Deck 12: Ethical Guidelines for Information Use
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/52
Play
Full screen (f)
Deck 12: Ethical Guidelines for Information Use
1
A manager that primarily focuses on the shareholders of the corporation rather than all of the vested parties in the businesses operations and activities is practicing which theory of normative business ethics?
A) Stakeholder theory
B) Investor theory
C) Stockholder theory
D) Shareholder theory
E) Social contract theory
A) Stakeholder theory
B) Investor theory
C) Stockholder theory
D) Shareholder theory
E) Social contract theory
C
2
A company should examine this area of the control of information if it wants to determine what data it has the right to monitor and capture from its employees.
A) Privacy
B) Accuracy
C) Accessibility
D) Perfection
E) Property
A) Privacy
B) Accuracy
C) Accessibility
D) Perfection
E) Property
A
3
The European Union relies on a government data protection agency and specific privacy protection standards outlined in the ___________.
A) Safe Harbor Framework
B) PAPA Principles
C) Directive on Data Protection
D) HIPPA
E) SoX Act
A) Safe Harbor Framework
B) PAPA Principles
C) Directive on Data Protection
D) HIPPA
E) SoX Act
C
4
Information privacy guidelines should come from what level in a company?
A) CEO and top-level executives
B) Middle management
C) Employees
D) Federal regulations
E) State laws
A) CEO and top-level executives
B) Middle management
C) Employees
D) Federal regulations
E) State laws

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
5
Which normative theory of business ethics would TJX have displayed if it had informed customers as soon as the breach was corrected and told other retailers how to prevent future security breaches?
A) Stakeholder
B) Stockholder
C) Social contract
D) Investor
E) Corporate social responsibility
A) Stakeholder
B) Stockholder
C) Social contract
D) Investor
E) Corporate social responsibility

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
6
"Who owns information?" and "What are the just and fair prices for its exchange?" are part of this ethical issue:
A) Privacy
B) Accuracy
C) Ownership
D) Property
E) Accessibility
A) Privacy
B) Accuracy
C) Ownership
D) Property
E) Accessibility

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
7
Green computing is often associated with supporting the triple bottom line known as:
A) Economic, environmental and social
B) Stockholder, stakeholder and society
C) People, Privacy and Property
D) Google, Facebook and Microsoft
E) Data, information and knowledge
A) Economic, environmental and social
B) Stockholder, stakeholder and society
C) People, Privacy and Property
D) Google, Facebook and Microsoft
E) Data, information and knowledge

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
8
This is a text message that is stored on a user's computer by a Web server that helps trace the user's browsing habits.
A) Script
B) Cookie
C) Id theft
D) Firewall
E) Data file
A) Script
B) Cookie
C) Id theft
D) Firewall
E) Data file

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
9
All of the following are examples of green computing EXCEPT:
A) Virtualization
B) Cloud computing
C) Tidal powered servers
D) Server workloads moved to off-peak hours
E) Cookies
A) Virtualization
B) Cloud computing
C) Tidal powered servers
D) Server workloads moved to off-peak hours
E) Cookies

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
10
TJX's handling of its serious data breach is consistent with which one of the following?
A) Stakeholder theory
B) Stockholder theory
C) Social normative
D) Social contract theory
E) Corporate social responsibility
A) Stakeholder theory
B) Stockholder theory
C) Social normative
D) Social contract theory
E) Corporate social responsibility

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
11
The European Union Directive on Data Protection does all of the following EXCEPT:
A) Expect accurate and up-to-date data on collected personal information
B) Allow companies to only keep data as long as necessary
C) Set standards for the collection, storage and processing of personal information
D) Regulate data standards for publically traded companies
E) Prohibit the transfer of personal data to non-European Union nations that do not meet certain standards
A) Expect accurate and up-to-date data on collected personal information
B) Allow companies to only keep data as long as necessary
C) Set standards for the collection, storage and processing of personal information
D) Regulate data standards for publically traded companies
E) Prohibit the transfer of personal data to non-European Union nations that do not meet certain standards

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
12
In the chapter,there is the statement,"Internet companies are in business for the money and hence they really would prefer to keep their customers in the dark about how their personal data is being used to generate profits".Assuming this statement is true,with which ethical theory would you say these Internet companies are most aligned?
A) Stockholder theory
B) Stakeholder theory
C) Property theory
D) Fiduciary theory
E) Normative theory
A) Stockholder theory
B) Stakeholder theory
C) Property theory
D) Fiduciary theory
E) Normative theory

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
13
This theory of normative business ethics seeks to create value for people in a manner that is just and nondiscriminatory.
A) Stakeholder theory
B) Investor theory
C) Social contract theory
D) Shareholder theory
E) Stockholder theory
A) Stakeholder theory
B) Investor theory
C) Social contract theory
D) Shareholder theory
E) Stockholder theory

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
14
This is the term used to describe ethical dilemmas that arise with the development and application of IT.
A) Stockholder theory
B) PAPA principles
C) Information ethics
D) Normative theories
E) IT dilemmas
A) Stockholder theory
B) PAPA principles
C) Information ethics
D) Normative theories
E) IT dilemmas

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
15
This act of 1996 is designed to safeguard the electronic exchange of patient records in the health care industry.
A) SoX
B) HIPAA
C) IETF
D) COBIT
E) PAPA
A) SoX
B) HIPAA
C) IETF
D) COBIT
E) PAPA

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
16
What principles,developed in 2000 by the US Department of Commerce (DOC) in consultation with the European Commission,allow U.S.companies to be placed on a list maintained by the DOC?
A) Safe Harbor framework
B) Approved Business framework
C) PAPA framework
D) Property Harbor framework
E) Safe Business framework
A) Safe Harbor framework
B) Approved Business framework
C) PAPA framework
D) Property Harbor framework
E) Safe Business framework

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
17
Today's managers must ensure that information about their employees and customers is only available to those who have a right to see it and use it,an issue referred to as:
A) Privacy
B) Accuracy
C) Accessibility
D) Perfection
E) Property
A) Privacy
B) Accuracy
C) Accessibility
D) Perfection
E) Property

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
18
In today's digital word,individuals can control their privacy through choice,______ ,and correction.
A) Protection
B) Consent
C) Property
D) Communication
E) Consideration
A) Protection
B) Consent
C) Property
D) Communication
E) Consideration

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
19
Questions like "Who is responsible for the reliability of information?" and "Who will be accountable for errors in the information?" are part of this ethical issue.
A) Privacy
B) Accuracy
C) Authenticity
D) Perfection
E) Purpose
A) Privacy
B) Accuracy
C) Authenticity
D) Perfection
E) Purpose

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
20
The question "What information does a person or an organization have a right or a privilege to obtain?" is part of this ethical issue.
A) Privacy
B) Accuracy
C) Accessibility
D) Perfection
E) Property
A) Privacy
B) Accuracy
C) Accessibility
D) Perfection
E) Property

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
21
This term is used to define energy-efficient computing resources.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
22
The Stakeholder theory requires managers to pursue projects in ways that are compatible with the well-being of society.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
23
Explain how green computing can satisfy each of the three normative theories of business ethics.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
24
Those who possess the "best" information and know how to use it,win.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
25
This is a crime in which the thief uses a victim's personal information to impersonate the victim.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
26
In today's digital word,individuals can control their privacy through ______,consent,and correction.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
27
Green computing benefits _____ which is sometimes referred to as "People,Planet,Profit".

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
28
Give an example of U.S.legislature designed to ensure the privacy and protection of information for a specific industry.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
29
In TJX's case,the security breach made its customers vulnerable to this.
A) Loss of personal property
B) Inaccurate personal data
C) Identity theft
D) Loss of access to personal data
E) Credit card fees
A) Loss of personal property
B) Inaccurate personal data
C) Identity theft
D) Loss of access to personal data
E) Credit card fees

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
30
List the four areas,as outlined in the text,which deal with control of information.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
31
Green computing is a passing phase and will likely be less strategic to companies in the future.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
32
Unlike the European Union,the U.S.has no general legislature ensuring Internet privacy rights.Instead,the U.S.encourages self-regulation and has introduced industry-specific regulations as needed.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
33
Over time it becomes easier to maintain the accuracy of information.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
34
"Digital natives" are uncomfortable building relationships on the Internet because they understand the consequences of sharing information publically.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
35
An Internet web site that wishes to abide by fair privacy practices will do all of the following EXCEPT:
A) Allow the consumer the choice to participate in the site or not
B) Post policies about how personal information gathered from consumers will be used
C) Afford the consumer the opportunity to view and contest the accuracy of the data collected
D) Secure collected consumer information
E) All of the above.
A) Allow the consumer the choice to participate in the site or not
B) Post policies about how personal information gathered from consumers will be used
C) Afford the consumer the opportunity to view and contest the accuracy of the data collected
D) Secure collected consumer information
E) All of the above.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
36
Google Flu Trends aggregates personal search data in order to estimate world-wide flu activity.Google's site has drawn criticism due to the sharing of users' online behavior without getting their consent.This,in essence,violates the user's right to:
A) Privacy
B) Property
C) Accuracy
D) Accessibility
E) Identity
A) Privacy
B) Property
C) Accuracy
D) Accessibility
E) Identity

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
37
This is a growing service designed to help individuals and companies clean up their online presence so that a search for their name produces favorable results.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
38
The social contract theory is made up of two distinct components - social welfare and _________.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
39
The concern about privacy on Facebook and other social media sites is greater in the U.S.than it is in Europe.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
40
Many organizations and even consumers use this to control access to a network like the Internet,allowing only authorized traffic to pass.
A) Encryption
B) VPN
C) Firewall
D) Anonymizing tools
E) Filtering
A) Encryption
B) VPN
C) Firewall
D) Anonymizing tools
E) Filtering

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
41
Match the U.S.legislative/regulatory act with the industry for which it governs the control of information.
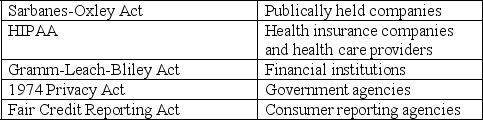


Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
42
Match the managerial control concern with the challenges a manager may face on a regular basis.



Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
43
Provide an example of a company that has faced a dilemma reconciling their corporate policies within a country where it hopes to operate.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
44
Match each normative theory of business ethics to its primary objective.



Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
45
Match the security tool to its security category.
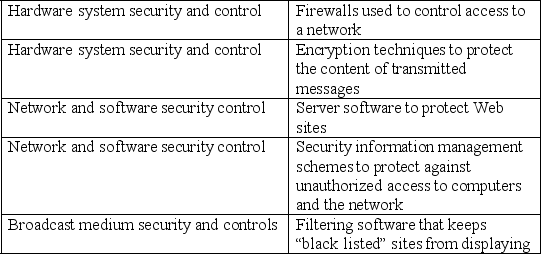


Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
46
Internal threats are considered the most lethal threat.What are they,why are they so lethal and what can a company do to protect against them?
Matching
Matching

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
47
Give reasons why users are so willing to forgo privacy on the Internet.

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
48
Bradley Manning,a U.S.intelligence officer,took over 500,000 documents from the U.S.State Department and gave them to a public Web site called Wikileaks for publication.These documents were far ranging in their content. Match the actions below with the failure to control and the misuse of sensitive information.



Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
49
How does the European Union approach data protection differently than the United States?

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
50
Match the situation below with the area of information control it falls under.
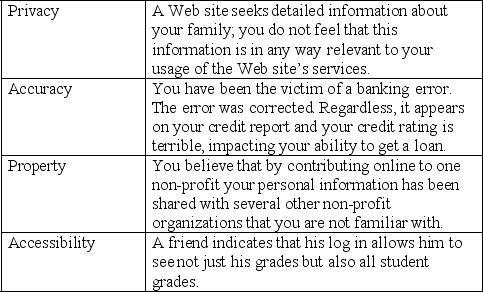


Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
51
Match the critical question with the information control issue it addresses.
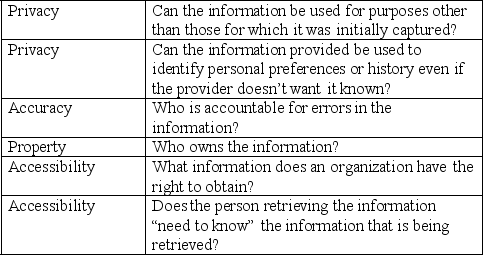


Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck
52
What security and controls should a company use to protect its computer infrastructure? Why do managers need to be involved in the decisions about security and control measures?

Unlock Deck
Unlock for access to all 52 flashcards in this deck.
Unlock Deck
k this deck



