Deck 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/98
Play
Full screen (f)
Deck 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)
1
Name three methods by which client configuration can be performed in an explicit ProxySG deployment.
A) Configure the user agent to point to the IP address or hostname of the ProxySG
B) Configure the user agent to point to the location of a PAC file
C) Configure the user agent to use WPAD
D) Use Symantec Management Center to configure the user agent
E) Configure forwarding hosts on the ProxySG
A) Configure the user agent to point to the IP address or hostname of the ProxySG
B) Configure the user agent to point to the location of a PAC file
C) Configure the user agent to use WPAD
D) Use Symantec Management Center to configure the user agent
E) Configure forwarding hosts on the ProxySG
Configure the user agent to point to the IP address or hostname of the ProxySG
Configure the user agent to point to the location of a PAC file
Configure the user agent to use WPAD
Configure the user agent to point to the location of a PAC file
Configure the user agent to use WPAD
2
Which services are included in the Intelligence Services Advanced Bundle?
A) Content categories
B) Threat risk levels
C) All of these
D) Geolocation
A) Content categories
B) Threat risk levels
C) All of these
D) Geolocation
All of these
3
Which SGOS edition is designed for Secure Web Gateway deployments?
A) Premium Edition
B) MACH5 edition
C) SWG Edition
D) Proxy Edition
A) Premium Edition
B) MACH5 edition
C) SWG Edition
D) Proxy Edition
SWG Edition
4
What does the authentication mode specify?
A) The time-to-live for credentials
B) The protocol used to communicate with the authentication service
C) The challenge type and the accepted surrogate
D) Whether the credentials will be encrypted
A) The time-to-live for credentials
B) The protocol used to communicate with the authentication service
C) The challenge type and the accepted surrogate
D) Whether the credentials will be encrypted

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
5
If you have configured continuous uploading of access logs and the ProxySG is unable to reach the upload destination, what happens to the log entries?
A) They are uploaded in real time to the backup upload destination configured in the Management Console
B) None of these answers
C) They are stored locally until the connection is re-established, and then they are uploaded
D) They are discarded
A) They are uploaded in real time to the backup upload destination configured in the Management Console
B) None of these answers
C) They are stored locally until the connection is re-established, and then they are uploaded
D) They are discarded

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
6
Which built-in tool would you use to monitor external resources?
A) Sysinfo
B) Health checks
C) Event log
D) SNMP
A) Sysinfo
B) Health checks
C) Event log
D) SNMP

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
7
Which Symantec product is best suited for simultaneously administering a large number of ProxySG appliances?
A) Reporter
B) PacketShaper
C) Content Analysis
D) Management Center
A) Reporter
B) PacketShaper
C) Content Analysis
D) Management Center

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
8
Where is the WebFilter database stored? (Select two)
A) On clients' mobile devices
B) On a properly licensed ProxySG
C) At several data centers around the world
D) At third-party data centers
A) On clients' mobile devices
B) On a properly licensed ProxySG
C) At several data centers around the world
D) At third-party data centers

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
9
When does the ProxySG establish an Schannel?
A) When a client request is first received
B) When the client sends an NTLM type 2 message to ProxySG
C) When IWA authentication fails
D) When the client sends an NTLM type 3 message to the ProxySG
A) When a client request is first received
B) When the client sends an NTLM type 2 message to ProxySG
C) When IWA authentication fails
D) When the client sends an NTLM type 3 message to the ProxySG

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
10
Why is Kerberos performance better than NTLM?
A) It uses less encryption
B) None of these answers
C) Only two round trips are required between the browser and an authentication server
D) It works with later versions of Microsoft Windows
A) It uses less encryption
B) None of these answers
C) Only two round trips are required between the browser and an authentication server
D) It works with later versions of Microsoft Windows

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
11
What stops further rule processing in a layer?
A) When the final rule on the layer is reached
B) When two rules match
C) When a later rule contradicts an earlier rule
D) The first rule in the layer that matches
A) When the final rule on the layer is reached
B) When two rules match
C) When a later rule contradicts an earlier rule
D) The first rule in the layer that matches

