Deck 12: Computer Programming
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/150
Play
Full screen (f)
Deck 12: Computer Programming
1
Among the most popular languages for game programming are C and C++.
True
2
Polymorpism provides OO programs with easy extensibility and can help simplify program code.
True
3
You should perform a walkthrough to verify that your algorithm works.
True
4
A sequence greeting changes the order in which instructions are carried out by directing the computer to execute an instruction elsewhere in the program.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
5
Polymorphism refers to the process of hiding the internal details of objects and their methods.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
6
Much of the power and flexibility of the Prolog language stems from its ability to sift through facts.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
7
A predictive methodology requires extensive planning and documentation up front.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
8
Signed certificates assure users that the original software is free of viruses and bugs.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
9
The declarative paradigm attempts to describe problems without specifying exactly how to arrive at a solution.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
10
One of the causes of buffer overflow is sloppy C and C++ programming.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
11
Algorithms are usually written in a format specific to the language to be used.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
12
Java offers a more structured programming environment than C and C++.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
13
COBOL and Fortran are considered second-generation languages.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
14
Pseudocode is a mixture of English and a programming language.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
15
OO programmers often use flowcharts to plan the classes to be programmed.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
16
Another name for threat modeling is risk analysis.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
17
Attack trees are used by security analysts.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
18
A class can produce any number of unique objects.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
19
A single high-level command does the work of multiple low-level commands.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
20
Computer users are discouraged from applying all available software patches.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
21
(Signed) code ensures that the software will not run if even one bit of the source code is changed._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
22
Prolog uses a process called (upwelling) to satisfy goals._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
23
In object-oriented programming,a method is activated by a(n) (message),which is included as a line of code._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
24
In a problem statement,a(n) (known) is something you accept as true in order to proceed with program planning._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
25
Control structures are instructions that specify the sequence in which a program is (written)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
26
You can express an algorithm as (pseudocode)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
27
Machine languages are (second)-generation languages._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
28
One defensive programming technique is to (rewrite) code to decrease its complexity._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
29
C is a(n) (high-level) language._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
30
The (input0 predicate of Prolog gathers data entered by the user._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
31
Programmers can offer a(n) (patch) to fix a defect in a software package that is already in the hands of consumers._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
32
In the context of programming,a(n) (program) statement defines certain elements that must be manipulated to achieve a result or goal._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
33
Software engineers tend to focus on ____.
A) designing
B) coding
C) developing
D) engineering
A) designing
B) coding
C) developing
D) engineering

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
34
A single programmer can,on average,write,test,and document only ____ lines of code per day.
A) 10
B) 15
C) 20
D) 25
A) 10
B) 15
C) 20
D) 25

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
35
A class (attribute) defines the characteristics of a set of objects._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
36
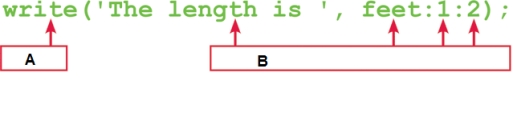
In the instruction in the accompanying figure,Box A points to a(n)____.
A) instruction
B) keyword
C) parameter
D) detail

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
37
Software engineering is a development process that uses ____ techniques to reduce cost and complexity of a computer program.
A) mathematical
B) engineering
C) management
D) all of the above
A) mathematical
B) engineering
C) management
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
38
A(n) (subroutine) (or procedure or function)is a section of code that is part of a program but is not included in the main sequential execution path._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
39
A computer program is typically stored as a file and transferred into ____ when needed.
A) RAM
B) ROM
C) RUM
D) REM
A) RAM
B) ROM
C) RUM
D) REM

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
40
The core of a(n) (OO) diagram is a box that contains information about a class._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
41
A ____ language typically includes commands specific to a particular CPU or microprocessor family.
A) high-level
B) low-level
C) third-generation
D) modular programming
A) high-level
B) low-level
C) third-generation
D) modular programming

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
42
A logic error is a type of ____ error.
A) syntax
B) compile-time
C) runtime
D) interpolator
A) syntax
B) compile-time
C) runtime
D) interpolator

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
43
When using a VDE,a ____ is a screen-based object whose behavior can be defined by the programmer.
A) control
B) property
C) form
D) grid
A) control
B) property
C) form
D) grid

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
44
A ____ error occurs when a program fails to perform as intended due to an error in the design of the program.
A) syntax
B) logic
C) runtime
D) programming
A) syntax
B) logic
C) runtime
D) programming

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
45
A ____ error occurs when an instruction does not follow the grammar of the programming language.
A) syntax
B) logic
C) runtime
D) grammar
A) syntax
B) logic
C) runtime
D) grammar

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
46
In gaming programming,explosions,flares,and fairy dust are accomplished by a(n)____.
A) FX subroutine
B) particle renderer
C) pathfinder
D) animatron
A) FX subroutine
B) particle renderer
C) pathfinder
D) animatron

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
47
When high-level languages were originally conceived in the 1950s,they were dubbed ____-generation languages.
A) first
B) second
C) third
D) fourth
A) first
B) second
C) third
D) fourth

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
48
Within the context of programming,a(n)____ is defined as an action associated with a form or control.
A) form
B) class
C) event
D) control
A) form
B) class
C) event
D) control

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
49

In the instruction in the accompanying figure,Box B points to ____.
A) instructions
B) keywords
C) parameters
D) commands

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
50
A ____ language uses command words and grammar based on human language.
A) high-level
B) low-level
C) machine
D) modular programming
A) high-level
B) low-level
C) machine
D) modular programming

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
51
The traditional approach to programming uses a(n)____ paradigm.
A) procedural
B) programming
C) multi-paradigm
D) object-oriented
A) procedural
B) programming
C) multi-paradigm
D) object-oriented

