Deck 3: Essential Layers of Computer Networking
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/40
Play
Full screen (f)
Deck 3: Essential Layers of Computer Networking
1
At the command prompt, "C:\>netstat -n" can be issued to
A) check available host stations within a network.
B) list sockets in TCP sessions.
C) check the subnetwork address of a host.
D) find the DNS server address of a host.
E) locate the DHCP server address of a host.
A) check available host stations within a network.
B) list sockets in TCP sessions.
C) check the subnetwork address of a host.
D) find the DNS server address of a host.
E) locate the DHCP server address of a host.
B
2
Which is NOT a PDU(Protocol Data Unit) ?
A) Frame
B) Packet
C) Segment
D) Datagram
E) HTTP
A) Frame
B) Packet
C) Segment
D) Datagram
E) HTTP
E
3
In the screenshot below, I just
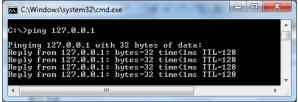
A) temporarily assigned an IP to a host.
B) contacted a server with the IP address of 127.0.0.1.
C) broadcasted a packet to the subnet of 127.0.0.x.
D) obtained the MAC address of 127.0.0.1.
E) tested my computer's TCP/IP protocol stack.

A) temporarily assigned an IP to a host.
B) contacted a server with the IP address of 127.0.0.1.
C) broadcasted a packet to the subnet of 127.0.0.x.
D) obtained the MAC address of 127.0.0.1.
E) tested my computer's TCP/IP protocol stack.
NA
4
Apache is a(n):
A) email server program
B) DNS server program
C) DHCP server program
D) HTTP (or web) server program
E) Operating system
A) email server program
B) DNS server program
C) DHCP server program
D) HTTP (or web) server program
E) Operating system

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
5
The Chrome browser operates on the _________ layer.
A) application
B) transport
C) internet
D) data link
E) physical
A) application
B) transport
C) internet
D) data link
E) physical

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
6
According to the encapsulation and de-encapsulation process between standard layers, the data field of a frame most likely includes a(n) :
A) IP packet
B) sending station's MAC address
C) receiving station's MAC address
D) TCP segment
E) application PDU (protocol data unit)
A) IP packet
B) sending station's MAC address
C) receiving station's MAC address
D) TCP segment
E) application PDU (protocol data unit)

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
7
According to the encapsulation and de-encapsulation process between standard layers, the data field of a packet may include a(n) :
A) UDP datagram
B) TCP segment
C) application PDU (protocol data unit)
D) Ethernet frame
E) UDP datagram or TCP segment
A) UDP datagram
B) TCP segment
C) application PDU (protocol data unit)
D) Ethernet frame
E) UDP datagram or TCP segment

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
8
Establishing a logical connection(or handshaking) between two computers requires the exchange of __________ messages.
A) 0
B) 1
C) 2
D) 3
E) 5
A) 0
B) 1
C) 2
D) 3
E) 5

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
9
The real-life analogy of an IP packet is:
A) the Jayne's letter to Brian
B) the airplane that delivers the Jayne's letter
C) the envelop that contains the Jayne's letter
D) Jayne and Brian's mailing addresses
E) Jayne and Brian's houses
A) the Jayne's letter to Brian
B) the airplane that delivers the Jayne's letter
C) the envelop that contains the Jayne's letter
D) Jayne and Brian's mailing addresses
E) Jayne and Brian's houses

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
10
A Class C network that uses 4 bits for the subnet ID can have up to _____ hosts in each subnet.
A) 14
B) 12
C) 16
D) 65,000
E) 4
A) 14
B) 12
C) 16
D) 65,000
E) 4

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
11
Which is the general delegation process of IP space to ISPs?
A) IEEE => Regional Registry => ISPs
B) InterNIC => Regional Registry => ISPs
C) IANA => Regional Registry => ISPs
D) Regional Registry => ICANN => ISPs
E) Regional Registry => InterNIC => ISP
A) IEEE => Regional Registry => ISPs
B) InterNIC => Regional Registry => ISPs
C) IANA => Regional Registry => ISPs
D) Regional Registry => ICANN => ISPs
E) Regional Registry => InterNIC => ISP

