Deck 16: Aruba Certified ClearPass Professional (ACCP) V6.7
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/40
Play
Full screen (f)
Deck 16: Aruba Certified ClearPass Professional (ACCP) V6.7
1
A company has an Aruba solution. The company wants to host a guest login portal with this solution, and the login portal must give guests the option to create their own login accounts. How can a network administrator help meet these criteria?
A) Choose the Internal captive portal with email registration option for the guest WLAN. Choose the Internal captive portal with email registration option for the guest WLAN.
B) Choose ClearPass or the other external captive portal option for the guest WLAN. Choose ClearPass or the other external captive portal
C) Make sure to create a guest provisioning account for the guest WLAN.
D) Disable authentication in the captive portal profile for the guest WLAN.
A) Choose the Internal captive portal with email registration option for the guest WLAN. Choose the Internal captive portal with email registration option for the guest WLAN.
B) Choose ClearPass or the other external captive portal option for the guest WLAN. Choose ClearPass or the other external captive portal
C) Make sure to create a guest provisioning account for the guest WLAN.
D) Disable authentication in the captive portal profile for the guest WLAN.
Choose ClearPass or the other external captive portal option for the guest WLAN. Choose ClearPass or the other external captive portal
2
How can network administrators upgrade AirMatch on an Aruba Mobility Master (MM)?
A) Upgrade Client Match as part of a global software upgrade, and upgrade AirMatch separately as a loadable service module (LSM).
B) Upgrade Client Match and AirMatch separately as loadable service modules (LSMs).
C) Upgrade AirMatch and Client Match through a global software upgrade.
D) Upgrade AirMatch as part of a global software upgrade, and upgrade Client Match separately as a loadable service module (LSM).
A) Upgrade Client Match as part of a global software upgrade, and upgrade AirMatch separately as a loadable service module (LSM).
B) Upgrade Client Match and AirMatch separately as loadable service modules (LSMs).
C) Upgrade AirMatch and Client Match through a global software upgrade.
D) Upgrade AirMatch as part of a global software upgrade, and upgrade Client Match separately as a loadable service module (LSM).
Upgrade Client Match and AirMatch separately as loadable service modules (LSMs).
3
What is a key difference between an Aruba Air Monitor (AM) and an Aruba Spectrum Analyzer (SA)?
A) An AM detects threats such as rogue APs, while an SA analyzes RF conditions.
B) An AM detects rogue APs and provides data services to clients, while an SA only detects rogue APs.
C) An AM scans on only one 802.11 frequency band, while an SA scans on both 802.11 frequency bands.
D) An AM both detects wireless intrusion attempts and mitigates them, while an SA only detects wireless intrusion attempts.
A) An AM detects threats such as rogue APs, while an SA analyzes RF conditions.
B) An AM detects rogue APs and provides data services to clients, while an SA only detects rogue APs.
C) An AM scans on only one 802.11 frequency band, while an SA scans on both 802.11 frequency bands.
D) An AM both detects wireless intrusion attempts and mitigates them, while an SA only detects wireless intrusion attempts.
An AM detects threats such as rogue APs, while an SA analyzes RF conditions.
4
Which IEEE standard provides the highest transmission rates in the 2.4GHz frequency band?
A) 802.11a
B) 802.11ac
C) 802.11g
D) 802.11n
A) 802.11a
B) 802.11ac
C) 802.11g
D) 802.11n

