Deck 6: HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching)
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/331
Play
Full screen (f)
Deck 6: HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching)
1
Assume that a TCP connection works properly, and the peer AS number configured for a BGP router is different from the AS number of its BGP peer. During the establishment of a BGP session, the BGP router exchanges routing information with its peer, and finds that its peer AS number is different from the AS number of the peer. Therefore, the BGP router sends a Notification message to the peer, indicating that the establishment of a BGP session fails. Which message can be identified by the Error Code field in the Notification message?
A) Route-refresh
B) Open
C) Keepalive
D) Update
A) Route-refresh
B) Open
C) Keepalive
D) Update
Open
2
The import-route limit command is used to set the maximum number of external routers that can be imported into an OSPF process.
True
3
Which of the following are characteristics of a high availability network? (Choose two.)
A) Faults seldom occur.
B) Services can be quickly restored when a fault occurs.
C) Faults never occur.
D) Services can only be manually restored when a fault occurs.
A) Faults seldom occur.
B) Services can be quickly restored when a fault occurs.
C) Faults never occur.
D) Services can only be manually restored when a fault occurs.
Faults seldom occur.
Services can be quickly restored when a fault occurs.
Services can be quickly restored when a fault occurs.
4
Which of the following elements together uniquely identify a LSA? (Choose three.)
A) LS type
B) Link state ID
C) Advertising Router
D) LS Sequence number
A) LS type
B) Link state ID
C) Advertising Router
D) LS Sequence number

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
5
Which of the following address types are reserved for multicast use?
A) Class A
B) Class B
C) Class E
D) Class D
A) Class A
B) Class B
C) Class E
D) Class D

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
6
Which types of packets are supported by BGP? (Choose three.)
A) Hello
B) Notification
C) Update
D) Route-refresh
A) Hello
B) Notification
C) Update
D) Route-refresh

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
7
By default, the cost of an OSPF interface is related to interface bandwidth. The algorithm for calculating the cost is: bandwidth-reference/bandwidth.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
8
An Autonomous System (AS) is a set of routers under a single technical administration, using the same routing policy.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
9
In VRP 5.7, which of the following dynamic protocols support GR? (Choose three.)
A) MPLS LDP/RSVP
B) IS-IS/OSPF
C) BGP
D) MSTP
A) MPLS LDP/RSVP
B) IS-IS/OSPF
C) BGP
D) MSTP

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
10
Which of the following statements about RPs are true? (Choose three.)
A) Different group addresses on a PIM-SM network can correspond to different RPs.
B) An RP is the root of an RPT.
C) An RP is elected out of BSRs.
D) All routers on a PIM-SM network must know the location of RPs.
A) Different group addresses on a PIM-SM network can correspond to different RPs.
B) An RP is the root of an RPT.
C) An RP is elected out of BSRs.
D) All routers on a PIM-SM network must know the location of RPs.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
11
Simple traffic classification in QoS classifies packets based on the 5-tuple information, including the source IP address, source port number, protocol number, destination IP address, and destination port number.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
12
In OSPF, the process of calculating shortest path tree can be divided into two phases, calculate Transit node first, then calculate Stub network.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
13
A network administrator needs to construct a small-scale network containing only 22 hosts and the ISP assigns only one public IP address as the egress address. Which of the following addresses can be used by the network administrator to plan the network?
A) 10.11.12.16/28
B) 172.31.255.128/27
C) 192.168.1.0/28
D) 209.165.202.128/27
A) 10.11.12.16/28
B) 172.31.255.128/27
C) 192.168.1.0/28
D) 209.165.202.128/27

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
14
BFD detects the link status immediately after a BFD session is set up. If BFD parameters are modified or deleted at one end of the BFD session, the other end will consider such a modification or deletion as a fault and services will be then affected. Therefore, exercise caution when modifying or deleting BFD parameters.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
15
Which of the followings is used to avoid route loops in BGP?
A) Use ORIGIN attribute to record route origin
B) Use AS_PATH attribute to record all ASs during a route passing from the local area to the destination in a certain order
C) Use NEXT_HOP attribute to record next hop of the route
D) Use MED attribute to influence export selection of other AS
A) Use ORIGIN attribute to record route origin
B) Use AS_PATH attribute to record all ASs during a route passing from the local area to the destination in a certain order
C) Use NEXT_HOP attribute to record next hop of the route
D) Use MED attribute to influence export selection of other AS

