FIGURE 30-1 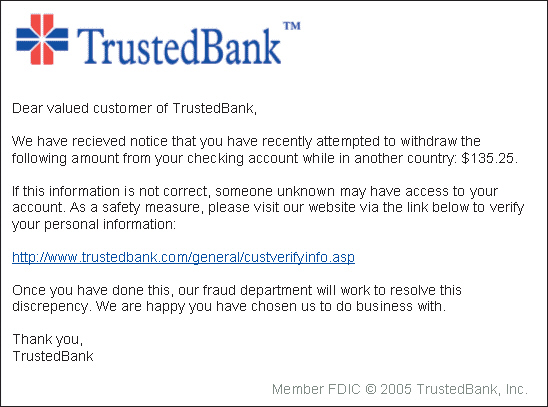 The message in Figure 30-1 above shows an example of ____.
The message in Figure 30-1 above shows an example of ____.
A) hacking
B) phishing
C) sniffing
D) browser hijacking
Correct Answer:
Verified
Q20: Firewalls help prevent employees from tampering with
Q21: The goal of _ is to collect
Q22: TSL and SSL technology enables _.
A) data
Q23: Case 30-2 Molly has just purchased a
Q24: Case 30-2 Molly has just purchased a
Q26: Case 30-1 Nelson is a graphic designer
Q27: A(n) _ is a program that hackers
Q28: Which of the following would be considered
Q29: External hard drives can be used to
Q30: If non-copyrighted information is published on a
Unlock this Answer For Free Now!
View this answer and more for free by performing one of the following actions

Scan the QR code to install the App and get 2 free unlocks

Unlock quizzes for free by uploading documents