Deck 4: Operating Systems and File Management
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question
Question

Unlock Deck
Sign up to unlock the cards in this deck!
Unlock Deck
Unlock Deck
1/150
Play
Full screen (f)
Deck 4: Operating Systems and File Management
1
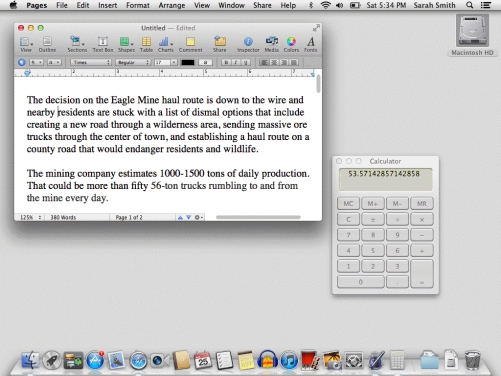
In the GUI shown in the accompanying figure there are two application windows: calculator and word processor.
True
2
In a dual boot system,to change operating systems,you have to reboot.
True
3
When you use Windows,Mac OS,or a Linux graphical file manager,each subdirectory is depicted as a folder.
True
4
A button allows you to select one item from several options.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
5
Microsoft Windows suffers from the reputation for being the most vulnerable to viruses,worms,and other attacks.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
6
A file extension is always the same as a file format.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
7
During the boot process,RAM is loaded into the operating system kernel.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
8
Some systems streamline the backup process by restoring a computer's operating system,device drivers,settings,and data in a single step - a process called restore pointing.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
9
Today's Windows operating systems do not require a kernel that accesses DOS.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
10
Folders cannot be created within other folders.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
11
A root directory can be subdivided into smaller lists.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
12
Often file management is represented by a tree metaphor.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
13
A General Purpose License,or GPL,allows anyone to make copies for their own use or to give or sell to others.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
14
The sequence of events that occurs between the time that you turn on a computer and the time that it is ready for you to issue commands is referred to as the boot process.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
15
To be certain a file can be opened by the recipient,simply save it as an .exe;then anyone can open it.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
16
Viruses can damage files to the point that your computer can't access any data on its hard disk.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
17
With remote backups,the speed for backing up and restoring data is independent of the speed of your Internet connection.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
18
File management utilities usually retain the files within a folder when that folder is deleted.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
19
One of the primary strengths of Windows is security.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
20
During a typical computing session,your computer might run an average of 50 processes.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
21
A(n) (desktop) operating system is designed for a desktop or notebook personal computer._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
22
When formatting a disk,tracks are divided into (sectors)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
23
(UNIX) is rather unique because it is distributed along with its source code under the terms of a GPL (General Public License)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
24
Mac OS X is a good platform for virtual (host) technologies that allow you to use one computer to simulate the hardware and software of another._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
25
When formatting a disk,the disk is divided into (tracks)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
26
A(n) (operating-system) disk is a removable storage medium containing the operating system files needed to boot your computer without accessing the hard disk._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
27
Activities associated with resource management by an operating system include all of the following EXCEPT ____.
A) managing processor resources
B) ensuring that input and output proceed in an orderly manner
C) keeping track of storage resources
D) installing new memory
A) managing processor resources
B) ensuring that input and output proceed in an orderly manner
C) keeping track of storage resources
D) installing new memory

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
28
A file (type) is an optional file identifier that is separated from the main file name by a period._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
29
Current versions of Windows and Mac OS support file names up to (20) characters long._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
30
A(n) (mirrored) user interface provides a way to select menu options and manipulate graphical objects displayed on the screen using a mouse or gesture._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
31
The operating system,application software,and ____ are organized similar to the chain of command in an army.
A) file types
B) device drivers
C) disk sectors
D) desktop
A) file types
B) device drivers
C) disk sectors
D) desktop

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
32
The section of data at the beginning of a file that contains information about a file is the file (format)._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
33
A command to print a document is relayed through various levels of ____.
A) hardware
B) software
C) both a.and b.
D) neither a.nor b.
A) hardware
B) software
C) both a.and b.
D) neither a.nor b.

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
34
A(n)____ system is a type of system software that acts as the master controller for all activities that take place within a computer system.
A) incremental
B) physical storage
C) boot
D) operating
A) incremental
B) physical storage
C) boot
D) operating

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
35
A restore (point) is a snapshot of your computer settings._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
36
Tracks and sectors are (numbered) to provide addresses for each data storage bin._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
37
Online backup services are also referred to as remote or (managed) backup services._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
38
(TIM) pioneered the idea of push technology in which notifications are automatically sent to a device._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
39
All of the following are examples of resources EXCEPT ____.
A) a peripheral
B) RAM
C) storage space
D) All of the above are resources
A) a peripheral
B) RAM
C) storage space
D) All of the above are resources

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
40
A program called (AutoBackup) supplied with Mac OS X is a good example of synchronization software._________________________