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
5
Assume that administrators accept the default forwarding mode for WLANs. How does wireless user traffic flow in a master-local architecture, and how does it flow in a Mobility Master (MM) architecture?
A) In the master-local architecture, traffic is tunneled to a local Mobility Controller (MC) to handle. In a MM architecture, all traffic is tunneled to the MM to handle.
B) In the master-local architecture, all traffic is tunneled to the master controller to handle. In a MM architecture, all traffic is tunneled to the MM to handle.
C) In both architectures, traffic is tunneled to a Mobility Controller (MC) to handle.
D) In both architectures, APs forward corporate user traffic locally and tunnel guest user traffic to a Mobility Controller (MC) to handle.
A) In the master-local architecture, traffic is tunneled to a local Mobility Controller (MC) to handle. In a MM architecture, all traffic is tunneled to the MM to handle.
B) In the master-local architecture, all traffic is tunneled to the master controller to handle. In a MM architecture, all traffic is tunneled to the MM to handle.
C) In both architectures, traffic is tunneled to a Mobility Controller (MC) to handle.
D) In both architectures, APs forward corporate user traffic locally and tunnel guest user traffic to a Mobility Controller (MC) to handle.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
6
Exhibit 1 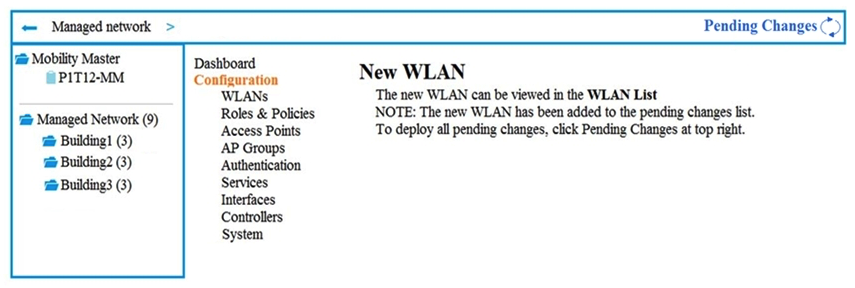 Exhibit 2
Exhibit 2 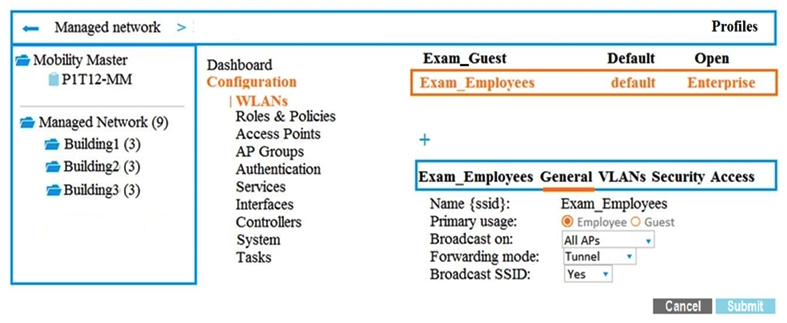 A company has an Aruba Mobility Master (MM)-based solution and needs a new WLAN for the corporate campus. A network administrator completes the creation of this WLAN, as shown in Exhibit 1. When administrators try to test a connection to the WLAN, the WLAN does not show up in the list of WLANs on the client. The administrator can see the WLAN in the list, as shown in Exhibit 2. What is the error?
A company has an Aruba Mobility Master (MM)-based solution and needs a new WLAN for the corporate campus. A network administrator completes the creation of this WLAN, as shown in Exhibit 1. When administrators try to test a connection to the WLAN, the WLAN does not show up in the list of WLANs on the client. The administrator can see the WLAN in the list, as shown in Exhibit 2. What is the error?
A) The configuration is not deployed.
B) The WLAN is configured at a lower level in the Managed Network hierarchy.
C) The Mobility Master (MM) does not have an active PEFNG license.
D) The WLAN is configured as a hidden SSID.
 Exhibit 2
Exhibit 2  A company has an Aruba Mobility Master (MM)-based solution and needs a new WLAN for the corporate campus. A network administrator completes the creation of this WLAN, as shown in Exhibit 1. When administrators try to test a connection to the WLAN, the WLAN does not show up in the list of WLANs on the client. The administrator can see the WLAN in the list, as shown in Exhibit 2. What is the error?
A company has an Aruba Mobility Master (MM)-based solution and needs a new WLAN for the corporate campus. A network administrator completes the creation of this WLAN, as shown in Exhibit 1. When administrators try to test a connection to the WLAN, the WLAN does not show up in the list of WLANs on the client. The administrator can see the WLAN in the list, as shown in Exhibit 2. What is the error?A) The configuration is not deployed.
B) The WLAN is configured at a lower level in the Managed Network hierarchy.
C) The Mobility Master (MM) does not have an active PEFNG license.
D) The WLAN is configured as a hidden SSID.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
7
A WLAN in an Aruba Mobility Master (MM)-based solution uses WPA2-Enterprise security. This WLAN currently authenticates users to Active Directory (AD), and users log in with their Windows domain credentials. Network administrators now want to authenticate the Windows clients as well, based on the client Computer Names. What should the administrator do on MM to achieve this goal?
A) Set up MAC Authentication on the WLAN.
B) Set up Machine Authentication on the WLAN.
C) Import the computer names from AD to the MM internal database.
D) Bind individual Mobility Controllers (MCs) to AD at the device level.
A) Set up MAC Authentication on the WLAN.
B) Set up Machine Authentication on the WLAN.
C) Import the computer names from AD to the MM internal database.
D) Bind individual Mobility Controllers (MCs) to AD at the device level.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
8
An Aruba Remote AP (RAP) operates in split-tunnel mode. How does the AP forward traffic?
A) It sends all user traffic in a GRE tunnel to a central Mobility Controller (MC), and it sends control traffic in an IPsec tunnel to the controller.
B) It sends user and control traffic in two separate IPsec tunnels to the Mobility Controller (MC).
C) It sends all employee and control traffic in a GRE tunnel to a central Mobility Controller (MC), and it bridges all guest traffic locally.
D) It sends traffic designed to the corporate network in an IPsec tunnel to a central Mobility Controller (MC), and it bridges other traffic locally.
A) It sends all user traffic in a GRE tunnel to a central Mobility Controller (MC), and it sends control traffic in an IPsec tunnel to the controller.
B) It sends user and control traffic in two separate IPsec tunnels to the Mobility Controller (MC).
C) It sends all employee and control traffic in a GRE tunnel to a central Mobility Controller (MC), and it bridges all guest traffic locally.
D) It sends traffic designed to the corporate network in an IPsec tunnel to a central Mobility Controller (MC), and it bridges other traffic locally.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
9
A network administrator configures this policy:  Users to which this policy apply are unable to receive IP addresses with DHCP. How should the administrator fix the issue?
Users to which this policy apply are unable to receive IP addresses with DHCP. How should the administrator fix the issue?
A) Move the user any svc-dhcp permit rule to the bottom of the list. Move the user any svc-dhcp permit rule to the bottom of the list.
B) Remove the deny rule from the policy. Remove the deny rule from the policy.
C) Use the correct service alias in the user any svc-dhcp permit rule. Use the correct service alias in the rule.
D) Change user to any in the user any svc-dhcp permit rule. Change user to any in the
 Users to which this policy apply are unable to receive IP addresses with DHCP. How should the administrator fix the issue?
Users to which this policy apply are unable to receive IP addresses with DHCP. How should the administrator fix the issue?A) Move the user any svc-dhcp permit rule to the bottom of the list. Move the user any svc-dhcp permit rule to the bottom of the list.
B) Remove the deny rule from the policy. Remove the deny rule from the policy.
C) Use the correct service alias in the user any svc-dhcp permit rule. Use the correct service alias in the rule.
D) Change user to any in the user any svc-dhcp permit rule. Change user to any in the

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
10
A company has an Aruba Mobility Master (MM)-based solution. Where can a network administrator look to find a list of alerts about a variety of issues on the MM or managed devices?
A) the top banner
B) the MM Maintenance pages
C) the Performance dashboard
D) the Potential issues dashboard
A) the top banner
B) the MM Maintenance pages
C) the Performance dashboard
D) the Potential issues dashboard

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
11
A network administrator wants to assign an authentication server group to the WPA2-Enterprise WLAN. Which profile should the administrator modify?
A) Virtual AP
B) SSID
C) AAA
D) L2 Authentication
A) Virtual AP
B) SSID
C) AAA
D) L2 Authentication

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
12
What is one reason for a network administrator to visit the Dashboard > Usage window on an Aruba Mobility Master (MM)?
A) to check license usage and determine the need for additional licenses
B) to generate reports about traffic patterns and network usage over the past several months
C) to view system usage statistics for the MM and troubleshoot potential issues
D) to analyze short term trends in network usage by client, AP, and application
A) to check license usage and determine the need for additional licenses
B) to generate reports about traffic patterns and network usage over the past several months
C) to view system usage statistics for the MM and troubleshoot potential issues
D) to analyze short term trends in network usage by client, AP, and application

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
13
A company has a Mobility Master (MM)-based solution. A network administrator wants to monitor the types of applications in use in the wireless network. Which dashboard page in the MM interface should the administrator visit?
A) Performance
B) Network
C) Traffic Analysis
D) Security
A) Performance
B) Network
C) Traffic Analysis
D) Security

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
14
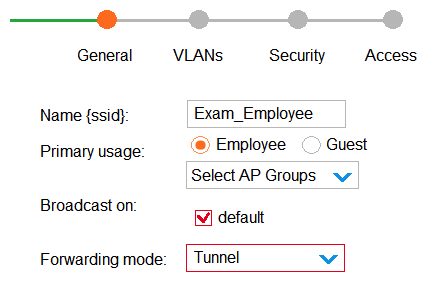 What describes the behavior for this WLAN?
What describes the behavior for this WLAN?A) No APs broadcast the SSID. Clients cannot connect to the WLAN until administrators activate it.
B) APs in the default group broadcast the SSID. Clients can connect to the WLAN on APs in any group.
C) No APs broadcast the SSID. Clients can connect to the WLAN on APs in the default group only.
D) APs in the default group broadcast the SSID. Clients can connect to the WLAN on APs in the default group only.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
15
A company wants to provide wireless access for guests with their Aruba solution. Which configuration feature requires the customer to purchase PEFNG licenses?
A) redirection of guests to an external captive portal
B) customization of the internal captive portal login page
C) addition of custom rules to control access for authenticated guests
D) provision of DHCP services to unauthenticated guests
A) redirection of guests to an external captive portal
B) customization of the internal captive portal login page
C) addition of custom rules to control access for authenticated guests
D) provision of DHCP services to unauthenticated guests

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
16
A company has an Aruba solution that supports an employee WLAN. How can network administrators control in which subnets user receive IP addresses?
A) Assign switch ports connected to APs to VLANs associated with the desired subnets.
B) Set the VLANs associated with desired subnets in the WLAN settings.
C) Configure firewall policies that permit the desired subnet, and add them to the initial role for the WLAN.
D) In the WLAN settings, configure User role rules with the desired subnet addresses as match criteria.
A) Assign switch ports connected to APs to VLANs associated with the desired subnets.
B) Set the VLANs associated with desired subnets in the WLAN settings.
C) Configure firewall policies that permit the desired subnet, and add them to the initial role for the WLAN.
D) In the WLAN settings, configure User role rules with the desired subnet addresses as match criteria.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
17
An AP operates on channel 6. Which device causes the most significant and consistent interference with the signal?
A) cellular phone
B) AP operating on channel 11
C) wireless security camera operating on channel 8
D) weather radar
A) cellular phone
B) AP operating on channel 11
C) wireless security camera operating on channel 8
D) weather radar

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
18
A company has an Aruba Mobility Master (MM)-based solution that runs ArubaOS 8 and uses the default AirMatch and Client Match settings. The ARM profile has been disabled for 5GHz radios. How are channel and transmit power settings managed for these radios?
A) with AirMatch
B) with Rule Based Client Match
C) with legacy ARM
D) with legacy Client Match
A) with AirMatch
B) with Rule Based Client Match
C) with legacy ARM
D) with legacy Client Match

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
19
What does an Aruba Mobility Master (MM) do before it deploys a configuration to a Mobility Controller (MC)?
A) It synchronizes the configuration with templates on Aruba AirWave.
B) It removes any commands that are not supported on that MC or have dependency errors.
C) It obtains the current configuration, encrypts it, and backs it up to a secure archive.
D) It encrypts the configuration to be deployed and backs it up to a secure archive.
A) It synchronizes the configuration with templates on Aruba AirWave.
B) It removes any commands that are not supported on that MC or have dependency errors.
C) It obtains the current configuration, encrypts it, and backs it up to a secure archive.
D) It encrypts the configuration to be deployed and backs it up to a secure archive.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
20
What is one difference between captive portal authentication and 802.1X authentication?
A) 802.1X authentication always authenticates the wireless client, while captive portal authentication always authenticates the wireless user.
B) 802.1X authentication is typically implemented without encryption, while captive authentication is often combined with WPA or WPA2.
C) 802.1X authentication occurs at Layer 2, while captive portal authentication occurs at Layer 3.
D) 802.1X authentication must use an LDAP server, while captive portal authentication can use a RADIUS server or an LDAP server.
A) 802.1X authentication always authenticates the wireless client, while captive portal authentication always authenticates the wireless user.
B) 802.1X authentication is typically implemented without encryption, while captive authentication is often combined with WPA or WPA2.
C) 802.1X authentication occurs at Layer 2, while captive portal authentication occurs at Layer 3.
D) 802.1X authentication must use an LDAP server, while captive portal authentication can use a RADIUS server or an LDAP server.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
21
Which components of a ClearPass is mandatory?
A) Authorization Source
B) Enforcement
C) Profiler
D) Role Mapping Policy
E) Posture
A) Authorization Source
B) Enforcement
C) Profiler
D) Role Mapping Policy
E) Posture

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
22
A company plans to deploy a Mobility Master (MM) solution with two MM nodes. The MM solution will manage 10 Mobility Controller (MC) appliance that will control a total of 400 APs. How should the network administrator install the AP licenses?
A) 40 AP licenses on the MM and no licenses on the MC
B) 400 AP licenses on the MM and no licenses on the MC
C) 800 AP licenses on each MC and no licenses on the MM
D) 800 AP licenses on the MM and 40 AP licenses on each MC
A) 40 AP licenses on the MM and no licenses on the MC
B) 400 AP licenses on the MM and no licenses on the MC
C) 800 AP licenses on each MC and no licenses on the MM
D) 800 AP licenses on the MM and 40 AP licenses on each MC

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
23
A company has a Mobility Master (MM)-based solution. There is a hardware issue with the MM appliance, and, as result, all connectivity is lost between the appliance and the network. The network manager is concerned about how this will impact licensing. How will the Mobility Controller (MC) be affected?
A) The MC maintains its current licenses for 30 days.
B) The MC loses all licenses and cannot support APs or clients.
C) The MC contacts Aruba Activate and uses the licensing limits defined there.
D) The MC maintains only licenses that have been locally installed on it.
A) The MC maintains its current licenses for 30 days.
B) The MC loses all licenses and cannot support APs or clients.
C) The MC contacts Aruba Activate and uses the licensing limits defined there.
D) The MC maintains only licenses that have been locally installed on it.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
24
Refer to the exhibit. 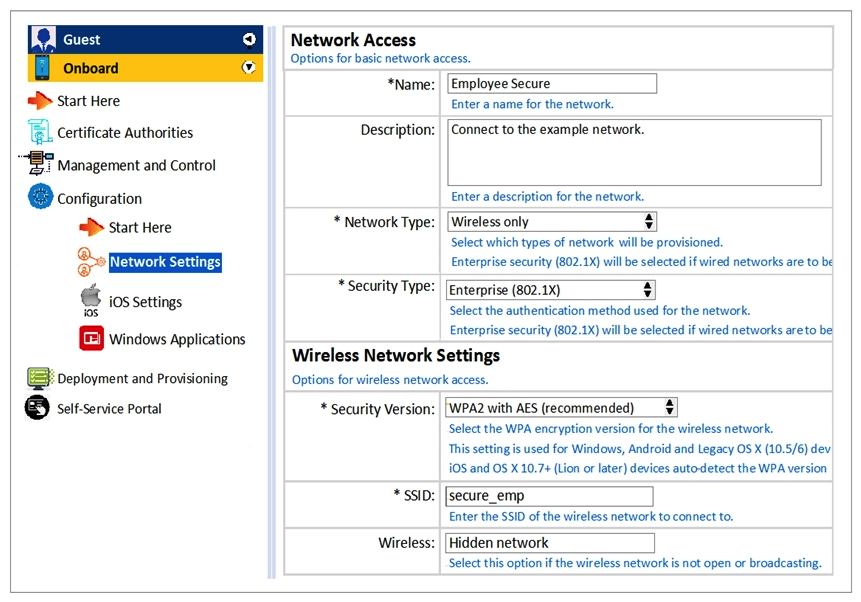 Which statements accurately describe the status of the Onboarded devices in the configuration for the network settings shown? (Choose two.)
Which statements accurately describe the status of the Onboarded devices in the configuration for the network settings shown? (Choose two.)
A) They will use WPA2-PSK with AES when connecting to the SSID.
B) They will to Employee_Secure SSID for provisioning their devices.
C) They will to Employee_Secure SSID after provisioning.
D) They will perform 802.1 authentication when connecting to the SSID.
E) They will connect to secure_emp SSID after provisioning.
 Which statements accurately describe the status of the Onboarded devices in the configuration for the network settings shown? (Choose two.)
Which statements accurately describe the status of the Onboarded devices in the configuration for the network settings shown? (Choose two.)A) They will use WPA2-PSK with AES when connecting to the SSID.
B) They will to Employee_Secure SSID for provisioning their devices.
C) They will to Employee_Secure SSID after provisioning.
D) They will perform 802.1 authentication when connecting to the SSID.
E) They will connect to secure_emp SSID after provisioning.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
25
Refer to the exhibit. 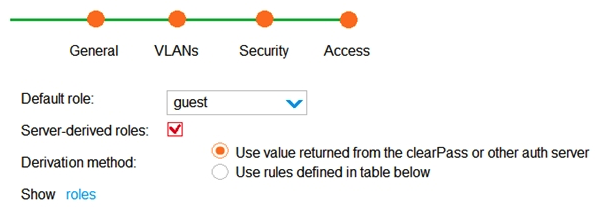 A network administrator sets up the Exam_Employees WLAN on an Aruba solution with a default role of guest, as shown in the exhibit. To which users does the guest role apply?
A network administrator sets up the Exam_Employees WLAN on an Aruba solution with a default role of guest, as shown in the exhibit. To which users does the guest role apply?
A) users who have connected to the SSID, but have not yet attempted authentication
B) users who successfully authenticate and are assigned to the default role by the RADIUS server
C) users who successfully authenticate and are not assigned a different role by the RADIUS server
D) users who fall authentication
 A network administrator sets up the Exam_Employees WLAN on an Aruba solution with a default role of guest, as shown in the exhibit. To which users does the guest role apply?
A network administrator sets up the Exam_Employees WLAN on an Aruba solution with a default role of guest, as shown in the exhibit. To which users does the guest role apply?A) users who have connected to the SSID, but have not yet attempted authentication
B) users who successfully authenticate and are assigned to the default role by the RADIUS server
C) users who successfully authenticate and are not assigned a different role by the RADIUS server
D) users who fall authentication

