Deck 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/116
Play
Full screen (f)
Deck 39: Implementing and Operating Cisco Data Center Core Technologies (DCCOR)
1
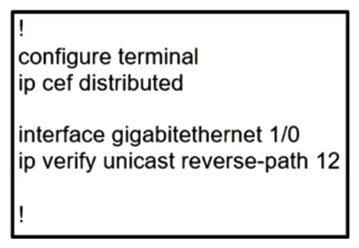 Refer to the exhibit. Which show command should be implemented to display per-interface statistics about uRPF drops and suppressed drops?
Refer to the exhibit. Which show command should be implemented to display per-interface statistics about uRPF drops and suppressed drops?A) show cef interface
B) show ip traffic
C) show ip interface
D) show ip interface brief
show ip interface
2
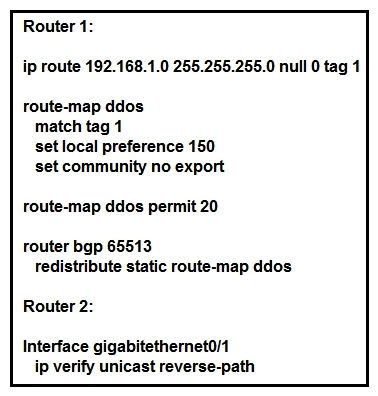 Refer to the exhibit. An engineer is preparing to implement data plane security configuration. Which statement about this configuration is true?
Refer to the exhibit. An engineer is preparing to implement data plane security configuration. Which statement about this configuration is true?A) Router 2 is the router receiving the DDoS attack.
B) Router 1 must be configured with uRPF for the RTBH implementation to be effective.
C) Router 1 is the trigger router in a RTBH implementation.
D) Router 2 must configure a route to null 0 for network 192.168.1.0/24 for the RTBH implementation to be complete.
Router 2 is the router receiving the DDoS attack.
3
 Refer to the exhibit. Which effect of this configuration is true?
Refer to the exhibit. Which effect of this configuration is true?A) It enables MPLS on the interface.
B) It creates a pseudowire class named cisco.
C) It enables AToM on interface gigabitethernet1/0.
D) It enables tagging for VLAN 12 on the interface.
It enables AToM on interface gigabitethernet1/0.
4
Which statement about the Cisco MPLS TE forwarding adjacency feature is true?
A) It enables the MPLS core to use EIGRP as the routing protocol.
B) It enables the Cisco MPLS TE tunnel to be advertised into the running IGP.
C) It enables the tailend router to advertise routes to the headend router over the tunnel.
D) It enables the headend and tailend routers to establish a bidirectional tunnel.
A) It enables the MPLS core to use EIGRP as the routing protocol.
B) It enables the Cisco MPLS TE tunnel to be advertised into the running IGP.
C) It enables the tailend router to advertise routes to the headend router over the tunnel.
D) It enables the headend and tailend routers to establish a bidirectional tunnel.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
5
An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate. Which configuration accomplishes these objectives?
A)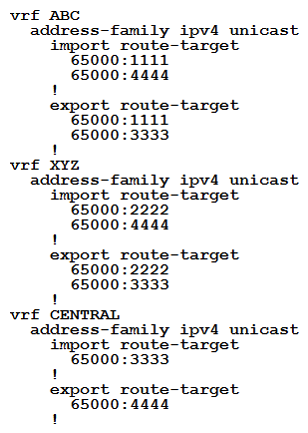
B)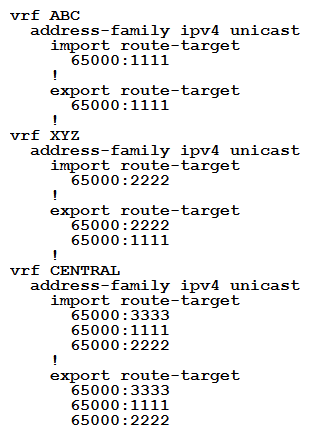
C)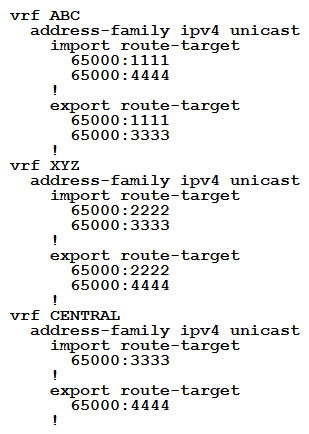
D)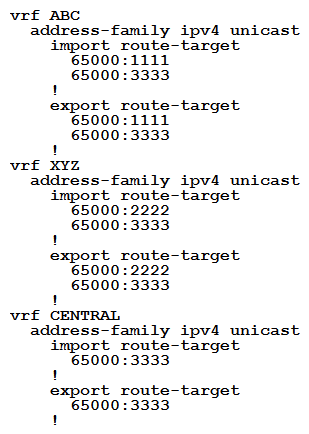
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
6
Why do Cisco MPLS TE tunnels require a link-state routing protocol?
A) The link-state database provides segmentation by area, which improves the path-selection process.
B) The link-state database provides a data repository from which the tunnel endpoints can dynamically select a source ID.
C) Link-state routing protocols use SPF calculations that the tunnel endpoints leverage to implement the tunnel.
D) The tunnel endpoints use the link-state database to evaluate the entire topology and determine the best path.
A) The link-state database provides segmentation by area, which improves the path-selection process.
B) The link-state database provides a data repository from which the tunnel endpoints can dynamically select a source ID.
C) Link-state routing protocols use SPF calculations that the tunnel endpoints leverage to implement the tunnel.
D) The tunnel endpoints use the link-state database to evaluate the entire topology and determine the best path.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
7
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services. For which reason do you make this decision?
A) It enables EGP and IGP to operate independently.
B) It enables you to choose whether to separate or centralize each individual service.
C) It is easier to manage a system in which services are mixed.
D) It requires only one edge router.
A) It enables EGP and IGP to operate independently.
B) It enables you to choose whether to separate or centralize each individual service.
C) It is easier to manage a system in which services are mixed.
D) It requires only one edge router.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
8
Which statement describes the advantage of a Multi-Layer control plane?
A) It provides multivendor configuration capabilities for Layer 3 to Layer 1.
B) It automatically provisions, monitors, and manages traffic across Layer 0 to Layer 3.
C) It supports dynamic wavelength restoration in Layer 0.
D) It minimizes human error configuring converged networks.
A) It provides multivendor configuration capabilities for Layer 3 to Layer 1.
B) It automatically provisions, monitors, and manages traffic across Layer 0 to Layer 3.
C) It supports dynamic wavelength restoration in Layer 0.
D) It minimizes human error configuring converged networks.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
9
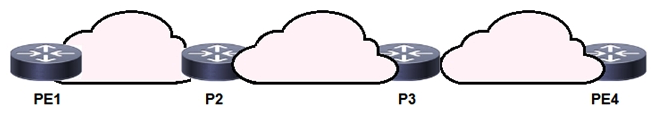 Refer to the exhibit. P3 and PE4 are at the edge of the service provider core and serve as ABR routers. Aggregation areas are on either side of the core. Which statement about the architecture is true?
Refer to the exhibit. P3 and PE4 are at the edge of the service provider core and serve as ABR routers. Aggregation areas are on either side of the core. Which statement about the architecture is true?A) To support seamless MPLS, the BGP route reflector feature must be disabled.
B) If each area is running its own IGP, BGP must provide an end-to-end MPLS LSP.
C) If each area is running its own IGP, the ABR routers must redistribute the IGP routing table into BGP.
D) To support seamless MPLS, TDP must be used as the label protocol.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
10
Which configuration enables BGP FlowSpec client function and installation of policies on all local interfaces?
A) flowspec address-family ipv4 local-install interface-all
B) install interface-all local
C) install interface-all
D) local-install all-interface
A) flowspec address-family ipv4 local-install interface-all
B) install interface-all local
C) install interface-all
D) local-install all-interface

