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
74
A company has an application that requires network traffic in both directions to multiple systems at a specific external domain. A firewall rule was created to allow traffic to and from the external domain, but the rule is blocking incoming traffic. What should an administrator enable in the firewall policy to allow this traffic?
A) Reverse DNS Lookup
B) TCP resequencing
C) Smart DHCP
D) Smart WINS
A) Reverse DNS Lookup
B) TCP resequencing
C) Smart DHCP
D) Smart WINS

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
75
A company needs to configure an Application and Device Control policy to block read/write access to all USB removable media on its Symantec Endpoint Protection (SEP) systems. Which tool should an administrator use to format the GUID and device IDs as required by SEP?
A) CheckSum.exe
B) DevViewer.exe
C) TaskMgr.exe
D) DeviceTree.exe
A) CheckSum.exe
B) DevViewer.exe
C) TaskMgr.exe
D) DeviceTree.exe

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
76
A financial company enforces a security policy that prevents banking system workstations from connecting to the Internet. Which Symantec Endpoint Protection technology is ineffective on this company's workstations?
A) Insight
B) Network Threat Protection
C) Browser Intrusion Prevention
D) Intrusion Prevention
A) Insight
B) Network Threat Protection
C) Browser Intrusion Prevention
D) Intrusion Prevention

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
77
Which package type should an administrator use to reduce a SEP environment's footprint when considering that new SEP 14 clients will be installed on point of sale terminals?
A) Default Standard Client
B) Default Embedded or VDI client
C) Default dark network client
D) Custom Standard client
A) Default Standard Client
B) Default Embedded or VDI client
C) Default dark network client
D) Custom Standard client

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
78
Which protection technology can detect botnet command and control traffic generated on the Symantec Endpoint Protection client machine?
A) Intrusion Prevention
B) Insight
C) Risk Tracer
D) SONAR
A) Intrusion Prevention
B) Insight
C) Risk Tracer
D) SONAR

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
79
A Symantec Endpoint Protection (SEP) administrator performed a disaster recovery without a database backup. In which file should the SEP administrator add "scm.agent.groupcreation=true" to enable the automatic creation of client groups?
A) conf.properties
B) httpd.conf
C) settings.conf
D) catalina.out
A) conf.properties
B) httpd.conf
C) settings.conf
D) catalina.out

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck
80
An administrator is recovering from a Symantec Endpoint Manager (SEPM) site failure. Which file should the administrator use during an install of SEPM to recover the lost environment according to Symantec Disaster Recovery Best Practice documentation?
A) Original installation log
B) Sylink.xml file from the SEPM
C) Settings.properties file
D) Recovery_timestamp file
A) Original installation log
B) Sylink.xml file from the SEPM
C) Settings.properties file
D) Recovery_timestamp file

Unlock Deck
Unlock for access to all 113 flashcards in this deck.
Unlock Deck
k this deck