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
12
Why is authentication using Basic credentials typically used over HTTPS?
A) Username and password are base-64 encoded
B) No session identifier is required
C) No cookies are required
D) No other credentials are compatible with HTTPS
A) Username and password are base-64 encoded
B) No session identifier is required
C) No cookies are required
D) No other credentials are compatible with HTTPS

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
13
SGOS is based on which other operating system?
A) Unix
B) VxWorks
C) pSOS
D) None of these answers
E) Windows
A) Unix
B) VxWorks
C) pSOS
D) None of these answers
E) Windows

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
14
What is one drawback to using apparent data type to detect the file type?
A) Presents a security risk
B) Less accurate than HTTP content type detection
C) None of these answers
D) Most resource-intensive
A) Presents a security risk
B) Less accurate than HTTP content type detection
C) None of these answers
D) Most resource-intensive

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
15
What does each proxy service define? (Choose two.)
A) ProxySG SGOS version
B) Proxy type to use to process traffic
C) Attributes
D) Policy
A) ProxySG SGOS version
B) Proxy type to use to process traffic
C) Attributes
D) Policy

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
16
When the ProxySG uses a virtual URL for user authentication, what must the virtual URL point to?
A) The IP address of the origin content server
B) A hostname that the user agent can DNS-resolve to an IP address
C) None of these answers
D) The IP address of the ProxySG
A) The IP address of the origin content server
B) A hostname that the user agent can DNS-resolve to an IP address
C) None of these answers
D) The IP address of the ProxySG

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
17
Which of the following is not a VPM trigger object?
A) Time
B) Source
C) Destination
D) Service
E) Action
A) Time
B) Source
C) Destination
D) Service
E) Action

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
18
By default, HTTP traffic that is logged is recorded to which log facility?
A) bcreportermain_v1
B) main
C) elf
D) http
A) bcreportermain_v1
B) main
C) elf
D) http

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
19
What rules in a VPM layer are being evaluated, what causes evaluation to stop and proceed to the next layer?
A) A miss against the trigger in that rule
B) Neither a miss nor a match
C) A default policy of Deny
D) A match against the trigger in that rule
A) A miss against the trigger in that rule
B) Neither a miss nor a match
C) A default policy of Deny
D) A match against the trigger in that rule

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
20
How do you create a new built-in exception of the ProxySG?
A) In the Visual Policy Manager
B) You cannot do this
C) In the Management Console
D) In Content Policy Language
A) In the Visual Policy Manager
B) You cannot do this
C) In the Management Console
D) In Content Policy Language

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
21
Which deployment method represents a single point of failure?
A) None of these answers
B) Inline XXX
C) Explicit
D) Transparent
A) None of these answers
B) Inline XXX
C) Explicit
D) Transparent

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
22
How does the Audit module get data?
A) Firewalls and proxies
B) Cloud application APIs
C) CloudSOC gateway
D) Manual uploads
A) Firewalls and proxies
B) Cloud application APIs
C) CloudSOC gateway
D) Manual uploads

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
23
Of the methods that the ProxySG uses to detect file type, which one is usually the most accurate?
A) Checking the HTTP content type (or MIME type)
B) Performing an anti-virus scan
C) Detecting apparent data type
D) Checking the file extension
A) Checking the HTTP content type (or MIME type)
B) Performing an anti-virus scan
C) Detecting apparent data type
D) Checking the file extension

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
24
If you lose the password to the setup console, which of these methods can be used to regain access to the setup console? (Choose three.)
A) Open a serial connection, and use the CLI command restore-defaults factory-defaults
B) Use the appliance reset button, if available on this model
C) Use the front panel buttons and screen, if available on this model, to reset the password
D) Press Control + ALT + DEL
A) Open a serial connection, and use the CLI command restore-defaults factory-defaults
B) Use the appliance reset button, if available on this model
C) Use the front panel buttons and screen, if available on this model, to reset the password
D) Press Control + ALT + DEL