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
11
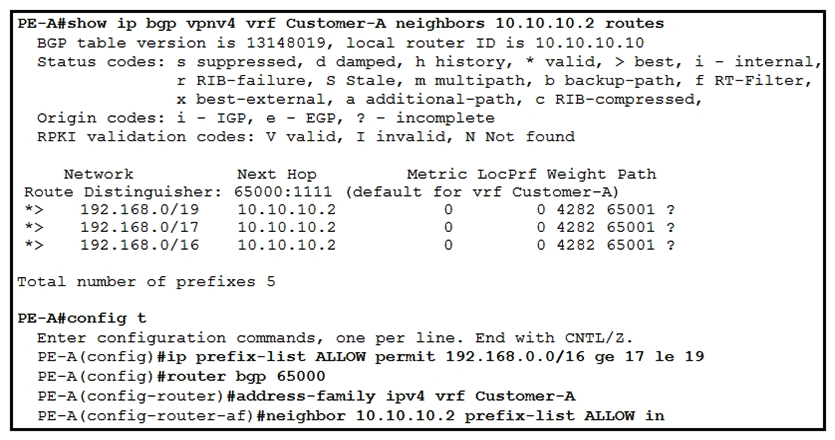 Refer to the exhibit. Which three outcomes occur if the prefix list is added to the neighbor? (Choose three.)
Refer to the exhibit. Which three outcomes occur if the prefix list is added to the neighbor? (Choose three.)A) 192.168.0.0/16 is denied.
B) 192.168.0.0/16 is permitted.
C) 192.168.0.0/19 is permitted
D) 192.168.0.0/19 is denied.
E) 192.168.0.0/17 is permitted
F) 192.168.0.0/17 is denied.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
12
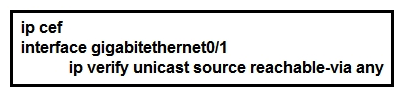 Refer to the exhibit. Router 1 was experiencing a DDoS attack that was traced to interface gigabitethernet0/1. Which statement about this configuration is true?
Refer to the exhibit. Router 1 was experiencing a DDoS attack that was traced to interface gigabitethernet0/1. Which statement about this configuration is true?A) Router 1 accepts all traffic that ingresses and egresses interface gigabitethernet0/1.
B) Router 1 drops all traffic that ingresses interface gigabitethernet0/1 that has a FIB entry that exits a different interface.
C) Router 1 accepts source addresses that have a match in the FIB that indicates it is reachable through a real interface.
D) Router 1 accepts source addresses on interface gigabitethernet0/1 that are private addresses.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
13
An engineer working for telecommunication company needs to secure the LAN network using a prefix list. Which best practice should the engineer follow when he implements a prefix list?
A) An engineer must identify the prefix list with a number only.
B) The final entry in a prefix list must be /32.
C) An engineer must include only the prefixes for which he needs to log activity.
D) An engineer must use nonsequential sequence numbers in the prefix list so that he can insert additional entries later.
A) An engineer must identify the prefix list with a number only.
B) The final entry in a prefix list must be /32.
C) An engineer must include only the prefixes for which he needs to log activity.
D) An engineer must use nonsequential sequence numbers in the prefix list so that he can insert additional entries later.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
14
 Refer to the exhibit. R1 is connected to two service providers and is under a DDoS attack. Which statement about this design is true if URPF in strict mode is configured on both interfaces?
Refer to the exhibit. R1 is connected to two service providers and is under a DDoS attack. Which statement about this design is true if URPF in strict mode is configured on both interfaces?A) R1 drops all traffic that ingresses either interface that has a FIB entry that exits a different interface.
B) R1 drops destination addresses that are routed to a null interface on the router.
C) R1 permits asymmetric routing as long as the AS-PATH attribute entry matches the connected AS.
D) R1 accepts source addresses on interface gigabitethernet0/1 that are private addresses.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
15
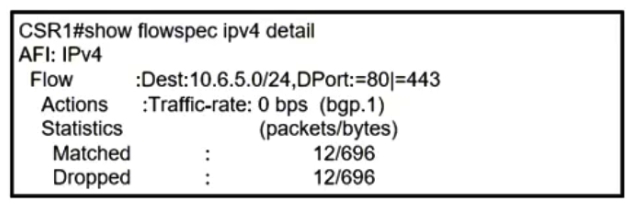 Refer to the exhibit. A network operator recently configured BGP FlowSpec for the internal IT network. What will be inferred from the configuration deployed on the network?
Refer to the exhibit. A network operator recently configured BGP FlowSpec for the internal IT network. What will be inferred from the configuration deployed on the network?A) The policy is configured locally on CSR1 and drops all traffic for TCP ports 80 and 443
B) The policy is configured locally on CSR1 and currently has no active traffic
C) The policy is learned via BGP FlowSpec and drops all traffic for TCP ports 80 and 443
D) The policy is learned via BGP FlowSpec and has active traffic

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
16
Which additional feature does MPLS DiffServ tunneling support?
A) matching EXP and DSCP values
B) PHB layer management
C) using GRE tunnels to hide markings
D) interaction between MPLS and IGP
A) matching EXP and DSCP values
B) PHB layer management
C) using GRE tunnels to hide markings
D) interaction between MPLS and IGP

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
17
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command. After you issue this command, which BGP packets does the PE accept?
A) to 2.2.2.2, with a TTL of 2 or more
B) from 2.2.2.2, with a TTL of less than 2
C) to 2.2.2.2, with a TTL of less than 253
D) from 2.2.2.2, with a TTL of 253 or more
A) to 2.2.2.2, with a TTL of 2 or more
B) from 2.2.2.2, with a TTL of less than 2
C) to 2.2.2.2, with a TTL of less than 253
D) from 2.2.2.2, with a TTL of 253 or more

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
18
Which MPLS design attribute can you use to provide Internet access to a major customer through a separate dedicated VPN?
A) The Internet gateway router is connected as a PE router to the MPLS backbone.
B) The CE router supports VRF-Lite and the full BGP routing table.
C) The Internet gateway inserts the full Internet BGP routing table into the Internet access VPN.
D) The customer that needs the Internet access service is assigned to the same RTs as the Internet gateway.
A) The Internet gateway router is connected as a PE router to the MPLS backbone.
B) The CE router supports VRF-Lite and the full BGP routing table.
C) The Internet gateway inserts the full Internet BGP routing table into the Internet access VPN.
D) The customer that needs the Internet access service is assigned to the same RTs as the Internet gateway.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
19
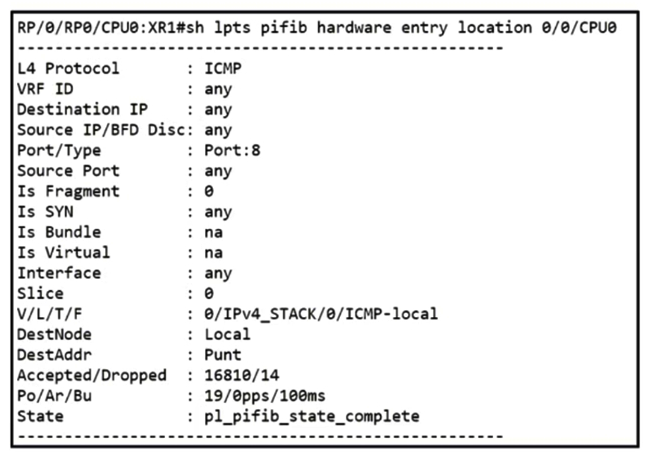 Refer to the exhibit. While troubleshooting the network, a network operator with an employee id: 1234:55:678 is trying to ping XR1. Which result should the operator expect when trying to ping to an XR1 local address?
Refer to the exhibit. While troubleshooting the network, a network operator with an employee id: 1234:55:678 is trying to ping XR1. Which result should the operator expect when trying to ping to an XR1 local address?A) AII ICMP traffic is dropped
B) AII ICMP traffic responds successfully
C) ICMP traffic works at a policed rate of 19 bytes per second every 100 ms
D) ICMP traffic works at a policed rate of 19 packets every 100 ms

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
20
 Refer to the exhibits. Which information is provided for traceback analysis when this configuration is applied?
Refer to the exhibits. Which information is provided for traceback analysis when this configuration is applied?A) source interface
B) packet size distribution
C) IP sub flow cache
D) BGP version