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
16
If the peer default-route-advertise command is used to advertise a default BGP route to peers, how will this operation affect the local BGP routing table?
A) An inactive default route will be generated in the local BGP routing table and this route will not be delivered to the IP routing table.
B) An active default route will be generated in the local BGP routing table and this route will be delivered to the IP routing table.
C) The local BGP routing table will not be affected and no default route will be generated in the local BGP routing table.
D) A default route will be generated in the local BGP routing table and whether to deliver this route to the IP routing table depends on route selection results.
A) An inactive default route will be generated in the local BGP routing table and this route will not be delivered to the IP routing table.
B) An active default route will be generated in the local BGP routing table and this route will be delivered to the IP routing table.
C) The local BGP routing table will not be affected and no default route will be generated in the local BGP routing table.
D) A default route will be generated in the local BGP routing table and whether to deliver this route to the IP routing table depends on route selection results.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
17
Which of the following statements are correct regarding intra-area route calculation of OSPF? (Choose two.)
A) Every OSPF router only uses one Router LSA to describe local active link state for one area.
B) Every OSPF uses more than one Router LSA to describe local active link state for one area.
C) One Router LSA only describes one link.
D) One Router LSA describes more than one link.
A) Every OSPF router only uses one Router LSA to describe local active link state for one area.
B) Every OSPF uses more than one Router LSA to describe local active link state for one area.
C) One Router LSA only describes one link.
D) One Router LSA describes more than one link.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
18
The preceding information is generated after a router receives a Report message from group 225.0.0.1 through Ethernet 6/1/0. 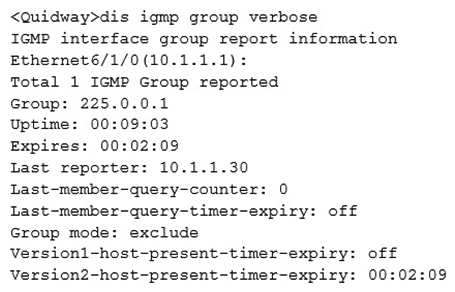 Which type of Report message will not be processed by the router?
Which type of Report message will not be processed by the router?
A) IS_IN
B) ALLOW
C) BLOCK
D) TO_IN
 Which type of Report message will not be processed by the router?
Which type of Report message will not be processed by the router?A) IS_IN
B) ALLOW
C) BLOCK
D) TO_IN

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
19
Which of the following statements about ACL type are true? (Choose three.)
A) ACL consists of basic ACL, advanced ACL and interface-based ACL
B) ACL ranging from 2000 to 2999 belongs to advanced ACL
C) ACL ranging from 3000 to 3999 belongs to advanced ACL
D) Advanced ACL can be used to match either destination address or source address
A) ACL consists of basic ACL, advanced ACL and interface-based ACL
B) ACL ranging from 2000 to 2999 belongs to advanced ACL
C) ACL ranging from 3000 to 3999 belongs to advanced ACL
D) Advanced ACL can be used to match either destination address or source address

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
20
Different from a Stub area, an NSSA supports Type-5 LSAs.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
21
OSPF is running on a network. In OSPF, what LSA type would only cause an Incremental SPF calculation? (Multiple Choice)
A) Type 3
B) Type 4
C) Type 1
D) Type 2
E) Type 5
A) Type 3
B) Type 4
C) Type 1
D) Type 2
E) Type 5

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
22
When a router within the HW network makes a forwarding decision, the _____is always used to select the best route from those installed in the routing table.
A) Routing process ID
B) Longest prefix match
C) Administrative Distance
D) Router ID
E) Peer ID
A) Routing process ID
B) Longest prefix match
C) Administrative Distance
D) Router ID
E) Peer ID

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
23
The link that connects a PC to a switch is ( ).
A) Access Link
B) Trunk Link
C) Hybrid Link
D) ISL Link
A) Access Link
B) Trunk Link
C) Hybrid Link
D) ISL Link

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
24
Which parameter will not be received from the root bridge by a non-root bridge running 802.1D STP?
A) Forward delay
B) Hello time
C) Root cost
D) Hold time
E) Max Age
A) Forward delay
B) Hello time
C) Root cost
D) Hold time
E) Max Age

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
25
Which of the following can be used for BGP route selection? (Multiple Choice)
A) DSCP
B) IP-PREFIX
C) ACL
D) AS-PATH-FILTER
A) DSCP
B) IP-PREFIX
C) ACL
D) AS-PATH-FILTER

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
26
Router HW1 is seeing a large number of Discard Eligible (DE) frames. In Frame-relay, as part of the Congestion-Control Mechanism, the DE bit works in conjunction with which of the following mechanisms?
A) Differentiated Services Code Point (DSCP) settings
B) Frame-relay Traffic Shaping (FRTS) settings
C) Class-to-Service (CoS) settings
D) Type-of-service (ToS) settings
E) Forward Explicit Congestion Notification (FECN) of Backward Explicit Congestion Notification (BECN) settings
A) Differentiated Services Code Point (DSCP) settings
B) Frame-relay Traffic Shaping (FRTS) settings
C) Class-to-Service (CoS) settings
D) Type-of-service (ToS) settings
E) Forward Explicit Congestion Notification (FECN) of Backward Explicit Congestion Notification (BECN) settings

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
27
If a router receives a BGP route carrying the no-export community attribute, which of the following actions does the router take?
A) Does not advertise the route to other BGP routers
B) Discards the route directly
C) Advertises the route to IBGP peers only
D) Advertises the route normally, but does not use it to forward data
A) Does not advertise the route to other BGP routers
B) Discards the route directly
C) Advertises the route to IBGP peers only
D) Advertises the route normally, but does not use it to forward data

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
28
With regard to TCP headers, which control bit tells the receiver to reset the TCP connection?
A) SND
B) CLR
C) PSH
D) SYN
E) RST
F) ACK
A) SND
B) CLR
C) PSH
D) SYN
E) RST
F) ACK

