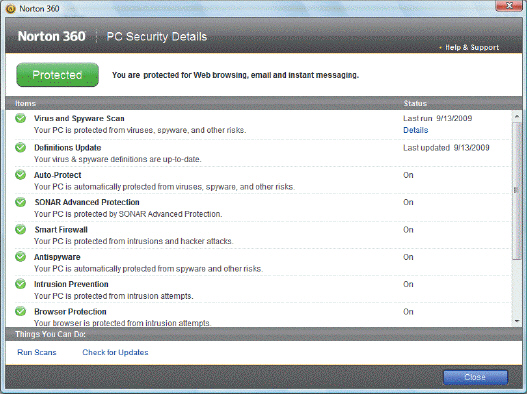
 The application shown in the accompanying figure is an example of a(n) ____.
The application shown in the accompanying figure is an example of a(n) ____.
A) firewall
B) Trojan horse
C) encryption program
D) security suite
Correct Answer:
Verified
Q45: Internet service providers use e-mail _ techniques
Q46: A _ is the basis for encrypting
Q47: A(n) _ contains your computer settings and
Q48: Kyle is training a new employee named
Q49: A good _ can be used to
Q51: The information that antivirus software uses to
Q52: A _ attack is when hackers intercept
Q53: Port scanning software can examine more than
Q54: Kyle is training a new employee named
Q55: _ can encrypt data based on the
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents