Deck 21: Aruba Certified Mobility Expert Written Exam
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/32
Play
Full screen (f)
Deck 21: Aruba Certified Mobility Expert Written Exam
1
A customer wants a WLAN solution that permits Aps to terminate WPA-2 encrypted traffic from different SSIDs to different geographic locations where non-related IT departments will take care of enforcing security policies. A key requirement is to minimize network congestion, overhead, and delay while providing data privacy from the client to the security policy enforcement point. Therefore, the solution must use the shortest path from source to destination. Which Aruba feature best accommodates this scenario?
A) Inter MC S2S IPsec tunnels
B) RAPs
C) Multizone Aps
D) VIA
E) Inter MC GRE tunnels
A) Inter MC S2S IPsec tunnels
B) RAPs
C) Multizone Aps
D) VIA
E) Inter MC GRE tunnels
RAPs
2
Users run encrypted Skype for Business traffic with no WMM support over an Aruba Mobility Master (MM) - Mobility Controller (MC) based network. When voice, video, and application sharing traffic arrive at the wired side of the network, all the flows look alike due to the lack of L2 and L3 markings How can the network administrator identify these flows and mark QoS accordingly?
A) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable WMM in a VAP profile.
B) Use a media firewall policy that match these three flows, and use permit and TOS actions with 56, 40, and 34 values for voice, video, and application sharing, respectively. Then enable the Skype4Business ALG in the UCC profiles.
C) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable the Skype4Business ALG in the UCC profiles.
D) Confirm the MM is the Openflow controller of the MCs and Openflow is enabled in VAP and the firewall roles. Then integrate the MM with the Skype4Business SDN API, and enable the Skype4Business ALG in the UCC profiles.
A) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable WMM in a VAP profile.
B) Use a media firewall policy that match these three flows, and use permit and TOS actions with 56, 40, and 34 values for voice, video, and application sharing, respectively. Then enable the Skype4Business ALG in the UCC profiles.
C) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and the firewall roles. Then enable the Skype4Business ALG in the UCC profiles.
D) Confirm the MM is the Openflow controller of the MCs and Openflow is enabled in VAP and the firewall roles. Then integrate the MM with the Skype4Business SDN API, and enable the Skype4Business ALG in the UCC profiles.
Confirm the MM is the Openflow controller of the MCs and Openflow is enabled in VAP and the firewall roles. Then integrate the MM with the Skype4Business SDN API, and enable the Skype4Business ALG in the UCC profiles.
3
An Aruba WiFi solution for a football stadium includes 2500 APs, two Mobility Masters (MM), and eight Mobility Controllers (MCs). Key requirements are seamless roaming and even distribution of APs and clients, even during a MC failure. Which MC's deployment option offers seamless roaming, and even AP client distribution among all MCs before and after a MC failure?
A) a two-member HA group in dual mode
B) an eight-member L2-connected cluster
C) two four-member L2-connected clusters
D) an eight-member HA group in dual mode
A) a two-member HA group in dual mode
B) an eight-member L2-connected cluster
C) two four-member L2-connected clusters
D) an eight-member HA group in dual mode
two four-member L2-connected clusters
4
A company plans to build a resort that includes a hotel with 1610 rooms, a casino, and a convention center. The company is interested in a mobility solution that provides scalability and a service-based approach, where they can rent the WLAN infrastructure at the convention center to any customer (tenant) that hosts events at the resort. The solution should provide: • Seamless roaming when users move from the hotel to the casino or the convention center • Simultaneous propagation of the resort and customer-owned SSIDs at the convention center • Null management access upon resort network infrastructure to the customers (tenants) • Configuration and monitor rights of rented SSIDs to the customers (tenants) Which deployment meets the requirements?
A) Deploy an MM-MC infrastructure with multizone AP's, with one zone for tenant SSIDs.
B) Deploy IAPs along with AirWave, and deploy role-based management access control.
C) Deploy IAPs with zone based SSIDs and manage them with different central accounts.
D) Deploy an MM-MC infrastructure, and create different hierarchy groups for MCs and APs.
E) Deploy IAPs, and manage them with different central accounts.
A) Deploy an MM-MC infrastructure with multizone AP's, with one zone for tenant SSIDs.
B) Deploy IAPs along with AirWave, and deploy role-based management access control.
C) Deploy IAPs with zone based SSIDs and manage them with different central accounts.
D) Deploy an MM-MC infrastructure, and create different hierarchy groups for MCs and APs.
E) Deploy IAPs, and manage them with different central accounts.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
5
A fully functional WLAN is deployed in a campus network using the following script. 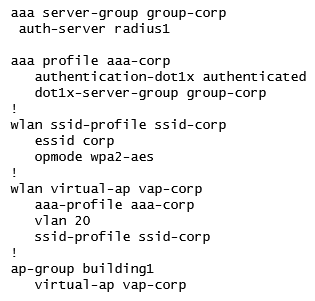 Which part of the script can a network administrator re-use to assign a different default role to users when they connect to the same SSID in a second building?
Which part of the script can a network administrator re-use to assign a different default role to users when they connect to the same SSID in a second building?
A) server group and ssid profile
B) server group and VAP profile
C) server group, aaa profile, and ssid profile
D) server group and VAP
 Which part of the script can a network administrator re-use to assign a different default role to users when they connect to the same SSID in a second building?
Which part of the script can a network administrator re-use to assign a different default role to users when they connect to the same SSID in a second building?A) server group and ssid profile
B) server group and VAP profile
C) server group, aaa profile, and ssid profile
D) server group and VAP

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
6
Refer to the exhibit: 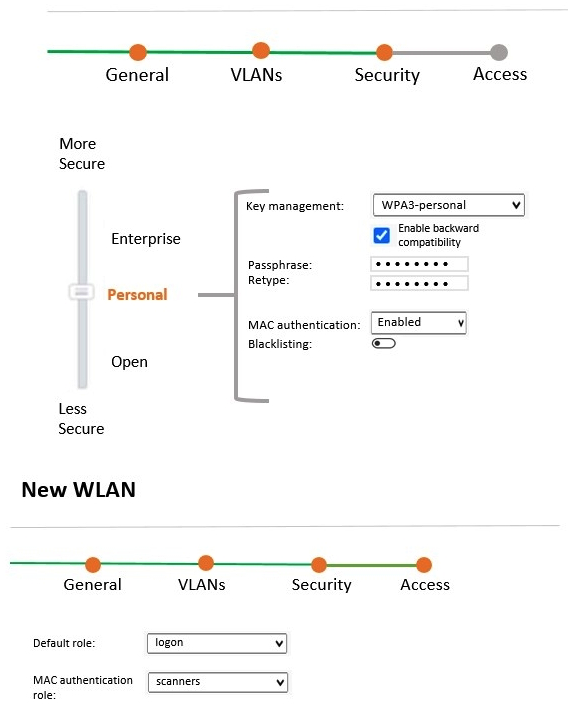 A company acquires ten barcode scanners to run inventory tasks. These WiFi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?
A company acquires ten barcode scanners to run inventory tasks. These WiFi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?
A) Set internal as the MAC authentication server group.
B) Add scanner MAC addresses in user derivation rules.
C) Enable L2 Authentication Fail Through.
D) Add scanner MAC addresses in the internal database.
 A company acquires ten barcode scanners to run inventory tasks. These WiFi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?
A company acquires ten barcode scanners to run inventory tasks. These WiFi devices support WPA2-PSK security only. The network administrator deploys a WLAN named scanners using the configuration shown in the exhibit. What must the network administrator do next to ensure that the scanner devices successfully connect to their SSID?A) Set internal as the MAC authentication server group.
B) Add scanner MAC addresses in user derivation rules.
C) Enable L2 Authentication Fail Through.
D) Add scanner MAC addresses in the internal database.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
7
A network administrator is in charge of a Mobility Master (MM) - Mobility Controller (MC) based WLAN. The administrator has deployed an Airwave Management Platform (AMP) server in order to improve the monitoring capabilities and generate reports and alerts. The administrator has configured SNMPv3 and Admin credentials on both the MMs and MCs and has created Groups and Folders in the AMP server. What two additional steps must the administrator do in order to let Airwave monitor the network devices? (Choose two.)
A) Manually add the Active MM and wait for automatic Discovery.
B) Map the AMP's IP address with a mgmt-config profile in the MM.
C) Set the AMP's IP address and Org string as DHCP option 43.
D) Manually add each MM, MC and Access Point in the AMP server.
E) Move "New" devices into a group and folder in Airwave.
A) Manually add the Active MM and wait for automatic Discovery.
B) Map the AMP's IP address with a mgmt-config profile in the MM.
C) Set the AMP's IP address and Org string as DHCP option 43.
D) Manually add each MM, MC and Access Point in the AMP server.
E) Move "New" devices into a group and folder in Airwave.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
8
A software development company has 764 employees who work from home. The company also has small offices located in different cities throughout the world. During working hours, they use RAPs to connect to a datacenter to upload software code as well as interact with databases. In the past two month, cabling issues have occurred connection to the 7240XM Mobility Controller (MC) that runs ArubaOS 8 and terminates the RAPs. These RAPs disconnect, affecting the users connected to the RAPs. This also causes problems with code uploads and database synchronizations. Therefore, the company decides to add a second 7240XM controller for redundancy. How should the network administrator deploy both controllers in order to provide the redundancy while preventing failover events from disconnecting users?
A) Connect both controllers with common VLANs, and create an HA fast failover group with public addresses in the internet VLAN.
B) Connect both controllers with common VLANs, and create an L2-connected cluster using public addresses in the internet VLAN.
C) Connect both controllers with different VLANs, and create an L2-connected cluster using public addresses in the internet VLAN.
D) Connect both controllers with common VLANs, and configure LMS/BLMS values equal to public addresses in the internet VLAN.
A) Connect both controllers with common VLANs, and create an HA fast failover group with public addresses in the internet VLAN.
B) Connect both controllers with common VLANs, and create an L2-connected cluster using public addresses in the internet VLAN.
C) Connect both controllers with different VLANs, and create an L2-connected cluster using public addresses in the internet VLAN.
D) Connect both controllers with common VLANs, and configure LMS/BLMS values equal to public addresses in the internet VLAN.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
9
Refer to the exhibit. 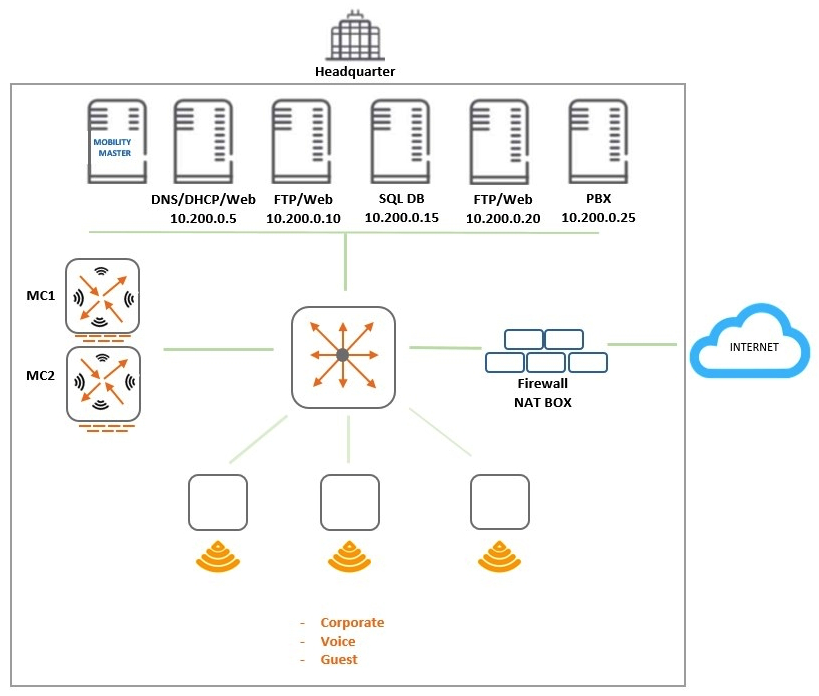 An organization provides WiFi access through a corporate SSID with an Aruba Mobility Master (MM) - Mobility Controller (MC) network that includes PEF functions. The organization wants to have a single firewall policy configured and applied to the employee role. This policy must allow users to reach Web, FTP, and DNS services, as shown in the exhibit. Other services should be exclusive to other roles. The client NICs should receive IP settings dynamically. Which policy design meets the organization's requirements while minimizing the number of policy rules?
An organization provides WiFi access through a corporate SSID with an Aruba Mobility Master (MM) - Mobility Controller (MC) network that includes PEF functions. The organization wants to have a single firewall policy configured and applied to the employee role. This policy must allow users to reach Web, FTP, and DNS services, as shown in the exhibit. Other services should be exclusive to other roles. The client NICs should receive IP settings dynamically. Which policy design meets the organization's requirements while minimizing the number of policy rules?
A)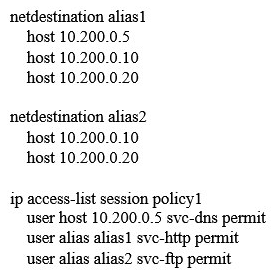
B)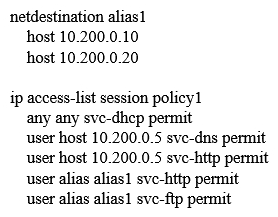
C)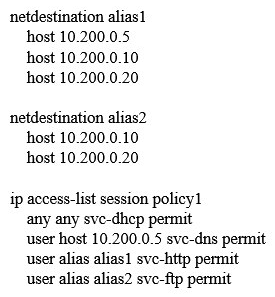
D)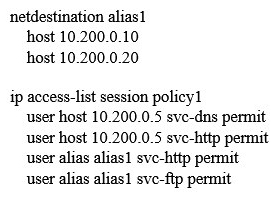
 An organization provides WiFi access through a corporate SSID with an Aruba Mobility Master (MM) - Mobility Controller (MC) network that includes PEF functions. The organization wants to have a single firewall policy configured and applied to the employee role. This policy must allow users to reach Web, FTP, and DNS services, as shown in the exhibit. Other services should be exclusive to other roles. The client NICs should receive IP settings dynamically. Which policy design meets the organization's requirements while minimizing the number of policy rules?
An organization provides WiFi access through a corporate SSID with an Aruba Mobility Master (MM) - Mobility Controller (MC) network that includes PEF functions. The organization wants to have a single firewall policy configured and applied to the employee role. This policy must allow users to reach Web, FTP, and DNS services, as shown in the exhibit. Other services should be exclusive to other roles. The client NICs should receive IP settings dynamically. Which policy design meets the organization's requirements while minimizing the number of policy rules?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
10
A company with 50 small coffee shops in a single country requires a single mobility solution that solves connectivity needs at both the main office and branch locations. Coffee shops must be provisioned with local WiFi internet access for customers. The shops must also have a private WLAN that offers communication to resources at the main office to upload sales, request supplies through a computer system, and make phone calls if needed. In order to simplify network operations, network devices at the coffee shops should be cloud managed. Which technologies best meet the company needs at the lowest cost?
A) IAP VPN
B) SD-Branch
C) Activate with RAPs
D) BOC with CAPs
A) IAP VPN
B) SD-Branch
C) Activate with RAPs
D) BOC with CAPs

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
11
A network administrator has racked up a 7210 Mobility Controller (MC) that will be terminating 200+ Aps on a medium-size branch office. Next, the technician cabled the appliance with 4SPF+ Direct Attached Cables (DACs) distributed between two-member switching stack and powered it up. What must the administrator do next in the MCs to assure maximum wired bandwidth utilization?
A) Map the four physical ports to port channel 0.
B) Disable spanning tree and allocate unique VLANs to each port.
C) Manually set 10Gbps speeds on all ports.
D) Configure the same MSTP region that the switches have.
E) Make all ports trunk interfaces and permit data VLANs.
A) Map the four physical ports to port channel 0.
B) Disable spanning tree and allocate unique VLANs to each port.
C) Manually set 10Gbps speeds on all ports.
D) Configure the same MSTP region that the switches have.
E) Make all ports trunk interfaces and permit data VLANs.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
12
Refer to the exhibit. 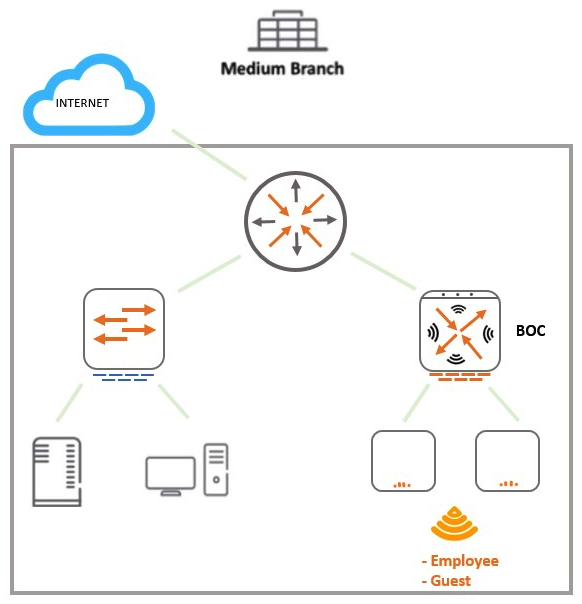 A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Choose two.)
A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Choose two.)
A) Configure all ports of the BOC as access ports on the controller VLAN, and change the gateway of clients to the core router IP.
B) Configure the uplink of the BOC as an access port on the controller VLAN, and add static routes in the router for the SSID VLAN subnets.
C) Configure the uplink of the BOC as a trunk port that permits the controller and the SSID VLANs. The controller VLAN must be native.
D) Configure the uplink of the BOC as an access port on the controller VLAN, and enable NAT for the SSID VLANs.
E) Configure the uplink of the BOC as a trunk port, tagging the controller and the SSOD VLANs, and enable NAT for the SSID VLANs.
 A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Choose two.)
A 7008 Branch Office Controller (BOC) is deployed in a remote office behind a core router. This core does not support 802.1q encapsulation. The Mobility Controller (MC) is the gateway for two tunneling mode SSIDs, as shown in the exhibit. Which two different configuration options ensure that wireless users are able to reach the branch network through the router? (Choose two.)A) Configure all ports of the BOC as access ports on the controller VLAN, and change the gateway of clients to the core router IP.
B) Configure the uplink of the BOC as an access port on the controller VLAN, and add static routes in the router for the SSID VLAN subnets.
C) Configure the uplink of the BOC as a trunk port that permits the controller and the SSID VLANs. The controller VLAN must be native.
D) Configure the uplink of the BOC as an access port on the controller VLAN, and enable NAT for the SSID VLANs.
E) Configure the uplink of the BOC as a trunk port, tagging the controller and the SSOD VLANs, and enable NAT for the SSID VLANs.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
13
Refer to the exhibits. Exhibit 1 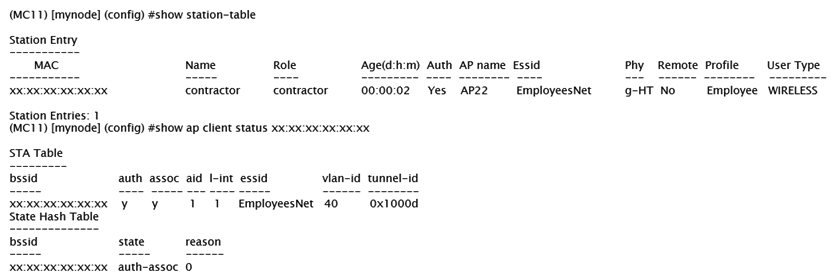 Exhibit 2
Exhibit 2 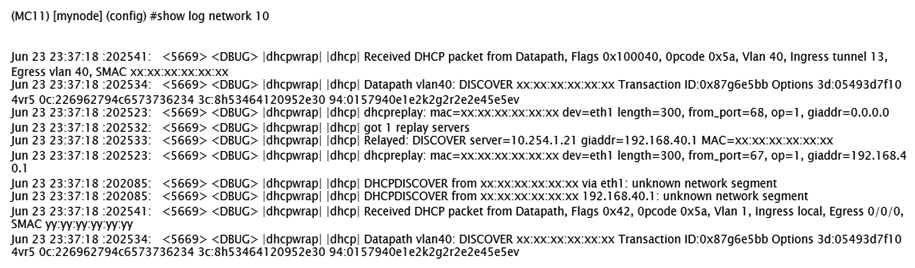 Exhibit 3
Exhibit 3 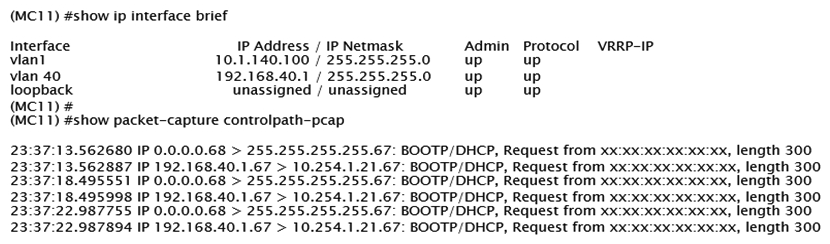 A network administrator wants to allow contractors to access the corporate WLAN named EmployeesNet with the contractor role in VLAN 40. When users connect, they do not seem to get an IP address. After some verification checks, the network administrator confirms the DHCP server (10.254.1.21) is reachable from the Mobility Controller (MC) and obtains the outputs shown in the exhibits. What should the network administrator do next to troubleshoot this problem?
A network administrator wants to allow contractors to access the corporate WLAN named EmployeesNet with the contractor role in VLAN 40. When users connect, they do not seem to get an IP address. After some verification checks, the network administrator confirms the DHCP server (10.254.1.21) is reachable from the Mobility Controller (MC) and obtains the outputs shown in the exhibits. What should the network administrator do next to troubleshoot this problem?
A) Permit UDP67 to the contractor role.
B) Remove the IP address in VLAN 40.
C) Configure the DHCP helper address.
D) Confirm there is an IP pool for VLAN 40.
 Exhibit 2
Exhibit 2  Exhibit 3
Exhibit 3  A network administrator wants to allow contractors to access the corporate WLAN named EmployeesNet with the contractor role in VLAN 40. When users connect, they do not seem to get an IP address. After some verification checks, the network administrator confirms the DHCP server (10.254.1.21) is reachable from the Mobility Controller (MC) and obtains the outputs shown in the exhibits. What should the network administrator do next to troubleshoot this problem?
A network administrator wants to allow contractors to access the corporate WLAN named EmployeesNet with the contractor role in VLAN 40. When users connect, they do not seem to get an IP address. After some verification checks, the network administrator confirms the DHCP server (10.254.1.21) is reachable from the Mobility Controller (MC) and obtains the outputs shown in the exhibits. What should the network administrator do next to troubleshoot this problem?A) Permit UDP67 to the contractor role.
B) Remove the IP address in VLAN 40.
C) Configure the DHCP helper address.
D) Confirm there is an IP pool for VLAN 40.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
14
Refer to the exhibit. 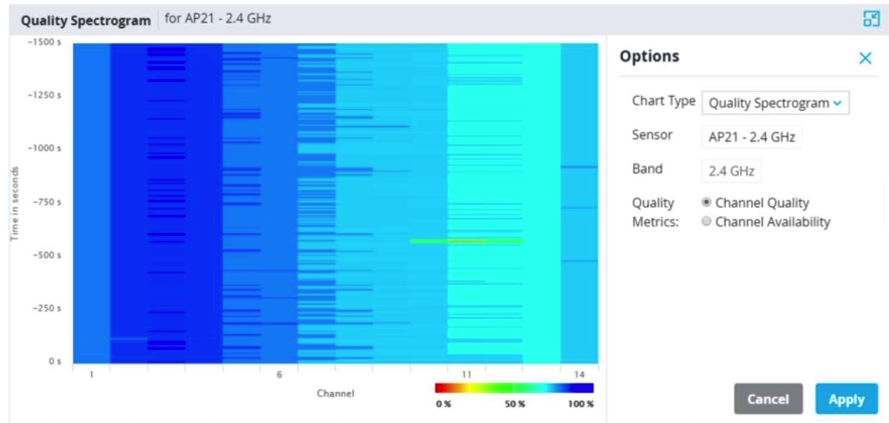 Based on the output shown in the exhibit, which channel offers the highest quality?
Based on the output shown in the exhibit, which channel offers the highest quality?
A) Channel 1
B) Channel 6
C) Channel 11
D) Channel 14
 Based on the output shown in the exhibit, which channel offers the highest quality?
Based on the output shown in the exhibit, which channel offers the highest quality?A) Channel 1
B) Channel 6
C) Channel 11
D) Channel 14

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
15
An Aruba Mobility Master (MM) - Mobility Controller (MC) solution is connected to a wired network that is ready to prioritize DSCP marked traffic. A group of WMM-enabled clients sends traffic marked at L2 only. What must the network administrator do to map those markings to DSCP equivalent values when traffic is received by the APs?
A) Enable WMM in the SSID profile.
B) Enable WMM in the VAP profile.
C) Enable Skype4Business ALG Support.
D) Enable traffic to be marked with session ACLs.
A) Enable WMM in the SSID profile.
B) Enable WMM in the VAP profile.
C) Enable Skype4Business ALG Support.
D) Enable traffic to be marked with session ACLs.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
16
Refer to the exhibit. 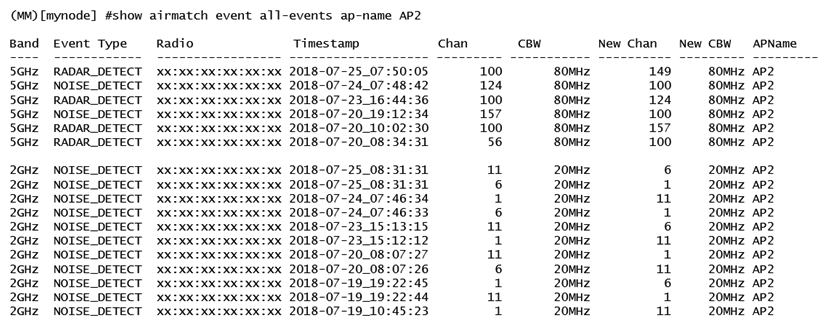 A network administrator deploys a Mobility Master (MM) - Mobility Controller (MC) network with Aps in different locations. Users in one of the locations report that the WiFi network works fine for several hours, and then they are suddenly disconnected. This symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?
A network administrator deploys a Mobility Master (MM) - Mobility Controller (MC) network with Aps in different locations. Users in one of the locations report that the WiFi network works fine for several hours, and then they are suddenly disconnected. This symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?
A) Adaptive Radio Management is reacting to RF events.
B) AirMatch is applying a scheduled optimization solution.
C) Users in the 2.4 GHz band are being affected by high interference.
D) AirMatch is reacting to non-scheduled RF events.
 A network administrator deploys a Mobility Master (MM) - Mobility Controller (MC) network with Aps in different locations. Users in one of the locations report that the WiFi network works fine for several hours, and then they are suddenly disconnected. This symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?
A network administrator deploys a Mobility Master (MM) - Mobility Controller (MC) network with Aps in different locations. Users in one of the locations report that the WiFi network works fine for several hours, and then they are suddenly disconnected. This symptom may happen at any time, up to three times every day, and lasts no more than two minutes. After some research, the network administrator logs into the MM and reviews the output shown in the exhibit. Based on this information, what is the most likely reason users get disconnected?A) Adaptive Radio Management is reacting to RF events.
B) AirMatch is applying a scheduled optimization solution.
C) Users in the 2.4 GHz band are being affected by high interference.
D) AirMatch is reacting to non-scheduled RF events.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
17
Refer to the exhibits. Exhibit 1  Exhibit 2
Exhibit 2  Exhibit 3
Exhibit 3  Exhibit 4
Exhibit 4 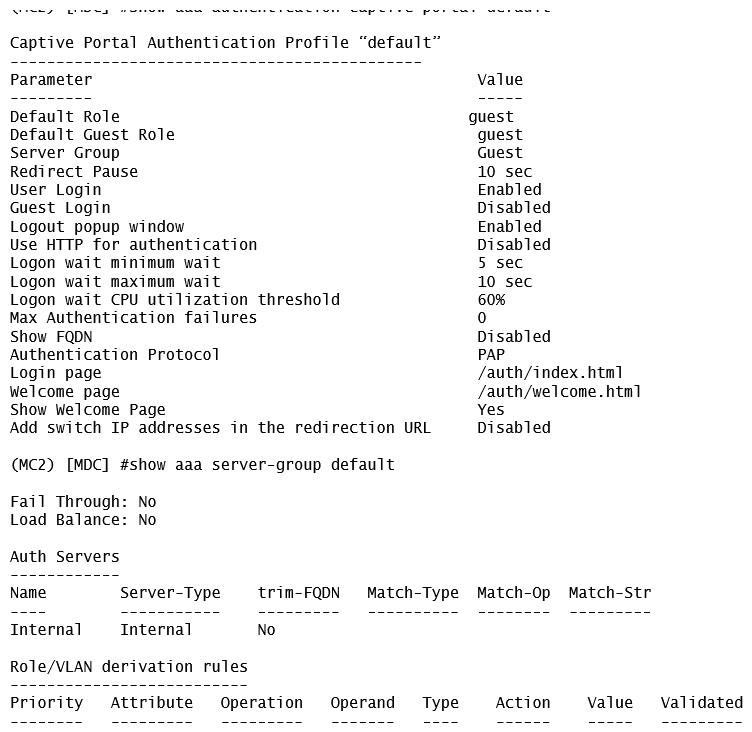 A captive portal-based solution is deployed in a Mobility Master (MM) - Mobility Controller (MC) network. A wireless station connects to the network and attempts the authentication process. The outputs are shown in the exhibits. Which names correlate with the authentication and captive portal servers?
A captive portal-based solution is deployed in a Mobility Master (MM) - Mobility Controller (MC) network. A wireless station connects to the network and attempts the authentication process. The outputs are shown in the exhibits. Which names correlate with the authentication and captive portal servers?
A) ClearPass.23 is the authentication server, and cp.mycompany.com is the captive portal server.
B) ClearPass.23 is the authentication server, and MC2 is the captive portal server.
C) Internal database in MC2 is the authentication server, and cp.mycompany.com is the captive portal server.
D) cp.mycompany.com is the authentication server, and ClearPass.23 is the captive portal server.
 Exhibit 2
Exhibit 2  Exhibit 3
Exhibit 3  Exhibit 4
Exhibit 4  A captive portal-based solution is deployed in a Mobility Master (MM) - Mobility Controller (MC) network. A wireless station connects to the network and attempts the authentication process. The outputs are shown in the exhibits. Which names correlate with the authentication and captive portal servers?
A captive portal-based solution is deployed in a Mobility Master (MM) - Mobility Controller (MC) network. A wireless station connects to the network and attempts the authentication process. The outputs are shown in the exhibits. Which names correlate with the authentication and captive portal servers?A) ClearPass.23 is the authentication server, and cp.mycompany.com is the captive portal server.
B) ClearPass.23 is the authentication server, and MC2 is the captive portal server.
C) Internal database in MC2 is the authentication server, and cp.mycompany.com is the captive portal server.
D) cp.mycompany.com is the authentication server, and ClearPass.23 is the captive portal server.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
18
Refer to the exhibits. 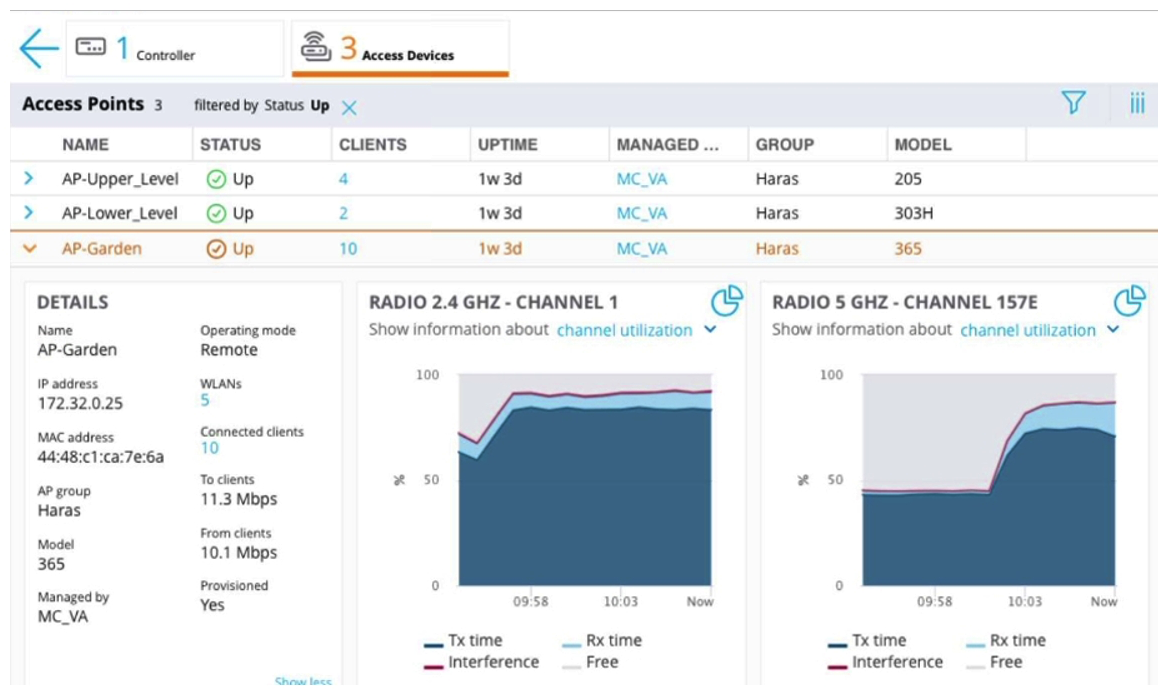
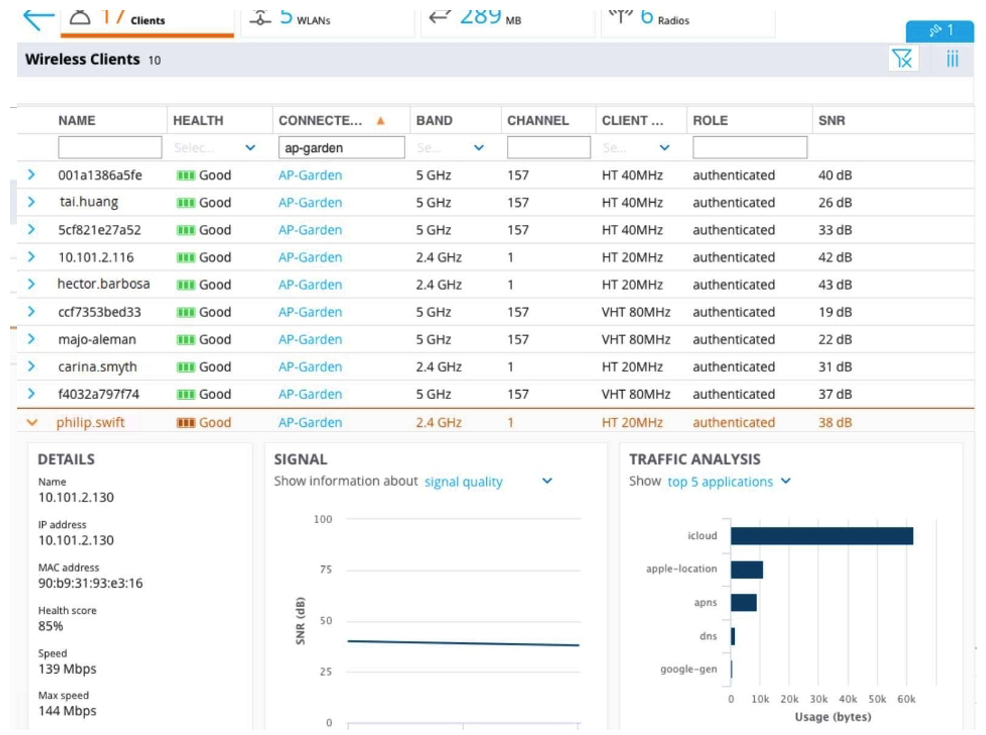 A user reports slow connectivity to a network administrator when connecting to AP-Garden and suggests that there might be a problem with the WLAN. The user's device supports 802.11n in the 2.4 GHz band. The network administrator finds the user in the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A user reports slow connectivity to a network administrator when connecting to AP-Garden and suggests that there might be a problem with the WLAN. The user's device supports 802.11n in the 2.4 GHz band. The network administrator finds the user in the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A) 2.4Ghz band is currently congested, therefore a NIC upgrade to 802.11ac or higher is recommended so the user can move to 5Ghz.
B) Channel usage is high and though this device has high speed the overall client rate is low on AP-Garden, there could be a few clients monopolizing the airtime on both bands at low speeds.
C) User's SNR value over time is lower than recommended, therefore he should either get closer to the Access Point or increase the transmit power.
D) 365s are low cost outdoor APs recommended for coverage design only. AP-Garden currently has more clients than recommended and is getting congested.