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
29
Which of the following statements are NOT true regarding the TCP sliding window protocol? (Multiple Choice)
A) The initial window offer is advertised by the sender
B) If the retransmission timer expires without the sender receiving an ACK message, the receiver retransmits the packet to the sender.
C) The size of the sliding window can only increase or stay the same
D) It allows the transmission of multiple frames before waiting for an acknowledgment
E) The receiver is required to acknowledge the data packets transmitted by the sender
F) The sender need not transmit a full window's worth of data
A) The initial window offer is advertised by the sender
B) If the retransmission timer expires without the sender receiving an ACK message, the receiver retransmits the packet to the sender.
C) The size of the sliding window can only increase or stay the same
D) It allows the transmission of multiple frames before waiting for an acknowledgment
E) The receiver is required to acknowledge the data packets transmitted by the sender
F) The sender need not transmit a full window's worth of data

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
30
In a data communication session between two hosts, the session layer in the OSI model generally communicates with what other layer of the OSI model?
A) The physical layer of the peer
B) The peer's presentation layer
C) The peer's session layer
D) The peer's application layer
E) The data link layer of the peer
A) The physical layer of the peer
B) The peer's presentation layer
C) The peer's session layer
D) The peer's application layer
E) The data link layer of the peer

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
31
Two routers configured to run BGP have been connected to a firewall, one on the inside interface and one on the outside interface. BGP has been configured so the two routers should peer, including the correct BGP session endpoint addresses and the correct BGP session hop-count limit (EBGP multihop). What is a good first test to see if BGP will work across the firewall?
A) There is no way to make BGP work across a firewall without special configuration, so there is no simple test that will show you if BGP will work, other than trying to start the peering session.
B) Attempt to Telnet from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If Telnet works, BGP will work, since telnet and BGP both use TCP to transport data
C) There is no way to make BGP work across a firewall
D) Ping from the router connected to the inside interface of the firewall to the router connected to the outside interface of the firewall. If you can ping between them, BGP should work, since BGP uses IP to transport packets.
A) There is no way to make BGP work across a firewall without special configuration, so there is no simple test that will show you if BGP will work, other than trying to start the peering session.
B) Attempt to Telnet from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If Telnet works, BGP will work, since telnet and BGP both use TCP to transport data
C) There is no way to make BGP work across a firewall
D) Ping from the router connected to the inside interface of the firewall to the router connected to the outside interface of the firewall. If you can ping between them, BGP should work, since BGP uses IP to transport packets.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
32
Spanning Tree Protocol calculates path cost based on which of the following?
A) Interface bandwidth
B) Interface delay
C) Hop count
D) Interface bandwidth and delay
E) Bridge priority
A) Interface bandwidth
B) Interface delay
C) Hop count
D) Interface bandwidth and delay
E) Bridge priority

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
33
On router HW1, you want to view the status of a frame relay connection. Which "display" commands will show the status of a Frame-Relay PVC? (Multiple choice)
A) display frame relay interface
B) display frame relay pvc
C) display fr lmi-info
D) display fr map-info interface Serial 0/0/0
E) display fr interface Serial 0/0/0
F) display fr inarp-info
A) display frame relay interface
B) display frame relay pvc
C) display fr lmi-info
D) display fr map-info interface Serial 0/0/0
E) display fr interface Serial 0/0/0
F) display fr inarp-info

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
34
What is the destination IP address of routing update packets sent by RIPv2?
A) 255.255.255.255
B) 224.0.0.1
C) 224.0.0.5
D) 224.0.0.9
E) 224.0.0.10
A) 255.255.255.255
B) 224.0.0.1
C) 224.0.0.5
D) 224.0.0.9
E) 224.0.0.10

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
35
Which types of prefixes will a router running BGP most likely advertise to an IBGP peer, assuming it is not configured as a route reflector?
A) Prefixes received from EBGP peers and prefixes received from route reflectors
B) All prefixes in its routing table
C) Prefixes received from EBGP peers and prefixes locally originated via network statements or imported
D) Prefixes received from other IBGP peers, prefixes received from EBGP peers, and prefixes imported to BGP
E) Prefixes received from other IBGP peers and prefixes received from router reflectors
F) Prefixes received from any other BGP peer and prefixes locally originated via network statements or imported
A) Prefixes received from EBGP peers and prefixes received from route reflectors
B) All prefixes in its routing table
C) Prefixes received from EBGP peers and prefixes locally originated via network statements or imported
D) Prefixes received from other IBGP peers, prefixes received from EBGP peers, and prefixes imported to BGP
E) Prefixes received from other IBGP peers and prefixes received from router reflectors
F) Prefixes received from any other BGP peer and prefixes locally originated via network statements or imported

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
36
Congestion management provides a means to manage and control traffic when traffic congestion occurs.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
37
When a router is building a routing table from different routing protocols, which of the following will determine the routes to be installed in the routing table?
A) The fastest routing process
B) uniqueness
C) Higher preference value
D) The route with the largest next-hop address
E) Low Router ID
A) The fastest routing process
B) uniqueness
C) Higher preference value
D) The route with the largest next-hop address
E) Low Router ID

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
38
Which of the following are found in a basic Network Layer Packet? (Multiple Choice.)
A) Network Layer Header
B) Path records
C) Data Link Layer Header
D) Upper Layer Data
E) Network Layer Trailer
A) Network Layer Header
B) Path records
C) Data Link Layer Header
D) Upper Layer Data
E) Network Layer Trailer