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
25
A primary difference between a proxy server and a firewall is that proxy is not fundamentally what?
A) An edge device
B) A man-in-the-middle
C) A Layer 3 switch
D) A router
A) An edge device
B) A man-in-the-middle
C) A Layer 3 switch
D) A router

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
26
Where in the Management Console would you look to find all sessions that are being intercepted by the services framework of the ProxySG?
A) Heartbeats
B) Maintenance > System Tools
C) Statistics > Sessions > Active Sessions
D) Advanced statistics
A) Heartbeats
B) Maintenance > System Tools
C) Statistics > Sessions > Active Sessions
D) Advanced statistics

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
27
Which of the following are recommended to improve CPU performance? (Choose two.)
A) Edit the size of emulated certificates
B) Deny wildcard certificates
C) Enable DHE
D) Reduce the number of emulated certificates
A) Edit the size of emulated certificates
B) Deny wildcard certificates
C) Enable DHE
D) Reduce the number of emulated certificates

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
28
What happens when the ProxySG bypasses traffic?
A) No policy can be applied
B) Only the default policy can be applied
C) The traffic is blocked
D) An exception message is displayed to the user
A) No policy can be applied
B) Only the default policy can be applied
C) The traffic is blocked
D) An exception message is displayed to the user

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
29
When must BCAAA be used?
A) When you need to establish more than one Schannel to increase performance
B) When the ProxySG cannot directly use APIs that require traditional operating systems
C) When more than one ProxySG are deployed
D) When Basic credentials are used
A) When you need to establish more than one Schannel to increase performance
B) When the ProxySG cannot directly use APIs that require traditional operating systems
C) When more than one ProxySG are deployed
D) When Basic credentials are used

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
30
What needs to be selected for the Explicit HTTP service to be able to hand off SSL traffic?
A) Port 443
B) Enable ADN
C) Early Intercept
D) Detect Protocol
A) Port 443
B) Enable ADN
C) Early Intercept
D) Detect Protocol

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
31
Which of the following are always included in both the request and response headers?
A) Information relevant to the connection between the client and the server
B) DNS query
C) ICAP version number
D) Cipher suite
A) Information relevant to the connection between the client and the server
B) DNS query
C) ICAP version number
D) Cipher suite

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
32
Where does ProxySG object caching usually result in the most bandwidth savings?
A) On the server side
B) On the client side
A) On the server side
B) On the client side

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
33
The ProxySG simultaneously opens multiple server connections to retrieve objects referenced on a web page before the client actually issues the requests for those objects. This statement best describes which ProxySG caching technique?
A) Asynchronous adaptive refresh
B) Popularity contest
C) Pipelining
D) Cost-based deletion
A) Asynchronous adaptive refresh
B) Popularity contest
C) Pipelining
D) Cost-based deletion

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
34
Where are surrogate credentials stored?
A) On the authentication server
B) In the ProxySG authentication cache
C) In a cookie in the user's web browser
A) On the authentication server
B) In the ProxySG authentication cache
C) In a cookie in the user's web browser

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
35
Does the policy trace flag malfunctioning policy?
A) Yes
B) No
A) Yes
B) No

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
36
What would happen if the ProxySG did not use surrogate credentials to authenticate users who use transparent proxy connections?
A) They would not be able to authenticate to the ProxySG
B) The ProxySG does not need to use surrogate credentials to authenticate users who use transparent proxy connections
C) They would have to reauthenticate for each domain that they access
A) They would not be able to authenticate to the ProxySG
B) The ProxySG does not need to use surrogate credentials to authenticate users who use transparent proxy connections
C) They would have to reauthenticate for each domain that they access

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
37
When policy created in the VPM is installed, what two files does the VPM update on the ProxySG? (Choose two.)
A) Local policy file
B) Central policy file
C) VPM-XML file
D) VPM-CPL file
A) Local policy file
B) Central policy file
C) VPM-XML file
D) VPM-CPL file

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
38
In the Management Console, how can you determine the serial number of the ProxySG?
A) Go to Configuration > Network
B) This information is not visible from the Management Console
C) The serial number is contained in the Management Console home link at top.
D) Go to Statistics > Advanced
A) Go to Configuration > Network
B) This information is not visible from the Management Console
C) The serial number is contained in the Management Console home link at top.
D) Go to Statistics > Advanced