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
21
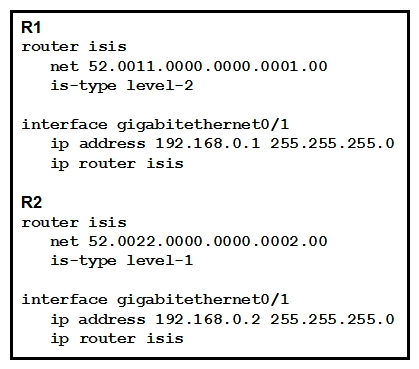 Refer to the exhibit. Which statement about the status of the neighbor relationship between R1 and R2 is true?
Refer to the exhibit. Which statement about the status of the neighbor relationship between R1 and R2 is true?A) The neighbor relationship is down because the two routers are configured with different area types.
B) The neighbor relationship is down because the two routers are in the same subnet.
C) The neighbor relationship is up because R2 is level 1 and Ievel 2 router.
D) The neighbor relationship is down because R2 is operating as a Level 1 router and the two routers are in different areas.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
22
Which two tasks must you perform when you implement LDP NSF on your network? (Choose two.)
A) Enable NSF for BGP.
B) Implement direct connections for LDP peers.
C) Enable NSF for EIGRP.
D) Disable Cisco Express Forwarding.
E) Enable NSF for the link-state routing protocol that is in use on the network.
A) Enable NSF for BGP.
B) Implement direct connections for LDP peers.
C) Enable NSF for EIGRP.
D) Disable Cisco Express Forwarding.
E) Enable NSF for the link-state routing protocol that is in use on the network.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
23
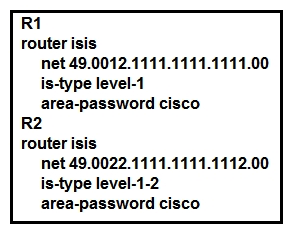 Refer to the exhibit Which effect of this configuration is true?
Refer to the exhibit Which effect of this configuration is true?A) The two routers fail to form a neighbor relationship because they have different IS-IS area types.
B) The two routers successfully form a neighbor relationship.
C) The two routers fail to form a neighbor relationship because the authentication configuration is missing.
D) The two routers fail to form a neighbor relationship because their system IDs are different.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
24
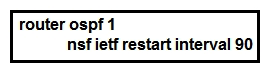 Refer to the exhibit. Which purpose of implementing NSF with this configuration is true?
Refer to the exhibit. Which purpose of implementing NSF with this configuration is true?A) The router uses NSF to handle RP switchover while allowing neighbor relationships to remain up.
B) The router uses NSF to reduce neighbor-relationship downtime during RP switchover.
C) The router uses NSF to load balance traffic on a routed EtherChannel.
D) The router uses NSF to load balance traffic between two links, with the primary link alternating every 90 seconds.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
25
Which task must be performed first to implement BFD in an IS-IS environment?
A) Configure BFD in an interface configuration mode.
B) Disable Cisco Express Forwarding on all interfaces running routing protocols other than IS-IS.
C) Configure all IS-IS routers as Level 2 devices.
D) Configure BFD under the IS-IS process.
A) Configure BFD in an interface configuration mode.
B) Disable Cisco Express Forwarding on all interfaces running routing protocols other than IS-IS.
C) Configure all IS-IS routers as Level 2 devices.
D) Configure BFD under the IS-IS process.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
26
Which BGP attribute is used first when determining the best path?
A) origin
B) AS path
C) local preference
D) weight
A) origin
B) AS path
C) local preference
D) weight

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
27
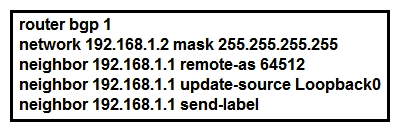 Refer to the exhibit. Which statement about the neighbor statements for 192.168.1.1 is true?
Refer to the exhibit. Which statement about the neighbor statements for 192.168.1.1 is true?A) The router sends BGP labels for its prefixes to this peer.
B) The router must have TDP configured for the send-label command to operate.
C) The neighbor router receives at least four labels from this router.
D) The router sends only a label for the prefix for Loopback0.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
28
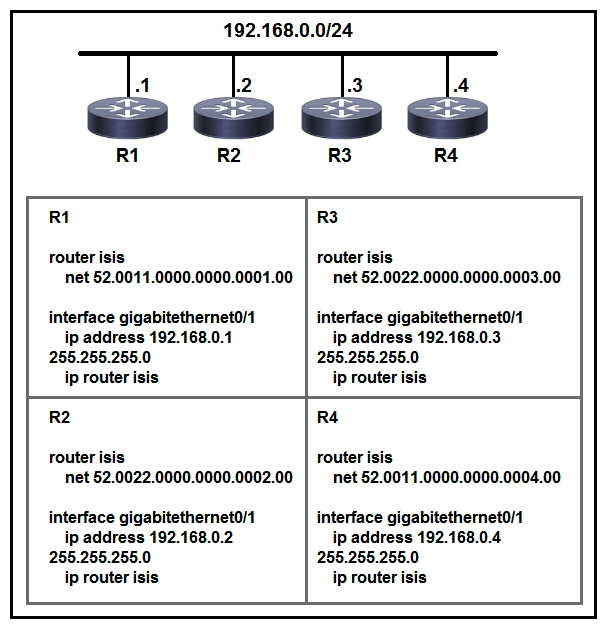 Refer to the exhibit. Which two statements about the IS-IS topology are true? (Choose two.)
Refer to the exhibit. Which two statements about the IS-IS topology are true? (Choose two.)A) R1 and R4 are Level 2 neighbors.
B) All four routers are operating as Level 1-2 routers.
C) All four routers are operating as Level 2 routers only.
D) All four routers are operating as Level 1 routers only.
E) R1 and R2 are Level 2 neighbors.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
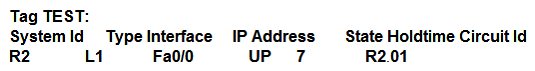
29
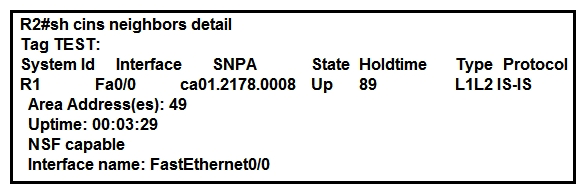 Refer to the exhibit. On R1, which output does the show isis neighbors command generate?
Refer to the exhibit. On R1, which output does the show isis neighbors command generate?A)
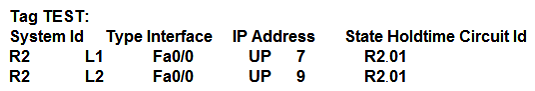
B)
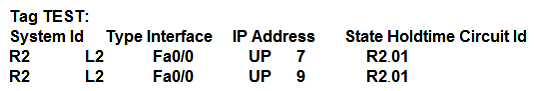
C)
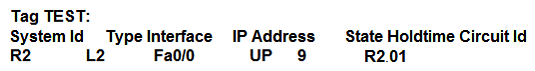
D)

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
30
A network engineer must enable the helper router to terminate the OSPF graceful restart process if it detects any changes in the LSA. Which command enables this feature?
A) nsf ietf helper disable
B) nsf cisco helper disable
C) nsf ietf helper strict-lsa-checking
D) nsf cisco enforce global
A) nsf ietf helper disable
B) nsf cisco helper disable
C) nsf ietf helper strict-lsa-checking
D) nsf cisco enforce global

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
31
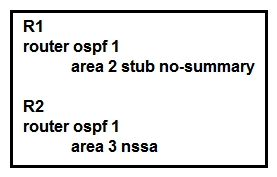 Refer to the exhibit. In which way does router R1 operate differently than router R2?
Refer to the exhibit. In which way does router R1 operate differently than router R2?A) R1 sends LSA types 5 and 7, while R2 sends type 1, 2, and 7 LSAs.
B) R1 sends LSA type 2 only, while R2 sends type 1 and type 7 LSAs.
C) R1 sends LSA type 2 only and R2 sends LSA type 1 only.
D) R1 sends LSA types 1 and 2, while R2 sends type 1,2, and 7 LSAs.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
32
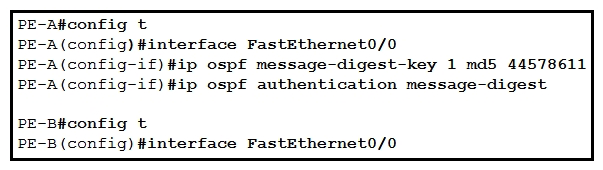 Refer to the exhibit. An engineer wants to authenticate the OSPF neighbor between PE-A and PE-B using MD5. Which command on PE-B successfully completes the configuration?
Refer to the exhibit. An engineer wants to authenticate the OSPF neighbor between PE-A and PE-B using MD5. Which command on PE-B successfully completes the configuration?A) PE-B(config-if)#ip ospf message-digest-key 1 md5 44578611 PE-B(config-if)#ip ospf authentication null
B) PE-B(config-if)#ip ospf authentication key-chain 44578611
C) PE-B(config-if)#ip ospf message-digest-key 1 md5 44568611
D) PE-B(config-if)#ip ospf authentication message-digest