 A user reports slow connectivity to a network administrator when connecting to AP-Garden and suggests that there might be a problem with the WLAN. The user's device supports 802.11n in the 2.4 GHz band. The network administrator finds the user in the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?
A user reports slow connectivity to a network administrator when connecting to AP-Garden and suggests that there might be a problem with the WLAN. The user's device supports 802.11n in the 2.4 GHz band. The network administrator finds the user in the Mobility Master (MM) and reviews the output shown in the exhibit. What can the network administrator conclude after analyzing the data?A) 2.4Ghz band is currently congested, therefore a NIC upgrade to 802.11ac or higher is recommended so the user can move to 5Ghz.
B) Channel usage is high and though this device has high speed the overall client rate is low on AP-Garden, there could be a few clients monopolizing the airtime on both bands at low speeds.
C) User's SNR value over time is lower than recommended, therefore he should either get closer to the Access Point or increase the transmit power.
D) 365s are low cost outdoor APs recommended for coverage design only. AP-Garden currently has more clients than recommended and is getting congested.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
19
Refer to the exhibit. 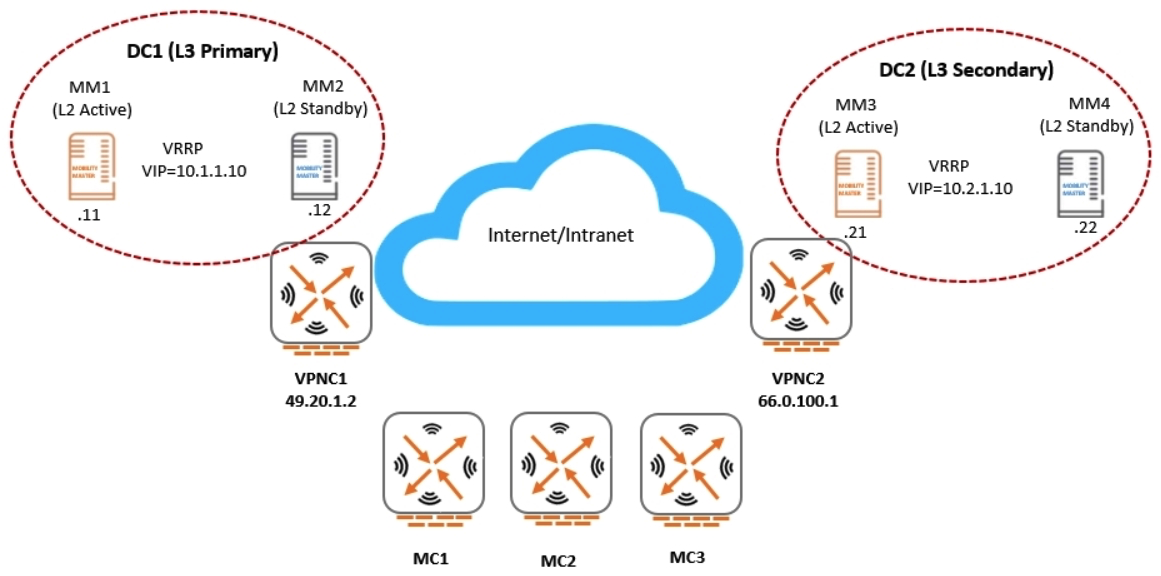
 An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active and, L3 Primary. Which MM IP will MCs communicate with if MM1 fails?
An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active and, L3 Primary. Which MM IP will MCs communicate with if MM1 fails?
A) 10.1.1.10
B) 10.1.1.12
C) 10.2.1.10
D) 10.2.1.21

 An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active and, L3 Primary. Which MM IP will MCs communicate with if MM1 fails?
An Aruba network is deployed with L2 and L3 Mobility Master (MM) redundancy across two datacenters, as shown in the exhibit. The network administrator confirms that all Mobility Controllers (MC) are currently communicating with MM1, which is the L2 Active and, L3 Primary. Which MM IP will MCs communicate with if MM1 fails?A) 10.1.1.10
B) 10.1.1.12
C) 10.2.1.10
D) 10.2.1.21

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
20
A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: "(MC_VA) [mynode] *#" When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)
A)![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_2c11_b2dd_211400029235_C1454_00.jpg)
B)![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5322_b2dd_c9106e67787f_C1454_00.jpg)
C)![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5323_b2dd_49256ccb35b2_C1454_00.jpg)
D)![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5324_b2dd_3f152f2cb3c6_C1454_00.jpg)
E)![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5325_b2dd_4984ac920475_C1454_00.jpg)
A)
![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_2c11_b2dd_211400029235_C1454_00.jpg)
B)
![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5322_b2dd_c9106e67787f_C1454_00.jpg)
C)
![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5323_b2dd_49256ccb35b2_C1454_00.jpg)
D)
![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5324_b2dd_3f152f2cb3c6_C1454_00.jpg)
E)
![<strong>A network administrator has updated the ArubaOS code of a standalone Mobility Controller (MC) that is used for User-Based Tunneling (UBT) to a newer early release. Ever since the MC seems to reject PAPI sessions from the switch with the 10.1.10.10 IP address. Also the controller's prompt is now followed by a star mark: (MC_VA) [mynode] *# When opening a support ticket, an Aruba TAC engineer asks the administrator to gather the crash logs and if possible replicate UBT connection attempts from the switch while running packet captures of PAPI traffic on the controller and obtain the PCAP files. The administrator has a PC with Wireshark and TFTP server using the 10.0.20.20 IP address. What commands must the administrator issue to accomplish these requests? (Choose two.)</strong> A) B) C) D) E)](https://d2lvgg3v3hfg70.cloudfront.net/C1454/11ec574e_f8b3_5325_b2dd_4984ac920475_C1454_00.jpg)

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
21
A company with 535 users deploys an Aruba solution with more than 1000 Aruba APs, two 7220 Mobility Controllers, and a single Mobility Master (MM) virtual appliance at the campus server farm. The MCs run a HA Fast failover group in dual mode and operate at 50% AP capacity. If there is an MM or MC failure, the network administrator must ensure that the network is fully manageable and the MC load does not exceed 80%. What can the network administrator do to meet these requirements?
A) Place the APs in the same hierarchy level.
B) Create a cluster with AP load balancing.
C) Enable oversubscription in the HA group.
D) Add an MC and an MM in the server farm.
E) Add an MM and enable DC redundancy.
F) Place the APs in two different AP-Groups.
A) Place the APs in the same hierarchy level.
B) Create a cluster with AP load balancing.
C) Enable oversubscription in the HA group.
D) Add an MC and an MM in the server farm.
E) Add an MM and enable DC redundancy.
F) Place the APs in two different AP-Groups.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
22
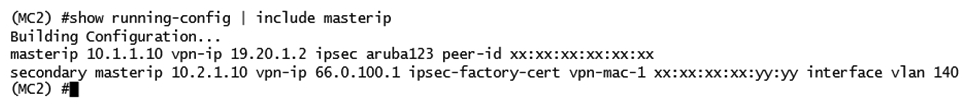
Refer to the exhibit. 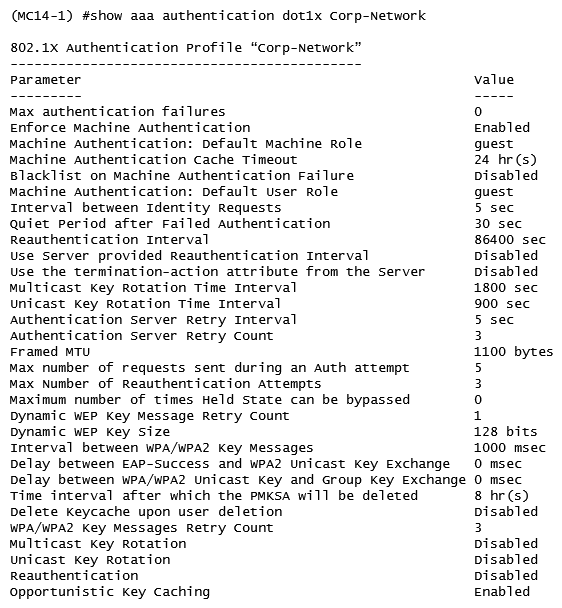 The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?
The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?
A) Set the reauth-period to 28800 enable reauthentication in the dot1x profile.
B) Set the reauth-period to 28800 enable reauthentication in the AAA profile.
C) Set the reauth-period to 28800 enable reauthentication in both dot1x and AAA profile.
D) Set the reauth-period to 28800 in the dot1x profile and enable reauthentication in the AAA profile.
 The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?
The network administrator must ensure that the configuration will force users to authenticate periodically every eight hours. Which configuration is required to effect this change?A) Set the reauth-period to 28800 enable reauthentication in the dot1x profile.
B) Set the reauth-period to 28800 enable reauthentication in the AAA profile.
C) Set the reauth-period to 28800 enable reauthentication in both dot1x and AAA profile.
D) Set the reauth-period to 28800 in the dot1x profile and enable reauthentication in the AAA profile.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
23
Refer to the exhibit. 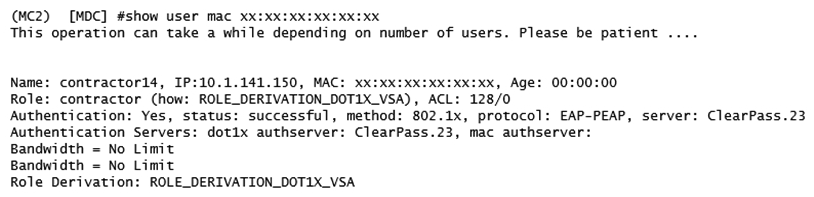 A network administrator is evaluating a deployment to validate that a user is assigned the proper role and reviews the output in the exhibit. How is the role assigned to user?
A network administrator is evaluating a deployment to validate that a user is assigned the proper role and reviews the output in the exhibit. How is the role assigned to user?
A) The MC assigned the role based on Aruba VSAs.
B) The MC assigned the machine authentication default user role.
C) The MC assigned the default role based on the authentication method.
D) The MC assigned the role based on server derivation rules.
 A network administrator is evaluating a deployment to validate that a user is assigned the proper role and reviews the output in the exhibit. How is the role assigned to user?
A network administrator is evaluating a deployment to validate that a user is assigned the proper role and reviews the output in the exhibit. How is the role assigned to user?A) The MC assigned the role based on Aruba VSAs.
B) The MC assigned the machine authentication default user role.
C) The MC assigned the default role based on the authentication method.
D) The MC assigned the role based on server derivation rules.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
24
Refer to the exhibits. 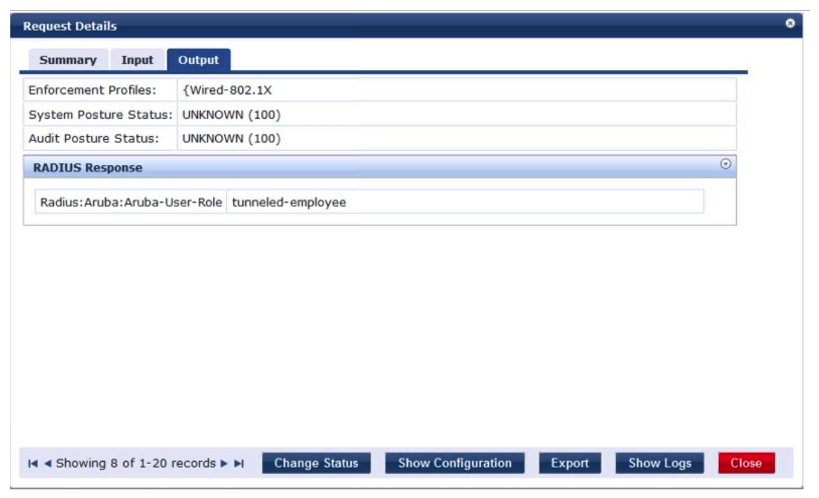
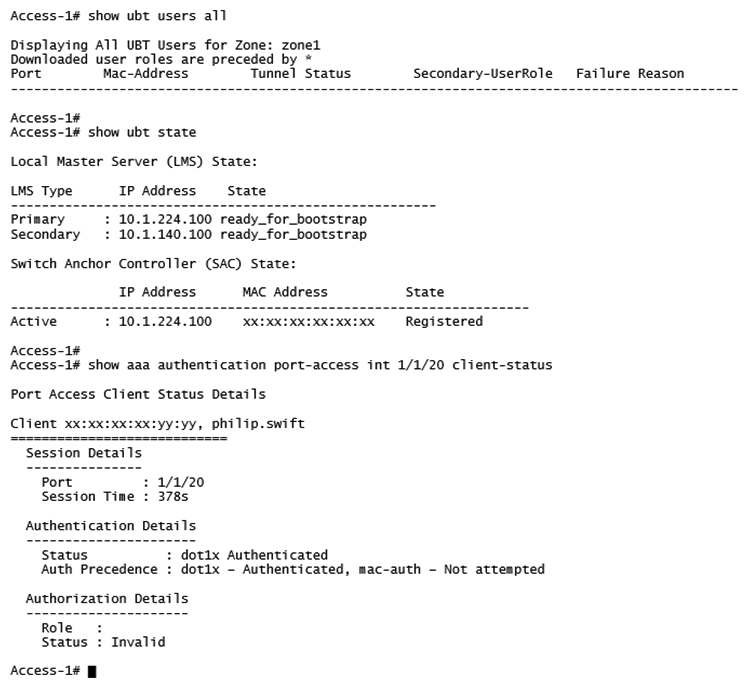 A network administrator deploys User Based Tunneling (UBT) in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the Aruba-User-Role attribute as expected. However, the AOS-CX based switch does not seem to build the tunnel to the Mobility Controller (MC) for this user. Why does the switch fail to run UBT for the user?
A network administrator deploys User Based Tunneling (UBT) in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the Aruba-User-Role attribute as expected. However, the AOS-CX based switch does not seem to build the tunnel to the Mobility Controller (MC) for this user. Why does the switch fail to run UBT for the user?
A) The switch has not fully associated to the MC.
B) ClearPass is sending the wrong Vendor ID.
C) The switch is not configured with the gateway-role.
D) ClearPass is sending the wrong VSA type.
E) The switch is not configured with the port-access role.

 A network administrator deploys User Based Tunneling (UBT) in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the Aruba-User-Role attribute as expected. However, the AOS-CX based switch does not seem to build the tunnel to the Mobility Controller (MC) for this user. Why does the switch fail to run UBT for the user?
A network administrator deploys User Based Tunneling (UBT) in a corporate network to unify the security policies enforcement. When users authenticate with 802.1X, ClearPass shows Accept results, and sends the Aruba-User-Role attribute as expected. However, the AOS-CX based switch does not seem to build the tunnel to the Mobility Controller (MC) for this user. Why does the switch fail to run UBT for the user?A) The switch has not fully associated to the MC.
B) ClearPass is sending the wrong Vendor ID.
C) The switch is not configured with the gateway-role.
D) ClearPass is sending the wrong VSA type.
E) The switch is not configured with the port-access role.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
25
A network administrator wants to permit explicit SSH, FTP and HHTP(s) access to servers in the 10.100.20.5 to 10.100.20.31 range, all devices in 10.100.21.0/24 network, and a host with IP address 10.100.22.70. The services must work properly at all times. Which configuration scripts accomplish this task with the fewer number of lines, while avoiding access to other devices not included in these ranges? (Choose two.)
A)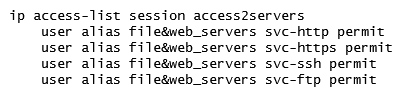
B)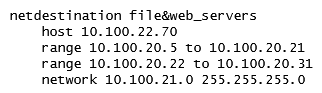
C)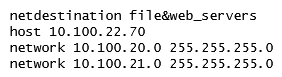
D)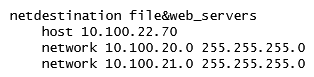
E)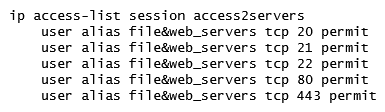
A)

B)

C)

D)

E)


Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
26
Users run Skype for Business on wireless clients with no WMM support over an Aruba Mobility Master (MM) - Mobility Controller (MC) based network. When traffic arrives at the wired network, it does not include either L2 or L3 markings. Which configuration steps should the network administrator take to classify and mark voice and video traffic with UCC heuristics mode?
A) Enable WMM in a VAP profile, and explicitly permit voice and video UDP ports in a firewall policy.
B) Confirm OpenFlow is enabled in the user role and VAP profile. Then enable WMM in a SSID profile, and explicitly permit voice and video UDP ports in a firewall policy.
C) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and firewall roles. Enable Skype4Business ALG in UCC profiles.
D) Confirm MM is the Openflow controller of MCs and Openflow is enabled in VAP and firewall roles. Enable Skype4Business ALG in UCC profiles.
A) Enable WMM in a VAP profile, and explicitly permit voice and video UDP ports in a firewall policy.
B) Confirm OpenFlow is enabled in the user role and VAP profile. Then enable WMM in a SSID profile, and explicitly permit voice and video UDP ports in a firewall policy.
C) Confirm the MC is the Openflow controller of the MMs and Openflow is enabled in VAP and firewall roles. Enable Skype4Business ALG in UCC profiles.
D) Confirm MM is the Openflow controller of MCs and Openflow is enabled in VAP and firewall roles. Enable Skype4Business ALG in UCC profiles.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
27
Refer to the exhibit.  Based on the output shown in the exhibit, with which Aruba devices has Access-1 established tunnels?
Based on the output shown in the exhibit, with which Aruba devices has Access-1 established tunnels?
A) a pair of standalone MCs
B) a pair of switches running VXLAN
C) a pair of MCs within a L3 cluster
D) a single standalone MC
 Based on the output shown in the exhibit, with which Aruba devices has Access-1 established tunnels?
Based on the output shown in the exhibit, with which Aruba devices has Access-1 established tunnels?A) a pair of standalone MCs
B) a pair of switches running VXLAN
C) a pair of MCs within a L3 cluster
D) a single standalone MC

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
28
Refer to the exhibit. 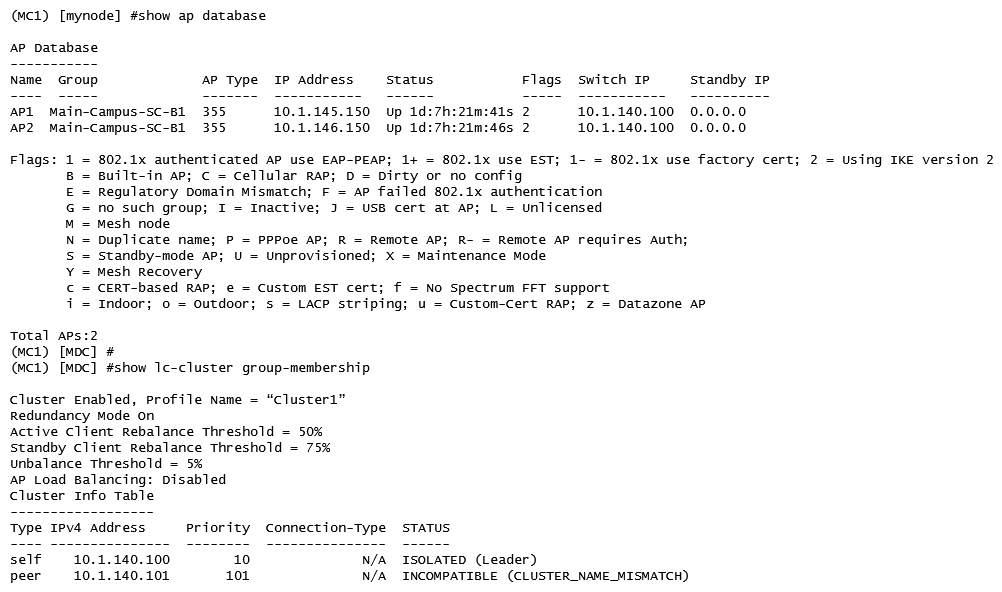 After deploying several cluster pairs, the network administrator notices that all APs assigned to Cluster1 communicate with MC1 instead of being distributed between members of the cluster. Also, no IP addresses are shown under the Standby IP column. What should the network administrator do to fix this situation?
After deploying several cluster pairs, the network administrator notices that all APs assigned to Cluster1 communicate with MC1 instead of being distributed between members of the cluster. Also, no IP addresses are shown under the Standby IP column. What should the network administrator do to fix this situation?
A) Apply the same cluster profile to both members.
B) Enable Cluster AP load balancing.
C) Rename the cluster profile as "CLUSTER1".
D) Place MCs at the same hierarchical group level.
 After deploying several cluster pairs, the network administrator notices that all APs assigned to Cluster1 communicate with MC1 instead of being distributed between members of the cluster. Also, no IP addresses are shown under the Standby IP column. What should the network administrator do to fix this situation?
After deploying several cluster pairs, the network administrator notices that all APs assigned to Cluster1 communicate with MC1 instead of being distributed between members of the cluster. Also, no IP addresses are shown under the Standby IP column. What should the network administrator do to fix this situation?A) Apply the same cluster profile to both members.
B) Enable Cluster AP load balancing.
C) Rename the cluster profile as "CLUSTER1".
D) Place MCs at the same hierarchical group level.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
29
Refer to the exhibit. 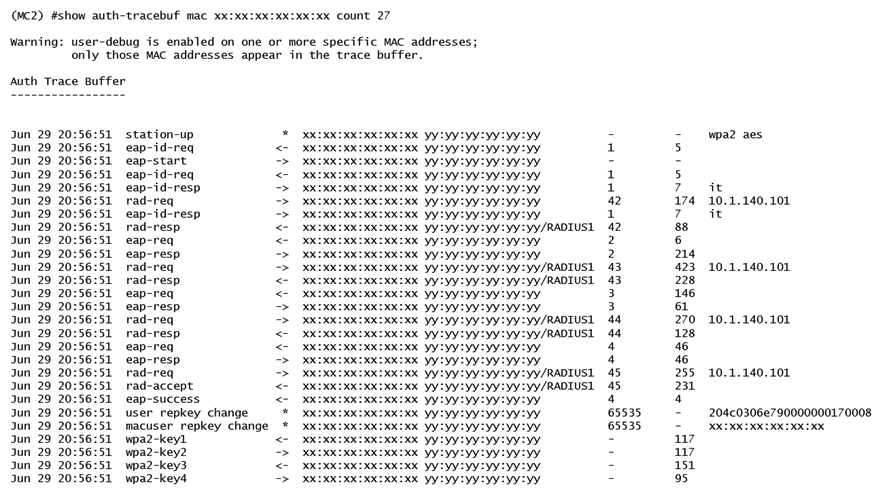 A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by a wireless station?
A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by a wireless station?
A) EAP authentication
B) 802.1X machine authentication
C) MAC authentication
D) 802.1X user authentication
 A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by a wireless station?
A network administrator is validating client connectivity and executes the show command shown in the exhibit. Which authentication method was used by a wireless station?A) EAP authentication
B) 802.1X machine authentication
C) MAC authentication
D) 802.1X user authentication