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
39
In which client connection type are user agents aware that a proxy has been deployed?
A) Explicit proxy
B) In every connection type
C) Inline
D) Transparent
A) Explicit proxy
B) In every connection type
C) Inline
D) Transparent

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
40
Which of the following is NOT a component of a proxy service listener?
A) Source IP address
B) Port range
C) Destination IP address
D) Proxy type
A) Source IP address
B) Port range
C) Destination IP address
D) Proxy type

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
41
What module should an administrator use to view all activities in cloud applications?
A) Protect
B) Audit
C) Detect
D) Investigate
A) Protect
B) Audit
C) Detect
D) Investigate

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
42
What policy should an administrator utilize to allow users access to Office 365, but prevent the extraction of files when their ThreatScore is higher than 30?
A) File transfer
B) Access enforcement
C) ThreatScore based
D) Data exposure
A) File transfer
B) Access enforcement
C) ThreatScore based
D) Data exposure

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
43
What Business Readiness Rating (BRR) category does the subcategory "Password Quality Rules" belong to?
A) Data
B) Compliance
C) Business
D) Access
A) Data
B) Compliance
C) Business
D) Access

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
44
What is the objective of File Sharing policies?
A) To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
B) To prevent users from sharing documents, either publicly, externally, or internally.
C) To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
D) To restrict the uploading and downloading of documents from the user's computer to the cloud application, based both on the content of the documents, and the characteristics of the user.
A) To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
B) To prevent users from sharing documents, either publicly, externally, or internally.
C) To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
D) To restrict the uploading and downloading of documents from the user's computer to the cloud application, based both on the content of the documents, and the characteristics of the user.

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
45
Which are three (3) levels of data exposure?
A) Public, external, and internal
B) Public, confidential, and company confidential
C) Public, semi-private, and private
D) Public, confidential, and private
A) Public, external, and internal
B) Public, confidential, and company confidential
C) Public, semi-private, and private
D) Public, confidential, and private

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
46
What action should an administrator take if a cloud application has significant risks, but mitigating controls are available?
A) Sanction
B) Monitor
C) Block
D) Substitute
A) Sanction
B) Monitor
C) Block
D) Substitute

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
47
What module requires administrative rights to make connections to cloud applications?
A) Securlets
B) Gatelets
C) Audit
D) Investigate
A) Securlets
B) Gatelets
C) Audit
D) Investigate

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
48
What CloudSOC module should an administrator use to identify and remediate malicious behavior within cloud applications?
A) Audit
B) Securlets
C) Detect
D) Investigate
A) Audit
B) Securlets
C) Detect
D) Investigate

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
49
Which detector will trigger if CloudSOC detects anomalously frequent sharing?
A) Behavior based
B) Threshold based
C) Sequence based
D) Threats based
A) Behavior based
B) Threshold based
C) Sequence based
D) Threats based

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
50
What modules are used in the use case "Identify and remediate malicious behavior within cloud applications"?
A) Detect, Protect, and Investigate
B) Detect and Investigate
C) Detect
D) Detect and Securlets
A) Detect, Protect, and Investigate
B) Detect and Investigate
C) Detect
D) Detect and Securlets