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
41
Within a single program,____ allows multiple parts to run simultaneously.
A) multitasking
B) multithreading
C) multiprocessing
D) multicomputing
A) multitasking
B) multithreading
C) multiprocessing
D) multicomputing

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
42
VMWare and Parallels Desktop software are examples of ____.
A) virtual machine software
B) dual boot software
C) application software
D) operating systems
A) virtual machine software
B) dual boot software
C) application software
D) operating systems

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
43
The term ____ is a technical term for the region of memory that holds data waiting to be transferred from one device to another.
A) RAM
B) ROM
C) buffer
D) storage
A) RAM
B) ROM
C) buffer
D) storage

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
44
An operating system's ____ capability supports a division of labor among all the processing units.
A) multitasking
B) multithreading
C) multiprocessing
D) multicomputing
A) multitasking
B) multithreading
C) multiprocessing
D) multicomputing

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
45
Files maintained by the Macintosh operating system can have two parts,called ____.
A) components
B) segments
C) forks
D) identifier and size
A) components
B) segments
C) forks
D) identifier and size

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
46
In the Mac OS,the resource ____ stores information about the data.
A) tab
B) fork
C) segment
D) metadata
A) tab
B) fork
C) segment
D) metadata

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
47
The strengths of Mac OS do NOT include ____.
A) its use of resource forks
B) reliability
C) security
D) all of the above
A) its use of resource forks
B) reliability
C) security
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
48
A ____ is an additional set of commands that the computer displays after you make a selection from the main menu.
A) submenu
B) dialog box
C) menu selection
D) all of the above
A) submenu
B) dialog box
C) menu selection
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
49
Through many editions,the Windows user interface was characterized by a colorful Start button in the ____ corner of the screen.
A) upper-left
B) lower-left
C) upper-right
D) lower-right
A) upper-left
B) lower-left
C) upper-right
D) lower-right

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
50
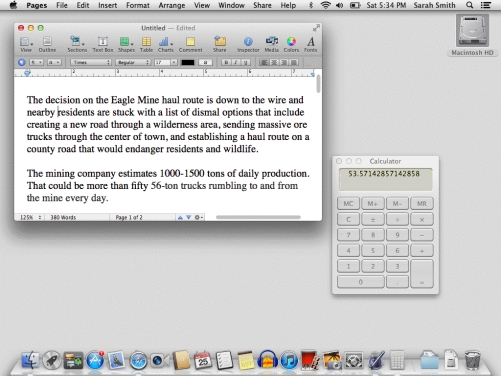
At the upper-right corner of the accompanying figure,the object labeled "Macintosh HD" is an example of a(n)____.
A) icon
B) menu
C) taskbar
D) window

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
51
Microsoft Windows is installed on more than ____ of the world's personal computers.
A) 80%
B) 85%
C) 90%
D) 95%
A) 80%
B) 85%
C) 90%
D) 95%

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
52

In the accompanying figure,the word "Calculator" appears in ____.
A) an icon
B) an Application window
C) the taskbar
D) none of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
53
____ provides process and memory management services that allow two or more tasks,jobs,or programs to run simultaneously.
A) Multitasking
B) Multithreading
C) Multiprocessing
D) Multicomputing
A) Multitasking
B) Multithreading
C) Multiprocessing
D) Multicomputing

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
54

In the accompanying figure,"Untitled" Word Document appears in a(n)____.
A) icon
B) menu
C) widget
D) application window

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
55
The number and variety of programs that run on ____ are unmatched by any other operating system.
A) Mac
B) Windows
C) Chrome
D) Linux
A) Mac
B) Windows
C) Chrome
D) Linux

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
56
The strengths of Microsoft Windows include all of the following EXCEPT ____.
A) number of applications
B) variety of hardware platforms on which it runs
C) large user community
D) reliability
A) number of applications
B) variety of hardware platforms on which it runs
C) large user community
D) reliability

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
57
In the Mac OS,the data ____ contains data or the commands for a program.
A) file
B) fork
C) segment
D) identifier
A) file
B) fork
C) segment
D) identifier

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
58
A ____ displays the options associated with a command.
A) submenu
B) dialog box
C) menu selection
D) all of the above
A) submenu
B) dialog box
C) menu selection
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
59

In the accompanying figure,the icons at the bottom of the screen appear in the ____.
A) menu bar
B) Start menu
C) dock
D) Address bar

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
60
Weaknesses of Mac OS include ____.
A) limited selection of applications
B) typically requires more tinkering
C) cryptic command-line user interface
D) all of the above
A) limited selection of applications
B) typically requires more tinkering
C) cryptic command-line user interface
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
61
Current versions of Windows support file names up to ____ characters long.
A) 125
B) 200
C) 255
D) unlimited
A) 125
B) 200
C) 255
D) unlimited

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
62
The operating system that was developed in 1969 by AT&T's Bell Labs and gained a good reputation for its dependability is ____.
A) INIX
B) UNIX
C) LINUX
D) LUNIX
A) INIX
B) UNIX
C) LINUX
D) LUNIX