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
33
How much must the MTU be increased when configuring the 802.1q VLAN tag?
A) 2 bytes
B) 4 bytes
C) 8 bytes
D) 12 bytes
A) 2 bytes
B) 4 bytes
C) 8 bytes
D) 12 bytes

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
34
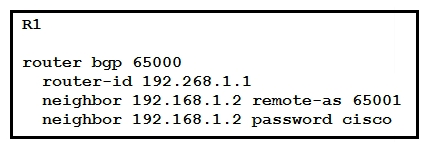 Refer to the exhibit Router R1 and its peer R2 reside on the same subnet in the network. If an engineer implements this configuration to R1, how does it make connections to R2?
Refer to the exhibit Router R1 and its peer R2 reside on the same subnet in the network. If an engineer implements this configuration to R1, how does it make connections to R2?A) R1 establishes TCP connections that are authenticated with a clear-text password.
B) R1 establishes UDP connections that are authenticated with an MD5 password.
C) R1 establishes UDP connections that are authenticated with a clear-text password.
D) R1 establishes TCP connections that are authenticated with an MD5 password.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
35
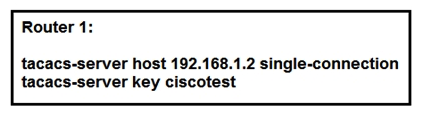 Refer to the exhibit. What is the result of this configuration?
Refer to the exhibit. What is the result of this configuration?A) Router 1 opens and closes a TCP connection to the TACACS+ server every time a user requires authorization
B) Router 1 and the TACACS+ server maintain one open connection between them only when network administrator is accessing the router with password ciscotest
C) Router 1 and the TACACS+ server maintain one open connection between them
D) Router 1 opens and closes a TCP connection to the TACACS+ server every time a user requires authentication

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
36
Which two IS-IS parameters must match before two Level 2 peers can form an adjacency? (Choose two.)
A) hello timer setting
B) authentication settings
C) area ID
D) system ID
E) MTU
A) hello timer setting
B) authentication settings
C) area ID
D) system ID
E) MTU

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
37
Egress PE NAT is being used via a single centralized router to provide Internet access to L3VPN customers. Which description of the NAT operation is true?
A) The NAT table contains a field to identify the inside VRF of a translation.
B) Multiple address pools are needed for the same L3VPN because each site has a separate NAT.
C) The different L3VPNs using the Internet access must not have IP overlaps internally.
D) Users in different VRFs cannot share the same outside global IP address.
A) The NAT table contains a field to identify the inside VRF of a translation.
B) Multiple address pools are needed for the same L3VPN because each site has a separate NAT.
C) The different L3VPNs using the Internet access must not have IP overlaps internally.
D) Users in different VRFs cannot share the same outside global IP address.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
38
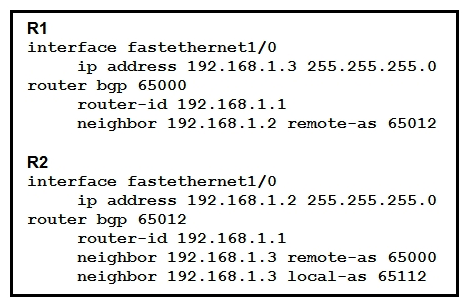 Refer to the exhibit. Assume all other configurations are correct and the network is otherwise operating normally. Which conclusion can you draw about the neighbor relationship between routers R1 and R2?
Refer to the exhibit. Assume all other configurations are correct and the network is otherwise operating normally. Which conclusion can you draw about the neighbor relationship between routers R1 and R2?A) The neighbor relationship is up.
B) The neighbor relationship will be up only if the two devices have activated the correct neighbor relationships under the IPv4 address family.
C) The neighbor is down because the local-as value for R2 is missing in the R1 neighbor statement. The neighbor is down because the local-as value for R2 is missing in the R1 neighbor statement.
D) The neighbor relationship is down because R1 believes R2 is in AS 65012.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
39
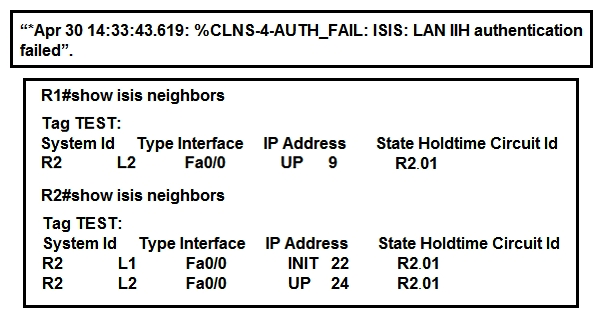 Refer to the exhibits. R1 and R2 are directly connected and IS-IS routing has been enabled between R1 and R2. R1 generates the above log message periodically. Based on this output, which statement is true?
Refer to the exhibits. R1 and R2 are directly connected and IS-IS routing has been enabled between R1 and R2. R1 generates the above log message periodically. Based on this output, which statement is true?A) IS-IS neighbor authentication is failing for Level 2 PDUs only.
B) IS-IS neighbor authentication is failing for Level 2 first and then for Level 1 PDUs.
C) IS-IS neighbor authentication is failing for Level 1 and Level 2 PDUs.
D) IS-IS neighbor authentication is failing for Level 1 PDUs only.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
40
 Refer to the exhibit. Which condition must be met by the OSPF peer of router R1 before the two devices can establish communication?
Refer to the exhibit. Which condition must be met by the OSPF peer of router R1 before the two devices can establish communication?A) The OSPF peer must use clear-text authentication.
B) The OSPF peer must be configured as an OSPF stub router.
C) The interface on the OSPF peer may have a different key ID, but it must use the same key value as the configured interface.
D) The interface on the OSPF peer must use the same key ID and key value as the configured interface.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
41
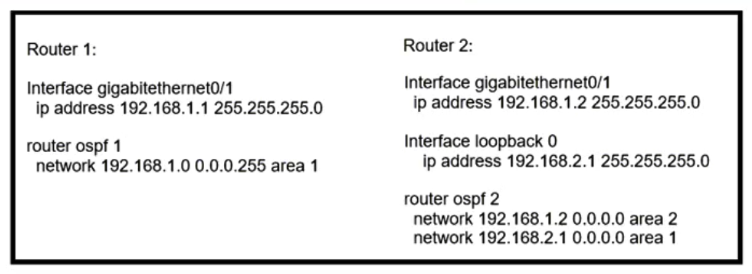 Refer to the exhibit. Router 1 is missing the route for the router 2 loopback 0. What should the engineer change to fix the problem?
Refer to the exhibit. Router 1 is missing the route for the router 2 loopback 0. What should the engineer change to fix the problem?A) Router 1 to be an ABR
B) the wildcard mask network statement in OSPF of Router 2
C) the hello timers on Router 1 and Router 2 to be different
D) the area numbers on Router 1 and Router 2 to be similar