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
51
Refer to the exhibit. What modules are used in the use case "Protect information from accidental and intentional exposure within cloud applications"? 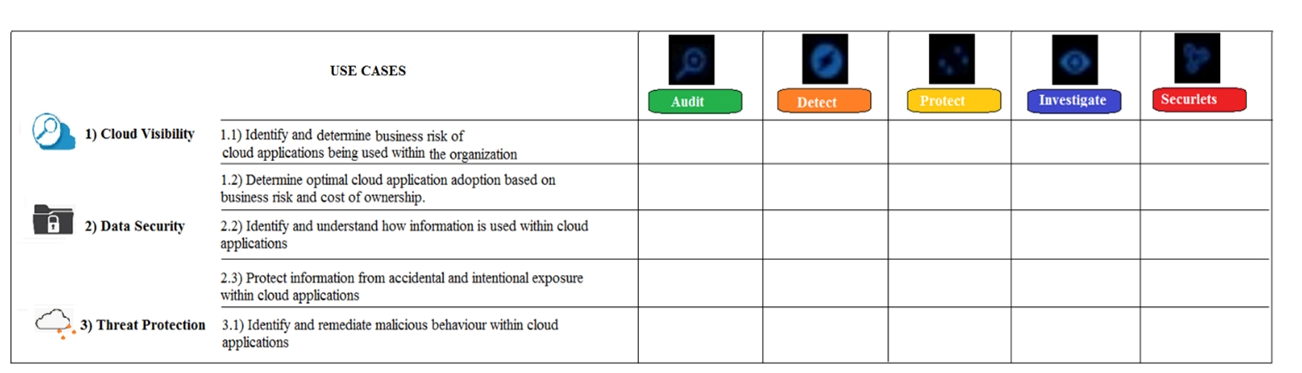
A) Protect and Investigate
B) Protect, Investigate, and Securlets
C) Protect and Audit
D) Protect and Securlets

A) Protect and Investigate
B) Protect, Investigate, and Securlets
C) Protect and Audit
D) Protect and Securlets

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
52
What module should an administrator use to identify anomalous user behavior such as large amounts of data being downloaded, too many files being shared, or logins from suspicious locations?
A) Detect
B) Protect
C) Investigate
D) Audit
A) Detect
B) Protect
C) Investigate
D) Audit

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
53
What type of policy should an administrator use to prevent a user that is behaving in anomalous ways from sharing public links while you monitor them?
A) Access monitoring
B) File transfer
C) Data exposure
D) Access enforcement
A) Access monitoring
B) File transfer
C) Data exposure
D) Access enforcement

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
54
What module should an administrator use to create policies with one click, and send them to the Protect Module?
A) Detect
B) Investigate
C) Audit
D) Securlet
A) Detect
B) Investigate
C) Audit
D) Securlet

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
55
Refer to the exhibit. What action should an administrator take if this incident was found in the Investigate module? 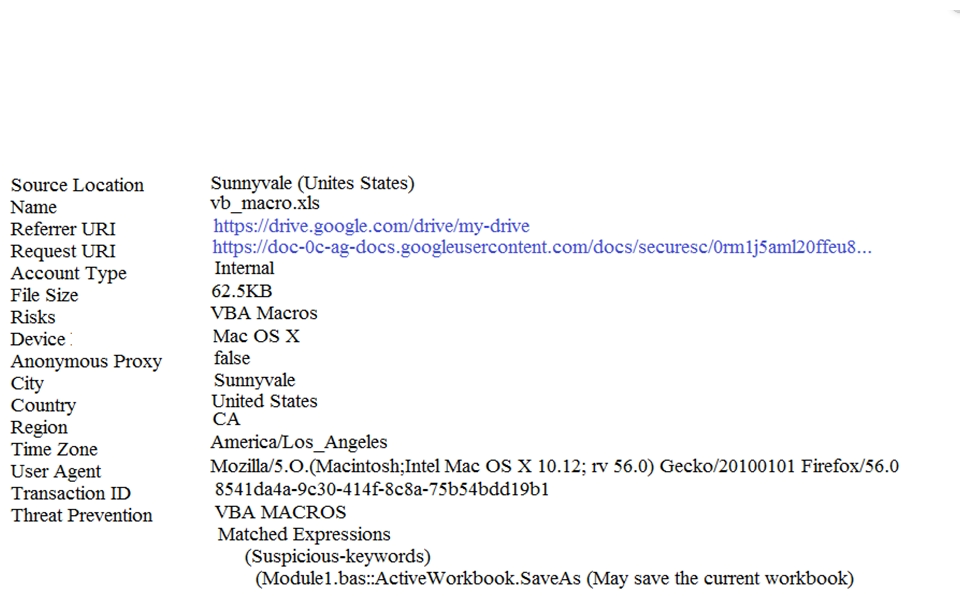
A) Create an access enforcement policy and block access to the file
B) Create a file transfer policy and block the download of the file
C) Create a file sharing policy and block the sharing of the file
D) Create an access monitoring policy and monitor the usage of the file