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
30
Refer to the exhibit. 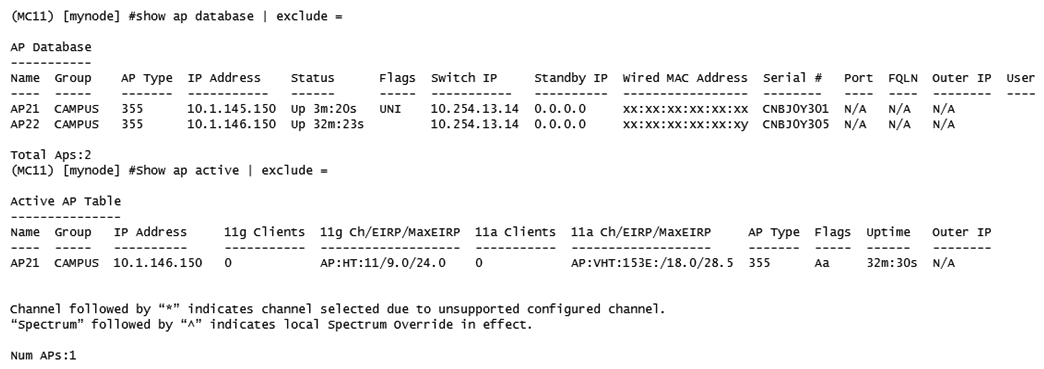 A network administrator deploys a new Mobility Master (MM) - Mobility Controller (MC) network. To test the solution, the network administrator accesses the console of a pair of APs and statically provisions them. However, one of the APs does not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?
A network administrator deploys a new Mobility Master (MM) - Mobility Controller (MC) network. To test the solution, the network administrator accesses the console of a pair of APs and statically provisions them. However, one of the APs does not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?
A) Create another AP group in the MC's configuration, and re-provision one AP with a different group.
B) Re-provision one of the APs with a different name, and add new entries with the proper group in the whitelist.
C) Re-provision the AP with a different group, and modify the name of one AP in the whitelist.
D) Re-provision one of the APs with a different name or modify the name in the whitelist.
 A network administrator deploys a new Mobility Master (MM) - Mobility Controller (MC) network. To test the solution, the network administrator accesses the console of a pair of APs and statically provisions them. However, one of the APs does not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?
A network administrator deploys a new Mobility Master (MM) - Mobility Controller (MC) network. To test the solution, the network administrator accesses the console of a pair of APs and statically provisions them. However, one of the APs does not propagate the configured SSIDs. The network administrator looks at the logs and sees the output shown in the exhibit. Which actions must the network administrator take to solve the problem?A) Create another AP group in the MC's configuration, and re-provision one AP with a different group.
B) Re-provision one of the APs with a different name, and add new entries with the proper group in the whitelist.
C) Re-provision the AP with a different group, and modify the name of one AP in the whitelist.
D) Re-provision one of the APs with a different name or modify the name in the whitelist.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
31
Refer to the exhibit 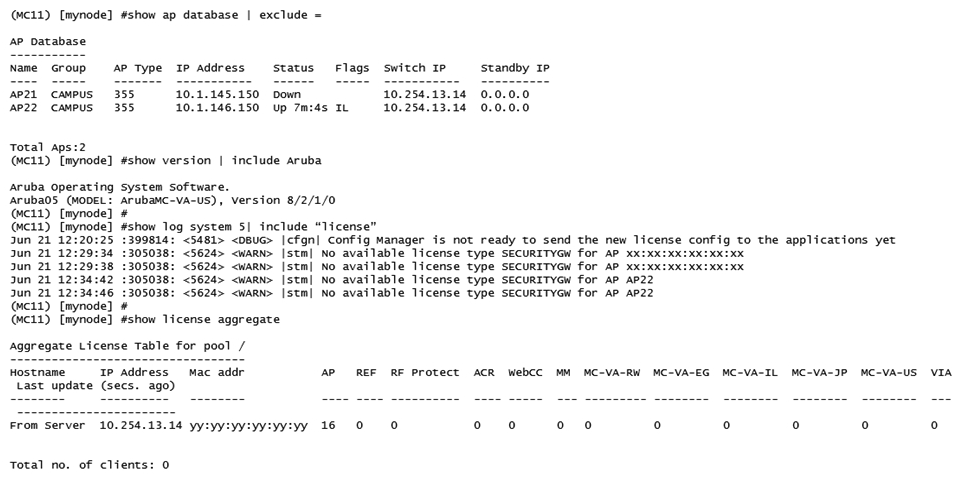 A network administrator deploys a standalone Mobility Controller (MC) and configures some VAPs within the CAMPUS AP group. The network administrator realizes that none of the VAPs are being broadcasted. Based on the output shown in the exhibit, what should the network administrator do to solve this problem?
A network administrator deploys a standalone Mobility Controller (MC) and configures some VAPs within the CAMPUS AP group. The network administrator realizes that none of the VAPs are being broadcasted. Based on the output shown in the exhibit, what should the network administrator do to solve this problem?
A) Install MC-VA licenses, then install PEF licenses and enabled the PEF feature.
B) Install MC-VA licenses, then reprovision the APs.
C) Install MM licenses, then install PEF licenses and enable the PEF feature.
D) Install MM licenses and install MC-VA licenses, then install RFP licenses.
 A network administrator deploys a standalone Mobility Controller (MC) and configures some VAPs within the CAMPUS AP group. The network administrator realizes that none of the VAPs are being broadcasted. Based on the output shown in the exhibit, what should the network administrator do to solve this problem?
A network administrator deploys a standalone Mobility Controller (MC) and configures some VAPs within the CAMPUS AP group. The network administrator realizes that none of the VAPs are being broadcasted. Based on the output shown in the exhibit, what should the network administrator do to solve this problem?A) Install MC-VA licenses, then install PEF licenses and enabled the PEF feature.
B) Install MC-VA licenses, then reprovision the APs.
C) Install MM licenses, then install PEF licenses and enable the PEF feature.
D) Install MM licenses and install MC-VA licenses, then install RFP licenses.

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck
32
A network administrator is in charge of a Mobility Master (MM) - Mobility Controller (MC) based network security. Recently the Air Monitors detected a Rogue AP in the network and the administrator wants to enable "Tarpit" based wireless containment. What profile must the administrator enable "tarpit" wireless containment on?
A) IDS Unauthorized device profile
B) IDS profile
C) IDS General profile
D) IDS DOS profile
A) IDS Unauthorized device profile
B) IDS profile
C) IDS General profile
D) IDS DOS profile

Unlock Deck
Unlock for access to all 32 flashcards in this deck.
Unlock Deck
k this deck