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
63
A file ____,in the context of Windows,is a piece of information that describes a file.
A) identifier
B) description
C) tag
D) meta data
A) identifier
B) description
C) tag
D) meta data

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
64
An extension of .sys designates a ____ type of file.
A) configuration
B) support
C) sound
D) database
A) configuration
B) support
C) sound
D) database

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
65
An extension of .wav designates a ____ type of file.
A) configuration
B) support
C) sound
D) database
A) configuration
B) support
C) sound
D) database

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
66
A computer file's location is defined by a ____.
A) file name
B) file specification
C) file extension
D) file folder
A) file name
B) file specification
C) file extension
D) file folder

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
67
A Linux ____ contains the Linux kernel,system utilities,GUI,applications,and installation routine.
A) set
B) group
C) distribution
D) push
A) set
B) group
C) distribution
D) push

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
68
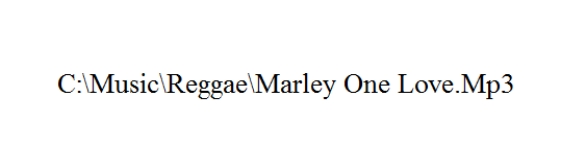
In the accompanying figure,Marley One Love is an example of a ____.
A) primary folder
B) secondary folder
C) file name
D) file extension

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
69
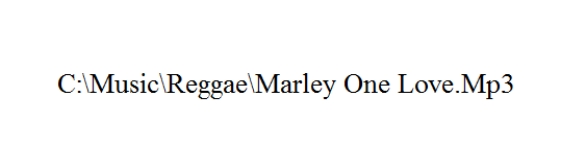
In the accompanying figure,mp3 is an example of a ____.
A) primary folder
B) secondary folder
C) file name
D) file extension

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
70
____ was developed by a Finnish student.It continues to gain popularity as an operating system for personal computers.It is distributed under the terms of a GPL.
A) INIX
B) UNIX
C) LINUX
D) LUNUX
A) INIX
B) UNIX
C) LINUX
D) LUNUX

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
71
An extension of .ocx designates a ____ type of file.
A) configuration
B) support
C) sound
D) database
A) configuration
B) support
C) sound
D) database

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
72
The significance of ____ data is that it cannot be intercepted by corporate spies or government censors.
A) encrypted
B) packaged
C) saved
D) parsed
A) encrypted
B) packaged
C) saved
D) parsed

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
73
The difference between the Save and the Save As commands is that ____.
A) one is used with an existing file and one is used when a new file without a name is open
B) one is used with an existing file,and one is used when you need a new name
C) one is used with an existing file,and one is used when you want to save in a new location
D) all of the above
A) one is used with an existing file and one is used when a new file without a name is open
B) one is used with an existing file,and one is used when you need a new name
C) one is used with an existing file,and one is used when you want to save in a new location
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
74
An optional file identifier that is separated from a main file name by a period is a ____.
A) file convention
B) file extension
C) file path
D) file folder
A) file convention
B) file extension
C) file path
D) file folder

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
75
RIM is the ____ company that developed the BlackBerry smartphone.
A) Canadian
B) American
C) Finnish
D) Chinese
A) Canadian
B) American
C) Finnish
D) Chinese

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
76
The main directory maintained by your computer's operating system is the ____ directory.
A) root
B) leaf
C) preset
D) support
A) root
B) leaf
C) preset
D) support

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
77
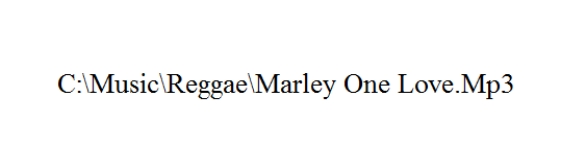
In the accompanying figure,Reggae is an example of a ____.
A) drive
B) primary folder
C) secondary folder
D) file name

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
78
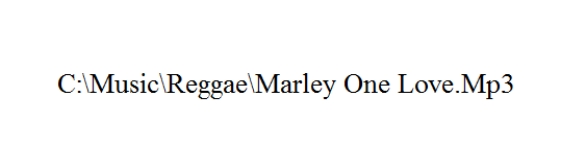
In the accompanying figure,"C:" is an example of a(n)____.
A) drive
B) folder
C) file name
D) extension

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
79
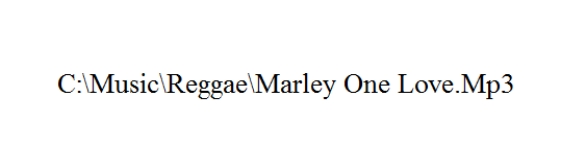
In the accompanying figure,Music is an example of a ____.
A) drive
B) primary folder
C) secondary folder
D) file name

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck
80
File management capabilities available from application software include ____ files.
A) saving
B) renaming
C) deleting
D) all of the above
A) saving
B) renaming
C) deleting
D) all of the above

Unlock Deck
Unlock for access to all 150 flashcards in this deck.
Unlock Deck
k this deck