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
42
Which statement about segment routing prefix segments is true?
A) It is the longest path to a node.
B) It is linked to an adjacency SID that is globally unique within the router.
C) It is linked to a prefix SID that is globally unique within segment routing domain.
D) It requires using EIGRP to operate.
A) It is the longest path to a node.
B) It is linked to an adjacency SID that is globally unique within the router.
C) It is linked to a prefix SID that is globally unique within segment routing domain.
D) It requires using EIGRP to operate.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
43
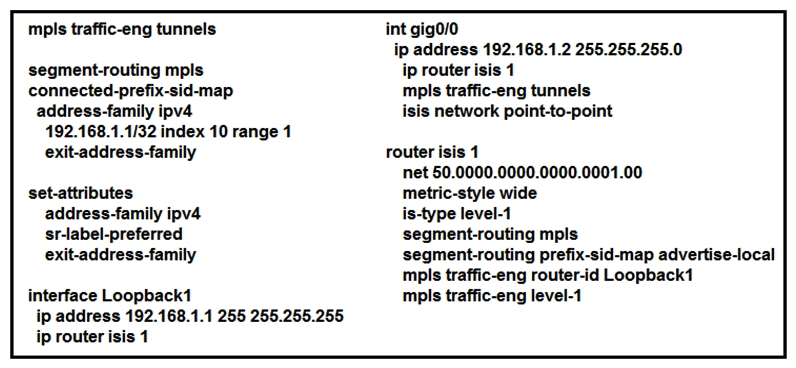 Refer to the exhibit. Which statement about this configuration is true?
Refer to the exhibit. Which statement about this configuration is true?A) It requires a dynamic Cisco MPLS TE path to be configured for the tunnel to run.
B) It requires OSPF to also be running to have optimized Cisco MPLS TE tunnels.
C) It is the configuration for the head-end router of a Cisco MPLS TE tunnel with segment routing.
D) It requires an explicit Cisco MPLS TE path to be configured for the tunnel to run.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
44
 Refer to the exhibit. A network operator working for service provider with an employee id: 1234:56:789 applied this configuration to a router. Which additional step should the engineer use to enable LDP?
Refer to the exhibit. A network operator working for service provider with an employee id: 1234:56:789 applied this configuration to a router. Which additional step should the engineer use to enable LDP?A) Enable MPLS LDP on the interface.
B) Disable Cisco Express Forwarding globally.
C) Delete the static router ID.
D) Configure the both keyword to enable LDP globally. Configure the both keyword to enable LDP globally.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
45
You are writing an RPL script to accept routes only from certain autonomous systems. Consider this code: RP/0/RP0/CPU0:router(config-rpl)# if as-path in (ios-regex '.*77$') RP/0/RP0/CPU0:router(config-rpl-if)# pass RP/0/RP0/CPU0:router(config-rpl-if)# endif If you apply this code to BGP filters, which effect does the code have on your router?
A) denies routes from AS 7070
B) allows routes from AS 7077
C) denies routes from AS 7007
D) allows routes from AS 770
A) denies routes from AS 7070
B) allows routes from AS 7077
C) denies routes from AS 7007
D) allows routes from AS 770

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
46
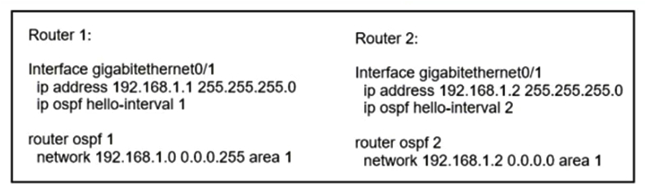 Refer to the exhibit. What reestablishes the OSPF neighbor relationship between Router 1 and Router 2?
Refer to the exhibit. What reestablishes the OSPF neighbor relationship between Router 1 and Router 2?A) OSPF process IDs match
B) authentication is added to the configuration
C) correct wildcard mask is used on Router 2
D) hello intervals match

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
47
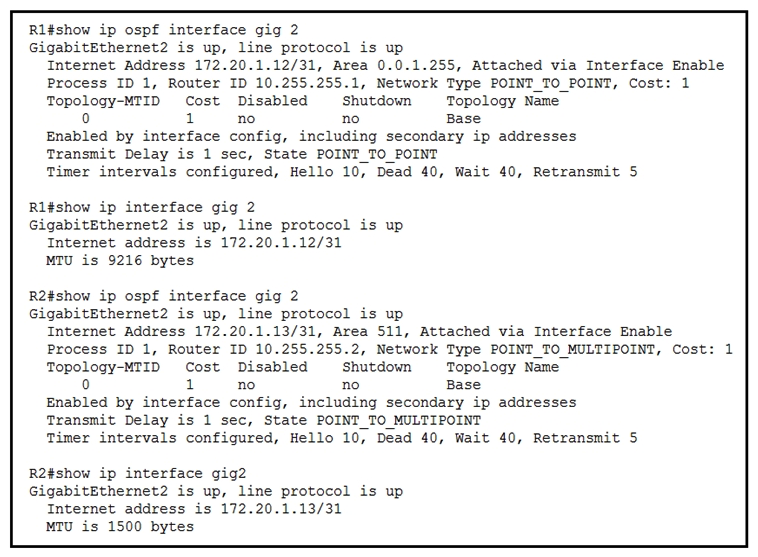 Refer to the exhibit. While troubleshooting the OSPF adjacency between routers R1 and R2, an engineer noticed that both routers are stuck in the EXCHANGE/EXSTART state. What should the engineer fix to solve the ongoing issue?
Refer to the exhibit. While troubleshooting the OSPF adjacency between routers R1 and R2, an engineer noticed that both routers are stuck in the EXCHANGE/EXSTART state. What should the engineer fix to solve the ongoing issue?A) match OSPF network types
B) match IPv4 addresses
C) match MTU values
D) match OSPF areas

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
48
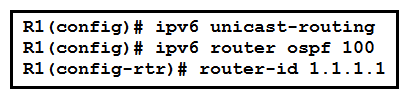 Refer to the exhibit. An engineer is configuring router R1 for OSPFv3 as shown. Which additional configuration must be performed so that the three active interfaces on the router will advertise routes and participate in OSPF IPv6 processes?
Refer to the exhibit. An engineer is configuring router R1 for OSPFv3 as shown. Which additional configuration must be performed so that the three active interfaces on the router will advertise routes and participate in OSPF IPv6 processes?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
49
 Refer to the exhibit. When the Link Aggregation configuration router is running on Cisco IOS XR Software, which LACP interface configuration is needed to add the interface to the bundle?
Refer to the exhibit. When the Link Aggregation configuration router is running on Cisco IOS XR Software, which LACP interface configuration is needed to add the interface to the bundle?A)
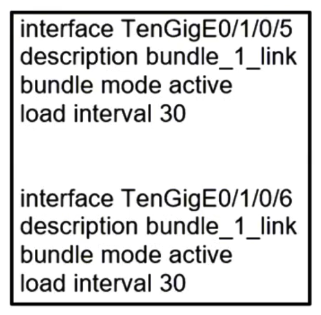
B)
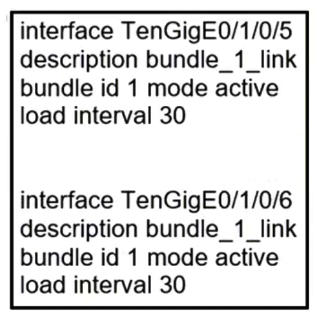
C)
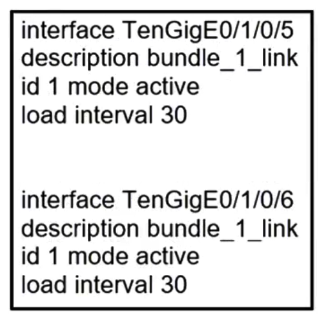
D)
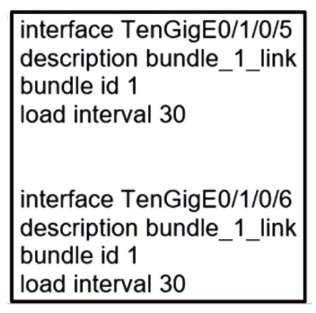

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
50
What are two factors to consider when implementing NSR High Availability on an MPLS PE router? (Choose two.)
A) It requires all PE-CE sessions to support NSR
B) It requires routing protocol extensions
C) It consumes more memory and CPU resources than NSF
D) It operates normally without NSR support on the PE peers
E) It cannot sync state information across redundant RPs
A) It requires all PE-CE sessions to support NSR
B) It requires routing protocol extensions
C) It consumes more memory and CPU resources than NSF
D) It operates normally without NSR support on the PE peers
E) It cannot sync state information across redundant RPs