A) Create an access enforcement policy and block access to the file
B) Create a file transfer policy and block the download of the file
C) Create a file sharing policy and block the sharing of the file
D) Create an access monitoring policy and monitor the usage of the file

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
56
Which type of a policy can perform a user log out from Single Sign On?
A) Access Monitoring policy
B) ThreatScore based policy
C) Access enforcement policy
D) None of the above
A) Access Monitoring policy
B) ThreatScore based policy
C) Access enforcement policy
D) None of the above

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
57
Refer to the exhibit. What does this Access Monitoring policy do? 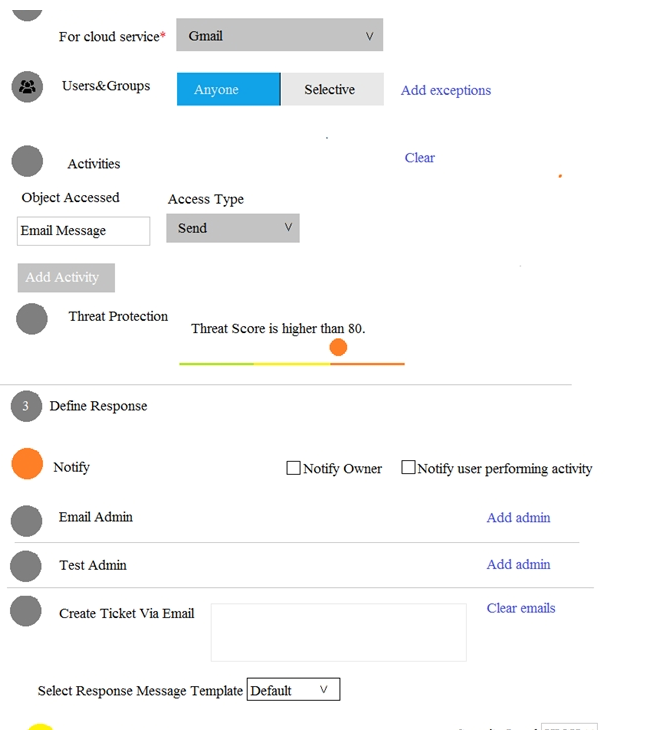
A) Notify the owner when an email is sent
B) Send a ticket when a user with a ThreatScore higher than 80 performs an invalid login
C) Notify the admin when a folder is deleted by a user with a ThreatScore higher than 80
D) Create a ticket when a user with a ThreatScore higher than 80 sends an email

A) Notify the owner when an email is sent
B) Send a ticket when a user with a ThreatScore higher than 80 performs an invalid login
C) Notify the admin when a folder is deleted by a user with a ThreatScore higher than 80
D) Create a ticket when a user with a ThreatScore higher than 80 sends an email

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
58
What compensatory control should an administrator implement if password quality rules of a cloud application has a low rating?
A) Single Sign On (SSO)
B) Block the application
C) Role based access
D) Biometric access
A) Single Sign On (SSO)
B) Block the application
C) Role based access
D) Biometric access

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
59
What type of solution should an administrator implement to secure the way users interact with cloud applications?
A) Intrusion Detection System/Intrusion Protection System (IDS/IPS)
B) Cloud Access Security Broker (CASB)
C) Web application firewalls
D) Proxies
A) Intrusion Detection System/Intrusion Protection System (IDS/IPS)
B) Cloud Access Security Broker (CASB)
C) Web application firewalls
D) Proxies

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
60
What type of policy should an administrator utilize to prevent the spread of malware through cloud applications?
A) Access monitoring
B) File transfer
C) File sharing
D) Access enforcement
A) Access monitoring
B) File transfer
C) File sharing
D) Access enforcement

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
61
What is the objective of the Access Monitoring policy?
A) To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
B) To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
C) To prevent users from sharing documents, either publically, externally, or internally.
D) To restrict the uploading and downloading of documents from the user's computer to the cloud application, based both on the content of the documents and the characteristics of the user.
A) To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
B) To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
C) To prevent users from sharing documents, either publically, externally, or internally.
D) To restrict the uploading and downloading of documents from the user's computer to the cloud application, based both on the content of the documents and the characteristics of the user.