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
26
An organization has decided to implement dual SSID Onboarding. An administrator has used the Onboard service template to create services for dual SSID Onboarding. Which statement is true?
A) The Onboard Authorization service is triggered when the user connects to the secure SSID.
B) The Onboard Authorization service is triggered during the Onboarding process.
C) The Onboard Authorization service is never triggered.
D) The device connects to the secure SSID for provisioning.
E) The Onboard Provisioning service is triggered when the user connects to the provisioning SSID to Onboard their device.
A) The Onboard Authorization service is triggered when the user connects to the secure SSID.
B) The Onboard Authorization service is triggered during the Onboarding process.
C) The Onboard Authorization service is never triggered.
D) The device connects to the secure SSID for provisioning.
E) The Onboard Provisioning service is triggered when the user connects to the provisioning SSID to Onboard their device.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
27
Why can't the Onguard posture check be done during 802.1x authentication?
A) Onguard uses TACACS so an additional service must be created.
B) 802.1x is already secure so Onguard is not needed.
C) Health Checks can't be used with 802.1x.
D) Onguard uses RADIUS so an additional service must be created.
E) Onguard uses HTTPS so an additional service must be created.
A) Onguard uses TACACS so an additional service must be created.
B) 802.1x is already secure so Onguard is not needed.
C) Health Checks can't be used with 802.1x.
D) Onguard uses RADIUS so an additional service must be created.
E) Onguard uses HTTPS so an additional service must be created.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
28
If the "Alerts" tab in an access tracker entry shows the following error message: "Access denied by policy", what could be a possible cause for authentication failure?
A) Configuration of the Enforcement Policy.
B) An error in the role mapping policy.
C) Failure to select an appropriate authentication method for the authentication request.
D) Implementation of a firewall policy on ClearPass.
E) Failure to find an appropriate service to process the authentication request.
A) Configuration of the Enforcement Policy.
B) An error in the role mapping policy.
C) Failure to select an appropriate authentication method for the authentication request.
D) Implementation of a firewall policy on ClearPass.
E) Failure to find an appropriate service to process the authentication request.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
29
Refer to the exhibits. Exhibit 1 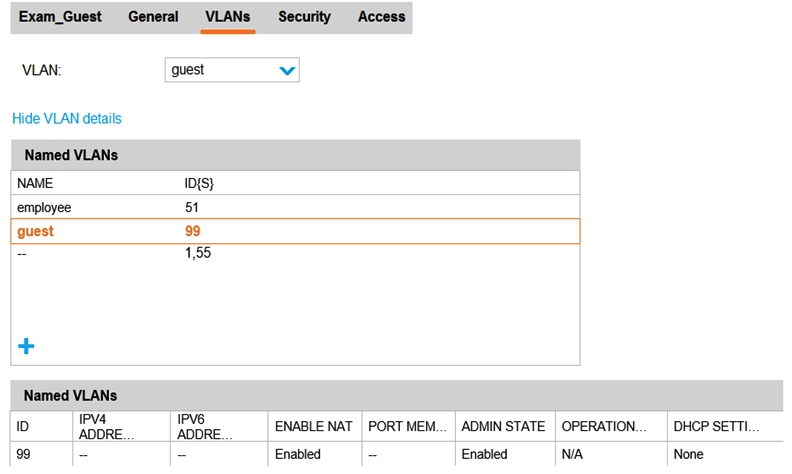 Exhibit 2
Exhibit 2 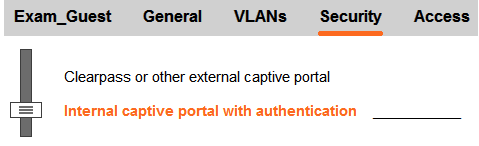 Exhibit 3
Exhibit 3 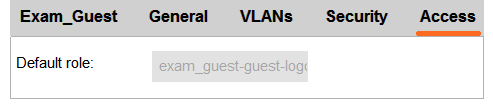 A network administrator creates a guest WLAN on an Aruba Mobility Manager (MM). The exhibits show some of the settings for the WLAN. The administrator does not change the policies for those roles. How does the firewall control guest clients when they first connect to the WLAN?
A network administrator creates a guest WLAN on an Aruba Mobility Manager (MM). The exhibits show some of the settings for the WLAN. The administrator does not change the policies for those roles. How does the firewall control guest clients when they first connect to the WLAN?
A) It permits them to send any DHCP traffic and DNS and web traffic to the Internet. It redirects web traffic destined to the private network to a login portal.
B) It does not permit them to send any traffic until they are authenticated.
C) It permits them to send any DHCP and DNS traffic, and it redirects all web traffic to a login portal.
D) It permits them to send any DHCP and RADIUS traffic. It redirects all web traffic destined to the Internet to a login portal and drops web traffic destined to the private network.
 Exhibit 2
Exhibit 2  Exhibit 3
Exhibit 3  A network administrator creates a guest WLAN on an Aruba Mobility Manager (MM). The exhibits show some of the settings for the WLAN. The administrator does not change the policies for those roles. How does the firewall control guest clients when they first connect to the WLAN?
A network administrator creates a guest WLAN on an Aruba Mobility Manager (MM). The exhibits show some of the settings for the WLAN. The administrator does not change the policies for those roles. How does the firewall control guest clients when they first connect to the WLAN?A) It permits them to send any DHCP traffic and DNS and web traffic to the Internet. It redirects web traffic destined to the private network to a login portal.
B) It does not permit them to send any traffic until they are authenticated.
C) It permits them to send any DHCP and DNS traffic, and it redirects all web traffic to a login portal.
D) It permits them to send any DHCP and RADIUS traffic. It redirects all web traffic destined to the Internet to a login portal and drops web traffic destined to the private network.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
30
A network administrator examines a list of 2.4GHz clients with low performance in the Mobility Master (MM) dashboard. Which property should pose a concern as a potential performance issue?
A) Radio PHY of HT 20MHz
B) Goodput data rate of 12Mbps
C) Max speed of 72Mbps
D) Usage of 10 MB
A) Radio PHY of HT 20MHz
B) Goodput data rate of 12Mbps
C) Max speed of 72Mbps
D) Usage of 10 MB