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
39
Before establishing a network, we must create VLANs. The users that do not need to communicate with each other should be added to the same VLAN for isolation.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
40
Which types of interfaces are supported by Huawei switches after the VLAN function is configured? (Choose three.)
A) Access interface
B) Trunk interface
C) Hybrid interface
D) Dialer interface
A) Access interface
B) Trunk interface
C) Hybrid interface
D) Dialer interface

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
41
Routers HW1 and HW2 are IP Multicast routers. These routers use (S, G) entries for multicast packet forwarding. Which of the following address types are used in the "S" entry?
A) The block of administratively scoped multicast addresses
B) Source Specific multicast addresses
C) SDP/SAP addresses
D) Any class A, Class B, or Class C host address
E) GLOP addresses
A) The block of administratively scoped multicast addresses
B) Source Specific multicast addresses
C) SDP/SAP addresses
D) Any class A, Class B, or Class C host address
E) GLOP addresses

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
42
Which of the following statements are true about RIPng? (Multiple Choice)
A) RIPng does not have an authentication mechanism
B) Each RIPng update packet contains a maximum of 25 routes
C) RIPng supports MD5 authentication
D) RIPng uses the link local address to send update packets
E) RIPng supports a maximum of 32 hops
A) RIPng does not have an authentication mechanism
B) Each RIPng update packet contains a maximum of 25 routes
C) RIPng supports MD5 authentication
D) RIPng uses the link local address to send update packets
E) RIPng supports a maximum of 32 hops

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
43
Before configuring AAA, you need to define the RADIUS server. The following commands can be used to define it. [Huawei]radius-server template EXAM [Huawei-radius-EXAM] radius-server shared-key cipher HUAwei123 [Huawei-radius-EXAM] radius-server authentication 10.7.66.66 1812 [Huawei-radius-EXAM] radius-server authorization 10.7.66.66 1812 [Huawei-radius-EXAM] radius-server accounting 10.7.66.66 1813 [Huawei-radius-EXAM] radius-server retransmit 2

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
44
Switches use IPSG to verify the source address of IP packets. IPSG obtains the binding table by listening to the address resolution process.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
45
An IPv6 device with the address of FC00::1 connects to the network and captures the following data packet. What is function of the data packet? 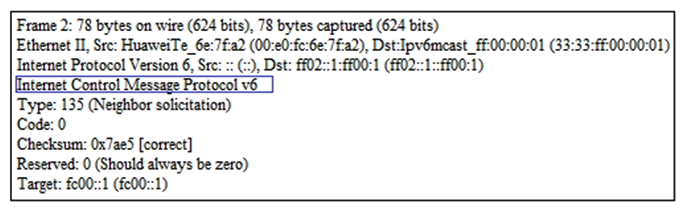
A) There are multiple routers on the network segment. One router advertises router redirect messages to the IPv6 device.
B) The router on this network segment tests the working status of the IPv6 device
C) The IPv6 device implements self-loop tests
D) Another device on this network segment requests to resolve the Layer 2 address of the IPv6 device
E) The IPv6 device requests the address of the egress router
F) The IPv6 device checks address configuration of other devices on the network

A) There are multiple routers on the network segment. One router advertises router redirect messages to the IPv6 device.
B) The router on this network segment tests the working status of the IPv6 device
C) The IPv6 device implements self-loop tests
D) Another device on this network segment requests to resolve the Layer 2 address of the IPv6 device
E) The IPv6 device requests the address of the egress router
F) The IPv6 device checks address configuration of other devices on the network

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
46
Source Specific Multicast (SSM)is being used throughput the HW IP Multicast network. Which of the following three statements about SSM are true? (Choose three.)
A) SSM uses Shortest-Path Trees Only
B) There are no RPs to worry about
C) SSM is best suited for applications that are of the Many-to-Many category
D) SSM uses shared Trees only
E) The use of SSM is recommended when there are many sources and it is desirable to keep the amount of mroute state in the routers in the network to a minimum.
F) SSM is best suited for applications that are of one-to-many category
A) SSM uses Shortest-Path Trees Only
B) There are no RPs to worry about
C) SSM is best suited for applications that are of the Many-to-Many category
D) SSM uses shared Trees only
E) The use of SSM is recommended when there are many sources and it is desirable to keep the amount of mroute state in the routers in the network to a minimum.
F) SSM is best suited for applications that are of one-to-many category

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
47
Which of the following are functions of Random Early Discard (RED)?
A) Avoiding global synchronization for TCP traffic
B) Performs rate limiting on the specified data traffic
C) Ensuring that high priority traffic gets sent first
D) Preventing starvation in lower priority queues
E) Minimizing packet delay jitter
A) Avoiding global synchronization for TCP traffic
B) Performs rate limiting on the specified data traffic
C) Ensuring that high priority traffic gets sent first
D) Preventing starvation in lower priority queues
E) Minimizing packet delay jitter