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
51
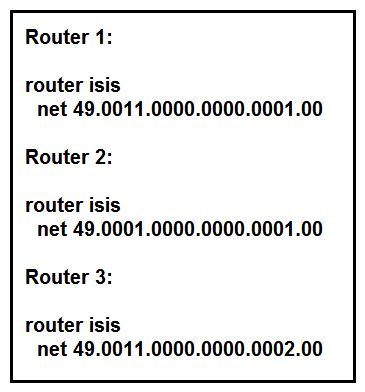 Refer to the exhibit. Router 4 is added to the network and must be in the same area as router 1. Which NET should the engineer assign?
Refer to the exhibit. Router 4 is added to the network and must be in the same area as router 1. Which NET should the engineer assign?A) 49.0111.0000.0000.0001.00
B) 49.0001.0000.0000.0004.00
C) 49.0011.0000.0000.0002.00
D) 49.0011.0000.0000.0003.00

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
52
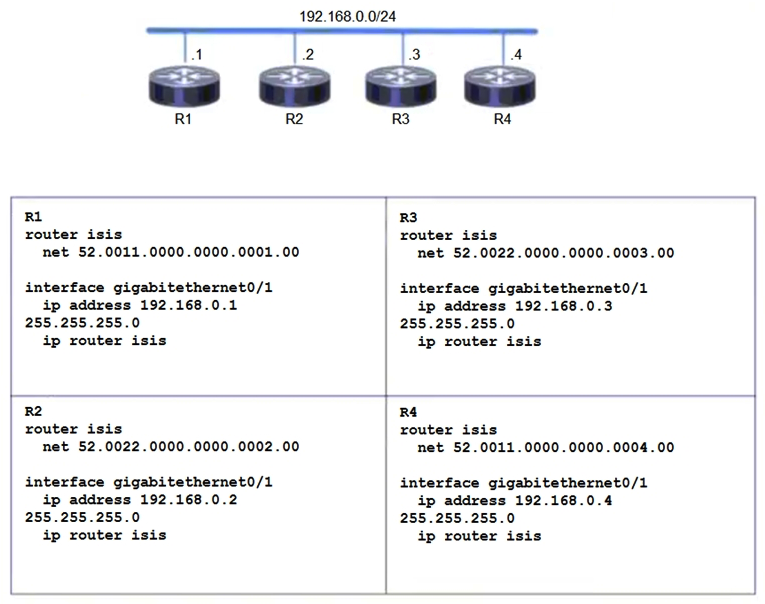 Refer to the exhibit. Which two topology changes happen to the IS-IS routers? (Choose two.)
Refer to the exhibit. Which two topology changes happen to the IS-IS routers? (Choose two.)A) R1 and R4 are Level 2 neighbors
B) All four routers are operating as Level 1-2 routers
C) All four routers are operating as Level 2 routers only
D) R1 and R2 are Level 2 neighbors
E) All four routers are operating as Level 1 routers only

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
53
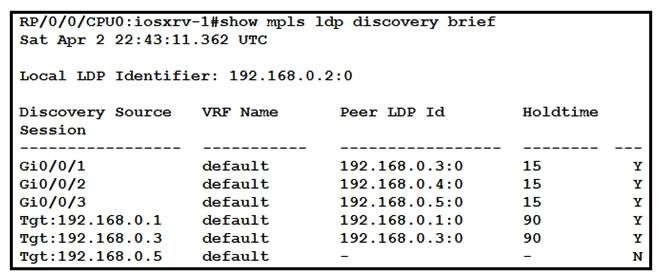 Refer to the exhibit. With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?
Refer to the exhibit. With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?A) 192.168.0.4
B) 192.168.0.5
C) 192.168.0.1
D) 192.168.0.3

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
54
Which utility can you use to locate MPLS faults?
A) MPLS LSP ping
B) QoS
C) MPLS traceroute
D) EEM
A) MPLS LSP ping
B) QoS
C) MPLS traceroute
D) EEM

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
55
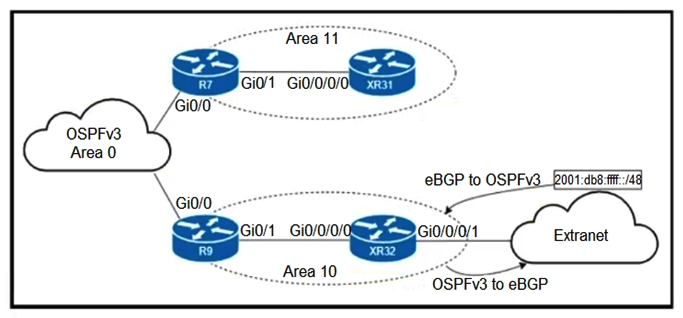 Refer to the exhibit. An engineer is updating this network to meet these conditions: Area 10 will receive inter-area routes and support mutual redistribution of external routes with the extranet. The ::/0 route is prohibited in Area 10. Area 11 will receive only the ::/0 route from the ABR. External route redistribution is not supported in Area 11. The ABR in Area 11 will advertise no interarea routes. Which two configurations must be performed to meet the requirements? (Choose two.)
Refer to the exhibit. An engineer is updating this network to meet these conditions: Area 10 will receive inter-area routes and support mutual redistribution of external routes with the extranet. The ::/0 route is prohibited in Area 10. Area 11 will receive only the ::/0 route from the ABR. External route redistribution is not supported in Area 11. The ABR in Area 11 will advertise no interarea routes. Which two configurations must be performed to meet the requirements? (Choose two.)A) Configure area 10 as nssa on R9 and XR32 Configure area 10 as nssa on R9 and XR32
B) Configure area 11 as stub no-summary on R7 and as stub on XR31 Configure area 11 as stub no-summary on R7 and as stub on XR31
C) Configure area 11 as nssa no-summary on R7 and as nssa on XR31 nssa no-summary
D) Configure area 11 as nssa default-information-originate on R7 and as nssa on XR31 nssa default-information-originate
E) Configure area 10 as stub on R9 and XR32

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
56
How can shared services in an MPLS Layer 3 VPN provide Internet access to the Customers of a central service provider?
A) Static routes on CE routers allow route leakage from a PE global routing table.
B) The CE router can establish a BGP peering to a PE router and use the PE device to reach the Internet.
C) The customer VRF uses route targets to import and export routes to and from a shared services VRF.
D) Route distinguishers are used to identify the routes that CEs can use to reach the Internet.
A) Static routes on CE routers allow route leakage from a PE global routing table.
B) The CE router can establish a BGP peering to a PE router and use the PE device to reach the Internet.
C) The customer VRF uses route targets to import and export routes to and from a shared services VRF.
D) Route distinguishers are used to identify the routes that CEs can use to reach the Internet.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
57
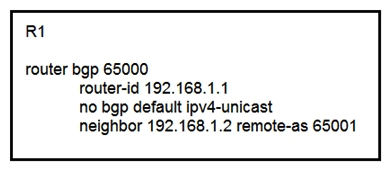 Refer to the exhibit. Which task completes the configuration?
Refer to the exhibit. Which task completes the configuration?A) Specify the local-as value in the neighbor statement
B) Specify the source interface in the neighbor statement
C) Specify the maximum number of prefixes that R1 receives from neighbor 192.168.1.2
D) Specify the activate neighbor 192.168.1.2 under the IPv4 address family

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
58
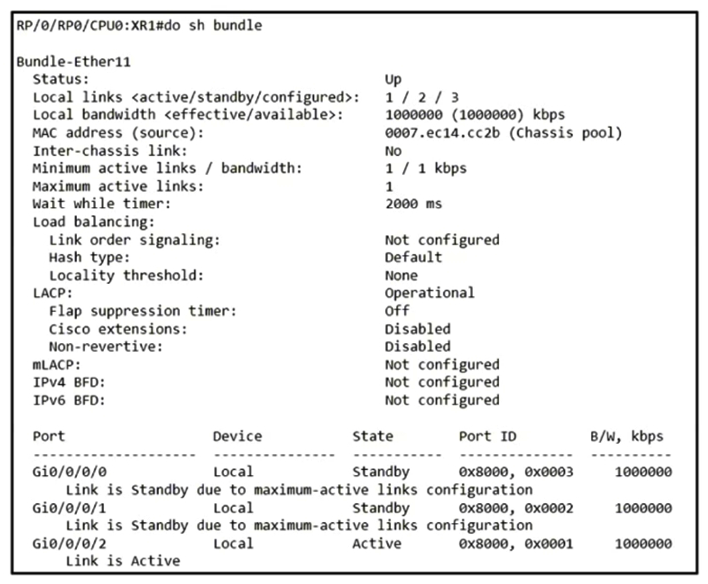 Refer to the exhibit. A network operator needs to shut down interface Gi0/0/0/2 for maintenance. What occurs to the interface states of Gi0/0/0/0 and Gi0/0/0/1?
Refer to the exhibit. A network operator needs to shut down interface Gi0/0/0/2 for maintenance. What occurs to the interface states of Gi0/0/0/0 and Gi0/0/0/1?A) Gi0/0/0/1 and Gi0/0/0/0 become active
B) Gi0/0/0/1 and Gi0/0/0/0 remain standby
C) Gi0/0/0/0 becomes active; Gi0/0/0/1 remains standby
D) Gi0/0/0/1 becomes active; Gi0/0/0/0 remains standby