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
31
A company has an Aruba Mobility Master (MM)-based solution. Under which circumstance will an AP radio change channel without the use of the Mobility Master (MM)?
A) when the MM detects that a different channel has significant better quality
B) when the AP detects a large amount of interference on its channel
C) when the Mobility Controller (MC) detects a rogue AP on the channel
D) when the Client Match rules indicate that nearby clients do not support the current channel
A) when the MM detects that a different channel has significant better quality
B) when the AP detects a large amount of interference on its channel
C) when the Mobility Controller (MC) detects a rogue AP on the channel
D) when the Client Match rules indicate that nearby clients do not support the current channel

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
32
Refer to the exhibit. 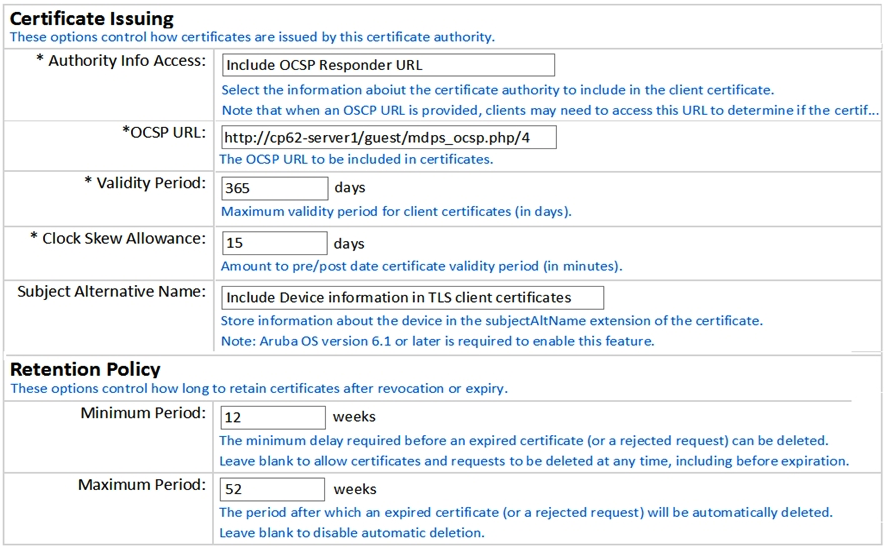 What is the purpose of the 'Clock Skew Allowance' setting? (Choose tow.)
What is the purpose of the 'Clock Skew Allowance' setting? (Choose tow.)
A) to ensure server certificate validation does not fail due to client clock sync issues
B) to set expiry time in client certificate to a few minutes longer that the default setting
C) to adjust clock time on client device to a few minutes before current time
D) to ensure client certificate validation does not fail due to client clock sync issues
E) to set start time in client certificate to a few minutes before current time
 What is the purpose of the 'Clock Skew Allowance' setting? (Choose tow.)
What is the purpose of the 'Clock Skew Allowance' setting? (Choose tow.)A) to ensure server certificate validation does not fail due to client clock sync issues
B) to set expiry time in client certificate to a few minutes longer that the default setting
C) to adjust clock time on client device to a few minutes before current time
D) to ensure client certificate validation does not fail due to client clock sync issues
E) to set start time in client certificate to a few minutes before current time

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
33
Refer to the exhibits. Exhibit 1 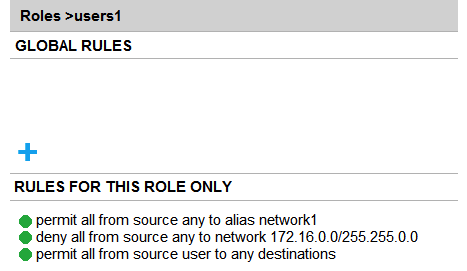 Exhibit 2
Exhibit 2 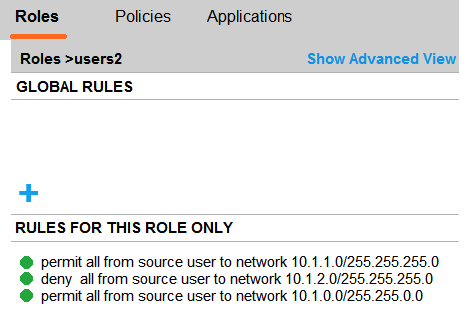 A company has an Aruba solution. Client 1 is assigned to the users1 role, and Client 2 is assigned to the users2 role. The exhibits show current firewall rules for those roles. The network1 alias used to be 10.1.1.0/24, but the network administrator now changes the network1 alias to 172.16.1.0/24. Client 1 and Client 2 both then send a packet destined to 172.16.1.10. How does the firewall handle these packets?
A company has an Aruba solution. Client 1 is assigned to the users1 role, and Client 2 is assigned to the users2 role. The exhibits show current firewall rules for those roles. The network1 alias used to be 10.1.1.0/24, but the network administrator now changes the network1 alias to 172.16.1.0/24. Client 1 and Client 2 both then send a packet destined to 172.16.1.10. How does the firewall handle these packets?
A) It denies both packets.
B) It denies the packet from Client 1 and permits the packet from Client 2.
C) It permits both packets.
D) It permits the packet from Client 1 and denies the packet from Client 2.
 Exhibit 2
Exhibit 2  A company has an Aruba solution. Client 1 is assigned to the users1 role, and Client 2 is assigned to the users2 role. The exhibits show current firewall rules for those roles. The network1 alias used to be 10.1.1.0/24, but the network administrator now changes the network1 alias to 172.16.1.0/24. Client 1 and Client 2 both then send a packet destined to 172.16.1.10. How does the firewall handle these packets?
A company has an Aruba solution. Client 1 is assigned to the users1 role, and Client 2 is assigned to the users2 role. The exhibits show current firewall rules for those roles. The network1 alias used to be 10.1.1.0/24, but the network administrator now changes the network1 alias to 172.16.1.0/24. Client 1 and Client 2 both then send a packet destined to 172.16.1.10. How does the firewall handle these packets?A) It denies both packets.
B) It denies the packet from Client 1 and permits the packet from Client 2.
C) It permits both packets.
D) It permits the packet from Client 1 and denies the packet from Client 2.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
34
Which is a valid policy simulation types in ClearPass? (Choose three.)
A) Enforcement Policy
B) Posture token derivation
C) Role Mapping
D) Endpoint Profiler
E) Chained simulation
A) Enforcement Policy
B) Posture token derivation
C) Role Mapping
D) Endpoint Profiler
E) Chained simulation