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
52
Assembly languages are considered ____-generation languages.
A) first
B) second
C) third
D) fourth
A) first
B) second
C) third
D) fourth

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
53
____ is a subset of the English language with a limited selection of sentence structures that reflect processing activities.
A) Pseudocode
B) Structured English
C) Sub English
D) Sub code
A) Pseudocode
B) Structured English
C) Sub English
D) Sub code

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
54
Languages which most closely resemble natural human languages are ____-generation languages.
A) second
B) third
C) fourth
D) fifth
A) second
B) third
C) fourth
D) fifth

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
55
Software specially designed for entering code for computer programs is a(n)____.
A) text editor
B) program editor
C) interpolator
D) VDE
A) text editor
B) program editor
C) interpolator
D) VDE

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
56
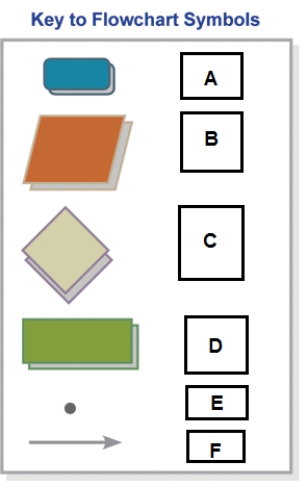
In the accompanying figure,A represents ____.
A) start or end
B) input or output
C) calculation
D) connector

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
57
The first computers were programmed using ____.
A) low-level languages
B) high-level languages
C) rewired circuitry
D) assembler language
A) low-level languages
B) high-level languages
C) rewired circuitry
D) assembler language

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
58
A collection of language-specific programming tools that enable a programmer to develop applications for a specific computer platform is a(n)____.
A) SDK
B) IDK
C) API
D) LPT
A) SDK
B) IDK
C) API
D) LPT

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
59
A computer programming language based on a declarative programming paradigm is a ____-generation language.
A) second
B) third
C) fourth
D) fifth
A) second
B) third
C) fourth
D) fifth

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
60
A ____ provides programmers with tools to build substantial sections of a program by pointing and clicking.
A) text editor
B) program editor
C) code editor
D) VDE
A) text editor
B) program editor
C) code editor
D) VDE

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
61

In the accompanying figure,D represents ____.
A) input or output
B) decision
C) calculation
D) connector

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
62
During ____ execution,the first instruction in the program is executed first,followed by the second.
A) conjunctive
B) sequential
C) parallel
D) functional
A) conjunctive
B) sequential
C) parallel
D) functional

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
63
A(n)____ is a unit of data that represents an abstraction or a real-world entity such as person,place,or thing.
A) class
B) object
C) attribute
D) variable
A) class
B) object
C) attribute
D) variable

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
64
A(n)____ attribute is available only to the routine in which it is defined.
A) class
B) public
C) private
D) object
A) class
B) public
C) private
D) object

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
65
The computer begins executing a Java program by locating a standard method called ____.
A) start()
B) begin()
C) initiate()
D) main()
A) start()
B) begin()
C) initiate()
D) main()

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
66
The first widely used,standardized procedural computer language was ____.
A) BASIC
B) C
C) Fortran
D) C++
A) BASIC
B) C
C) Fortran
D) C++

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
67
A(n)____ paradigm is based on the idea that the solution for a program can be visualized in terms of objects that interact with each other.
A) procedural
B) object-oriented
C) objective
D) declarative
A) procedural
B) object-oriented
C) objective
D) declarative

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
68

In the accompanying figure,E represents ____.
A) flow line
B) decision
C) calculation
D) connector

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
69
A ____ control structure tells a computer what to do based on whether a condition is true or false.
A) sequence
B) selection
C) repetition
D) directing
A) sequence
B) selection
C) repetition
D) directing

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
70
A method is activated by a message which is included as a line of program code also referred to as a(n)____.
A) get
B) fetch
C) call
D) include
A) get
B) fetch
C) call
D) include

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
71
The advantages of polymorphism include ____.
A) easy extensibility
B) simplifying program code
C) the ability to dispense with procedural languages
D) both a and b
A) easy extensibility
B) simplifying program code
C) the ability to dispense with procedural languages
D) both a and b

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
72
____ refers to passing certain characteristics from one class to another class.
A) Extensibility
B) Objectification
C) Inheritance
D) Encapsulation
A) Extensibility
B) Objectification
C) Inheritance
D) Encapsulation

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
73
A ____ control structure changes the order in which instructions are carried out by directing the computer to execute an instruction elsewhere in the program.
A) sequence
B) selection
C) repetition
D) directing
A) sequence
B) selection
C) repetition
D) directing

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
74

In the accompanying figure,B represents ____.
A) start or end
B) input or output
C) calculation
D) connector

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
75

In the accompanying figure,C represents ____.
A) input or output
B) decision
C) calculation
D) connector

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
76

In the accompanying figure,F represents ____.
A) decision
B) flow line
C) calculation
D) connector

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
77
____ attributes define the characteristics of a set of objects.
A) Class
B) Public
C) Private
D) Object
A) Class
B) Public
C) Private
D) Object

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
78
A(n)____ attribute is available for use by any routine in the program.
A) class
B) public
C) private
D) object
A) class
B) public
C) private
D) object

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
79
The ability to redefine a method in a subclass is called ____.
A) encapsulation
B) polymorphism
C) inheritance
D) instantiation
A) encapsulation
B) polymorphism
C) inheritance
D) instantiation

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
80
The first computer language to work with objects,classes,inheritance,and methods was ____.
A) Java
B) C++
C) SIMULA
D) Smalltalk
A) Java
B) C++
C) SIMULA
D) Smalltalk

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck