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
59
Which regular expression query modifier function indicates the start of a string?
A) +
B) ^
C) $
D) [^]
A) +
B) ^
C) $
D) [^]

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
60
When configuring traffic engineering tunnels in Cisco MPLS core network, you see the traffic is not tacking the expected path in the core. Which command do you use to quickly check path of a TE tunnel?
A) traceroute
B) show mpls traffic-engineering tunnels
C) Ping
D) traceroute mpls ipv4
A) traceroute
B) show mpls traffic-engineering tunnels
C) Ping
D) traceroute mpls ipv4

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
61
 Refer to the exhibit. Which statement supports QPPB implementation?
Refer to the exhibit. Which statement supports QPPB implementation?A) QPPB policies affect only egress traffic.
B) QoS policies rely exclusively on BGP attributes to manipulate traffic.
C) QoS policies are identified in the MPLS forwarding table.
D) QoS policies use BGP to gain full coverage on the network.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
62
 Refer to the exhibit. A network engineer is implementing a BGP routing policy. Which effect of this configuration is true?
Refer to the exhibit. A network engineer is implementing a BGP routing policy. Which effect of this configuration is true?A) All traffic that matches acl10 is allowed without any change to its local-preference.
B) All traffic that matches acl10 is dropped without any change to its local-preference.
C) If traffic matches acl10, it is allowed and its local-preference is set to 300.
D) All traffic is assigned a local-preference of 300 regardless of its destination.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
63
An engineer needs to implement QOS mechanism on customer's network as some applications going over the Internet are slower than others. Which two actions must the engineer perform when implementing traffic shaping on the network in order to accomplish this task? (Choose two.)
A) Implement packet remarking for excess traffic
B) Configure a queue with sufficient memory to buffer excess packets
C) Implement a scheduling function to handle delayed packets
D) Configure the token values in bytes
E) Configure a threshold over which excess packets are discarded
A) Implement packet remarking for excess traffic
B) Configure a queue with sufficient memory to buffer excess packets
C) Implement a scheduling function to handle delayed packets
D) Configure the token values in bytes
E) Configure a threshold over which excess packets are discarded

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
64
A regional MPLS VPN provider operates in two regions and wants to provide MPLS L3VPN service for a customer with two sites in these separate locations. The VPN provider approaches another organization to provide backbone carrier services so that the provider can connect to these two locations. Which statement about this scenario is true?
A) When edge routers at different regional sites are connected over the global carrier backbone, MP-eBGP must run between the routers to exchange the customer VPNv4 routes.
B) When eBGP is used for label exchange using the send-label option, MPLS-BGP forwarding is configured under the global ABC CSC PE-to-CE interface.
C) When BGP is used for both route and label exchange, the neighbor a.b.c.d send-label command is used under the address-family VPNv4 command mode. When BGP is used for both route and label exchange, the neighbor a.b.c.d send-label command is used under the address-family VPNv4 command mode.
D) When IGP is used for route exchange and LDP for label exchange, MPLS is enabled only on the VRF interface on the backbone-carrier PE side.
A) When edge routers at different regional sites are connected over the global carrier backbone, MP-eBGP must run between the routers to exchange the customer VPNv4 routes.
B) When eBGP is used for label exchange using the send-label option, MPLS-BGP forwarding is configured under the global ABC CSC PE-to-CE interface.
C) When BGP is used for both route and label exchange, the neighbor a.b.c.d send-label command is used under the address-family VPNv4 command mode. When BGP is used for both route and label exchange, the neighbor a.b.c.d send-label command is used under the address-family VPNv4 command mode.
D) When IGP is used for route exchange and LDP for label exchange, MPLS is enabled only on the VRF interface on the backbone-carrier PE side.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
65
 Refer to the exhibit. Which statement describes the effect of this configuration?
Refer to the exhibit. Which statement describes the effect of this configuration?A) It matches HTTP traffic for use in a policy map.
B) It applies a service policy to all interfaces remarking HTTP traffic.
C) It creates an ACL named WEB that filters HTTP traffic.
D) It modifies the default policy map to allow all HTTP traffic through the router.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
66
Why do packet loops occur during the configuration of BIDIR-PIM?
A) The network does not support BIDIR-PIM.
B) The network is partially upgraded to support BIDIR-PIM.
C) The router has not been configured to advertise itself.
D) No interface for carrying traffic for multicast groups has been configured.
A) The network does not support BIDIR-PIM.
B) The network is partially upgraded to support BIDIR-PIM.
C) The router has not been configured to advertise itself.
D) No interface for carrying traffic for multicast groups has been configured.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
67
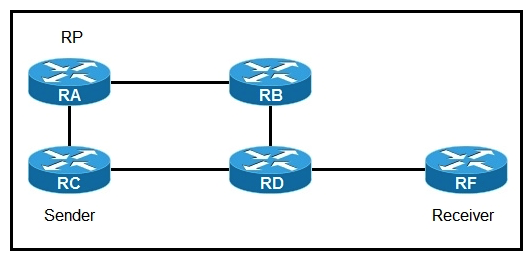 Refer to the exhibit. If router A is the RP, which PIM mode can you configure so that devices will send multicast traffic toward the RP?
Refer to the exhibit. If router A is the RP, which PIM mode can you configure so that devices will send multicast traffic toward the RP?A) PIM-SM
B) BIDIR-PIM
C) PIM-SSM
D) PIM-DM

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
68
What is the characteristic of the TI-LFA?
A) It guarantees a loop-free path for all areas configured in OSPF
B) It guarantees a loop-free path for all interfaces in the OSPF super backbone
C) It applies only on the instance and makes all the interfaces inherit the configuration
D) It applies on the area and instance and makes all the interfaces inherit the configuration
A) It guarantees a loop-free path for all areas configured in OSPF
B) It guarantees a loop-free path for all interfaces in the OSPF super backbone
C) It applies only on the instance and makes all the interfaces inherit the configuration
D) It applies on the area and instance and makes all the interfaces inherit the configuration

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
69
 Refer to the exhibit. A network engineer is implementing QoS services. Which two statements about the qos-group keyword on Cisco IOS XR are true? (Choose two.)
Refer to the exhibit. A network engineer is implementing QoS services. Which two statements about the qos-group keyword on Cisco IOS XR are true? (Choose two.)A) It marks packets for end-to-end QoS policy enforcement across the network.
B) QoS group marking occurs on the ingress.
C) The QoS group numbering corresponds to priority level.
D) QoS group can be used in fabric QoS policy as match criteria.
E) It cannot be used with priority traffic class.