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
35
Refer to the exhibit. 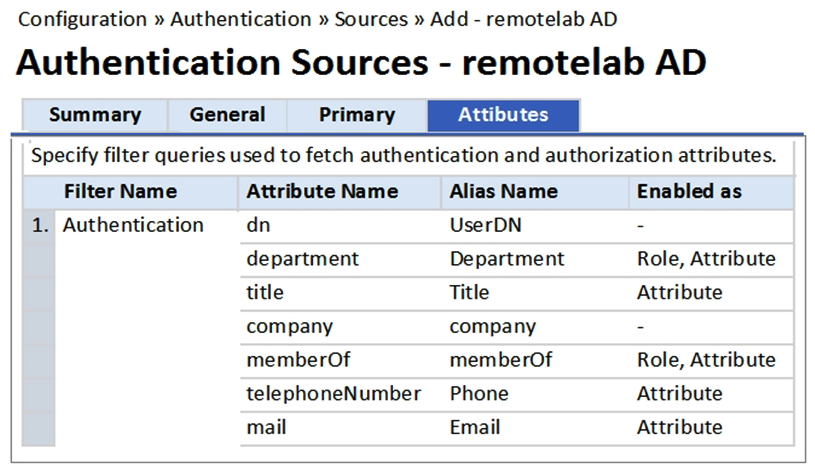 Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?
Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?
A) The attribute values of department, title, memberOf, telephoneNumber, mail are directly applied as ClearPass roles.
B) The attribute values of department and memberOf are directly applied as ClearPass roles.
C) Only the attribute value of company can be used in role mapping policies, not other attributes.
D) Only the attribute value of department and memberOf can be used in role mapping policies.
E) Only the attribute value of title, memberOf, telephoneNumber can be used in role mapping policies.
 Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?
Based on the Attribute configuration shown, which statement accurately describes the status of attribute values?A) The attribute values of department, title, memberOf, telephoneNumber, mail are directly applied as ClearPass roles.
B) The attribute values of department and memberOf are directly applied as ClearPass roles.
C) Only the attribute value of company can be used in role mapping policies, not other attributes.
D) Only the attribute value of department and memberOf can be used in role mapping policies.
E) Only the attribute value of title, memberOf, telephoneNumber can be used in role mapping policies.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
36
Which statement is true about the databases in ClearPass?
A) Entries in the guest user database do not expire.
B) A Static host list can only contain a list of IP addresses.
C) Entries in the guest user database can be deleted.
D) Entries in the local user database cannot be modified.
E) The endpoints database can only be populated by manually adding MAC addresses to the table.
A) Entries in the guest user database do not expire.
B) A Static host list can only contain a list of IP addresses.
C) Entries in the guest user database can be deleted.
D) Entries in the local user database cannot be modified.
E) The endpoints database can only be populated by manually adding MAC addresses to the table.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
37
Refer to the exhibit. 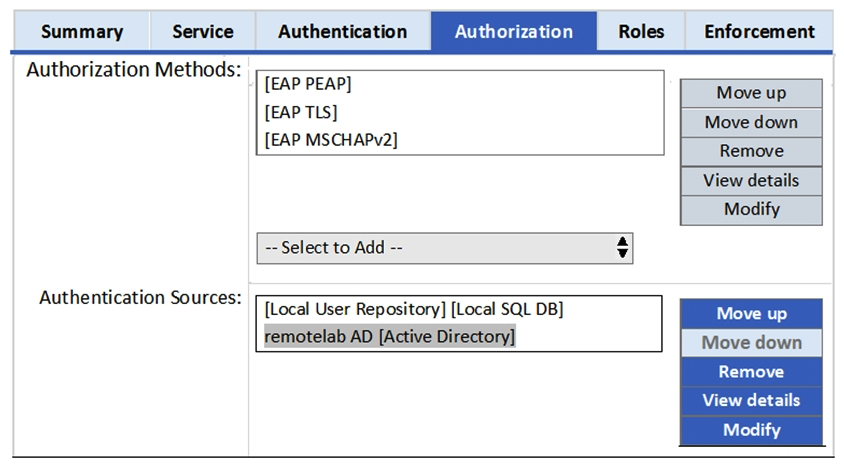 Based on the Authentication sources configuration shown, which statement accurately describes the outcome if the user is not found?
Based on the Authentication sources configuration shown, which statement accurately describes the outcome if the user is not found?
A) If the user is not found in the local user repository and remotelab AD, a reject message is sent back to the NAD.
B) If the user is not found in the local user repository but is present in the remotelab AD, a reject message is sent back to the NAD.
C) If the user is not found in the local user repository, a reject message is sent back to the NAD.
D) If the user is not found in the remotelab AD but is present in the local user repository, a reject message is sent back to the NAD.
 Based on the Authentication sources configuration shown, which statement accurately describes the outcome if the user is not found?
Based on the Authentication sources configuration shown, which statement accurately describes the outcome if the user is not found?A) If the user is not found in the local user repository and remotelab AD, a reject message is sent back to the NAD.
B) If the user is not found in the local user repository but is present in the remotelab AD, a reject message is sent back to the NAD.
C) If the user is not found in the local user repository, a reject message is sent back to the NAD.