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
48
From the list of applications below, identify the TCP port numbers used for 443, 179,137,110, and 23 in the proper sequence:
A) HTTPS, BGP, NetBios Name Server, POP3, Telnet
B) Finger, DHCP Server, NetBios Name Server, POP3, Telnet
C) BGP, POP3, SNMP, TFTP, Telnet
D) LDAP, SNMP, TFTP, POP3, Telnet
E) HTTPS, SNMP, POP3, DNS, Telnet
A) HTTPS, BGP, NetBios Name Server, POP3, Telnet
B) Finger, DHCP Server, NetBios Name Server, POP3, Telnet
C) BGP, POP3, SNMP, TFTP, Telnet
D) LDAP, SNMP, TFTP, POP3, Telnet
E) HTTPS, SNMP, POP3, DNS, Telnet

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
49
Authentication can be configured in the IS-IS protocol to enhance IS-IS security. The IS-IS authentication functions include interface authentication, area authentication, and routing domain authentication.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
50
Which of the following statements about penultimate hop popping are true?
A) It can only be used with LDP
B) It enables the Edge LSR to request a label pop operation from its upstream neighbors
C) It is only used when two or more labels are stacked
D) It is requested through LDP using a special label value that is also called the implicit-null value
E) It is used only for directly connected subnets or aggregate routes
A) It can only be used with LDP
B) It enables the Edge LSR to request a label pop operation from its upstream neighbors
C) It is only used when two or more labels are stacked
D) It is requested through LDP using a special label value that is also called the implicit-null value
E) It is used only for directly connected subnets or aggregate routes

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
51
Based on the routing information exchange mode, MPLS VPNs are usually classified into two types. One is the overlay VPN. What is the other type of MPLS VPN?
A) L3 VPN
B) Virtual Private Network
C) L2 VPN
D) Peer-to-Peer VPN
A) L3 VPN
B) Virtual Private Network
C) L2 VPN
D) Peer-to-Peer VPN

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
52
Which of the following are legal representations of the IPv6 prefix 12AB00000000CD30? (Multiple Choice)
A) 12AB::CD3::/64
B) 12AB::CD30/64
C) 12AB::0000:0000:CD30:0000:0000:0000:0000/64
D) 12AB:0:0:CD3::/64
E) 12AB:0:0:CD3/64
A) 12AB::CD3::/64
B) 12AB::CD30/64
C) 12AB::0000:0000:CD30:0000:0000:0000:0000/64
D) 12AB:0:0:CD3::/64
E) 12AB:0:0:CD3/64

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
53
Which of the following scenarios can an AS-path-filter be used for? (Multiple Choice)
A) Apply clauses in a route-policy
B) Filtering the routes received from a BGP peer based on the as-path attributes of the routes, for example, peer X.X.X.X as path-filter import
C) Filtering the routes sent to a BGP peer based on the as-path attributes of the routers, for example, peer X.X.X.X as-path-filter export
D) If-match clauses in a route-policy
A) Apply clauses in a route-policy
B) Filtering the routes received from a BGP peer based on the as-path attributes of the routes, for example, peer X.X.X.X as path-filter import
C) Filtering the routes sent to a BGP peer based on the as-path attributes of the routers, for example, peer X.X.X.X as-path-filter export
D) If-match clauses in a route-policy

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
54
You must configure a router for Policy Based Routing (PBR). PBR allows network administrators to implement routing policies to allow or deny paths on which of the following? (Multiple Choice)
A) Protocol
B) Identification of a particular end system
C) Application
D) Throughput
E) Size of packets
F) None of the above
A) Protocol
B) Identification of a particular end system
C) Application
D) Throughput
E) Size of packets
F) None of the above

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
55
The HW network consists of Network A and B that are connected via Router HW1 and Router HW2. The HW network is shown in the following exhibit. To set up an IPSec VPN between routers HW1 and HW2, which of the following crypto access-lists must be configured on Router HW1 in order to send LAN to LAN traffic across the encrypted VPN tunnel? 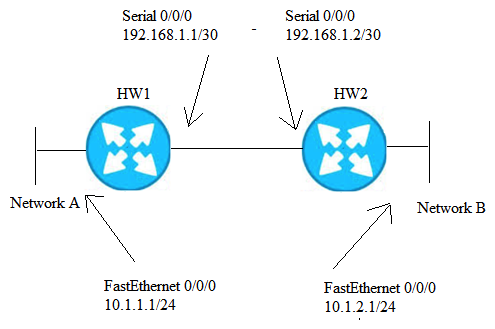
A) rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
B) rule permit ip source 10.1.1.0 0.0.0.255 destination 192.168.1.2 0
C) rule permit ip source 198.168.1.1 0 destination 192.168.1.2 0
D) rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
E) rule permit ip source 192.168.1.1 0 destination 10.1.2.0 0.0.0.255

A) rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
B) rule permit ip source 10.1.1.0 0.0.0.255 destination 192.168.1.2 0
C) rule permit ip source 198.168.1.1 0 destination 192.168.1.2 0
D) rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
E) rule permit ip source 192.168.1.1 0 destination 10.1.2.0 0.0.0.255

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
56
Which of the following are differences between PIM-SM and PIM-DM? (Multiple Choice)
A) PIM-SM has RPTs and SPTs but PIM-DM has only RPTs
B) BSRs/RPs exist only on a PIM-SM network, not on a PIM-DM network
C) PIM-SM is applicable to a network with few receivers; PIM-DM is applicable to a network with a larger number of receivers
D) Whether in PIM-SM or PIM-DM mode, receiver hosts must join multicast groups through IGMP
A) PIM-SM has RPTs and SPTs but PIM-DM has only RPTs
B) BSRs/RPs exist only on a PIM-SM network, not on a PIM-DM network
C) PIM-SM is applicable to a network with few receivers; PIM-DM is applicable to a network with a larger number of receivers
D) Whether in PIM-SM or PIM-DM mode, receiver hosts must join multicast groups through IGMP