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
12
Standard details of network cables should be defined in the _____ layer
A) application
B) transport
C) internet
D) data link
E) physical
A) application
B) transport
C) internet
D) data link
E) physical

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
13
Which of the following is NOT a layer in the hybrid TCP/IP-OSI architecture?
A) physical
B) session
C) internet
D) data link
E) transport
A) physical
B) session
C) internet
D) data link
E) transport

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
14
Which correctly pairs a standard layer and its PDU name?
A) application - segment
B) transport - frame
C) internet - packet
D) data link - segment
E) physical - datagram
A) application - segment
B) transport - frame
C) internet - packet
D) data link - segment
E) physical - datagram

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
15
Which of these is an internet layer function?
A) Provision of message integrity
B) Flow control
C) Error control
D) Session management
E) Packet creation
A) Provision of message integrity
B) Flow control
C) Error control
D) Session management
E) Packet creation

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
16
Below message is generated at the _____ layer:
"GET / /HTTP 1.1
Host: www.whitehouse.gov"
A) application
B) transport
C) internet
D) data link
E) physical
"GET / /HTTP 1.1
Host: www.whitehouse.gov"
A) application
B) transport
C) internet
D) data link
E) physical

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
17
SYN and ACK are exchanged for _______ between two hosts:
A) session establishment
B) data exchange
C) pinging
D) detection of transmission errors
E) detection of lost messages
A) session establishment
B) data exchange
C) pinging
D) detection of transmission errors
E) detection of lost messages

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
18
As for TCP and UDP, which statement is CORRECT?
A) Both are connection-oriented protocol.
B) Both are defined at the transport layer of TCP/IP.
C) Both are reliable protocol.
D) TCP is better than UDP in handling real-time traffic.
E) Both undertake the detection and correction of transmission errors.
A) Both are connection-oriented protocol.
B) Both are defined at the transport layer of TCP/IP.
C) Both are reliable protocol.
D) TCP is better than UDP in handling real-time traffic.
E) Both undertake the detection and correction of transmission errors.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
19
The TTL (time to live) value included in an IP packet indicates:
A) a maximum number of circuits a packet can go through.
B) a maximum number of routers a packet can go through.
C) a maximum number of switches a packet can go through within a network.
D) the amount of time (ex. 3 minutes) left before the expiration of a packet.
E) the amount of time initially given to a packet for its delivery.
A) a maximum number of circuits a packet can go through.
B) a maximum number of routers a packet can go through.
C) a maximum number of switches a packet can go through within a network.
D) the amount of time (ex. 3 minutes) left before the expiration of a packet.
E) the amount of time initially given to a packet for its delivery.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
20
Temporary IP addresses are dynamically allocated by the _________ to requesting hosts.
A) SNMP server
B) DNS server
C) SMTP server
D) DHCP server
E) Remote access server
A) SNMP server
B) DNS server
C) SMTP server
D) DHCP server
E) Remote access server

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
21
When a workstation tries to communicate with a server (ex. www.cnn.com), which of these is a possible port number of the sender ?
A) 80
B) 21
C) 58
D) 110
E) 65000
A) 80
B) 21
C) 58
D) 110
E) 65000

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
22
________ is an application layer protocol that enables mapping between host names and their IP addresses.
A) SMTP
B) DNS
C) IRC
D) SSH
E) SNMP
A) SMTP
B) DNS
C) IRC
D) SSH
E) SNMP

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
23
The port number, 134, must be most likely:
A) a well-known port number assigned to a server application.
B) an ephemeral port number assigned to a server application.
C) a dynamic port number assigned to a client application.
D) a dynamic port number assigned to a server application.
E) a well-known port number assigned to a client application.
A) a well-known port number assigned to a server application.
B) an ephemeral port number assigned to a server application.
C) a dynamic port number assigned to a client application.
D) a dynamic port number assigned to a server application.
E) a well-known port number assigned to a client application.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
24
A protocol should govern communications between:
A) programs in the same layer of a computer.
B) programs in the same layer of two different computers.
C) programs in two different layers of a computer.
D) programs in two different layers of two different computers.
E) B and C are both correct.
A) programs in the same layer of a computer.
B) programs in the same layer of two different computers.
C) programs in two different layers of a computer.
D) programs in two different layers of two different computers.
E) B and C are both correct.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
25
Choose a CORRECT statement on port numbers.
A) Generally, server hosts use ephemeral port numbers to identify applications.
B) Port numbers are assigned to both TCP and UDP applications.
C) Well-known port numbers range 0 through 65535.
D) Computer operating systems use an identical range of ephemeral port numbers.
E) The source port of a TCP segment is generally 80 when a browser initiates correspondence with a web server.
A) Generally, server hosts use ephemeral port numbers to identify applications.
B) Port numbers are assigned to both TCP and UDP applications.
C) Well-known port numbers range 0 through 65535.
D) Computer operating systems use an identical range of ephemeral port numbers.
E) The source port of a TCP segment is generally 80 when a browser initiates correspondence with a web server.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
26
Which statement is true?
A) The official address of the Internet is the host name.
B) IP packets contain a header, a data, and a trailer fields.
C) OSI standards are more popular than TCP/IP standards in the application layer.
D) International Standard Organization (ISO) is responsible for developing TCP/IP standards.
E) TCP/IP standards dominate the internet layer.
A) The official address of the Internet is the host name.
B) IP packets contain a header, a data, and a trailer fields.
C) OSI standards are more popular than TCP/IP standards in the application layer.
D) International Standard Organization (ISO) is responsible for developing TCP/IP standards.
E) TCP/IP standards dominate the internet layer.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
27
Which PDU (protocol data unit) contains information necessary for handshaking (or session establishment) between two hosts?
A) transport layer's segment
B) transport layer's datagram
C) internet layer's packet
D) data link layer's frame
E) application PDU
A) transport layer's segment
B) transport layer's datagram
C) internet layer's packet
D) data link layer's frame
E) application PDU

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
28
In TCP, which party should decide whether to retransmit a lost or damaged segment?
A) the original sender station
B) the receiver station
C) either the sender or the receiver station depending on the situation.
D) the first router that connects the sender station to the Internet
E) the first router that connects the receiver station to the Internet
A) the original sender station
B) the receiver station
C) either the sender or the receiver station depending on the situation.
D) the first router that connects the sender station to the Internet
E) the first router that connects the receiver station to the Internet

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
29
Choose an INCORRECT statement on the transport layer process.
A) The port information should be found in the transport layer's TCP segment.
B) The port information should be found in the transport layer's UDP datagram.
C) Opening a TCP connection needs the handshaking process to establish a session.
D) The normal termination of a TCP connection takes exchange of several packets.
E) Transporting multiple files necessary to construct a web page takes one TCP session (assume that HTTP1.1 is used).
A) The port information should be found in the transport layer's TCP segment.
B) The port information should be found in the transport layer's UDP datagram.
C) Opening a TCP connection needs the handshaking process to establish a session.
D) The normal termination of a TCP connection takes exchange of several packets.
E) Transporting multiple files necessary to construct a web page takes one TCP session (assume that HTTP1.1 is used).

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
30
Choose a CORRECT statement on the flag field bit of the TCP segment.
A) The ACK bit is used to initiate a session.
B) The SYN bit is used to acknowledge packet arrival.
C) The END bit is used to terminate a session.
D) The INI bit is used to initiate a session.
E) The FIN bit is used to terminate a session.
A) The ACK bit is used to initiate a session.
B) The SYN bit is used to acknowledge packet arrival.
C) The END bit is used to terminate a session.
D) The INI bit is used to initiate a session.
E) The FIN bit is used to terminate a session.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
31
MAC addresses are used at the _________ layer for addressing.
A) Application
B) Data Link
C) Internet
D) Physical
E) Transport
A) Application
B) Data Link
C) Internet
D) Physical
E) Transport

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
32
ICMP messages are encapsulated in the data field of _________ for transmission.
A) IP
B) TCP
C) UDP
D) DNS
E) HTTP
A) IP
B) TCP
C) UDP
D) DNS
E) HTTP