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
70
A router RP is configured to perform MPLS LDP graceful restart. Which three steps are included when the RP sends an LDP initialization message to a neighbor to establish an LDP session? (Choose three.)
A) Learn from Neighbor (N) flag, set to 1
B) Recovery Time field
C) Type-9 LSA
D) Reconnect Timeout field
E) Graceful restart capability in OPEN message
F) Learn from Network (L) flag, set to 1
A) Learn from Neighbor (N) flag, set to 1
B) Recovery Time field
C) Type-9 LSA
D) Reconnect Timeout field
E) Graceful restart capability in OPEN message
F) Learn from Network (L) flag, set to 1

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
71
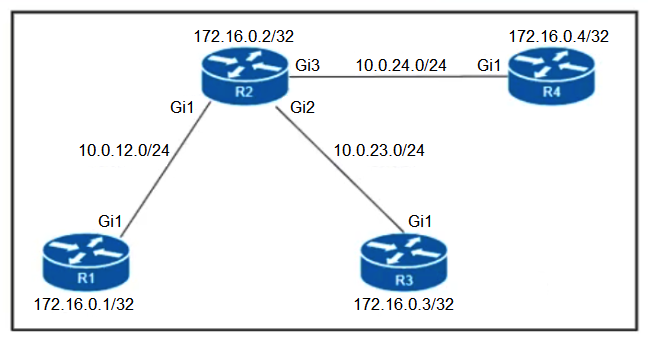 Refer to the exhibit. Which configuration must be applied to each of the four routers on the network to reduce LDP LIB size and advertise label bindings for the /32 loopback IP space only?
Refer to the exhibit. Which configuration must be applied to each of the four routers on the network to reduce LDP LIB size and advertise label bindings for the /32 loopback IP space only?A)

B)

C)

D)
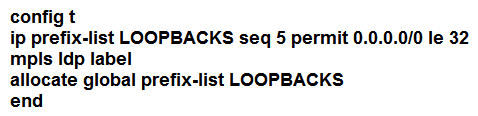

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
72
 Refer to the exhibit. An engineer is configuring two routers to support MPLS LDP sessions between them. The R1 configuration is complete, and work has started on R2 as shown. Which additional configuration must the engineer apply to R2 to complete the task?
Refer to the exhibit. An engineer is configuring two routers to support MPLS LDP sessions between them. The R1 configuration is complete, and work has started on R2 as shown. Which additional configuration must the engineer apply to R2 to complete the task?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
73
What causes multicast traffic to permanently stay on the shared tree and not switch to the source tree?
A) SSM range is being used
B) The RP announcements are being filtered
C) The SPT threshold is set to infinity
D) The RP IP address is configured incorrectly
A) SSM range is being used
B) The RP announcements are being filtered
C) The SPT threshold is set to infinity
D) The RP IP address is configured incorrectly

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
74
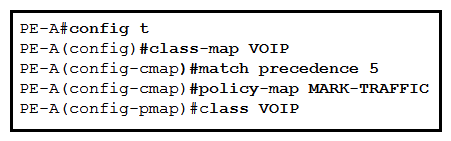 Refer to the exhibit. Which command is used to complete this configuration for QoS class-based marking?
Refer to the exhibit. Which command is used to complete this configuration for QoS class-based marking?A) PE-A(config-pmap-c)#set dscp ef
B) PE-A(config-pmap-c)#priority
C) PE-A(config-pmap-c)#random-detect
D) PE-A(config-pmap-c)#fair-queue

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
75
Which two actions describe LSP delegation to PCE servers? (Choose two.)
A) removing TE re-optimization timer timeouts
B) changing the precedence of any of the PCE servers
C) entering the mpls traffic-eng reoptimize command entering the mpls traffic-eng reoptimize command
D) adding a new PCE server with lower precedence than the primary PCE
E) adding a new PCE server with higher precedence than the primary PCE
A) removing TE re-optimization timer timeouts
B) changing the precedence of any of the PCE servers
C) entering the mpls traffic-eng reoptimize command entering the mpls traffic-eng reoptimize command
D) adding a new PCE server with lower precedence than the primary PCE
E) adding a new PCE server with higher precedence than the primary PCE

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
76
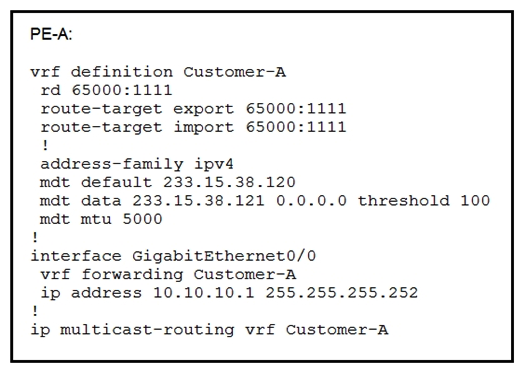 Refer to the exhibit. An engineer is implementing Auto-RP and reviewing the configuration of the PE-A. Which configuration permits Auto-RP messages to be forwarded over this interface?
Refer to the exhibit. An engineer is implementing Auto-RP and reviewing the configuration of the PE-A. Which configuration permits Auto-RP messages to be forwarded over this interface?A) PE-A(config-if)#no ip pim bsr-border
B) PE-A(config-if)#ip igmp version 3
C) PE-A(config-if)#ip pim sparse-mode
D) PE-A(config-if)#ip pim sparse-dense-mode

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
77
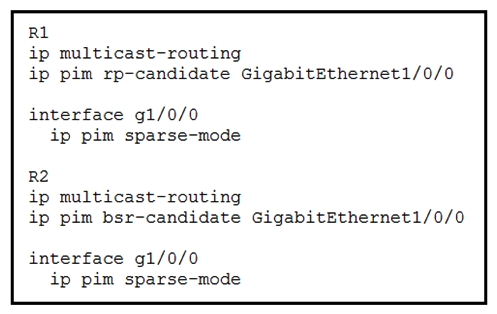 Refer to the exhibit. An engineer configured multicast routing on client's network. What is the effect of this multicast implementation?
Refer to the exhibit. An engineer configured multicast routing on client's network. What is the effect of this multicast implementation?A) R2 is unable to share information because the ip pim autorp listener command is missing R2 is unable to share information because the ip pim autorp listener command is missing
B) R1 floods information about R2 throughout the multicast domain
C) R2 floods information about R1 throughout the multicast domain
D) R2 is elected as the RP for this domain

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
78
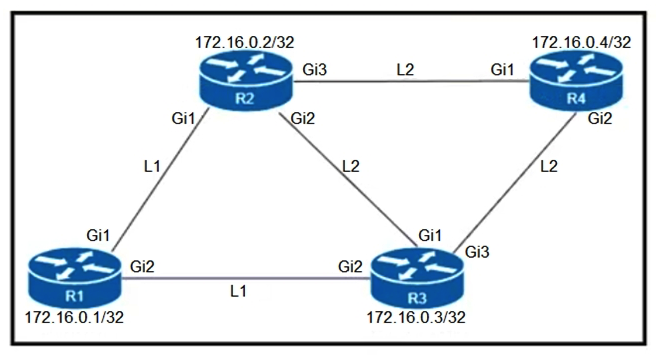 Refer to the exhibit. An engineer must configure router R2 as the new P router in the network. Which configuration must be applied to R2 to enable LDP-IGP Sync on its L2 IS-IS adjacencies?
Refer to the exhibit. An engineer must configure router R2 as the new P router in the network. Which configuration must be applied to R2 to enable LDP-IGP Sync on its L2 IS-IS adjacencies?A)

B)
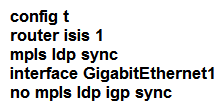
C)
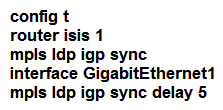
D)


Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
79
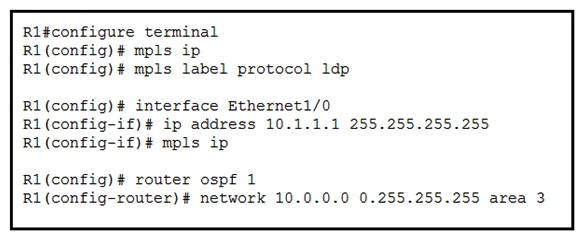 Refer to the exhibit. A network engineer is configuring MPLS LDP synchronization on router R1. Which additional configuration must an engineer apply to R1 so that it will synchronize to OSPF process 1?
Refer to the exhibit. A network engineer is configuring MPLS LDP synchronization on router R1. Which additional configuration must an engineer apply to R1 so that it will synchronize to OSPF process 1?A)

B)

C)

D)


Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck
80
A network engineer is configuring a router to send multicast traffic for the 239.10.10.10 group. Which configuration must an engineer apply to the router to implement IGMP and forward the traffic?
A)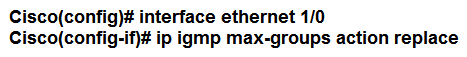
B)
C)
D)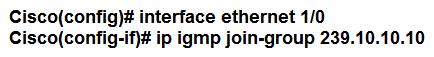
A)
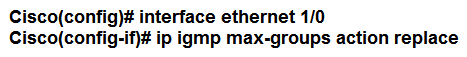
B)

C)

D)
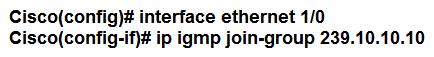

Unlock Deck
Unlock for access to all 116 flashcards in this deck.
Unlock Deck
k this deck