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
57
Each DD packet has a DD sequence number for packet acknowledgment. A DD sequence number is two-bytes long.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
58
The default SSM group address range is 232.0.0.0/8. Which of the following configurations can be performed to modify the SSM group address range?
A) Run the ssm-policy advanced-acl-number command in the system view to configure the SSM group address range
B) Run the ssm-policy basic-acl-number command in the system view to configure the SSM group address range
C) Run the ssm-policy advanced-acl-number command in the PIM view to configure the SSM group address range
D) Run the ssm-policy basic-acl-number command in the PIM view to configure the SSM group address range
A) Run the ssm-policy advanced-acl-number command in the system view to configure the SSM group address range
B) Run the ssm-policy basic-acl-number command in the system view to configure the SSM group address range
C) Run the ssm-policy advanced-acl-number command in the PIM view to configure the SSM group address range
D) Run the ssm-policy basic-acl-number command in the PIM view to configure the SSM group address range

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
59
Which of the following statements are false about Weighted Round Robin (WRR)? (Multiple Choice)
A) WRR is a congestion management technology
B) WRR prevents congestion on the network
C) WRR ensures important traffic being forwarded first
D) WRR ensures that all queues being serviced
E) WRR cannot be used on gigabit-ethernet interfaces
A) WRR is a congestion management technology
B) WRR prevents congestion on the network
C) WRR ensures important traffic being forwarded first
D) WRR ensures that all queues being serviced
E) WRR cannot be used on gigabit-ethernet interfaces

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
60
Which IPv6 header field has a function similar to that of the "Type of Service" field in an IPv4 header?
A) Flow Label
B) Traffic Class
C) Next Header
D) Version
A) Flow Label
B) Traffic Class
C) Next Header
D) Version

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
61
After IS-IS area authentication is configured, which of the following IS-IS packets will carry authentication information?
A) IS-IS Level-1 SNPs and LSPs
B) IS-IS Level-1 Hello PDUs
C) IS-IS Level-2 Hello PDUs
D) IS-IS Level-2 SNPs and LSPs
A) IS-IS Level-1 SNPs and LSPs
B) IS-IS Level-1 Hello PDUs
C) IS-IS Level-2 Hello PDUs
D) IS-IS Level-2 SNPs and LSPs

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
62
Which of the following statements is false about the DSCP field?
A) When the DSCP value is EF, data is forwarded in expedited forwarding mode
B) CS in DSCP classifies data based on eight priorities
C) DSCP can represent the data priority as well as the packet drop probability
D) The DSCP value can be 0. When the value is 0, the default packet forwarding mechanism is used
A) When the DSCP value is EF, data is forwarded in expedited forwarding mode
B) CS in DSCP classifies data based on eight priorities
C) DSCP can represent the data priority as well as the packet drop probability
D) The DSCP value can be 0. When the value is 0, the default packet forwarding mechanism is used

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
63
Which of the following statements regarding LACP are true?
A) You can run the following commands to delete member interfaces from an Eth-Trunk: interface GigabitEthernet0/0/1 shutdown undo eth-trunk 1 undo shutdown
B) You can run the following commands to prevent frequent flapping due to physical link faults on an Eth-Trunk: interface eth-trunk 1 lacp preempt enable lacp preempt delay delay-time
C) You can run the following commands to add member interfaces to an Eth-Trunk: trunkport GigabitEthernet0/0/1
D) You can run the following commands to enable load balancing based on source IP addresses for an Eth-Trunk: load-balance src-dst-ip
A) You can run the following commands to delete member interfaces from an Eth-Trunk: interface GigabitEthernet0/0/1 shutdown undo eth-trunk 1 undo shutdown
B) You can run the following commands to prevent frequent flapping due to physical link faults on an Eth-Trunk: interface eth-trunk 1 lacp preempt enable lacp preempt delay delay-time
C) You can run the following commands to add member interfaces to an Eth-Trunk: trunkport GigabitEthernet0/0/1
D) You can run the following commands to enable load balancing based on source IP addresses for an Eth-Trunk: load-balance src-dst-ip