D) If the user is not found in the remotelab AD but is present in the local user repository, a reject message is sent back to the NAD.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
38
Refer to the exhibit. 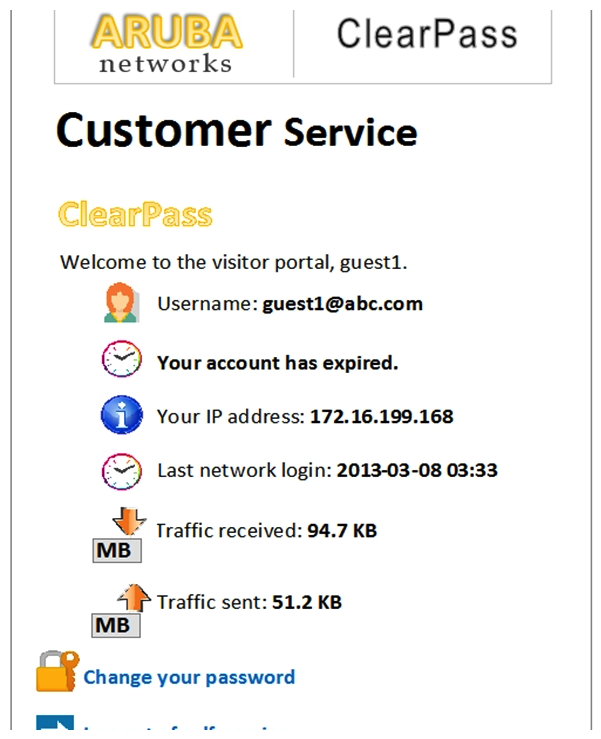 A user logged in to the Self-Service Portal as shown. What does the traffic received and sent statistics present?
A user logged in to the Self-Service Portal as shown. What does the traffic received and sent statistics present?
A) These show the total amount of traffic the guest transmitted, as seen through RADIUS CoA packets from the NAD to ClearPass.
B) These show the total amount of traffic the NAD transmitted to ClearPass, as seen through RADIUS accounting messages from the NAD to ClearPass.
C) These show the total amount of traffic the guest transmitted after account expiration, as seen through RADIUS accounting messages sent from the NAD to ClearPass.
D) These show the total amount of traffic the guest transmitted, as seen through RADIUS CoA packets from the client to ClearPass.
E) These show the total amount of traffic the guest transmitted, as seen through RADIUS accounting messages sent from the NAD to ClearPass.
 A user logged in to the Self-Service Portal as shown. What does the traffic received and sent statistics present?
A user logged in to the Self-Service Portal as shown. What does the traffic received and sent statistics present?A) These show the total amount of traffic the guest transmitted, as seen through RADIUS CoA packets from the NAD to ClearPass.
B) These show the total amount of traffic the NAD transmitted to ClearPass, as seen through RADIUS accounting messages from the NAD to ClearPass.
C) These show the total amount of traffic the guest transmitted after account expiration, as seen through RADIUS accounting messages sent from the NAD to ClearPass.
D) These show the total amount of traffic the guest transmitted, as seen through RADIUS CoA packets from the client to ClearPass.
E) These show the total amount of traffic the guest transmitted, as seen through RADIUS accounting messages sent from the NAD to ClearPass.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
39
A company has an Aruba Mobility Master (MM)-based solution. A network administrator wants to collect and analyze information about clients and access points (APs) over extended periods of time. What should the administrator do to achieve this goal?
A) Run a Traffic Analysis report on the MM.
B) Add Aruba AirWave to the solution.
C) Enable archival from the MM interface Maintenance windows.
D) Make sure that MM has sufficient AppRF licenses.
A) Run a Traffic Analysis report on the MM.
B) Add Aruba AirWave to the solution.
C) Enable archival from the MM interface Maintenance windows.
D) Make sure that MM has sufficient AppRF licenses.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
40
An Android device goes through the single-SSID Onboarding process and successfully connects using EAP-TLS to the secure network. What is the order in which services are triggered?
A) Onboard Provisioning, Onboard Authorization, Onboard Pre-Auth
B) Onboard Authorization, Onboard Provisioning, Onboard Authorization
C) Onboard Provisioning, Onboard Pre-Auth, Onboard Authorization
D) Onboard Provisioning, Onboard Authorization, Onboard Provisioning
E) Onboard Provisioning, Onboard Pre-Auth, Onboard Authorization, Onboard Provisioning
A) Onboard Provisioning, Onboard Authorization, Onboard Pre-Auth
B) Onboard Authorization, Onboard Provisioning, Onboard Authorization
C) Onboard Provisioning, Onboard Pre-Auth, Onboard Authorization
D) Onboard Provisioning, Onboard Authorization, Onboard Provisioning
E) Onboard Provisioning, Onboard Pre-Auth, Onboard Authorization, Onboard Provisioning

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck