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
62
Where should an administrator locate the level of exposure in files in the Securlet module?
A) Exposure level
B) Exposed files
C) Exposed content
D) Exposure summary
A) Exposure level
B) Exposed files
C) Exposed content
D) Exposure summary

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
63
What are the four (4) types of detectors?
A) Threshold based, download/upload based, threats based, and sequence based
B) Threshold based, behavior based, and sequence based
C) Threshold based, behavior based, download/upload based, and access control based
D) Threshold based, behavior based, malware based, and sequence based
A) Threshold based, download/upload based, threats based, and sequence based
B) Threshold based, behavior based, and sequence based
C) Threshold based, behavior based, download/upload based, and access control based
D) Threshold based, behavior based, malware based, and sequence based

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
64
How should an administrator handle a cloud application that fails to meet compliance requirements, but the business need outweighs the risk?
A) Sanction
B) Monitor
C) Block
D) Review
A) Sanction
B) Monitor
C) Block
D) Review

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
65
Which CloudSOC module is similar to a Data Loss Prevention (DLP) system?
A) Detect
B) Investigate
C) Audit
D) Protect
A) Detect
B) Investigate
C) Audit
D) Protect

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
66
What variable increases when a detector is triggered by a suspicious behavior?
A) Risk Rating
B) Business Readiness Rating (BRR)
C) Incident Index
D) ThreatScore
A) Risk Rating
B) Business Readiness Rating (BRR)
C) Incident Index
D) ThreatScore

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
67
Which CloudSOC module(s) use cloud application APIs as data sources?
A) Detect, Protect, Investigate, and Securlets
B) Audit
C) Detect, Protect, and Investigate
D) Investigate and Securlets
A) Detect, Protect, Investigate, and Securlets
B) Audit
C) Detect, Protect, and Investigate
D) Investigate and Securlets

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
68
What are three (3) main risks that CloudSOC solves in cloud applications?
A) Phishing, Data Security, Threat Protection
B) Cloud Visibility, Data Security, Threat Protection
C) Cloud Visibility, Data Security, Web Scanning
D) Phishing, Cloud Visibility, Threat Protection
A) Phishing, Data Security, Threat Protection
B) Cloud Visibility, Data Security, Threat Protection
C) Cloud Visibility, Data Security, Web Scanning
D) Phishing, Cloud Visibility, Threat Protection

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
69
Refer to the exhibit. An administrator found this incident in the Investigate module. What type of policy should an administrator create to get email notifications if the incident happens again? 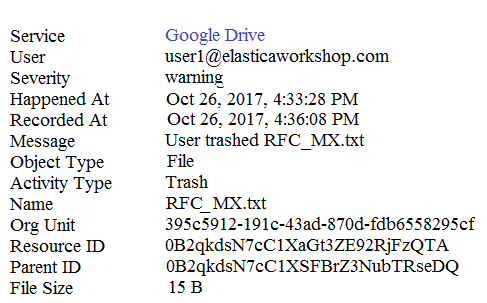
A) File sharing policy
B) File transfer policy
C) Access monitoring policy
D) Data exposure policy

A) File sharing policy
B) File transfer policy
C) Access monitoring policy
D) Data exposure policy

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
70
What Business Readiness Rating (BRR) category does the subcategory "HTTP Security Headers" belong to?
A) Informational
B) Service
C) Administrative
D) Data
A) Informational
B) Service
C) Administrative
D) Data

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
71
What module should an administrator utilize to view all the activities in cloud applications and conduct analysis?
A) Audit
B) Detect
C) Protect
D) Investigate
A) Audit
B) Detect
C) Protect
D) Investigate