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
64
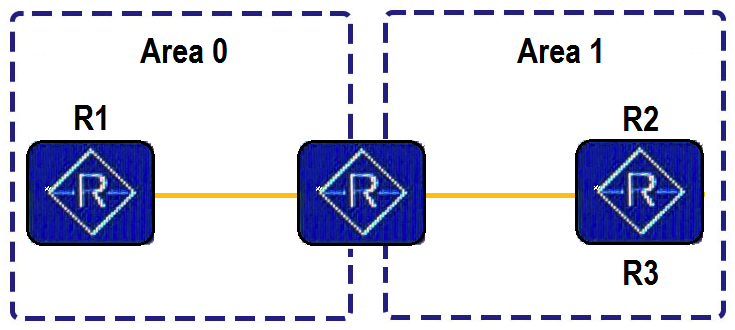 As shown in the following figure, R1, R2, and R3 run OSPF and advertise their loopback interface addresses into OSPF. Which of the following statements is false?
As shown in the following figure, R1, R2, and R3 run OSPF and advertise their loopback interface addresses into OSPF. Which of the following statements is false?A) The filter import command can be executed on R2 in Area 0 to filter loopback interface routes of R3.
B) The filter-policy import command can be executed on R1 to filter loopback interface routes of R3.
C) The filter export command can be executed on R2 in Area 1 to filter loopback interface routes of R3.
D) The filter-policy export command can be executed on R2 to filter loopback interface routes of R3.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
65
Which of the following statements regarding the stub area and NSSA in OSPF is false?
A) The Type 5 LSA cannot be flooded to a stub area, but can be flooded to an NSSA.
B) The Type 3 LSA can be flooded to a stub area and an NSSA.
C) The Type 4 LSA cannot be flooded to a stub area and an NSSA.
D) The Type 7 LSA cannot be flooded to a stub area, but can be flooded to an NSSA.
A) The Type 5 LSA cannot be flooded to a stub area, but can be flooded to an NSSA.
B) The Type 3 LSA can be flooded to a stub area and an NSSA.
C) The Type 4 LSA cannot be flooded to a stub area and an NSSA.
D) The Type 7 LSA cannot be flooded to a stub area, but can be flooded to an NSSA.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
66
You must ensure that mission critical traffic is prioritized in the HW network. The IP precedence of a packet can be determined by which of the following?
A) The three most significant bits of the ToS byte
B) All 8 bits of the ToS byte
C) The three least significant bits of the ToS byte
D) Bit 4, 5, and 6 of the ToS byte
A) The three most significant bits of the ToS byte
B) All 8 bits of the ToS byte
C) The three least significant bits of the ToS byte
D) Bit 4, 5, and 6 of the ToS byte

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
67
Type 5 LSAs in OSPF are used to transmit external routes. Which of the following statements regarding Type 5 LSAs is false?
A) Type 5 LSAs are advertised by ASBRs and flooded on OSPF networks except stub areas and NSSAs.
B) Filtering policies can be configured on ABRs or ASBRs to filter Type 5 LSAs.
C) A Type 5 LSA contains the FA address, which is 0.0.0.0. The FA address is reserved only and does not take effect.
D) Routers in the same area as the ASBR can calculate external routes through intra-area LSAs and Type 5 LSAs.
A) Type 5 LSAs are advertised by ASBRs and flooded on OSPF networks except stub areas and NSSAs.
B) Filtering policies can be configured on ABRs or ASBRs to filter Type 5 LSAs.
C) A Type 5 LSA contains the FA address, which is 0.0.0.0. The FA address is reserved only and does not take effect.
D) Routers in the same area as the ASBR can calculate external routes through intra-area LSAs and Type 5 LSAs.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
68
A route selection tool can define multiple entries. Which of the following tools will automatically generate a deny-any entry at the end of the configuration?
A) Route policy
B) IP-prefix
C) Community-filter
D) AS-Path-filter
A) Route policy
B) IP-prefix
C) Community-filter
D) AS-Path-filter

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
69
To improve delay and jitter on frame relay links, we can fragment and assemble the frame between multiple PVCs. This is similar to what happens with PPP multilink.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
70
Which of the following command outputs indicates that a loop has occurred on a switch?
A)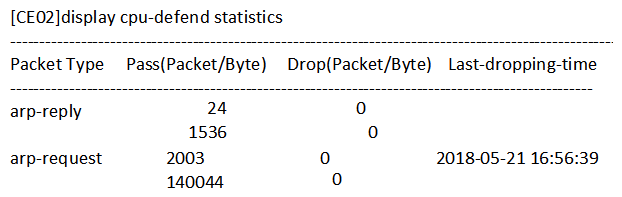
B)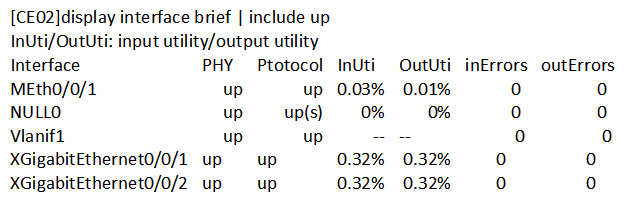
C)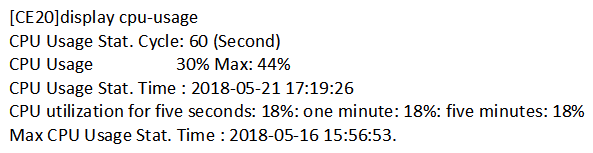
D)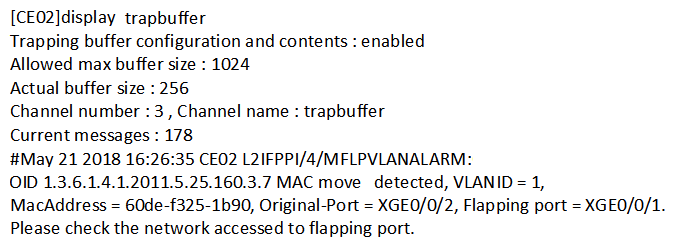
A)

B)

C)

D)


Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
71
Which of the following AS-_Path attribute values can be matched by the AS-Path filter configured using ip as-path filter 1 permit .*(100|400$command?
A) 100
B) 3100
C) 300 4200
D) 1234 1400
A) 100
B) 3100
C) 300 4200
D) 1234 1400

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
72
On a BGP/MPLS Ipv4 VPN, OSPF, LDP, and static routes are configured. Which of the following protocols must be enabled with GR to achieve NSF on PEs? (Multiple Choice)
A) Static routes
B) MPLS LDP
C) OSPF
D) BGP
A) Static routes
B) MPLS LDP
C) OSPF
D) BGP

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
73
Which of the following statements regarding the process of sending and receiving data frames on a port in access link-type is true?
A) Tagged data frames that are received are directly discarded.
B) Only untagged data frames are received.
C) VLAN tags are removed before data frames are sent.
D) A switch learns the destination MAC address in the data frames when they are received on the switch's port.
A) Tagged data frames that are received are directly discarded.
B) Only untagged data frames are received.
C) VLAN tags are removed before data frames are sent.
D) A switch learns the destination MAC address in the data frames when they are received on the switch's port.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
74
How long will a Huawei running RSTP wait before aging out the BPDUs on an interface?
A) Hello time interval
B) 6 seconds
C) MaxAge interval
D) BPDUs on the interface will not be aged out
E) Forward delay
A) Hello time interval
B) 6 seconds
C) MaxAge interval
D) BPDUs on the interface will not be aged out
E) Forward delay

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
75
As shown in the figure below, R1 and R2 are connected through a PPP link, and the IP addresses on the directly connected interfaces are not on the same network segment. R1 and R2 can communicate with each other through the directly connected interfaces. However, communication on the Ethernet link fails if the IP addresses on the directly connected interfaces are on the same network segment. What are the causes of this? 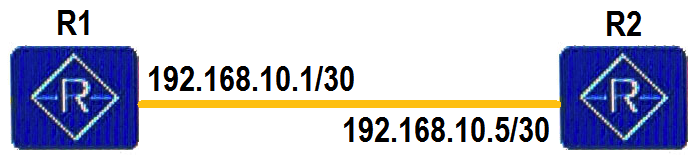
A) The Ethernet header does not need to be encapsulated into data packets between R1 and R2 that are directly connected through a POS interface, and ARP does not need be used to obtain MAC addresses.
B) R1 and R2 that are directly connected through a POS interface learn the MAC address of each other using LCP, and ARP does not need to be used to obtain MAC addresses.
C) R1 and R2 that are directly connected through a POS interface learn the 24-bit subnet route of each other through IPCP.
D) R1 and R2 that are directly connected through a POS interface learn the 32-bit host route of each other through IPCP.
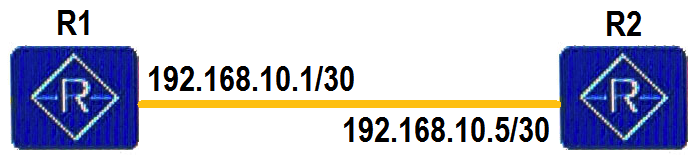
A) The Ethernet header does not need to be encapsulated into data packets between R1 and R2 that are directly connected through a POS interface, and ARP does not need be used to obtain MAC addresses.
B) R1 and R2 that are directly connected through a POS interface learn the MAC address of each other using LCP, and ARP does not need to be used to obtain MAC addresses.
C) R1 and R2 that are directly connected through a POS interface learn the 24-bit subnet route of each other through IPCP.
D) R1 and R2 that are directly connected through a POS interface learn the 32-bit host route of each other through IPCP.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
76
On a broadcast network, DIS election starts only after the neighbor relationship is established.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
77
After the shutdown command is run on one of two directly connected devices that establish an IBGP peer relationship, the BGP connection will not be torn down immediately.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
78
On a Huawei device, when an external route is imported to IS-IS and the tag of the external route is set, the IS-IS metric type does not need to be changed, and the default style is retained.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
79
Which of the following statements regarding PPPoE data frames are true?
A) The Ethernet_Type field has a fixed value of 0x8863.
B) The Session_ID field of a PPP session must be the value specified in the Discovery phase and cannot be changed.
C) When PPPoE is used to transmit session data, Code must be set to 0x0.
D) After a PPPoE session is set up, all Ethernet packets are unicast.
A) The Ethernet_Type field has a fixed value of 0x8863.
B) The Session_ID field of a PPP session must be the value specified in the Discovery phase and cannot be changed.
C) When PPPoE is used to transmit session data, Code must be set to 0x0.
D) After a PPPoE session is set up, all Ethernet packets are unicast.

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck
80
A new Syslog server is being installed in the HW network to accept network management information. What characteristics apply to these Syslog messages? (Multiple Choice)
A) Its transmission is acknowledgment
B) Its transmission is secure
C) Its transmission is not secure
D) Its transmission is not reliable
E) Its transmission is not acknowledged
F) Its transmission is reliable
A) Its transmission is acknowledgment
B) Its transmission is secure
C) Its transmission is not secure
D) Its transmission is not reliable
E) Its transmission is not acknowledged
F) Its transmission is reliable

Unlock Deck
Unlock for access to all 331 flashcards in this deck.
Unlock Deck
k this deck