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
33
I am trying to reach a web server, www.chicago.edu. The response message from the DNS server tells my computer the _____.
A) domain name of the www.chicago.edu server
B) IP address of the www.chicago.edu server
C) Default gateway address of the www.chicago.edu server
D) ISP of www.chicago.edu
E) MAC address of the www.chicago.edu server
A) domain name of the www.chicago.edu server
B) IP address of the www.chicago.edu server
C) Default gateway address of the www.chicago.edu server
D) ISP of www.chicago.edu
E) MAC address of the www.chicago.edu server

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
34
When does TCP of a host station decide to retransmit a segment?
A) When it does not receive an acknowledgment from the receiver.
B) Never. TCP is not capable of retransmitting segments.
C) When the neighboring switch requests a retransmission due to a lost segment.
D) When the neighboring router requests a retransmission due to a lost segment.
E) When a TCP connection is not properly closed.
A) When it does not receive an acknowledgment from the receiver.
B) Never. TCP is not capable of retransmitting segments.
C) When the neighboring switch requests a retransmission due to a lost segment.
D) When the neighboring router requests a retransmission due to a lost segment.
E) When a TCP connection is not properly closed.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
35
Choose a WRONG statement on the network architecture.
A) It defines basic networking functions and their relationships.
B) It is typically manifested in a layer structure.
C) It is also called as a reference model.
D) A company has to choose either TCP/IP or OSI for its implementation.
E) Many communication standards are defined in it in the form of protocols.
A) It defines basic networking functions and their relationships.
B) It is typically manifested in a layer structure.
C) It is also called as a reference model.
D) A company has to choose either TCP/IP or OSI for its implementation.
E) Many communication standards are defined in it in the form of protocols.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
36
The following figure demonstrates layer processing necessary to exchange data between two host computers. The device within the ellipse must be a _______. 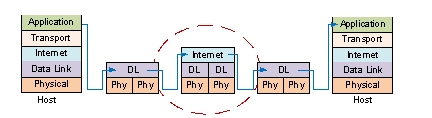
A) Bridge
B) Switch
C) Router
D) Hub
E) Access point

A) Bridge
B) Switch
C) Router
D) Hub
E) Access point

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
37
UDP (User Datagram Protocol)
A) belongs to the data link layer.
B) is frequently used by real-time applications.
C) provides a connection-oriented service.
D) belongs to the network layer.
E) Issues an acknowledgment when a packet is received.
A) belongs to the data link layer.
B) is frequently used by real-time applications.
C) provides a connection-oriented service.
D) belongs to the network layer.
E) Issues an acknowledgment when a packet is received.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
38
Which statement is CORRECT on the connection-orientation/reliability of communications?
A) Connectionless services have explicit openings and closings.
B) Almost all protocols currently in use are connection-oriented and reliable in nature.
C) Reliable protocols resend lost or damaged messages.
D) TCP is the only unreliable protocol.
E) TCP is a connection-less protocol that does not need handshaking.
A) Connectionless services have explicit openings and closings.
B) Almost all protocols currently in use are connection-oriented and reliable in nature.
C) Reliable protocols resend lost or damaged messages.
D) TCP is the only unreliable protocol.
E) TCP is a connection-less protocol that does not need handshaking.

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
39
Refer to the figure in which the "www.yahoo.com" server is pinged. What is the protocol used to produce the message for communication between two hosts? ________________________. 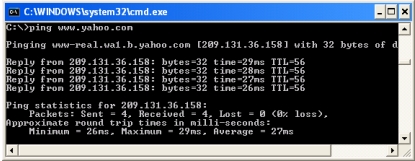
A) DHCP
B) DNS
C) ICMP
D) HTTP
E) ARP

A) DHCP
B) DNS
C) ICMP
D) HTTP
E) ARP

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck
40
Which is NOT correctly paired in terms of the software or hardware of a host computer that implements each layer function? Choose the least relevant.
A) A
B) B
C) C
D) D
E) E
A) A
B) B
C) C
D) D
E) E

Unlock Deck
Unlock for access to all 40 flashcards in this deck.
Unlock Deck
k this deck