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
72
What CloudSOC module should an administrator use to identify and understand how information is used within cloud applications?
A) Investigate
B) Securlets
C) Audit
D) Detect
A) Investigate
B) Securlets
C) Audit
D) Detect

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
73
Which CloudSOC module is similar to an Intrusion Protection System (IPS)/Intrusion Detection System (IDS)?
A) Protect
B) Investigate
C) Detect
D) Audit
A) Protect
B) Investigate
C) Detect
D) Audit

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
74
What should an administrator utilize to steer traffic from client devices to the CloudSOC gateway?
A) SpanVA
B) ProxySG
C) The Reach agent
D) SCP/SFTP
A) SpanVA
B) ProxySG
C) The Reach agent
D) SCP/SFTP

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
75
What Business Readiness Rating (BRR) category does the subcategory "User Audit Trail" belong to?
A) Data
B) Informational
C) Administrative
D) Business
A) Data
B) Informational
C) Administrative
D) Business

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
76
What Rule Type in ContentIQ profiles do business, computing, encryption, engineering, health, and legal belong to?
A) Content types
B) Custom dictionaries
C) Keywords
D) Risk types
A) Content types
B) Custom dictionaries
C) Keywords
D) Risk types

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
77
What categories should an administrator utilize to classify cloud applications during the cloud applications adoption workflow?
A) Accept, Reject, Block
B) Accept, Monitor, Block
C) Valid, Invalid, In Process
D) Sanction, Monitor, Block
A) Accept, Reject, Block
B) Accept, Monitor, Block
C) Valid, Invalid, In Process
D) Sanction, Monitor, Block

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
78
What should an administrator use to identify document types specified by the user?
A) Custom dictionaries
B) Training profiles
C) Risk types
D) Content types
A) Custom dictionaries
B) Training profiles
C) Risk types
D) Content types

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
79
Refer to the exhibit. Which CloudSOC module(s) use firewalls and proxies as data sources? 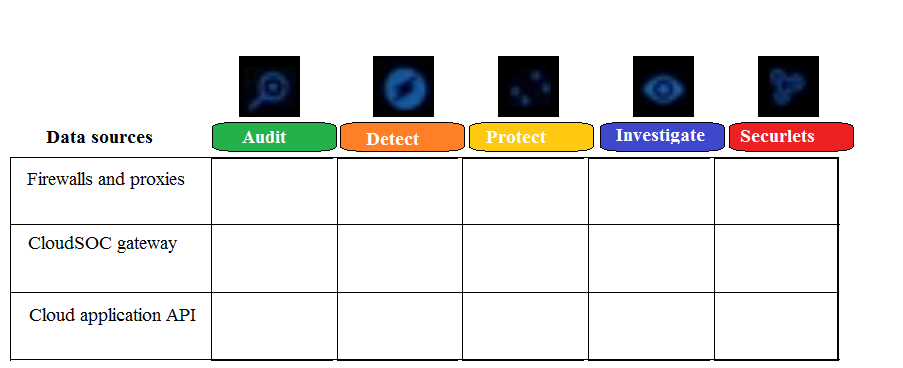
A) Detect, Protect, and Investigate
B) Detect, Protect, Investigate, and Securlets
C) Audit and Investigate
D) Audit

A) Detect, Protect, and Investigate
B) Detect, Protect, Investigate, and Securlets
C) Audit and Investigate
D) Audit

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck
80
What is the objective of the Access Enforcement policy?
A) To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
B) To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
C) To restrict the uploading and downloading of documents from the user's computer to the cloud application, based both on the content of the documents, and the characteristics of the user.
D) To restrict user access to cloud applications not based on content, but based on the user's characteristics, such as devices and locations.
A) To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
B) To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
C) To restrict the uploading and downloading of documents from the user's computer to the cloud application, based both on the content of the documents, and the characteristics of the user.
D) To restrict user access to cloud applications not based on content, but based on the user's characteristics, such as devices and locations.

Unlock Deck
Unlock for access to all 98 flashcards in this deck.
Unlock Deck
k this deck



